Production release notes
| Current | Upcoming | |
|---|---|---|
| Production | 2022.09.0 | 2022.09.1 Production release is scheduled to begin deployment on September 19 |
| Preview | 2022.09.0 |
2022.09.1 Preview release is scheduled to begin deployment on September 14 |
September 2022
2022.09.0: Monthly Production release began deployment on September 6
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 6.7.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Okta ADFS plugin, version 1.7.11
This version of the plugin contains bug fixes, security enhancements, and support for an additional top-level domain. See Okta ADFS Plugin Version History.
Okta MFA Credential Provider for Windows, version 1.3.7
This version of the agent contains fixes, security enhancements, and support for an additional top-level domain. See Okta MFA Credential Provider for Windows Version History.
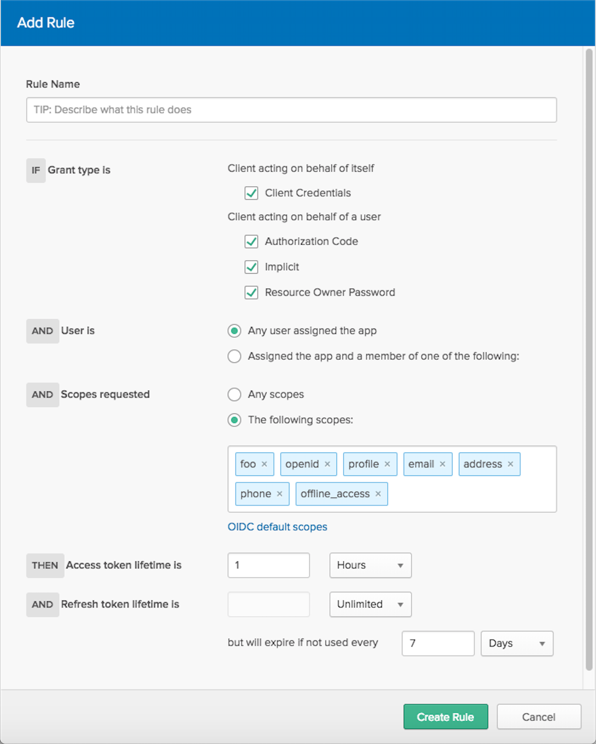
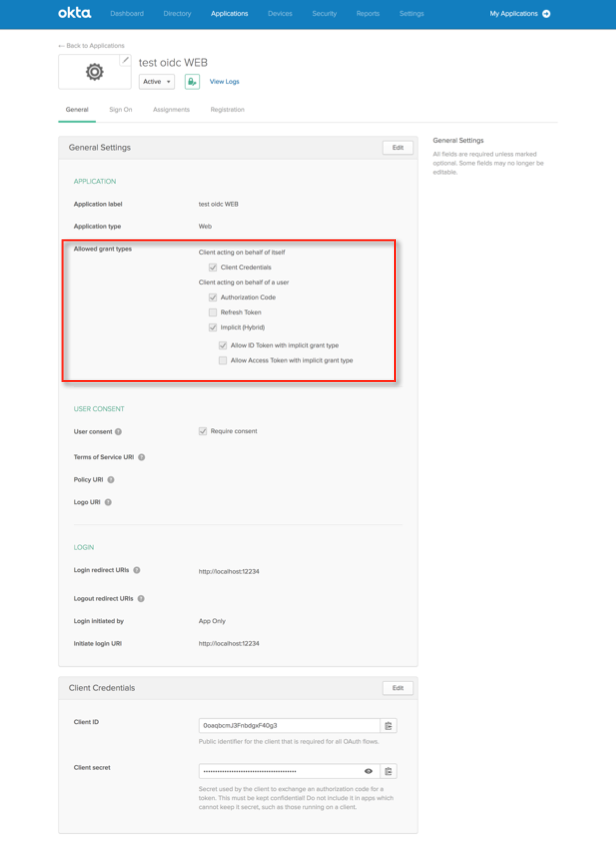
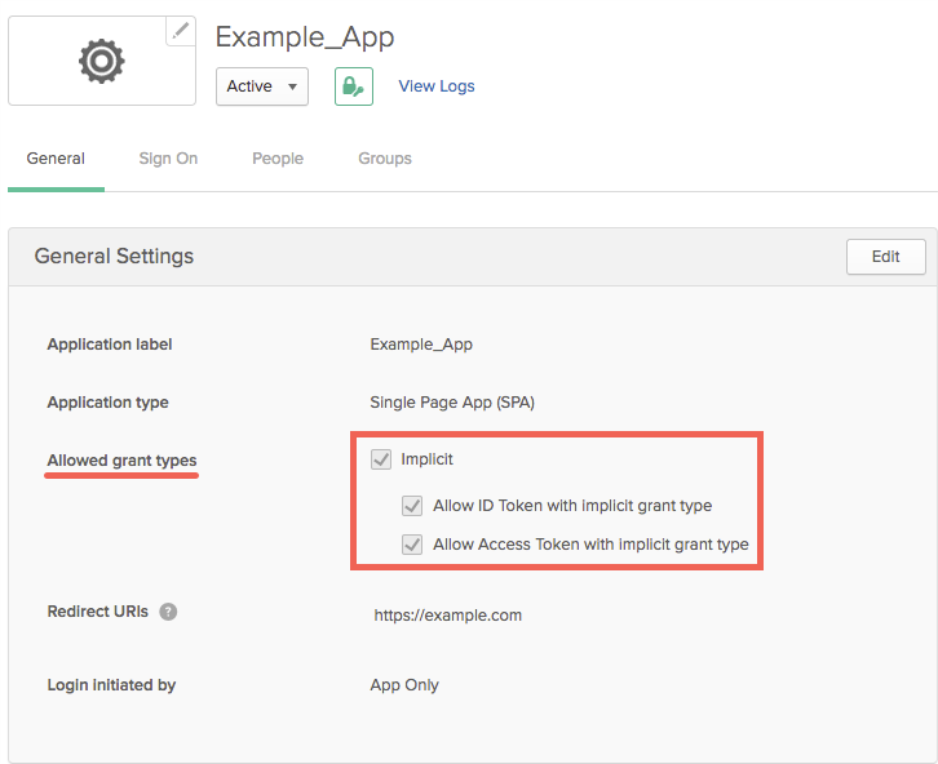
PKCE validation for OIDC app integrations
You can now require Proof Key for Code Exchange (PKCE) as an additional verification step for any OIDC app integration except service apps. The OAuth Security Best Current Practice recommendation is to use PKCE for all uses of the authorization code flow, regardless of the client type. See Create OIDC app integrations using AIW.
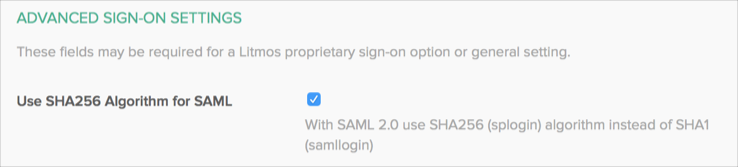
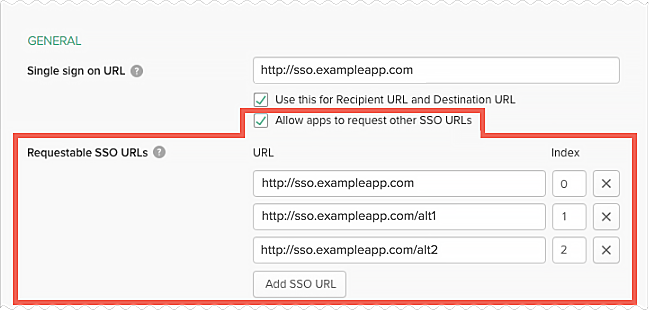
Validation and verification of signed SAML requests
Using signed SAML requests ensures that incoming requests are from genuine applications. When this is configured, Okta only accepts SAML requests signed using the certificate associated with the app integration. Having signed SAML requests also resolves scenarios where the Assertion Consumer Service (ACS) URL requested after authentication can be one of several domains or URLs. When a Service Provider sends a signed authentication request, Okta can accept dynamic ACS values as part of the SAML request and posts the SAML assertion response to the ACS value specified in the request. See the Advanced Settings section of Create SAML app integrations using AIW.
Shared SWA app accounts, password restriction
For SWA apps with an account sign in option set to Users share a single username and password set by administrator, only Super admins or App admins with permissions for that app can view the password.
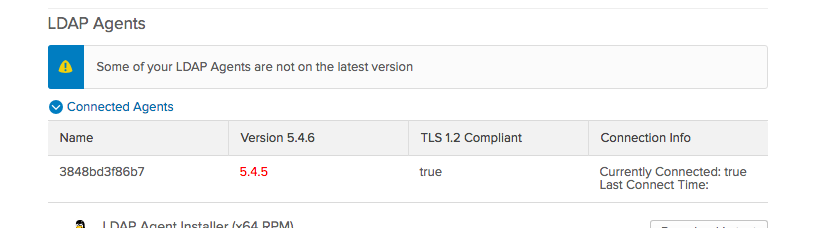
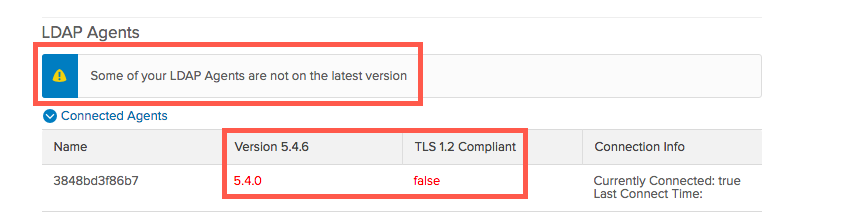
LDAP real-time synchronization
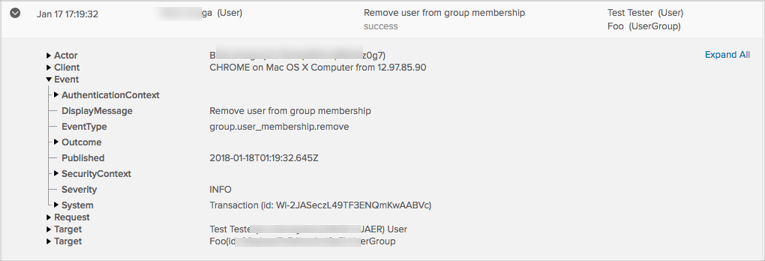
With real-time synchronization, user profiles, groups, and group memberships can now be updated when LDAP-sourced users sign in to Okta, or when they refresh their People page. Admins no longer need to perform full or incremental imports of user attributes, and user profiles, groups, and group memberships are always up to date. Real-time synchronization also reduces the burden on system resources because user attributes are imported and updated individually and not in large groups. See Manage your LDAP integration.
Improved status updates for AD-sourced users
The status of AD-sourced users is now automatically changed from staged to activated following successful Desktop Single Sign-on (DSSO) authentication. This change reduces the time admins need to spend manually activating users and speeds user access to applications. See Active Directory Desktop Single Sign-on.
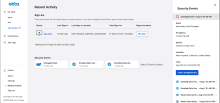
New Recent Activity page on the new Okta end-user dashboard
The Recent Activity page provides end users with a summary of recent sign-in and security events for their Okta account. End users can also report suspicious activity to their Okta admin by clicking I don’t recognize this. See Recent Activity.
Enhancements
Custom domain status
On Customizations > Domain, a new Status field indicates whether the Custom URL Domain configuration is active, pending, or certificate expired. See Customize the Okta URL Domain.
Visual improvements on the Admin Dashboard
The Updated at timestamp now appears at the top right of the Overview widget. The Overview and Status widgets now take up less space. See Dashboard.
OIN Manager user interface changes
The OIN Manager includes the following updates:
- The UI has been updated to match the current Okta style.
- The Okta logo has been updated.
- A note that lists the time required to process new submissions is displayed.
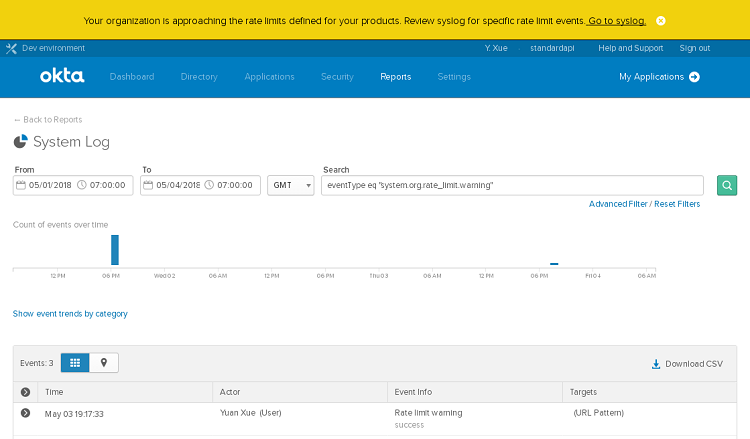
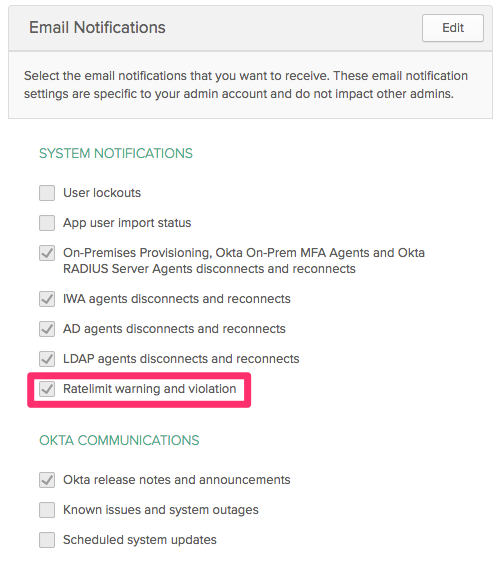
403 error for rate limit violations
When an org reaches its operational rate limit for SMS requests, a 403 Forbidden error is now displayed instead of a 429 Too many requests error. See Configure client-based rate limiting
Early Access Features
New Features
SSO apps dashboard widget
The new SSO apps widget displays the number of user sign-in events across each of your org’s apps over a selected period of time. You can use it to see which apps are used most frequently and to easily monitor the authentication activity across your org. See Monitor your SSO apps.
Fixes
General Fixes
OKTA-489391
Some apps couldn't be assigned using the Assign button if the organization had too many custom object values.
OKTA-496347
The password field in the Add Person widget was incorrectly truncated.
OKTA-499408
The help link for Automatically update Okta Active Directory (AD) agents on the Early Access page pointed to an outdated help topic.
OKTA-504008
The Workflows section of the app details page failed to load when an invalid link was encountered.
OKTA-506480
AD agent emails incorrectly indicated that agents already running the latest version had recently been auto-updated.
OKTA-518347
Some Org2Org users had the same ExternalID on the target org.
OKTA-522043
Users could sign in with the Okta IWA Web agent after delegated authentication was disabled.
OKTA-523140
When Salesforce provisioning was configured using OAuth, Salesforce Community Profiles weren’t displayed.
OKTA-523199
Group app assignments failed due to SQL grammar.
OKTA-523607
Users could sign in with ADSSO after delegated authentication was disabled.
OKTA-524632
Searching for users on the Assign People page returned an Invalid Search Criteria error if the secondary email was marked as a sensitive attribute.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Salesforce (OKTA-516730)
August 2022
2022.08.0: Monthly Production release began deployment on August 8
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Configurable API token rate limits
Admins can now configure a percentage rate-limit capacity for individual API tokens. Previously, when a token rate limit violation occurred, it wasn’t clear which token consumed the limit. Setting a maximum capacity for each token solves this problem and gives admins a new tool to investigate rate-limit violations and plan for future deployments. See API token management.
Salesforce REST OAuth
Admins can now upgrade to the latest version of our Salesforce integration. OAuth authentication will be now used for Provisioning and Imports. See Configure OAuth and REST integration. This feature is made available to all orgs.
Custom Administrator Roles
The standard admin roles available today don’t always meet all the granular delegated administration requirements, which may result in admins having either more or less permissions than they need.
The Custom Administrator Roles feature allows super admins to:
-
Create admin assignments with granular roles, which include specific user, group, and application permissions.
-
Constrain these admin assignments to resource sets.
Use Custom Administrators Roles to:
-
Increase admin productivity.
-
Decentralize the span of access that any one admin has.
-
Grant autonomy to different business units for self-management.
Some important things to note:
-
The Administrators page has been updated with a new, more intuitive interface for managing roles and permissions. See About the Administrators page.
-
Your pre-existing roles are referred to as “standard roles”. The standard role functionality is the same as earlier but the UI is different. See Use standard roles.
-
You can continue using the pre-existing roles and your existing assignments remain the same.
-
You can also assign custom roles to users who have standard roles assigned.
See Custom administrator roles and Best practices for creating a custom role assignment.
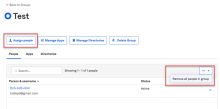
Bulk assign users to groups
Admins can now use bulk import functionality to assign multiple users to specific Okta groups. Bulk user import significantly reduces the time admins spend managing user group assignments. In addition, this functionality makes it easier for large enterprise orgs to adopt Okta as their access management provider. See Bulk assign people to a group. This feature will be gradually made available to all orgs.
Okta Admin Console Groups page enhancements
The Okta Admin Console Groups page has been updated to simplify the addition of large numbers of users to groups and reduce the likelihood that all users can be accidentally removed from a group. In addition, search functionality has been significantly improved to make adding and removing users from groups quicker and easier. See Manage groups. This feature will be gradually made available to all orgs.
Advanced search for users and groups
To make it easier for admins to quickly locate and manage users and groups, enhanced people and group search functionality is now available. Admins can limit search results to specific criteria using the SCIM protocol to query. They can also use Created On and Last Updated On in their queries to identify when users or groups were created or last modified, and search for groups and users using both base and custom attributes. These advanced search options optimize search results and help reduce the time spent searching for specific information. See View group members. This feature will be gradually made available to all orgs.
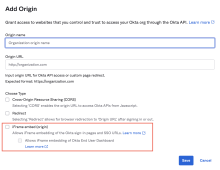
Trusted Origins for iFrame embedding
You can now choose which origins can embed Okta sign-in pages and the Okta End-User Dashboard using Trusted Origins for iFrame embedding. This feature offers a granular control over iFrame embedding compared to the existing embedding option in Customization, which doesn't let you distinguish between secure and non-secure origins. Trusted Origins under Security > API allows you to selectively configure the origins you trust. It also provides enhanced security as it uses a more secure frame-ancestors directive in Content Security Policy that protects your data from web attacks such as clickjacking. You can also migrate your existing iFrames to Trusted Origins. See Trusted Origins for iFrame embedding.
Okta Sign-in Widget, version 6.6
Upgrades to visual assets have been made to reflect latest branding requirements for common 3rd party identity providers (Google, Facebook, and others). This changes the appearance of social login buttons in the Sign-In Widget. Customers who may have self-styled these buttons with CSS overrides may have to adjust overrides to adopt the new defaults, which comply with 3rd party branding requirements.
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta AD agent, version 3.12.0
This version of the agent contains the following changes:
-
Improved group membership information logging
-
Security enhancements
Okta RADIUS Server agent, version 2.17.5
This version of the agent contains security fixes and resolves a memory leak that occurred when agents were configured for EAP-TTLS. See Okta RADIUS Server Agent Version History.
Okta On-Prem MFA agent, version 1.5.1
This version of the agent contains security fixes. See Okta Okta On-Prem MFA Agent Version History.
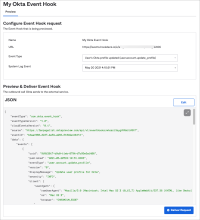
Event hooks for log streaming
To provide better visibility into changes in the state of Okta log streams, event logs pertaining to log stream management, such as stream deactivation, are now eligible for event hooks. Event hooks allow you to automate detection and responses to changes in the state of a log stream. See Log Streaming.
Self-service registration deprecation
The Self-service registration feature is being deprecated from Classic Engine. See End-user registration for information about this expanded feature in Identity Engine. For any questions or concerns, contact your Customer Success Manager (CSM) or Okta Support.
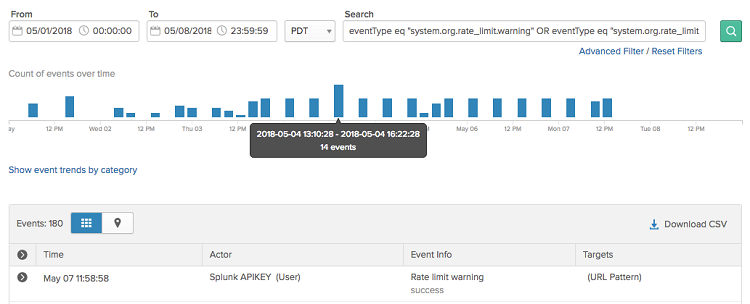
Rate Limits dashboard includes API Token data
The Rate Limits dashboard now includes API Token data on the Rate limit usage over time graph. You can view bar graph data from API tokens or by IP address to review any spike in traffic. See bar graph and API rate limits by token.
Enhancements
System Log events for Report CSV actions
For enhanced security and auditing, the System Log now records new events when CSVs of reports are requested, generated, and downloaded.
System Log events for customer support
To enhance security, System Log events are now generated for every customer support activity, including viewing configurations or data and performing impersonation. Each event includes the user ID of the support person.
System Log update for app sign-on policy
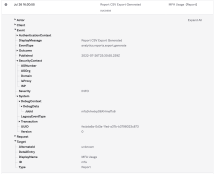
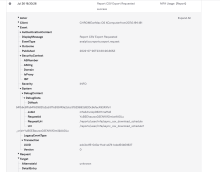
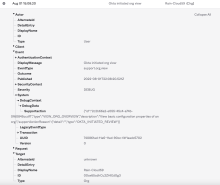
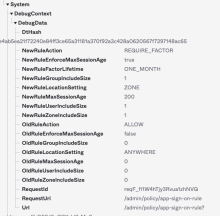
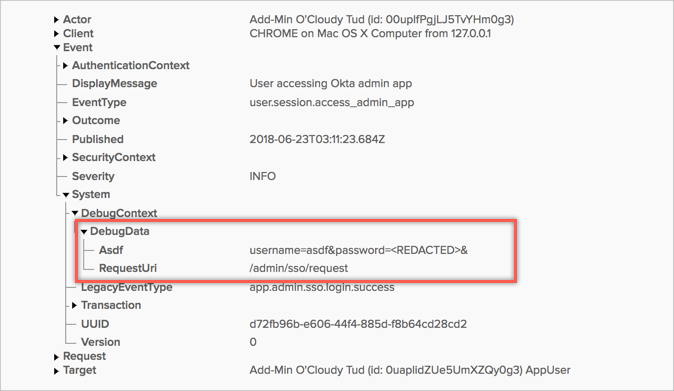
App sign-on policy update events include a new DebugData field with details about how the rule was changed.
System Log update for telephony operations
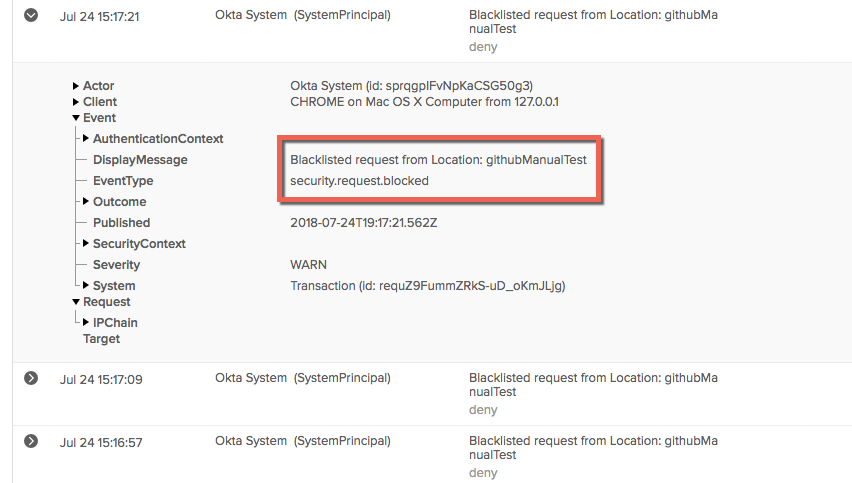
The system.operation.rate_limit.violation event is no longer fired when SMS or Voice messages are blocked due to telephony operational rate limit violations. Instead, telephony system.sms.send.* and system.voice.send.* events are issued as a DENY System Log message.
Microsoft Azure Join documentation
Help documentation is now available for users integrating Azure Join and Okta. See Typical workflow for integrating Hybrid Azure AD Join.
Customization name change
The Disable the Okta interstitial page feature is renamed Disable the Okta loading page. See Configure general customization settings.
AD Agent auto-updates only when operational
The AD agent auto-update scheduler no longer automatically updates non-operational agents. See Schedule agent auto-updates.
OIN Manager enhancements
The contents of the automated email sent when an integration has been moved to Draft after a period of inactivity have been updated.
Dynamic issuer mode for identity providers
You can configure the dynamic issuer mode for an identity provider using the Identity Provider API. When you set issuerMode to DYNAMIC, Okta uses the domain from the authorizeURI as the domain for the redirect URI when returning the authentication response.
Clock skew requirement removed
Users can now access the End-User Dashboard without syncing their device clock to the server time. See The new Okta end-user experience.
Early Access Features
New Features
This release doesn't have any Early Access features.
Fixes
General Fixes
OKTA-454135
The pending user action status was unclear on the new group membership page.
OKTA-466964
The Edit icons on the Application > Provisioning tab were visible to admins who didn’t have the Manage applications permission.
OKTA-494505
Okta Expression Language worked incorrectly in app pages after the page was saved and reloaded.
OKTA-502692
When the Disable Security Question for Recovery feature was enabled and an admin used the Users API to create a user with a pre-assigned password, the magic link sent in the activation email didn't expire after the first use.
OKTA-505852
AD agents running versions prior to 3.8.0 were displayed in existing auto-update schedules.
OKTA-508762
Workday incremental imports with a pre-hire level set prematurely picked up some updates from within the pre-hire interval.
OKTA-509671
When a custom admin role was deleted, users with no other assigned admin roles could still see the Admin button on the Okta End-User Dashboard.
OKTA-510346
Imports failed when the same object was deleted twice.
OKTA-511933
LDAP agents failed to parse queries when group names had special characters.
OKTA-512433
On the Admin Dashboard, the Items count for the Applications can be updated to use SAML task wasn’t correct.
OKTA-515783
Sometimes, in the Groups page Description column, an equals sign (=) replaced the forward slash ( / ) in LDAP-sourced group names.
OKTA-517100, OKTA-517101
VoiceOver screen readers didn’t read the text for country names or the values in the Set up Options list of the Sign-In Widget during Okta Verify registration.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Accredible (OKTA-511942)
-
SurveyMonkey (OKTA-509109)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Talking Talent: For configuration information, see Okta Configuration Guide for Talking Talent.
OIDC for the following Okta Verified applications:
- Doccly Lender: For configuration information, see the Okta Integration Guide.
- Mux: For configuration information, see How to set up an Okta Single Sign-On integration for Mux.
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-493980
The OK button on the post-import screen didn’t work after AD imports were completed.
OKTA-499402
Some AD users couldn’t be confirmed and activated using the Create Users API.
OKTA-518622
The Office 365 app sometimes failed to save Sign On tab changes in WS-Federation Auto mode, when multiple domain federation was enabled.
OKTA-521207
The Security Events section on the Recent Activity page became unresponsive if user agent information was missing from event logs.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
SurveyMonkey (OKTA-517783)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Juro: For configuration information, see the Juro SCIM Configuration Guide.
SAML for the following Okta Verified applications:
-
Plumm (OKTA-472978)
-
RecruitBot (OKTA-520397)
-
Talking Talent (OKTA-501296)
Generally Available
Fixes
General Fixes
OKTA-508490
Okta Verify push notifications originating from Okta RADIUS agent version 2.17.4 displayed the RADIUS server's location instead of the user's (client) location.
OKTA-518573
Admins whose custom role only contained the Edit application’s user assignments permission couldn’t view the Application page for OIDC apps.
OKTA-520653
An error message appeared when admins attempted to upload the Symantec VIP certificate on the Symantec VIP Settings page.
OKTA-521640
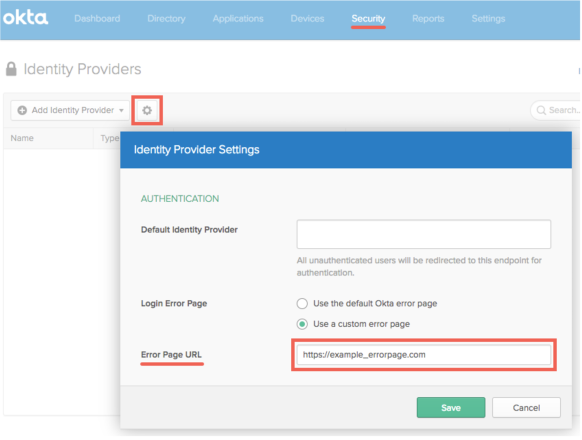
The Contact your administrator message wasn’t displayed on custom error pages.
OKTA-522376
On the End-User Dashboard, users couldn’t close an app drawer by clicking the menu on the app tile.
OKTA-526305H
An error occurred when running scheduled profile sync jobs for provisioned apps.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Blackblaud (OKTA-516841)
-
Bloomberg (OKTA-517367)
-
The Hartford EBC (OKTA-521645)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- FiveTran: For configuration information, see Fivetran SCIM configuration guide for Okta.
- Island: For configuration information, see Island Configuration Guide (you'll need Island permissions to access this documentation).
- Observe: For configuration information, see Observe + Okta | SCIM Instructions.
- Smartsheet: For configuration information, see Directory integration with Okta.
SAML for the following Okta Verified applications:
-
Island (OKTA-508653)
-
Money Forward IT Management Cloud (OKTA-520399)
Generally Available
Fixes
General Fixes
OKTA-474140
When an admin added a custom SMS translation that exceeded the maximum character length, the list page displayed the newly added translation even though the API request failed. After the page was refreshed, this newly added translation disappeared.
OKTA-485674
App-level roadblocks weren’t triggered for AD instances when org-level roadblocks were disabled.
OKTA-499602
Despite having insufficient permissions, a report admin was able to use the Mappings API to edit the UD mappings for an Identity Provider configured in Okta.
OKTA-502227
Imported passwords with a malformed bcrypt hash format caused an error during the password reset flow.
OKTA-505861
App user lists weren't updated on the page after they were edited and saved.
OKTA-517168
SAML IdPs and certificates weren’t displayed properly in the Admin Console.
OKTA-517781
Office 365 roles weren’t properly provisioned in Okta for some users in AD groups.
OKTA-517881
The Custom Authenticator didn’t check whether the client app was a desktop or mobile application that runs on a particular type of device.
OKTA-522531
Okta didn’t verify location information for network zone validation when users signed in.
OKTA-522539
The SCIM configuration's Excluded Fields option didn't work as intended.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Ray Wenderlich (OKTA-524067)
-
Team Grantt (OKTA-522984)
-
Travelers Insurance (OKTA-518696)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- CloudGate: For configuration information, see How to configure SCIM for CloudGate.
- Grayscale: For configuration information, see Okta SCIM Guide for Single Sign-On.
- LUSID: For configuration information, see Provisioning LUSID using Okta and SCIM.
- Wayleadr: For configuration information, see SCIM Integration with Okta.
SAML for the following Okta Verified application:
-
LUSID (OKTA-524169)
OIDC for the following Okta Verified application:
- BeyondTrust Privilege Management Cloud - Windows and Mac: For configuration information, see BeyondTrust Add PMC Instance to Okta.
July 2022
2022.07.0: Monthly Production release began deployment on July 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta LDAP agent, version 5.14.0
This version of the agent contains security fixes. See Okta LDAP Agent version history.
Server-generated secret keys lengthened
Server-generated secret keys have been lengthened to enhance security. These keys are used to generate one-time passwords for multifactor authentication in FIPS-enabled environments and orgs.
Password synchronization for LDAP-sourced users
When the passwords of LDAP-sourced users are reset in Okta and LDAP delegated authentication is enabled, the new password is now immediately synchronized to the user's assigned applications that are configured for password synchronization. This change makes sure that user passwords remain current and reduces the likelihood that users will be unable to access their applications. See Application password synchronization.
Configure sign-on policies based on identity providers
Admins now have the option to configure a sign-on policy based on a specific identity provider. This allows admins more flexibility to dictate which IDP can be used to obtain an Okta session. See Configure an Okta sign-on policy.
SSO capability to OIN apps
Customers who subscribe to the MFA-only package of services now have basic single sign-on functionality to Okta Integration Network apps.
Legacy user group ID support
Validation rules have been relaxed to support user group entity legacy ID formats created prior to 2012.
OIN Manager developer terms
OIN Manager pages now include links to developer terms and conditions. See Developer Terms.
Enhancements
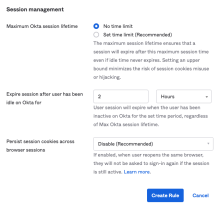
Session management section for adding an Okta sign-on policy rule
A new Session management section is available when adding a new Okta sign-on policy rule or editing an existing one.
The section includes two new options:
-
Maximum Okta session lifetime: Set time limit for user sessions.
-
Persist session cookies across browser sessions: Allow the user to continue a session after reopening a closed browser.
These options were previously only available through the Okta API, but now they can be configured from the Admin Console also.
Session Expires After is now renamed Expire session after user has been idle on Okta for.
Additional warnings and descriptions clarify the functionality of the fields and how to better configure them.
User.session.start System Log events
A user.session.start System Log event is fired after successful app-specific DelAuth sign-in events.
Default policy new conditions
The default authentication now allows access with any two factor types and requires re-authentication after 12 hours. See Add an authentication policy rule.
OIN App Catalog user interface changes
The Languages Supported section of the app details page has been removed.
Improvements to API authorization server interface
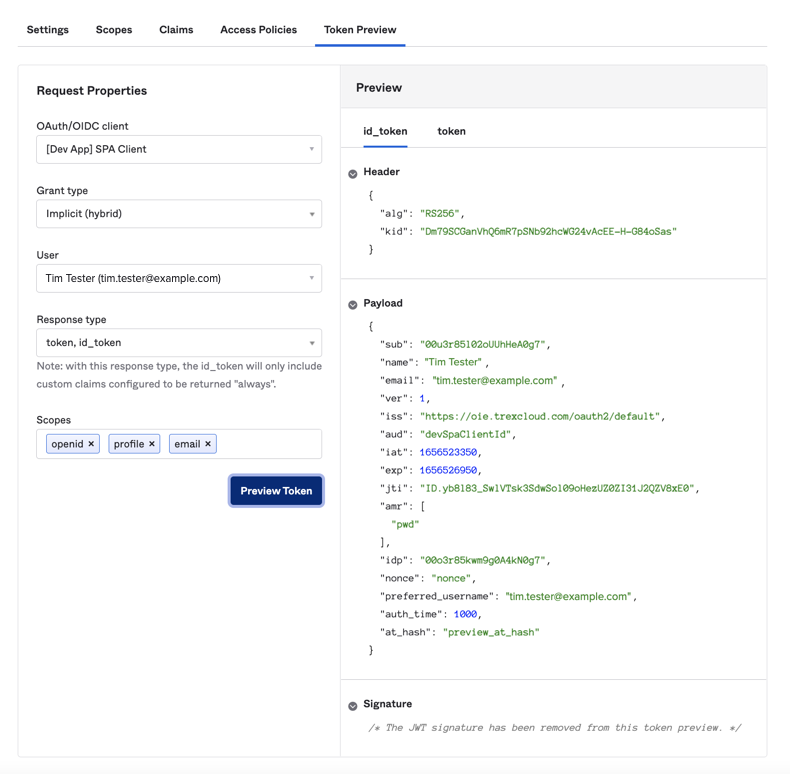
Administrators working with OIDC client applications can now see a preview of the information contained in the refresh token and the device secret returned by the authorization server. See API Access Management.
New HealthInsight security task
A new MFA Requirements task appears if admins set up an Okta sign-on policy with New Device behavior but don't select At every sign-in.
The purpose of this security task is to ensure that the MFA requirements configured by the admin aren’t in conflict with Okta Behavior Detection functionality, and that the MFA policy rule isn’t bypassed unintentionally. When admins select the security task, recommendations appear for correcting the configuration. See MFA requirements.
Organization settings name change
The Organization section of the Security > General page is renamed Organization Security. See General Security.
Early Access Features
New Features
This release doesn't have any Early Access features.
Fixes
General Fixes
OKTA-449159
In the Add Identity Provider - Microsoft UI, the Microsoft Scopes help link pointed to an incorrect URL.
OKTA-480772
AD-sourced users who reset their passwords in AD had to reset their passwords again when using IWA or ADSSO to sign in to Okta.
OKTA-481136
When users were provisioned to AD from Okta, mappings from AD to Okta weren't applied for appuser.externalId.
OKTA-498957
When configuring SAML signing certificates for a SAML 2.0 app, admins were unable to right-click and copy the Identity Provider metadata link in the Admin Console.
OKTA-500367
Unique properties associated with non-existent users weren't cleared when user validation failed during user creation.
OKTA-506002
Since uniqueness requires exact value matches, making schema properties of type Number unique was an issue and is no longer supported. Use Integer or String properties instead.
OKTA-506333
Warning messages appeared on the Okta Sign-On Policy - Add Rule and Edit Rule page even though the relevant fields weren’t visible.
OKTA-507888
On the Pages panel of Customizations > Branding, the Okta defaults appeared instead of an org’s selected theme.
OKTA-509079
The Welcome page, SMS reminder prompt, and security image prompt weren’t shown for users who accessed Okta using AD SSO in Incognito mode.
OKTA-510483
Sometimes an error occurred when an admin attempted to edit a resource set that included a deleted app.
OKTA-515057H
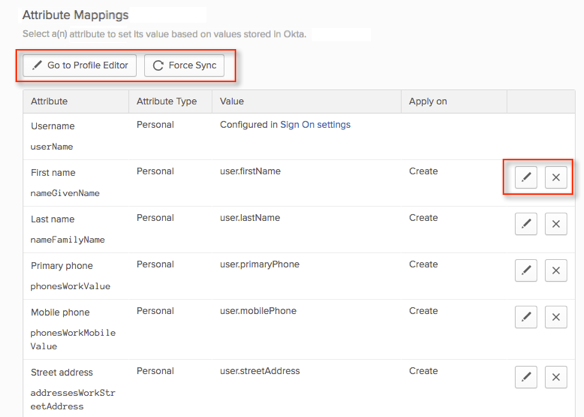
Clicking the Force Sync button resulted in a 404 error with an incorrect message.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
GetFeedback (OKTA-505764)
-
GoToWebinar (OKTA-502955)
-
NordLayer (OKTA-505977)
Weekly Updates
Generally Available
Fixes
OKTA-511954HF
Refreshing the LDAP schema attribute list ignored CaseIgnoreString type attributes from AD LDS.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
QuickBooks (OKTA-508237)
Applications
New Integrations
New SCIM Integration application
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Millie: For configuration information, see Provisioning Setup - Okta.
Generally Available
Fixes
General Fixes
OKTA-472638
Operations that assigned custom roles to a user or group and included a nonexistent resource returned an HTTP 500 Internal Server Error.
OKTA-478496
LDAP incremental imports were converted to full imports when the wrong ModifyTimestamp was set.
OKTA-485621
The expiration time on the custom email template for the Password Reset by Admin was disabled in UTC.
OKTA-496351
When an admin selected a customized display language, some text on the Admin Dashboard was misaligned and some links remained untranslated.
OKTA-498030
Users weren't assigned to an app under group-managed app assignments when the app instance was deactivated and later reactivated.
OKTA-500540
Some admins couldn’t add Velocity macros to their custom email templates.
OKTA-502195
The formatting for the last updated timestamp was inconsistent on the Email and Error pages code editors.
OKTA-509046
IP addresses weren’t rendered correctly when users clicked See All on the Networks page.
OKTA-509722
The dropdown menu that appears when an admin clicks their username wasn’t aligned properly.
OKTA-510274
Custom logos didn't appear correctly on the Device Trust error page.
OKTA-513592
In some Preview orgs, admins couldn't successfully generate password health reports.
OKTA-514634
The layout of the Error pages code editor was inconsistent with other code editors.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
Meetup (OKTA-513999)
Applications
Application Updates
-
The BombBomb OIDC integration is updated to use the following URLs:
-
Additional Redirect URI: https://auth.bombbomb.com/login/callback
-
Post Logout Redirect URI: https://app.bombbomb.com/app/index.php?actn=logout
-
-
The Airtable SCIM integration is updated to support Push user updates. See How to manage users via IdP sync - ELA only for more info.
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Plumm: For configuration information, see Configuring Provisioning for Plumm.
SAML for the following Okta Verified applications:
-
iCIMS Talent Cloud (OKTA-507875)
-
NexTraq (OKTA-454943)
-
Torq (OKTA-511525)
-
Vanta (OKTA-514567)
June 2022
2022.06.0: Monthly Production release began deployment on June 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 6.4.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Hyperdrive agent, version 1.2.0
Okta for MFA provides more security for Electronic Prescribing for Controlled Substances (EPCS) clinician flows when using the Epic Hyperdrive platform. This plugin is compatible with both Classic Engine and Identity Engine orgs (EPCS clinician flows for customers still using the deprecated Epic Hyperspace platform aren't supported on Identity Engine). See MFA for Electronic Prescribing for Controlled Substances - Hyperdrive and Okta Hyperdrive agent version history.
Okta LDAP agent, version 5.13.0
This version contains:
-
An upgraded version of Amazon Corretto
-
Security fixes
-
Improved handling of exception in poller thread
-
Bug fixes
This agent will be gradually made available to all orgs.
JIRA Authenticator Toolkit, version 3.1.9
This version contains:
-
Support for Jira 8.22.2
-
Bug fixes
Okta Browser Plugin, version 6.10.0
This version includes the following fixes:
- Some elements weren't accessible in the Okta Browser Plugin Change password dialog.
- The Okta Browser Plugin briefly displayed a prompt when users opened SWA apps from the dashboard.
Expose groups in the LDAP interface directory information tree (DIT)
To simplify access control decisions for their orgs, admins can now select the groups they want to expose in the LDAP interface directory information tree (DIT). In addition to Okta groups, admins now have the option to view the application groups that are significant to their orgs, including Active Directory (AD) and LDAP groups. See Expose app groups in the LDAP interface directory information tree.
Enhancements
System Log events for telephony rate limit violations
Telephony system.sms.send.* and system.voice.send.* events are now issued with a DENY System Log message when SMS or voice messages are blocked due to telephony operational rate limit violations. The system.operation.rate_limit.violation event is still fired but will be deprecated in the 2022.08.0 release.
Additionally, the way that the MobilePhoneID hash is created for all system.sms.send.* and system.voice.send.* events is changed.
See System Log.
Enhancements to the base OIDC IdP connector
The generic OpenID Connect (OIDC) identity provider (IdP) connector offers PKCE as an additional verification mechanism. You can also define a regular expression to match Okta usernames when authenticating through this connector. See Create an Identity Provider in Okta.
OIN Manager user interface changes
The OIN Manager includes the following updates:
-
The App categories field has been renamed to Use cases to be consistent with the OIN catalog.
-
Single Sign-On is the default use case.
JWT claim enhancement
For custom JSON Web Token (JWT) claims, the name portion now supports the URI format, including the slash and colon characters. Any name containing a colon character must be a URI.
System Log enhancement for inline hook types
The inline hook type is now included in the debug data for a System Log debug context event.
Unique names enforced for custom admin roles
When a super admin creates a custom admin role with a duplicate role name, the following error message now appears: There is already an admin role with this name. See Custom administrator roles.
Improved text for resource set constraints
On the Create new resource set and Edit resource set pages, the Constrain to all check box labels now include the selected resource type (Constrain to all groups, for example). See Work with the resource set component.
Policy condition text changes
Enhancements were made to the multifactor authentication items on the Okta Sign-On Policy Add Rule modal to improve user experience. See Configure an Okta sign-on policy.
Reschedule your OIE upgrade directly from the Okta Administrator Dashboard
The OIE Upgrade widget that appears on the Administrator Dashboard for orgs with a scheduled OIE upgrade now provides the ability to reschedule the upgrade. When you click the Reschedule my upgrade link on the widget, a dialog opens where you can select a new time and date for the upgrade. See Upgrade to Okta Identity Engine.
Customers can opt for empty mandatory fields
Okta now fails provisioning jobs when it receives an empty or null value in mandatory fields during SCIM integration. Customers can revert to the previous behavior by contacting Okta support.
Group limit removed for Authorization Code grant type flows
The 100-group limit for the /token endpoint is removed for the Authorization Code and Authorization Code with PKCE grant type flows.
Early Access Features
New Features
Run delegated flows from the Admin Console
With delegated flows, admins can be assigned the ability to run Okta Workflows directly from the Admin Console. Flows that are delegated to an admin appear on the Delegated Flows page where they can be invoked without signing in to the Workflows Console. This gives super admins more granular control over their admin assignments. See Delegated flows.
OIDC Identity Providers private/public key pair support
Previously, Okta only supported the use of client secret as the client authentication method with an OpenID Connect-based Identity Provider. Okta now supports the use of private/public key pairs (private_key_jwt) with OpenID Connect-based Identity Providers. Additionally, the Signed Request Object now also supports the use of private/public key pairs. See Create an Identity Provider in Okta.
Fixes
General Fixes
OKTA-402945
Some read-only admins could edit General Security settings.
OKTA-462264
In the Application accounts need deprovisioning task, selecting a single task to rerun caused Okta to rerun all tasks.
OKTA-471339
Creating a new LDAP integration from the App Catalog resulted in a Resource not found error.
OKTA-479711
When a user added or removed from a group with a custom admin role, the System Log displayed a Grant user privilege event.
OKTA-480925
Admins didn’t receive timely email notifications when users locked themselves out of their accounts.
OKTA-481268
Some IP addresses didn’t display GeoLocation data in the System Log.
OKTA-482826
Some users imported from Active Directory were stuck in one-time password mode if they were activated more than once.
OKTA-488912
When a super admin searched for a group on the Edit resources to a standard role page, the search results didn’t appear until the admin typed in at least three characters.
OKTA-489049
When admins clicked the Tasks tab on the End-user Dashboard, the page took too long to load and the web browser became unresponsive if there were a large number of entitlements.
OKTA-489500
VoiceOver screen readers didn’t read the text for the Can’t scan? link on the Setup Options page when users tried to enroll themselves in Okta Verify.
OKTA-491194
Deleting a custom attribute created a job that consistently timed out for orgs with a large number of users.
OKTA-491583
When using an OIDC app with refresh tokens, clients could obtain an access token through an existing refresh token if the user consent to the offline_access scope was revoked.
OKTA-493059
Admins couldn't upload certificate chains in tree format.
OKTA-493075
The Admin Role Assignments report sometimes included duplicate records.
OKTA-496025
The Delete dialog in the LDAP interface was missing a question mark.
OKTA-497498
Some apps deleted the app username during user provisioning.
OKTA-497934
The Group Search endpoint didn't reflect the last membership update.
OKTA-501623
Simultaneous user profile updates and deactivations sometimes resulted in a permanent DEACTIVATING status for the user.
OKTA-501729
When an admin created a new user with the User must change password on first login option selected, the user's status was mistakenly set to ACTIVE instead of PASSWORD_EXPIRED.
OKTA-502404
Users couldn’t temporarily sign in if their org subdomain was changed.
OKTA-502620
In Assign People, users who were removed from the permitted group were still available.
OKTA-503377
Users could use ADSSO to sign in to Okta when delegated authentication was disabled.
OKTA-503378
Users could continue to use the Okta IWA Web agent to sign in to Okta when delegated authentication was disabled.
OKTA-503715
The file sizes and hash values displayed on the Downloads page for the Linux RADIUS installers were incorrect.
OKTA-505960H
Admins who clicked the Resources > Help Center link from the Admin Console weren’t automatically signed into the Okta Help Center.
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Rivet: For configuration information, see How To Configure Okta SSO with Rivet.
SAML for the following Okta Verified applications:
-
Briq (OKTA-495218)
-
Uber for Business (OKTA-499842)
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-479211
The Settings page displayed an error message when users removed Okta Verify from the Extra Verification list, even though the removal was successful.
OKTA-487409
When the maximum number of trusted origins with iFrame embedding was reached, the limit wasn't displayed in the Admin Console.
OKTA-488510
Admins and developers couldn’t add a role=“presentation” attribute to the HTML table tag for custom email templates. This caused accessibility issues for screen readers.
OKTA-492197
The messages explaining the Registration Activation email template were incorrect.
OKTA-493959
Changes to unmapped attributes triggered a profile sync for downstream apps.
OKTA-494008
Long group descriptions weren’t displayed properly on the Edit resources to a standard role page.
OKTA-494490
Password health reports couldn't be generated if user sign-in data was missing.
OKTA-495068
For non-English locales, some buttons were misaligned.
OKTA-496486
Admins couldn't change the Okta domain field on an OIDC custom app instance's General tab. This field was read-only by design but caused confusion during custom domain creation.
OKTA-506310
The Authenticator sequencing field on the Okta Sign-On Policy - Add Rule page was mislabeled.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
iCloud (OKTA-500366)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Common Room: For configuration information, see OKTA SCIM Setup guide.
- Oracle Cloud Infrastructure IAM: For configuration information, see User Provisioning from Okta to Oracle Cloud Infrastructure IAM.
- Teampay: For configuration information, see Teampay documentation, here (you need Teampay credentials to view this doucmentation).
- Vault: For configuration information, see SSO setup OKTA - SCIM integrations.
SAML for the following Okta Verified application:
-
Agora (OKTA-500061)
Generally Available
Fixes
General Fixes
OKTA-415496
When the Okta Service was in safe mode or read-only mode, some users could sign in before completing MFA enrollment.
OKTA-484202
The Learn More button on the Agents page of the Admin Console didn't link to the documentation page.
OKTA-484374
The error message for the Create Users API contained unnecessary information.
OKTA-487243
When an admin expired user passwords in a bulk action, the Expiring all passwords pop-up message didn’t disappear after the action was successful.
OKTA-488909
Some factors didn't appear in the Sign-In Widget drop-down menu.
OKTA-494619
If an admin modified the credentials for an OAuth client that used a client secret or a JSON Web Key (JWK), the System Log didn’t record the event.
OKTA-497143
The Admin Roles Assignments report was called Custom Admin Roles report in the report email and CSV file.
OKTA-506333
Warning messages appeared on the Okta Sign-On Policy - Add Rule and Edit Rule page even though the relevant fields weren’t visible.
OKTA-506570
After admins disabled the Recent Activity Early Access feature, users who accessed the https://org-name.okta.com/enduser/recent-activity page received a 404 error instead of being redirected to the home page.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
eVerify (OKTA-502426)
-
Orion Advisor (OKTA-503428)
Applications
New Integrations
SAML for the following Okta Verified application:
-
Vault Platform (OKTA-502036)
Generally Available
Fixes
General Fixes
OKTA-490308
Read-only admins were unable to view IdP details.
OKTA-504696
Long role names weren’t displayed properly on the Administrators > Admins tab.
OKTA-504710
ThreatInsight reported sign-in attempts from IP addresses that weren’t blocked as a threat and generated unnecessary MFA challenges.
OKTA-505471
IdP routing rules didn’t work with the webfinger API.
OKTA-507188
When a create user API request failed due to non-compliant user credentials, the Add user to application membership events were listed incorrectly in the System Log.
OKTA-508174
The edit menus on the Branding page were misaligned.
OKTA-509203
The OIE Upgrade widget displayed an incorrect time after an admin used the Reschedule my upgrade link to select a new time/date.
Applications
Application Update
The Australian Access Federation application integration is removed from the OIN Catalog.
New Integrations
SAML for the following Okta Verified application:
-
Time By Ping (OKTA-493080)
May 2022
2022.05.0: Monthly Production release began deployment on May 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta AD agent, version 3.11.0
This version of the agent contains the following changes:
-
Increased minimum .NET version supported to 4.6.2. If the installer doesn't detect .NET 4.6.2 or higher, it won't be installed.
-
Security enhancements
-
Removed unsupported libraries
Okta ADFS plugin, version 1.7.10
This version of the plugin contains bug fixes and security enhancements. See Okta ADFS Plugin Version History.
Okta RADIUS agent, version 2.17.4
This version of the agent contains bug fixes and security enhancements. See Okta RADIUS Server Agent Version History.
Okta On-Prem MFA agent, version 1.5.0
This version of the agent contains security enhancements. See Okta On-Prem MFA Agent Version History.
Okta Provisioning agent, version 2.0.10
This release of the Okta Provisioning agent contains vulnerability fixes. See Okta Provisioning agent and SDK version history.
Jira Authenticator, version 3.1.8
This release contains bug fixes. See Okta Jira Authenticator Version History.
Okta Resource Center access
The Okta Resource Center is a collection of product tours, step-by-step guides, and announcements that helps you learn about new features and how to perform tasks within the Admin Console. You can launch the Okta Resource Center by clicking the blue icon from anywhere in the Admin Console. See Okta Resource Center.
Use Okta MFA for Azure AD Conditional Access and Windows Hello for Business Enrollment
You can use Okta MFA to:
- Satisfy Azure AD Conditional Access MFA requirements for your federated Office 365 app instance.
- Enroll end users into Windows Hello for Business.
See Use Okta MFA to satisfy Azure AD MFA requirements for Office 365.
Client secret rotation and key management
Rotating client secrets without service or application downtime is a challenge. Additionally, JSON Web Key management can be cumbersome. To make client secret rotation a seamless process and improve JWK management, you can now create overlapping client secrets and manage JWK key pairs in the Admin Console. You can also create JWK key pairs from the admin console without having to use an external tool. See Manage secrets and keys for OIDC apps.
Application SAML Certificates
Separate SAML signing certificates are now assigned when admins create new SAML applications or configure SAML-enabled OIN apps. Okta previously created SAML certificates that were scoped to an entire org. With this feature, SAML certificates are issued and scoped at the application level to provide more fine-grained control and a more secure solution overall. See Create SAML app integrations using AIW.
Okta API access with OAuth 2.0 for Org2Org
Previously, the Org2Org integration only supported token-based access to the Okta API. You can now configure the Org2Org integration to access the Okta API as an OAuth 2.0 client. This increases security by limiting the scope of access and providing a better mechanism to rotate credentials. See Integrate Okta Org2Org with Okta.
Enhancements
PKCE is a verification method for OIDC SPA and Native app integrations
The OIDC App Integration Wizard now identifies that PKCE is not a client authentication method. Instead, for SPA and Native apps, the AIW creates apps listing PKCE as a verification method. See Create OIDC app integrations using AIW.
Add agent permissions to custom admin roles
Custom admins can perform AD agent auto-updates for AD instances they have access to. They can also view the agents dashboard page to see the statuses of all agents associated with app instances they can manage. See Automatically update Okta agents.
Group count tooltip on the Admin Dashboard
On the Admin Dashboard, the Overview section now provides an "Includes only Okta sourced groups and excludes those sourced externally, such as AD groups" tooltip for the Groups count. The new tooltip helps you understand how your groups count is calculated. You can view the tooltip by hovering your cursor over the Groups count on the Overview section. See View your org at a glance.
Okta End-User Dashboard enhancements
-
Unread notifications are more visible to users.
-
The End-User Dashboard Preview function bar has moved to a separate dialog. See Preview an end user's dashboard.
-
The Last sign in link at the bottom of the Okta End-User Dashboard now includes the entire text of the message in the hyperlink.
-
The title of the copy password dialog in the Okta End-User Dashboard is more specific.
System Log enhancements for block zone events
-
The zone.make_blacklist event in the System Log now encompasses two actions: when an admin creates a blocked network zone, and when an admin marks an existing blocked zone as unblocked. Previously, this event was only recorded when a pre-existing network zone was converted into a block list.
-
The zone.remove_blacklist System Log event now encompasses two actions: when a network zone is converted into an allow list, and when an admin deletes a blocked zone. Previously, this event was only recorded when a pre-existing network zone was converted to an allow list.
System Log enhancement for network zone events
A network zone ID is now added as a target for all network zone events in the System Log.
Enhancements to ThreatInsight
ThreatInsight is improved to further protect rate limit consumption from malicious actors. Requests from actors with a high threat level continue to be logged and/or blocked depending on the org's configuration. Now, additional requests that seem malicious but have a lower threat level no longer count towards org rate limits.
OIN Catalog enhancements
Integrations in the OIN Catalog help end users address issues across a variety of industries. Okta has added the ability to filter integrations by industry to help both prospective and current Okta users identify the OIN integrations that best meet their needs. Additionally, the OIN Catalog interface has been updated with the following enhancements for improved navigation:
-
The search interface has been updated and popular search terms can now be selected.
-
Details pages for integrations have been updated for usability.
-
Navigation breadcrumbs have been added to the OIN Catalog.
-
Integrations can now be sorted alphabetically and by recently added.
OIN Catalog search functionality and filter updates
-
OIN Catalog search results now prioritize complete word matches from the search phrase.
-
Integrations in the OIN Catalog can now be filtered by RADIUS functionality.
OIN Manager enhancements
The OIN Manager now requires that ISV submissions for SCIM integrations confirm that the integration meets API response timing requirements. See Publish an OIN integration.
Auto-update task no longer requires pip
The device trust enrollment and renewal script on macOS no longer requires the pip package manager to install Python pyOpenSSL packages.
Early Access Features
New Features
New permissions for custom admin roles
Super admins can now assign these new permissions to their custom admin roles:
-
Manage authorization server
-
View authorization server
-
Manage customizations
-
View customizations
The authorization server permissions can be scoped to all or to a subset of the org’s authorization servers. With these new permissions, super admins can now create custom admin roles with more granular permissions for managing their org’s customizations and authorization servers. See About role permissions.
Additional resource and entitlements reports
Reports help your Okta org manage and track user access to resources, meet audit and compliance requirements, and monitor organizational security. The following reports are now available:
-
Group Membership report: Lists individual members of a group and how membership was granted.
-
User App Access report: Lists which users can access an application and how access was granted.
Fixes
General Fixes
OKTA-386570
If an LDAP interface bind request failed, subsequent searches failed with an internal server error instead of a permissions denied error.
OKTA-435855
Web and SPA app integrations created with an Authorization code or Interaction code grant type incorrectly returned an error if the Login Initiated By Either Okta or App option was selected.
OKTA-472350
Group push mapping for multiple Org2Org applications failed for some customers.
OKTA-476896
On the Administrators page, deactivated users with assigned admin roles were included in the Individually assigned count.
OKTA-477494
Some invalid EL expressions incorrectly passed validation.
OKTA-477634
Some users experienced delays when searching for an app on the Okta End-User Dashboard.
OKTA-481752
When users tried to enroll in Okta Verify, VoiceOver screen readers didn't highlight the mobile device type correctly or allow users to select a device. It also selected the iPhone option even though the Android option was also available.
OKTA-482435
When admins upgraded an app to SAML 2.0, the SAML 2.0 setup instructions used the org-scoped certificate instead of the app-scoped certificate.
OKTA-484366
Admins couldn’t use the objectGuid attribute as a unique identifier when integrating AD LDS LDAP servers with Okta.
OKTA-488233
Parallel JIT requests for the same username created duplicate users.
OKTA-488428
Some users lost the ability to reveal passwords for an app when the app drawer feature was enabled.
OKTA-488663
When Full Featured Code Editor was enabled, the full screen toggle on the error page code editor didn’t change to a minimize icon.
OKTA-489050
Sometimes an error message was displayed when admins viewed applications in the Admin Console.
OKTA-491164
Some admins weren’t assigned the Admin Console when they were added to a group with assigned admin roles.
OKTA-491264
Sometimes when a super admin deleted a custom admin role that contained email notifications, admins couldn’t update their email notification settings.
OKTA-495549
When groups were exposed in the LDAP interface directory information tree, some filters referencing the entryDn attribute returned the incorrect result code if the group wasn’t found.
OKTA-495598
AD-sourced users who reset their passwords in AD had to reset their passwords again when using IWA or ADSSO to sign in to Okta.
App Integration Fix
The following SWA app was not working correctly and is now fixed:
-
NDFR/SDU (OKTA-485335)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Cisco Umbrella User Management: For configuration information, see Cisco Umbrella - Provision Identities from Okta.
- Dialpad: For configuration information, see Dialpad + Okta | SCIM Instructions.
- Heap Analytics: For configuration information, see SCIM Provisioning: Okta.
SAML for the following Okta Verified applications
-
Common Room (OKTA-483683)
-
Datto Workplace (OKTA-487599)
-
Sounding Board (OKTA-489395)
Weekly Updates
Fixes
General Fixes
OKTA-385107
When User Profile Mappings were configured with invalid EL expressions, the validity check returned unwanted text.
OKTA-468575
Attempting to upload a new or replacement certificate to an existing RADIUS application resulted in an error.
OKTA-469428
Users could set their username as an answer to a security question if the case of at least one character was different.
OKTA-478259
When a super admin assigned an admin role to an ineligible group, the resulting error message was unclear.
OKTA-478844
Token endpoint events weren’t logged as expected by the System Log and Splunk.
OKTA-482807
Admins received a ${request.date} is required error when they tried to add a translation for the New Sign-On Notification email template.
OKTA-485981
Admins were able to save a Global Session Policy rule to deny sign-in attempts from specified zones even though no zones were selected.
OKTA-491554
The Client Secret UI didn’t render properly when users switched between authentication methods in an app instance.
OKTA-493632
A hyphen was incorrectly added to an app's tooltip when an end user hovered over the app on the End User Dashboard.
OKTA-496728
Client-side access tokens and ID tokens weren't revoked and cleared from an Okta domain’s localStorage when a user signed out from a custom OIDC application.
OKTA-498263H
The Activate/Deactivate button for Password Policy didn’t work.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
CUES (OKTA-486595)
-
GetFeedback (OKTA-488495)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Britive: For configuration information, see Integrating Okta for Provisioning.
- Uber for Business: For configuration information, see Configuring Okta Provisioning for Uber.
SAML for the following Okta Verified applications:
-
Britive (OKTA-487233)
-
OpsLevel (OKTA-484506)
-
Planview ID (OKTA-487235)
Generally Available
Sign-In Widget, version 6.3.2
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-477341
On some pages, the help text incorrectly showed Manage people and Manage apps instead of Assign people and Assign apps.
OKTA-489341
Customers couldn’t deactivate agents that hadn't completed the configuration process.
OKTA-494778
If a user tried to remove a read-only group from their profile page, an error resulted but no error message was shown.
OKTA-497940
When a custom OIDC app integration was created with the Login flow set to Redirect to app to initiate login, sign-in attempts returned an access denied error instead of directing the user to the correct Initiate login URI.
App Integration Fixes
The following SWA apps weren't working correctly and are now fixed:
-
Indeed (OKTA-489451)
-
Mutual of Omaha (OKTA-489714)
-
Telus Mobility (OKTA-489114)
Applications
Application Update:
-
Amazon AWS: The OIDC Client ID for CLI access property is now available in the default version of the Amazon AWS app in Preview orgs.
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Forma: For configuration information, see Forma Scim Integration Guide.
SAML for the following Okta Verified application:
-
eLearnPOSH (OKTA-491201)
Generally Available
Sign-In Widget, version 6.3.3
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-460513
Group function of the group rule didn't work properly when there was a target group involved.
OKTA-477637
Unique properties weren't deleted when the group they were associated with was deleted.
OKTA-483103
Users were still able to sign in through ADSSO when their Okta account was locked.
OKTA-488513
Links for app notes weren't properly converted in the new app settings drawer.
OKTA-489412
Office 365 users weren't deprovisioned after being deactivated in Okta.
OKTA-493308
Office 365 user provisioning tasks sometimes failed if certain properties were mapped to an empty string in Okta.
OKTA-499251
Admins couldn’t delete the Okta Verify authenticator from the list of authenticators even though it wasn’t required by any enrollment or authentication policies.
OKTA-500096H
On-premises AD agents weren’t automatically updated to the latest AD version by scheduled updates, and progress banners for manual updates displayed inaccurate agent versions.
OKTA-502045H
Some events didn’t display GeoLocation client data in the System Log.
Applications
Application Update
ModernHealth SCIM functionality has been deprecated and can no longer be used by customers. SAML is still supported.
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Dashworks.ai: For configuration information, see Configure Provisioning for Dashworks.ai.
- Forma: For configuration information, see Forma Scim Integration Guide.
- Parkable: For configuration information, see Parkable SCIM configuration.
April 2022
2022.04.0: Monthly Production release began deployment on April 4
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 6.2.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta On-Prem MFA Agent, version 1.4.9
This version of the agent contains security enhancements. See Okta On-Prem MFA Agent Version History.
Okta Browser Plugin, version 6.9.0 for all browsers
This version includes the following changes:
- Keyboard navigation didn't work properly when users attempted to switch to a new app list in the plugin popover window. Users were unable to close the plugin popover window with keyboard input.
- Version 6.8.0 of the plugin caused issues for some users when they attempted to sign in to an SWA app in an iframe.
Admin Experience Redesign toggle removed
The toggle that allowed super admins to switch between the Admin Experience Redesign and the old experience has been removed. All Okta admins now benefit from our restyled Okta Admin Dashboard, responsive navigation side bar, and modern look and feel.
Allow or deny custom clients in Office 365 sign-on policy
You can filter specific clients in an Office 365 app sign-on rule to allow or deny them access to Office 365 resources. This filter can be used to deny access to untrusted clients or to only allow trusted clients. See Allow or deny custom clients in Office 365 sign on policy
Improved AD group membership synchronization
The ADAppUser distinguished name field is now updated when a user is added to an Okta group and a matching group exists in AD. When an Okta provisioning request moves a user to a new organizational unit, the change is quickly duplicated in AD. This new functionality helps ensure the accuracy and integrity of AD group membership information. Manage Active Directory users and groups.
New App Drawer
The updated app settings panel on the Okta End-User Dashboard allows end users to see all app details in a single view without having to expand multiple sections. End users can quickly differentiate between SWA apps where they have set a username and password and SAML / OIDC apps that are admin-managed with no additional user settings. The updated app settings panel also provides accessibility improvements with better screen reader support and color contrast. See View the app settings page.
ShareFile REST OAuth
Admins can now upgrade to the latest version of our ShareFile integration. OAuth provides more secure authentication and will be now used for Provisioning and Imports. See Configure ShareFile OAuth and REST integration. This feature is made available to all orgs.
Enhancements
Federation Broker Mode UI improvements
The user interface prompts for Federation Broker Mode have been improved to provide more information about the feature. This feature can also be enabled through the OIDC app creation wizard. See Enable Federation Broker Mode.
Recent activity page link for end users
If Recent Activity is enabled, users can click Last sign in in the footer of the left navigation bar to go directly to the Recent Activity page.
Burst rate limits available on Rate Limit Dashboard
The Rate Limit Dashboard, available from the Admin Console, now includes data on burst limits in your Okta org, in addition to rate limit warnings and violations. The Violations dashboard was renamed Events to acknowledge the increase of scope, and includes the ability to filter on timeline as well as the type of event (warning, burst, and violation). Hovering over the burst rates in the graphs provides more detail and links to the system log for individual endpoint calls. The individual Usage graphs provide details on bursts for the individual API. See Rate limit dashboard and Burst rate limits.
New ThreatInsight enforcement action
If you configure ThreatInsight to log and enforce security based on the threat level detected, ThreatInsight can either limit or block authentication requests from suspicious IP addresses. For example, if a specific IP address is suspected of malicious activity but the threat level is considered low, authentication requests from the IP address are not denied access but might be subjected to a rate limit. See Configure Okta ThreatInsight.
New MFA help link
A new help link appears on Okta-hosted custom Sign-In Widgets. This link directs users to a page where they can learn more about the MFAn options available when they sign in. See Customize text on your sign-in page.
PIV IDP user profile mapping
You can now use idpuser.subjectUid in an Okta user profile when mapping IDP Username for Personal Identity Verification (PIV) IDPs. See Add a Smart Card identity provider.
Custom app logo preview
Admins can now preview a custom logo before applying it to an app. See Customize an application logo.
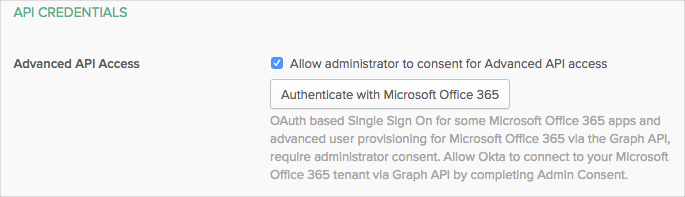
Updated error message for Microsoft Graph API
An error message for Microsoft Graph API has been updated to include more details and a possible workaround.
Debug logging for token exchange
The following fields have been added to the System Log for assistance in debugging OAuth2 token exchange events:
- requested_token_type
- subject_token_type
- actor_token_type
- resource
Updated SAML setup instructions
Setup instructions for SAML 2.0 apps now use per app SHA2 certificate during the app creation.
Change to the number of free SMS messages allowed
To balance growing costs of SMS usage while maintaining a commitment to developer and free trial orgs, Okta is changing the number of free SMS messages these orgs are allowed each month. Beginning April 4, 2022, orgs may send a maximum of 100 messages per month. For more information about this change, visit the Okta Developer Community.
Early Access Features
New Feature
Full Featured Code Editor for error pages
Full Featured Code Editor integrates Monaco code editing library into the Admin Console to make editing code for error pages more efficient and less reliant on documentation. Developers can write, test, and publish code faster with the better syntax highlighting, autocomplete, autosave, diff view, and a Revert changes button. See Customize the Okta-hosted error pages.
Enhancement
Fixes
General Fixes
OKTA-442031
Some Okta Mobile sign-in flows didn’t work for admins when the Okta Admin Console app required step-up authentication.
OKTA-460284
SAP Litmos imports failed with an unexpected error.
OKTA-472816
When app admins selected the Agents tab, the error message “Error rendering agents monitor table” appeared and no agents were listed.
OKTA-473180
Sometimes AssertionId for SAML1.1 assertions was poorly formatted.
OKTA-475767
Sometimes, in the Groups page Description column, an equals sign (=) replaced the forward slash ( / ) in LDAP-sourced group names.
OKTA-475773
Users could continue to use the Okta IWA Web agent to sign in to Okta when delegated authentication was disabled.
OKTA-475774
Users could use ADSSO to sign in to Okta when delegated authentication was disabled.
OKTA-478467
Admins who didn’t have permission to view the Agent monitors page received agent auto-update email notifications.
OKTA-479110
The sender email address on the Customizations > Emails page was inconsistent with the sender email address on individual templates.
OKTA-479701
Admins were shown events that were unrelated to their account in the Security Events section of the Recent Activity page.
OKTA-481319
An attribute for an app couldn't be re-added as a different type with the same variable name.
OKTA-482086
Some admins saw an error if they tried to run a report using resource sets created more than a year ago.
OKTA-482915
Admins were unable to remove unconfirmed imported users.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
MyFonts (OKTA-476809)
-
Quickbooks Time Tracker (OKTA-476695)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Snow Atlas SSO: For configuration information, see Okta as SSO provider.
- Transform: For configuration information, see Configuring Provisioning for Transform.
SAML for the following Okta Verified applications:
-
Atomic Console (OKTA-479344)
-
Intra-mart Accel Platform (OKTA-476864)
-
Mulesoft - Anypoint Platform (OKTA-461170)
-
OfficeTogether (OKTA-476827)
-
QTAKE Cloud (OKTA-480924)
OIDC for the following Okta Verified application:
-
ResoluteAI: For configuration information, see ResoluteAI: Setting up Okta.
Weekly Updates
Generally Available
Fixes
General Fixes
OKTA-482299
When a super admin removed all admin role assignments from a user, a time-out error sometimes appeared.
OKTA-482472
Admins with view permissions could see the Edit button in the User Account section of Customizations > Other.
OKTA-483335
When users signed in to Salesforce with the OAuth app, they weren't prompted to Allow Access. This only occurred if the Salesforce app was configured and the user already had an active session.
OKTA-483338
When users signed in to Google with the OAuth app, they weren't prompted to Allow Access. This only occurred if the Google app was configured and the user already had an active session.
OKTA-484416
In orgs that included OMM apps, Okta RADIUS agents weren’t able to service authentication requests after restart.
OKTA-484971
The Recent Activity section of the Okta End-User Dashboard didn't load properly for Internet Explorer users.
OKTA-484981
Due to a race condition and its exception handling, some users synced through imports received Access Forbidden errors for some applications.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
A Bead Store (OKTA-481911)
-
Adobe (OKTA-479001)
-
Adobe Stock (OKTA-483342)
-
American Express Business (OKTA-482556)
-
Mutual of Omaha (OKTA-481802)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
fax.plus: For configuration information, see SCIM - OKTA.
-
PubHive Navigator: For configuration information, see PubHive Navigator - Okta Configuration Guide.
-
Tailscale: For configuration information, see User & group provisioning for Okta.
SAML for the following Okta Verified applications:
-
CardinalOps (OKTA-482262)
-
Curator by InterWorks (OKTA-481345)
-
ModernLoop (OKTA-482260)
Generally Available
Fixes
General Fixes
OKTA-389310
The nonce length for WebAuthn challenges didn't have enough characters for the recommended level of entropy.
OKTA-461412
Reactivating some users reassigned them to deleted apps.
OKTA-473141
The Enable Provisioning link from group push led to a blank Provisioning tab.
OKTA-479938
Okta IWA agent Desktop Single Sign-on (DSSO) occasionally failed to authenticate a legitimate user when Okta was operating in safe or read-only mode.
OKTA-483618
Some app users lost static attribute mappings during a scheduled org-wide reconciliation.
OKTA-484245
Deleting a group sometimes resulted in 404 errors when admins searched for a policy.
OKTA-488985
The setup instructions for a manual WS-Federation configuration for Office 365 incorrectly displayed an SHA-2 certificate instead of the SHA-1 org-scoped certificate.
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Applauz: For configuration information, see Integrating Applauz with Okta.
SAML for the following Okta Verified applications:
-
Axiad Cloud (OKTA-465658)
-
BizLibrary (OKTA-438712)
-
Greene King (OKTA-480468)
-
SendGrid (OKTA-485059)
-
SourceWhale (OKTA-472980)
-
TestRigor (OKTA-486166)
Generally Available
Sign-In Widget, version 6.2.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-468644
When a super admin scoped a standard role to a group or app and then saved the resource set, any unsaved role assignments were removed from the Administrator assignment by role page.
OKTA-477295
When an admin deleted a user who was excluded in a group rule, the error message Failure to activate the rule appeared.
OKTA-483742
When admins deleted Okta AD agents, scheduled agent auto-updates continued and caused exception errors.
OKTA-484482
The iframeControlHideCatalog option didn't hide the Add Apps link when the Okta End-User Dashboard was embedded.
OKTA-485860
Admins whose custom admin role contained the Edit users' authenticator operations and Edit users' lifecycle states permissions could create API tokens.
OKTA-486474
Some imports hit a roadblock when import safeguards were turned off.
OKTA-487293
SAML inline hooks with an AuthNRequest sometimes failed.
OKTA-487334
The SWA copy password window on the Okta End-User dashboard contained UI issues for Internet Explorer users.
OKTA-487453
Deleted users were reindexed in Elasticsearch when admins deleted user data.
OKTA-488616
The doctype declaration wasn’t displayed in the default template for error pages code editor.
OKTA-493627
Because of a change to the cryptographic libraries in macOS 12.3 (Monterey), Okta Device Registration Task, version 1.3.2, failed to enroll or renew certificates.
OKTA-495596H
Admins couldn't customize the End-User Dashboard layout.
OKTA-495695H
A Classic Engine org couldn't upgrade to Identity Engine if its users were enrolled in Okta Mobile.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Carta (OKTA-486196)
-
Chartbeat (OKTA-485773)
-
Rippe and Kingston LMS (OKTA-482602)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
-
Axiad Cloud: For configuration information, see OKTA Axiad Cloud App Document.
-
Loadmill: For configuration information, see Loadmill Okta SSO integration.
-
Torq: For configuration information, see Configure SSO with Okta Open ID from App Catalog.
SAML for the following Okta Verified applications
-
Heap Analytics (OKTA-486230)
-
Secure Code Warrior (OKTA-476859)
March 2022
2022.03.0: Monthly Production release began deployment on March 7
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 6.1.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta SSO IWA Web App agent, version 1.15.0
This version of the agent contains:
-
Security enhancements.
-
Making .NET Framework 4.6.2 the minimal supported version. Earlier versions are automatically upgraded during agent installation.
-
Okta Military Cloud support.
Okta Active Directory Password Sync agent, version 1.5.0
This version of the agent includes:
-
Security enhancements.
-
Making .NET Framework 4.6.2 the minimal supported version. Earlier versions are automatically upgraded during agent installation.
-
Okta Military Cloud support.
See Okta Active Directory Password Sync Agent version history.
Okta AD agent, version 3.10.0
This version of the agent contains:
-
Okta Military Cloud support.
-
Bug fixes.
Okta LDAP agent, version 5.12.0
This version of the agent contains support for Okta Military Cloud. See Okta LDAP Agent version history.
Okta Provisioning agent, version 2.0.9
This release of the Okta Provisioning agent contains vulnerability fixes.
Event hooks for custom admin roles
Custom admin role events are now available for use as Event Hooks. This provides more security to admins by ensuring that they have the correct permission to perform tasks. See Event hooks.
Enhanced email macros for email template customization
Enhanced Email Macros updates the email templating engine to use Velocity Templating Language (VTL). This feature unlocks new syntax that provides enhanced conditional logic and access to all attributes in the Okta User Profile object. This allows developers and admins more customizations in their user-facing emails. See Customize email templates (Developer docs) and Customize an email template.
Enforce limit and log per client mode for OAuth 2.0 /authorize and /login/login.htm endpoints
The default client-based rate limit for OAuth 2.0 /authorize and /login/login.htm endpoints is now elevated to Enforce limit and log per client (recommended) mode. This means that if your org’s client-based rate limit was previously set to Do nothing or Log per client, the setting is changed to Enforce limit and log per client (recommended) mode.
Note that based on the email communication sent out on Feb 3, 2022 and Feb 25, 2022, these changes are not applicable to certain orgs. See Default client-based rate limit mode change.
New ThreatInsight enforcement option
ThreatInsight evaluates authentication requests to detect potentially malicious activity from IP addresses exhibiting suspicious behavior. If you enable the Log and enforce security based on threat level option, ThreatInsight can limit or block authentication requests from suspicious IP addresses based on the threat level detected. For example, if a specific IP address is suspected of malicious activity but the threat level is considered low, authentication requests from the IP address are not denied access but might be subjected to a rate limit. The rate limit helps ensure that requests from a suspicious IP address don't overload authentication services and affect legitimate traffic. However, if an IP address is suspected of malicious activity and the threat level detected is high, authentication requests from the IP address are blocked. See Configure Okta ThreatInsight.
Validation for custom message templates
If you customize the default SMS message template, the Admin Console checks the message to determine whether it contains GSM or non-GSM characters and enforces the GSM or non-GSM character limit before saving the message. This check ensures that you don't create custom SMS messages that exceed the GSM or non-GSM character limit for message segments.
If you change existing custom templates, the new restrictions are enforced if your messages contain non-GSM characters.
For more information about customizing SMS templates, see Configure and use telephony.
Custom Administrator Roles
The standard admin roles available today don’t always meet all the granular delegated administration requirements, which may result in admins having either more or less permissions than they need.
The Custom Administrator Roles feature allows super admins to:
-
Create admin assignments with granular roles, which include specific user, group, and application permissions.
-
Constrain these admin assignments to resource sets.
Use Custom Administrators Roles to:
-
Increase admin productivity.
-
Decentralize the span of access that any one admin has.
-
Grant autonomy to different business units for self-management.
Some important things to note:
-
The Administrators page has been updated with a new, more intuitive interface for managing roles and permissions. See About the Administrators page.
-
Your pre-existing roles are referred to as “standard roles”. The standard role functionality is the same as earlier but the UI is different. See Use standard roles.
-
You can continue using the pre-existing roles and your existing assignments remain the same.
-
You can also assign custom roles to users who have standard roles assigned.
See Custom administrator roles and Best practices for creating a custom role assignment.
System Log events for group app assignments
When an admin role is assigned to a group, the Okta Admin Console is now assigned to the group members much faster, and an Add assigned application to group event (group.application_assignment.add) appears in the System Log. This helps super admins monitor the event activity in their org. See System Log.
Immutable unique data types for Okta LDAP and AD agent actions
Immutable unique data types can now be used with Okta LDAP and AD agent actions. The use of immutable unique data types lets admins locate users when a username is updated, or when the user is moved to another OU. Immutable unique data type support reduces the time admins spend managing users and makes sure they can always locate user profiles after an update or when a username changes.
ShareFile REST OAuth
Admins can now upgrade to the latest version of our ShareFile integration. OAuth provides more secure authentication and will be now used for Provisioning and Imports. See Configure ShareFile OAuth and REST integration. This feature is currently available for new orgs only.
Group Push enhancements
Group Push now supports the ability to link to existing groups in NetSuite. You can centrally manage these apps in Okta. This is important because it allows you to set up and push Okta groups into NetSuite instead of recreating them in NetSuite. See About Group Push.
Support for additional social Identity Providers
Social login is a form of SSO that uses existing information from a service such as Facebook, Twitter, or Google to sign in, instead of creating a new account specifically for a third-party website. Social Identity Provider (IdP) popularity varies by industry and region. We're making it easy for Okta admins to add new IdPs with out-of-the-box integrations for GitHub, GitLab, Salesforce, and Amazon, with more to come. These integrations add to our existing social IdP catalog in the OIN, allowing users to quickly sign up or sign in to your application without entering their email or creating a new password. See External Identity Providers.
Risk and behavior evaluation
To improve the visibility of risk scoring and behavior detection, all sign-in requests are evaluated for risk factors and changes in behavior. Impacted orgs can view the results of the evaluation in the System Log. See Identity providers.
Enhancements
Copy button updates
In the app settings panel of the Okta End-User Dashboard, the copy buttons for the username and password fields are renamed Copy username and Copy password.
Group assignment priority
If a group rule results in a higher group app assignment priority on an existing app user, the user is now remapped to the higher priority group assignment.
Extensibility for notifications of group push failure circumstances
Group push failure event hooks now allow customers to monitor for failures that won't be retried and use them to trigger automations, such as execution of a flow in Okta Workflows.
Group push notification improvements
Group push failure notifications have been repurposed and improved to provide better error descriptions for customers.
Early Access Features
New Features
Group search in the Admin Console
Admins can now use the Search bar to quickly find groups, in addition to users and apps. See Admin Console search.
Automatically update public keys in the Admin Console
Using private_key_jwt as your app's client authentication method requires that you upload public keys to Okta and then use the private keys to sign the assertion. Then, you must update the client configuration each time you rotate the key pairs. This is time-consuming and error-prone. To seamlessly use key pairs and rotate them frequently, you can now configure private_key_jwt client authentication in the Admin Console for OAuth clients by specifying the URI where you store your public keys. See Manage secrets and keys for OIDC apps.
User accounts report
Use this report to view users with accounts in Okta and their profile information. It helps you manage and track user access to resources, meet audit and compliance requirements, and monitor the security of your org. The report is located in the Entitlements and Access section of the Reports page. See User Accounts report
Enhancements
Incremental Imports for the Org2Org app
Okta now supports incremental imports for the Org2Org app. Incremental imports improve performance by only importing users that were created, updated, or deleted since your last import. See Okta Org2Org.
Fixes
General Fixes
OKTA-404202
All users imported that are not confirmed will be removed using Clear Unconfirmed Users tool.
OKTA-447833
Admins couldn’t set up a custom domain URL with a top-level domain of .inc.
OKTA-455641
The Edit Assignment page for the Box app didn’t handle non-alphabetical characters properly.
OKTA-457771
Some users imported from Active Directory were missing apps assigned through group assignment.
OKTA-460013
Okta will schedule group reconciliation for any assigned user that is operationalized.
OKTA-461371
VoiceOver screen readers didn’t read the descriptions for the options to send Okta Verify activation links using SMS and email.
OKTA-466022
Admins whose custom role contained the Run imports permission couldn’t view their org’s LDAP integrations.
OKTA-468707
The System Log didn't display ThreatSuspected=false for authentication events when no threat evaluation was done.
OKTA-469843
Sign-In Widget polling didn't resume when the network became available.
OKTA-470096
Group membership changes didn’t automatically activate Group Push.
OKTA-471299
When ThreatInsight evaluated sign-in attempts for unknown users, the threat level was incorrectly displayed as threatLevel=UNKNOWN in the System Log.
OKTA-471605H
In SP-initiated flows, users' sessions ended when they closed the browser even if they selected Keep me signed in.
OKTA-471605H
In SP-initiated flows, users' sessions ended when they closed the browser even if they selected Keep me signed in.
OKTA-472304H
Group push for some customers resulted in a timeout error after one minute.
OKTA-473512
When the Custom Admin Roles feature was enabled, super admins were called Super Organization Administrators.
App Integration Fixes
The following SWA app were not working correctly and are now fixed
- Asana (OKTA-467306)
- Dashlane Business (OKTA-466333)
- Guardian Insurance (OKTA-470966)
- Loop11 (OKTA-471181)
- Names & Faces (OKTA-468537)
- Nord Layer (OKTA-469771)
- Optum Health Financial (OKTA-465956)
- QuickBooks (OKTA-467864)
- Twitter (OKTA-470889)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- ArmorCode: For configuration information, see Armorcode - How to configure Armorcode app on Okta.
- Cognism: For configuration information, see Okta SCIM Configuration setup.
- Indi: For configuration information, see Okta SSO integration with Indi.
- strongDM: For configuration information, see Set up an App in Okta for User & Group Provisioning.
- Trusona: For configuration information, see Integrating Trusona and Okta SCIM.
SAML for the following Okta Verified applications:
-
Happeo (OKTA-461895)
-
ScreenMeet (OKTA-466613)
-
Shortcut (OKTA-461249)
-
Wonderwerk (OKTA-454149)
-
Zero Networks (OKTA-472331)
OIDC for the following Okta Verified applications:
- Artificial: For configuration information, see Using Okta to log in to Artificial.
- strongDM: For configuration information, see SSO with Okta.
Weekly Updates
Generally Available
Sign-In Widget, version 6.1.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-374857
When admins searched for groups in the new LDAP interface, results weren’t returned if the search query contained all lowercase characters.
OKTA-375035
The error message “The operation is not allowed” appeared to users who entered their new password during self-service password recovery even though the new password was saved and could be used for authentication.
OKTA-440514
Sensitive attributes were exposed when Identity Provider routing rules contained Boolean expressions.
OKTA-452618
Admins whose custom role contained the Edit users' lifecycle states permission but not the View users and their details permission could view the Profile tab on the user page.
OKTA-457354
Updating an access policy rule through the Admin Console sometimes resulted in a browser error. This occurred if the rule was created using the Authorization Server API without an include array in the User Condition object.
OKTA-459720
Some apps that require admin configuration appeared on the App Catalog page of the End-User Dashboard.
OKTA-464002
Admins with two active Okta orgs linked together by the same company name were unable to sign in to the OIN Manager portal.
OKTA-470268
If tasks were pending, users experienced slow or unresponsive web browsers after navigating to the Tasks page of the End-User Dashboard.
OKTA-470378
Confirmation messages shown when app assignments were removed or when groups were removed from app instances were inconsistent and unclear.
OKTA-470384
Screen readers didn't properly read text in the App Settings page the when user set focus on Username or Password fields.
OKTA-470541
Sometimes importing from the SuccessFactors app integration failed after timing out.
OKTA-470701
Keyboard navigation and screen readers occasionally lost focus while in the App Settings page of the End-User Dashboard.
OKTA-471079
Users with iOS 15.3.1 devices weren’t able to change their passwords in Okta Mobile 6.29.1-14.
OKTA-472593
When the Custom Admin Roles feature was enabled, the Administrator assignment by admin, Edit resources to a standard role, and Edit resource set pages didn’t display group details for imported AD/LDAP groups.
OKTA-473963
VoiceOver screen readers didn’t read the descriptions for the options in drop-down lists on Okta Verify.
OKTA-474143
A new public key was displayed in the UI despite the new key generation operation being canceled.
OKTA-476453
Displaying the App Catalog in List View on the End-User Dashboard caused UI errors in Internet Explorer browsers.
OKTA-477943H
Admins couldn’t change the version of the Sign-In Widget for custom domains.
OKTA-478421H
When AD/LDAP users were imported into groups with assigned admin roles, the resulting admin role updates were delayed, and the Grant user privilege event didn’t appear in the System Log.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Data.ai (OKTA-472317)
-
Google Play (OKTA-470657)
-
Zenefit (OKTA-472199)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
SmartHR: For configuration information, see Okta user provisioning integration with SCIM.
-
Wonderverk: For configuration information, see Wonderverk's Okta documentation.
OIDC for the following Okta Verified applications:
-
ePMX: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
-
Marvin: For configuration information, see Okta Configuration Guide.
-
Pretaa: For configuration information, see Pretaa Integration with Okta- OpenID Connect.
Generally Available
Sign-In Widget, version 6.1.2
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-411070
Some administrator roles were incorrectly given access to Okta Management device and setting endpoints.
OKTA-414109
Admins who only had the View application and their details permission could see the Self Service section on the Application > Assignments tab.
OKTA-417477
Making valid changes to the device_sso or online_access scopes in the Edit Scope dialog incorrectly returned an error message.
OKTA-441233
When a super admin saved the email notification settings for a role without making any changes, the settings weren’t restored to their default values for existing admins with that role.
OKTA-457226
Some text strings on the Multifactor page weren't translated.
OKTA-463551
Lengthy app names weren't fully listed in the search index of the Okta End-User Dashboard.
OKTA-464002
Sometimes a user was unable to access app integrations in OIN Manager when the account that submitted the integration had been disabled.
OKTA-464217
Onboarding guides were still shown to new users after admins disabled the feature in Customizations > Other > Display Options.
OKTA-466304
Messages weren't descriptive for errors that occurred during SCIM integration for custom SAML apps.
OKTA-469449
Admins couldn’t change their custom sign-in page, and the wrong error message was displayed.
OKTA-469451
Send test email failed with a 500 error for some email templates.
OKTA-471670
The ThreatSuspected field was missing in the user.session.start event for Radius sign-in requests.
OKTA-473387
Variables didn’t work in the subject lines of some email templates.
OKTA-476019
Unsaved edits appeared in the read-only view of Identity Provider routing rules.
OKTA-478605
During OAuth app creation, EC public keys weren't recognized and couldn't be validated.
OKTA-479004
Some Preview orgs experienced Office 365 import failures with the error message, “An error occurred while creating the Azure Active Directory Graph API client.”
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
MyAtt (OKTA-473277)
-
Nationwide Financial (OKTA-473149)
Applications
New Integrations
New SCIM Integration application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Qapita QapMap: For configuration information, see How to configure SSO between Qapita and Okta.
SAML for the following Okta Verified application:
-
Ashby (OKTA-470597)
Generally Available
Fixes
General Fixes
OKTA-409838
When the Custom Admin Roles feature was enabled, admins without the View users and their details permission could see the Profile tab on the user page.
OKTA-448751
The Admin Dashboard sometimes displayed an inaccurate number of user groups.
OKTA-448946
Updating a Salesforce app username created a new user instead of pushing a profile update.
OKTA-456820
If users authenticated with a custom IdP factor, their client details weren't captured in the System Log.
OKTA-461147
The Remember My Last Used Factor functionality didn’t display all available factors, and the factor that was automatically selected hadn't been previously used.
OKTA-469698
The Office 365 Tasks app didn't take users to the Tasks tab of the Outlook web app.
OKTA-472294
When using Branding or Custom Domain features, admins who clicked a button multiple times received an error even though the action completed successfully.
OKTA-472467
Screen readers couldn't tell whether Password input field was hidden or revealed.
OKTA-474997
The Registration - Email Verification email template didn't support translated text.
OKTA-479799
When the Custom Admin Roles feature was enabled, some admins couldn’t view groups on the Administrators > Admins tab.
OKTA-479983
The Client Secret page didn't render the UI correctly for orgs with the Client Secrets Management feature enabled.
OKTA-480151
Some Expression Language variables still appeared in automated emails.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Angie's List (OKTA-477233)
-
FortiCloud (OKTA-478241)
-
Lutron (OKTA-476161)
-
Tableau (OKTA-471013)
Applications
New Integrations
New SCIM Integration applications:
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
EZOfficeinventory: For configuration information, see Implement User Provisioning via SCIM with EZOfficeInventory and Okta.
-
Qapita QapMap: For configuration information, see How to configure SSO between Qapita and Okta.
SAML for the following Okta Verified application:
-
Perdoo (OKTA-472102)
OIDC for the following Okta Verified application:
-
Jira SAML SSO by miniOrange: For configuration information, see OAuth/OpenID Single Sign On (SSO) into Jira using Okta.
February 2022
2022.02.0: Monthly Production release began deployment on February 7
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 6.0.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta AD agent, version 3.9.0
This version of the agent contains bug fixes. See Okta Active Directory agent version history.
Okta LDAP agent, version 5.11.0
This version of the agent contains:
-
Support for Proxy Authorization Control version 2 (2.16.840.1.113730.3.4.18). Users who are required to change their password after it is reset by an admin are no longer prompted twice for their password when accessing the End-User Dashboard. This new functionality is available only with LDAP services that support Proxy Authorization Control version 2. To enable this feature, contact Okta Support.
-
Internal improvements and bug fixes.
Burst rate limits for authentication and authorization flows
Burst rate limits provide peace of mind by ensuring an unplanned spike doesn't negatively affect the end user's experience. See Burst rate limits.
OIN catalog replaces categories with use cases
Integrations in the OIN catalog address multiple use cases beyond SSO, such as LCM, social login, and identity proofing. Okta helps prospective and current orgs identify the OIN integrations that best meet their needs by highlighting the use cases that the integrations address and the functionality that the integrations use. This information is provided on both the OIN Catalog landing page and the integration details page. Okta also provides calls to action to help users immediately find value with these integrations across the Okta product platform. Use cases and functionalities replace app categories and filters, which were previously used to sort integrations. This feature will be gradually made available to all orgs.
Provisioning to Office 365 now requires Admin Consent for Microsoft Graph API
Admins are now required to grant consent for Okta to call Microsoft Graph API to enable provisioning features for Office 365 app instances. This change prepares Okta to migrate provisioning operations to Microsoft Graph API in 2022, which will improve performance and reliability for Office 365 provisioning operations. It also enhances security for Okta customers by limiting Okta's permissions in the customer's Azure Active Directory to only those operations which are required for provisioning. Okta customers who previously configured provisioning to Office 365 are required to grant admin consent in order to make any changes to their existing provisioning settings. See Provide Microsoft admin consent for Okta.
Configure a custom error page
You can customize the text and the look and feel of error pages using an embedded HTML editor. When used together with a custom URL domain (required) and a custom Okta-hosted sign-in page, this feature offers a fully customized error page. For details, see Configure a custom error page.
Configure a custom Okta-hosted sign-in page
You can customize the text and the look and feel of the Okta-hosted sign-in page using form controls and an embedded HTML editor. When used together with a custom URL domain (required) and a custom Okta-hosted error page, this feature offers a fully customized end user sign-in experience hosted by Okta. For details, see Configure a custom Okta-hosted sign-in page.
Custom domains with Okta-managed certificates
When you customize an Okta URL domain, your Okta-hosted pages are branded with your own URL. Okta-managed certificates automatically renew through a Let’s Encrypt integration, a free certificate authority. Okta-managed certificate renewals lower customer developer maintenance costs and reduce the high risk of a site outage when certificates expire. See Customize the Okta URL domain.
Secondary email option for LDAP-sourced users
Admins can now enable a secondary email option for LDAP-sourced users in new orgs. When the secondary email option is enabled, LDAP-sourced users who haven’t previously provided a secondary email are now prompted to provide it on the Okta Welcome page. The prompt continues to appear until a secondary email is provided.
A secondary email helps reduce support calls by providing LDAP-sourced users with another option to recover their password when their primary email is unavailable. See Configure optional user account fields.
Password expiry for AD LDS-sourced users
Admins can now expire the passwords of AD Lightweight Directory Services-sourced users. Forcing users to change their password when they next sign in to Okta keeps passwords updated and enhances org security. See AD LDS LDAP integration reference.
Improved password status accuracy for LDAP-sourced users
The status of LDAP-sourced users is now accurately displayed on the user’s profile page. Previously, the user status incorrectly displayed Password Reset when a password was active. This update reduces the time admins need to spend monitoring and managing user passwords. See About user account status.
New features for HealthInsight
- Administrators can now enable end user email notifications when an end user changes or resets their password. See General Security and HealthInsight.
- HealthInsight now includes a recommendation for admins to enable Password Changed email notifications if the notification isn't yet enabled for the org. See Password changed notification for end users.
- HealthInsight now displays a suspicious sign-in count within the recommendation that users enable ThreatInsight in block mode. See Okta ThreatInsight
Risk scoring improvements
Risk scoring has been improved to detect suspicious sign-in attempts based on additional IP signals. See Risk scoring.
Enhancements
Custom URL domain certificate expiration reminders
Email reminders for custom URL domain certificate expiration are now sent to super admins and org admins only.
OIN Manager enhancements
Users can now select a maximum of five app categories for ISV submissions. If an app category isn't selected, the app is placed in the all integrations category. See App information.
Error message and logging improvements
An error message for group push mapping to alert that a group is not active or not found has been added. Error logging has also been improved.
Email and SMS notification renamed
The New Device Notification email and SMS messages have been renamed New sign-on notification.
New behavior for Custom User Profile link
When users click the Custom User Profile link, the page now opens in a new browser tab or window.
New System Log event when user signs in
Admins now see the user.authentication.verify event in the System Log. This event is triggered when a user successfully signs in to their account. This feature is made available to all orgs.
App notes
App notes written by an admin are now displayed for users who hover over the app on the Okta End-User Dashboard.
Masking for eight digit phone numbers
The masking algorithm now reveals fewer digits for shorter phone numbers. For example, if the phone number has eight digits, the first five digits are masked and the final three digits are visible.
Early Access Features
New Features
Additional Okta username formats for LDAP-sourced users
Three additional Okta username formats are now available for LDAP-sourced users. In addition to the existing options, admins can now select Employee Number, Common Name, and Choose from schema to form the Okta username. These new options allow admins to use both delegated authentication and Just-In-Time (JIT) provisioning with LDAP directory services. With these new provisioning options, it is now easier for admins to integrate their LDAP servers with Okta. See Configure LDAP integration settings.
Okta Epic Hyperspace agent, version 1.3.2
This EA version of the agent contains security enhancements. See Okta Hyperspace Agent Version History.
Fixes
General Fixes
OKTA-294735
In the email template editor, the subject was translated to the admin’s display language but the rest of the content remained in English.
OKTA-383630
Macros didn’t render correctly in the subject field for Send test email and Email preview.
OKTA-419837
The warning message for custom code editors referred to Theme builder instead of Branding.
OKTA-419847
On-Prem MFA API tokens contained scopes beyond what was required for agent operation.
OKTA-423419
Some email templates returned errors if Velocity variables weren’t enclosed in brackets. This occurred for orgs with Enhanced Email Macros enabled.
OKTA-430327
Repeatedly assigning and unassigning a user to a group that provisions applications converted that user from a group assignment to an individual assignment.
OKTA-433751
End users received errors when accessing SWA apps through the Okta End-User Dashboard if their app passwords contained ampersands.
OKTA-436486
Some orgs couldn’t save email templates containing Velocity variables. This occurred for orgs with Enhanced Email Macros enabled.
OKTA-442296
Some end users received a 400 error after signing in to the Okta End-User Dashboard.
OKTA-443420
The Admin Console became unresponsive if admins performed a search with an unlimited number of characters on the People page.
OKTA-443777
Admins couldn’t use the objectGuid attribute as a unique identifier when integrating AD LDS LDAP servers with Okta.
OKTA-451206
When admins enabled LDAP real-time synchronization, the system.agent.ad.realtimesync event erroneously appeared in the System Log.
OKTA-455372
If the information required to evaluate behavior was not available, the System Log displayed BAD_REQUEST for rules that included behavior detection.
OKTA-451159
Org2Org attempts to push users sometimes resulted in java.net.SocketTimeoutException: Read timed out errors.
OKTA-455199
Error messages weren’t shown to users who signed in to orgs using passwordless authorization and an Identity Provider from IP addresses outside of the allowed network zone.
OKTA-456690
The View logs option on the People page was available to all users.
OKTA-459571
In the admin console, the status of RADIUS agents randomly changed from Operational to Disrupted.
OKTA-460366
On Security > Networks > Add IP Zone, proxy IP addresses weren't explicitly identified as trusted proxy IP addresses.
OKTA-461015
Event information was missing from the Report Suspicious Activity page after users changed their password in the Sign-In Widget.
OKTA-461198
When the Custom Admin Roles feature was enabled, read-only admins could see the Assign to People, Assign to Groups, and Edit User buttons on the Applications page.
OKTA-461686
The error message DownloadedObjectsProcessJob: null id in com.okta.monolith.platform.groups.db.dto.MembershipOktaGroup appeared after a full import of LDAP attributes.
OKTA-462025
Admins who refreshed a page in the custom URL domain wizard weren’t returned to the correct step.
OKTA-462114
The ${user.login} variable appeared in default email templates.
OKTA-462312
No warning message appeared when an attribute was saved as both sensitive and required in the Profile Editor.
OKTA-462807
Some orgs couldn't provision out-of-sync users.
OKTA-463388
Some valid Philippines phone numbers were identified as invalid and rejected when users tried to enroll in SMS authentication.
OKTA-467470H
When the Okta Browser Plugin was installed, applications opened from the new End-User Dashboard into pop-up windows instead of regular browser tabs. This occurred for Internet Explorer users only.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
- AppSplit (OKTA-462294)
- Auth0 (OKTA-456042)
- Dockerhub (OKTA-463515)
- FinServ (OKTA-463959)
- LoansPQ (OKTA-462410)
- MeridianLink LoansPQ (OKTA-460940)
- New Relic (OKTA-464710)
- ProtonMail (OKTA-463545)
- Salto Keys (OKTA-464469)
- WePay (OKTA-462296)
- Wikispaces (OKTA-462300)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- BrightHire: For configuration information, see Okta SCIM Integration Guide.
- CertCentral: For configuration information, see CertCentral integration with Okta-OpenID.
- Compliance Genie: For configuration information, see Compliance Genie: Setting up SSO with OKTA.
- UniPrint InfinityCloud: For configuration information, see Configuring Okta for InfinityCloud via App Catalog.
- VidCruiter: For configuration information, see Configuring SCIM with Okta.
SAML for the following Okta Verified applications:
-
Compliance Genie (OKTA-456834)
-
SecureCodeWarrior (OKTA-455728)
OIDC for the following Okta Verified application:
- Atomic Console: For configuration information, see Atomic Console OKTA OIN App Configuration Guide.
Weekly Updates
Fixes
General Fixes
OKTA-422710
When the Custom Admin Roles feature was enabled, admins who didn’t have the Manage groups permission could view the Actions drop-down menu on the Groups > Rules tab.
OKTA-439826
Windows Server 2008 R2 was identified as a supported operating system on the Set Up Active Directory page.
OKTA-447818
Admins could remove users from a group on the Group Profile page but couldn't remove the group membership on the User Profile page.
OKTA-452937
Admins experienced page scrolling errors when approving requests for Salesforce apps.
OKTA-455572
End users were unable to see their existing password when editing sign-in information for an SWA app.
OKTA-456429
On the App Access Locked page, the contact your administrator link was broken.
OKTA-458310
The Groups page displayed the Admin roles tab for non-AD/LDAP groups. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-460374
When a default application was configured for the Sign-In Widget, no banner indicated to users which app they were signing in to.
OKTA-460647
UI elements for app settings on the Okta End-User Dashboard were inconsistent for admins and end users.
OKTA-460719
The Add Log Stream and Add Identity Provider pages were improperly rendered in Internet Explorer 11.
OKTA-461134
Tooltips didn't wrap properly on the Okta End-User Dashboard.
OKTA-461604
The Username field was missing for admins in the self-service app request workflow.
OKTA-462025
Admins who refreshed a page in the custom URL domain wizard weren’t returned to the correct step.
OKTA-462639
Some international SMS messages had the wrong country code displayed in the System Log.
OKTA-463346
In Internet Explorer 11, apps on the Okta End-User Dashboard displayed incorrect titles.
OKTA-463905
Super admins didn't receive an error if they saved the Administrator assignment by resource set or Administrator assignment by role page without selecting a resource set/role. This occurred for orgs with the Custom Admin Role feature enabled.
OKTA-465050
The app settings drawer incorrectly displayed a password field for SAML apps.
OKTA-466901
Custom attributes identified as cn (Common Name) were automatically mapped as username in Okta.
OKTA-471193H
Group push from Okta to Office 365 didn’t work.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
- Schwab Retirement Plan Center (OKTA-464739)
- SquareSpace (OKTA-466252)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Happeo: For configuration information, see Configuring Okta Provisioning for Happeo.
-
Orca Security: For configuration information, see Okta SSO Configuration SCIM 2.0.
-
Perimeter 81: For configuration information, see Okta (SCIM).
-
Rolebot: For configuration information, see How to configure Single Sign On (OIDC) with Okta.
-
SafeGuard Cyber: For configuration information, see SafeGuard Cyber Okta Configuration Guide.
SAML for the following Okta Verified application:
- CloudAlly (OKTA-453596)
Generally Available
Sign-In Widget, version 6.0.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-449722
There was a spelling error in the Help link (Optional) section of the Settings > Account > End User Information page.
OKTA-456339
Admins whose custom admin role contained the Run imports permission couldn't click Back to Applications on the Applications page.
OKTA-456831
For self-service registered users, verification emails sent using the Resend Verification Email button didn’t appear in the System Log.
OKTA-461740
VoiceOver screen readers read the wrong description for the Okta Verify enrollment QR code.
OKTA-463803
Group push didn't work for orgs configured with a required custom attribute.
OKTA-464251
End users incorrectly received prompts to sign in again when nearing the end of their session lifetime.
OKTA-465665
End users saw a blank page if they signed in to the Okta End-User Dashboard with a custom domain that ended with com.com.
OKTA-466301
The following issues occurred in the OIN App Catalog on Internet Explorer 11:
- The app details page wasn’t shown when an app was selected from the Browse Integration Catalog search results.
- App details pages didn’t render correctly.
- Users weren't able to use the up and down arrow keys to navigate search results.
OKTA-466425
On the Okta End-User Dashboard, the app setting drawer's Reveal password wasn't accessible by keyboard commands.
OKTA-468607
When the Custom Admin Roles feature was enabled, newly added admins didn’t always appear on the Administrators page.
OKTA-469099
When orgs enabled both Branding and Custom Domain URL, the default domain displayed customized error pages.
January 2022
2022.01.0: Monthly Production release began deployment on January 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 5.16.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Okta Provisioning agent, version 2.0.6
This version of the agent contains security fixes. See Okta Provisioning agent and SDK version history
Okta On-Prem MFA agent, version 1.4.8
This version of the agent contains security fixes. See Okta On-Prem MFA Agent Version History.
Okta Active Directory agent, version 3.8.0
This version of the agent contains:
- Agent auto-update support
- Improved logging functionality to assist with issue resolution
- Bug fixes
Okta RADIUS Server agent, version 2.17.2
This version of the agent contains security fixes. See Okta RADIUS Server Agent Version History.
Delivery status of SMS messages in the System Log
Administrators can now view the delivery status for SMS messages in the System Log. For information about the new event type, see Configure and use telephony.
Feature name change: New Sign-On Notification
The New Device Notification functionality is renamed to New Sign-On Notification in the Admin Dashboard, the email notification title, and elsewhere. It refers to the email notification a user receives when there’s a sign-in event from an unrecognized device.
New permissions for custom admin roles
The following new permissions can now be assigned to a custom admin role:
-
Activate users
-
Deactivate users
-
Suspend users
-
Unsuspend user
-
Delete users
-
Unlock users
-
Clear user sessions
-
Reset users' authenticators
-
Reset users' passwords
-
Set users' temporary password
-
Run imports.
The new permissions give super admins more granular control over their delegated org permissions. See About role permissions.
Editable Sign-in URL
End users can edit sign-in URLs for their apps on the App Settings page.
Service Principal Name functionality improvement
New Service Principal Name (SPN) functionality allows Agentless Desktop Single Sign-on (ADSSO) authentication to continue without interruption when an SPN is updated. A service account and an SPN are required for ADSSO Kerberos authentication. With this change, you can now update the SPN frequently as an additional security precaution. See Create a service account and configure a Service Principal Name.
OAuth Dynamic Issuer option
An authorization server’s issuer URL can be used to validate whether tokens are issued by the correct authorization server. You can configure the issuer URL to be either the Okta subdomain (such as company.okta.com) or a custom domain (such as sso.company.com). See Create the Authorization Server.
When there are applications that use Okta’s subdomain and other applications that use the custom domain, the issuer validation breaks because the value is hard-coded to one domain or the other.
With Dynamic Issuer Mode, the issuer value in minted tokens is dynamically updated based on the URL that is used to initiate the original authorize request.
For example, if the authorize request is https://sso.company.com/api/v1/authorize, the issuer value is https://sso.company.com.
Dynamic Issuer Mode helps with:
-
Split deployment use cases
-
Migration use cases when customers migrate from the Okta domain to a custom domain
-
Support with multiple custom domains
Rate limit dashboard
The new rate limit dashboard helps you investigate the cause of rate limit warnings and violations. You can also use it to view historical data and top consumers by their IP address.
This helps you:
-
Isolate outliers
-
Prevent issues in response to alerts
-
Find and address the root cause of rate limit violations
You can access the dashboard using the link provided in the rate limit violation event in the System Log. See Rate limit dashboard.
You can also open the dashboard in the Admin Console to monitor API usage over a period of time, change rate limit settings, and customize the warning threshold. See Rate limit monitoring.
Error response updated for malicious IP address sign-in requests
If you block suspicious traffic and ThreatInsight detects that a sign-in request comes from a malicious IP address, Okta automatically denies the user access to the organization. The user receives an error in response to the request. From the user’s perspective, the blocked request can’t be identified as the result of ThreatInsight having identified the IP address as malicious.
Make Okta the source for Group Push groups
Admins can now make Okta the profile source for all members of a group that is used for Group Push. When this feature is enabled, integrated apps can't change app group memberships. This functionality allows admins to maintain the accuracy of app group membership and prevents changes to group membership after a push. See Manage Group Push.
Password change notifications for LDAP-sourced users
Password change email notifications may now be sent to LDAP-sourced users.
LDAP-sourced users secondary email prompt on first sign in
Admins now have the option to prompt LDAP-sourced users for a secondary email when they sign in to Okta for the first time. When a secondary email is provided, password reset and activation notifications are sent to the user’s primary and secondary email addresses. Duplicating these notifications increases the likelihood they are seen by users and reduces support requests. See Configure optional user account fields.
Directory Debugger for Okta AD and LDAP agents
Admins can now enable the Directory Debugger to provide Okta Support with access to Okta AD and LDAP agent diagnostic data. This new diagnostic and troubleshooting tool accelerates issue resolution by eliminating delays collecting data and improves communication between orgs and Okta. See Enable the Directories Debugger.
Enhancements
Improved SIW error messages
The Sign-In Widget now has improved JIT error messages.
OIN Manager enhancements
The OIN Manager includes the following updates for ISV submissions:
-
It clarifies that OID and SAML integrations must support multi-tenancy.
-
It clarifies that only one OIDC mode can be selected for an OID integration.
-
It allows the format ${app.domain}/redirect_url for URIs.
-
It no longer allows ISV submissions for the Social Login and Log Streaming categories. See OIN App Integration Catalog.
-
It allows the use of app instance properties when configuring single logout (SLO) for SAML app integrations.
-
It requires that ISV submissions specify one or more use cases. Existing submissions may need to be updated to change from previous categories to the new use cases.
Updated interstitial page animation
A new animation is displayed on a loading page when users sign in to an app from Okta.
SHA type displayed for SAML certificates
SHA type is now displayed for SAML certificates in the Admin Console.
Fixes
General Fixes
OKTA-379478
The Medallia Mobile application dataAccess attribute wasn't automatically updated after changes were made to a user's group membership.
OKTA-412445
The SAML assertion sent by Okta to AWS exceeded the max character length supported by AWS (100,000 characters).
OKTA-420065
Launch on sign-in apps on the Okta End-User Dashboard launched multiple times after the user signed in.
OKTA-444924
An incorrect error message appeared when admins searched for groups and the Expression Language query included invalid attributes.
OKTA-447750
Users signing in to OIDC apps through Okta-hosted Sign-In Widgets on custom authorization servers received an access error message before they could provide their password.
OKTA-448006
Some branded pages used an org’s previously uploaded logo rather than their new theme logo.
OKTA-453672
When admins created custom language and country code attributes in the Profile Editor, the format property wasn’t updated and submitted.
OKTA-454206
Some admins without super admin permissions could view a link to the Admin role assignments report. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-456082
Mitigation of CSV Injection wasn't provided in all Okta-generated CSV reports.
OKTA-456084H
Admins received a 500 Internal Server Error when attempting to delete a YubiKey in blocked status.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Bendigo Bank (OKTA-454211)
-
EdgeCast (OKTA-453148)
-
Maxwell Health (OKTA-454213)
-
My T-Mobile (OKTA-455732)
-
Redis (OKTA-454218)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Javelo: For configuration information, see Okta SCIM - Javelo App.
- Workstream: For configuration information, see Configuring SCIM for Workstream.
SAML for the following Okta Verified application:
-
Regal Voice (OKTA-448791)
Weekly Updates
Fixes
General Fixes
OKTA-427502
After a Smart Card IDP was deactivated, the PIV button continued to appear when users signed in.
OKTA-443601
In the User Accounts section of the Customizations page, the incorrect term User Identity Master was used instead of User Identity Source.
OKTA-445110
Admins couldn’t search for suspended users on the Groups > People page.
OKTA-450647
When the Custom Admin Roles feature was enabled, the Admin role assignments report included deactivated admins.
OKTA-454965
Admins couldn’t unsubscribe from Okta AD agent auto-update email notifications because the Agent auto-update notifications: AD agent checkbox wasn’t available in the System notifications area of the Settings page.
OKTA-458760H
When the New Social Identity Provider integrations feature was enabled, IdP profiles weren't always saved and the Redirect Domain field wasn't available.
OKTA-461273H
Some Smartcard/PIV users were unable to sign in due to inaccessible Certificate Revocation Lists (CRL).
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Circulation (OKTA-456780)
-
CWT (OKTA-455733)
-
Key Bank (OKTA-455731)
-
MyFitnessPal (OKTA-455735)
-
Shutterstock (OKTA-456777)
-
The Hartford EBC (OKTA-454220)
-
TimeLog (OKTA-457372)
-
Verizon Wireless Business (OKTA-455729)
-
Xfinity (OKTA-457369)
Applications
New Integrations
SAML for the following Okta Verified applications:
-
Blingby Live (OKTA-455293)
-
BrightHire (OKTA-456906)
-
Jones (OKTA-453595)
-
TrackJS (OKTA-456630)
Generally Available
Sign-In Widget, version 5.16.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-288443
Links from an expired session didn't redirect users to the Okta End-User Dashboard when they signed in.
OKTA-332414
The All apps filter in the Okta End-User Dashboard catalog was incorrectly translated.
OKTA-412803
An incorrect warning message containing a user’s ID appeared when OpenLDAP-sourced users attempted to sign in to Okta.
OKTA-414419
Admins with the View application and their details permission could view the Push Status drop-down menu and the Push Groups, Refresh App Groups, and Bulk Edit buttons on the Application > Push Groups tab. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-416052
The Sort Apps button and its drop-down menu were covered by the left navigation bar on mobile devices.
OKTA-419846
RADIUS agent API tokens contained scopes beyond what was required for agent operation.
OKTA-433758
Some users created in AD and imported into Okta were missing external IDs when automatically assigned to apps.
OKTA-441218
When the Custom Admin Roles feature was enabled, third-party admins could view their admin email notification settings.
OKTA-443467
Admins were unable to sign in to the Admin Console if they had first signed in with a non-admin user account.
OKTA-446224, OKTA-455268
New admins weren’t always provisioned for Salesforce Help Center.
OKTA-446449
Memberships to Salesforce Public Groups were removed from Salesforce when group memberships were updated in Okta.
OKTA-447069
Some users were unable to access their bookmark apps after migrating to the new Okta End-User Dashboard.
OKTA-447114
Okta sent MFA reset email notifications even though the factor deactivation didn’t take effect.
OKTA-447813
Sometimes, admins were unable to remove apps from the Create a resource set page. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-454385
Password change email notifications were incorrectly sent to end users in orgs with URLs containing api/v1/user.
OKTA-457233
The default zone name for legacy IP zones was hardcoded in English and displayed in the Admin Console as a text string that could not be localized.
OKTA-457592
On the Admin assignment by admin and Admin assignment by role pages, an error sometimes appeared when the admin removed an existing standard role from the assignment and replaced it with another role. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-458302
When admins enabled LDAP interface app group support, the Directory Information Tree (DIT) included app instances that users couldn’t access.
OKTA-460597
When the Custom Admin Roles and CSV Directory features were enabled, admins with the Manage applications permission couldn’t access the Directory Integrations page.
OKTA-460636
When the Custom Admin Roles and Application Entitlement Policy features were enabled, admins with the Edit application's user assignments permission couldn’t assign apps to users.
OKTA-460767
Admins could click Finish multiple times after adding or updating a custom domain certificate. This resulted in duplicate API calls.
OKTA-460908
Some lengthy app names caused UI errors on the Okta End-User Dashboard.
OKTA-462342
When a user copied their username in the app drawer, they were incorrectly notified that the app's password was copied to the clipboard.
OKTA-466809H
A script error occurred when users with an embedded Internet Explorer browser attempted to sign in to Okta.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Allegra (OKTA-449137)
-
Clio (OKTA-458076)
-
DocuSign (OKTA-456094)
-
Expedia (OKTA-455734)
-
FreeAgent (OKTA-454216)
-
Go to Connect (OKTA-454638)
-
QuickBooks (OKTA-457705)
-
SuccessFactors (OKTA-449132)
-
TeamPassword (OKTA-456778)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Almanac: For configuration information, see Almanac - Okta SCIM Configuration.
- Dashworks: For configuration information, see Dashworks Integration with Okta- OpenID Connect.
- Offishall: For configuration information, see User provisioning with Okta.
- Opal: For configuration information, see Setting up Opal's Okta SCIM Integration.
- Xakia: For configuration information, see Okta App SCIM Configuration Guide.
SAML for the following Okta Verified applications:
-
Almanac (OKTA-456412)
-
Observe (OKTA-455308)
-
ReviewInc (OKTA-457711)
-
Spherexx (OKTA-453592)
-
Transform (OKTA-457712)
-
VidCruiter (OKTA-461233)
OIDC for the following Okta Verified applications:
- Atomic Dashboard: For configuration information, see Atomic Dashboard OKTA OIN App Configuration Guide.
- Fellow.app: For configuration information, see Fellow Okta Integration Guide (SSO).
December 2021
2021.12.0: Monthly Production release began deployment on December 13
* Features may not be available in all Okta Product SKUs.
Sign-In Widget, version 5.14.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Choose client types for Office 365 sign-on policy
When creating app sign-on policy rules to manage access to Office 365 apps, you can now specify client types such as web browser, modern auth, or Exchange ActiveSync. This allows you to apply Office 365 sign-on policies to granular use-cases. See Office 365 sign-on rules options.
Branding now available in the Admin Console
This UI release provides admins and developers with an Admin Console UI to upload brand assets to customize their Okta-hosted pages. The Customizations tab in the Admin Console is also now moved to a top-level menu item in the left-hand navigation, and Branding-related controls have all been moved under it. The Settings > Appearance tab has also been removed, and functionality moved under the Customizations tab for ease of use. See Branding.
Admin Experience Redesign toggle removed
The toggle that allowed super admins to switch between the Admin Experience Redesign and the old experience has been removed. All Okta admins now benefit from our restyled Okta Admin Dashboard, responsive navigation side bar, and modern look and feel. If you need more time to adapt to the new user experience, you can revert to the old experience by contacting Okta Support until April 2022.
Upload Logo for org deprecated
The Upload Logo for Org endpoint (api/v1/org/logo) is deprecated. Use the Upload Theme Logo (/api/v1/brands/${brandId}/themes/${themeId}/logo) endpoint instead.
Policy rule events now eligible for event hooks
The following policy rule events are now eligible for event hooks:
-
policy.rule.activate
-
policy.rule.delete
See Event hooks.
Salesforce Federated ID REST OAuth
Admins can now upgrade to the latest version of our Salesforce Federated ID integration. OAuth provides enhanced security and is now used for Provisioning and Imports authentication. This feature is currently available for new orgs only. See Configure OAuth and REST integration.
Localized SAML setup instructions
To achieve its objective of becoming the leader in identity and access management, Okta is actively expanding to numerous countries. To better serve this diverse market, Okta has begun localizing its customer-facing products to improve usability. To facilitate this process for SAML setup instructions, Okta will automatically provide the instructions in the user's chosen display language, if a translated version is available. Currently, a limited number of SAML setup instructions are now available in Japanese. See .
Okta MFA Credential Provider for Windows, version 1.3.5
This version of the agent contains:
-
Security enhancements
-
Internal fixes
See Okta MFA Credential Provider for Windows Version History.
Okta On-Prem MFA agent, version 1.4.6
This version of the agent contains updates for certain security vulnerabilities.
Okta RADIUS Server agent, version 2.17.0
This version of the agent contains updates for certain security vulnerabilities.
Okta Browser Plugin, version 6.6.0 for all browsers
This version includes minor bug fixes and improvements. See Okta Browser Plugin version history.
Enhancements
Org setting to disable device token binding
For compatibility purposes, orgs can now disable device binding. Device binding ensures that state tokens are used only by the actor who initiated the authentication flow. See General Security.
SharePoint (On-Premises) instructions updated
SharePoint (On-Premises) instructions have been updated to remove SharePoint 2010 from the Downloads page.
Early Access Features
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-372730
Org admins couldn't add social Identity Providers.
OKTA-393284
UI errors occurred when users hovered over a locked app on the Okta End-User Dashboard.
OKTA-416595
The spinner stayed visible after a sign-in error in some orgs with security image disabled.
OKTA-430797
Password push events were not showing in the System Log when multiple domains were federated in the same Office 365 app.
OKTA-433327
App usernames weren't updated automatically on non-provisioning enabled apps.
OKTA-438888
The Client drop-down menu wasn't displayed properly when admins added a new access policy for Authorization Servers using Internet Explorer.
OKTA-439104
Random users were unassigned from applications when imported and assigned by group.
OKTA-439327
Applying admin-managed tabs to end users occasionally completed much later, after the changes were initially made.
OKTA-441168
Users were directed to the wrong step of the Log Stream creation wizard when they clicked a link to create a specific type of Log Stream.
OKTA-443459
Some users who accessed the Okta End-User Dashboard saw a blank screen.
OKTA-449400
The text field for an app’s alternative name was missing from the app drawer.
OKTA-450158
In orgs with a custom domain URL and self-service registration enabled, users who went directly to the registration link saw a 404 error.
OKTA-450543
Users weren't prompted to correct their device’s time if their device was behind the server’s time by more than five minutes or ahead by more than 65 minutes.
OKTA-450896
The search bar on the Okta End-User Dashboard produced results that were inaccessible for screen readers.
OKTA-450927
Two scrollbars were displayed for mobile users.
OKTA-457787H
Apps on the Okta End User Dashboard on Internet Explorer opened as a pop-up window instead of a new tab.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Amplitude (OKTA-449138)
-
Australian Financial Review (OKTA-450189)
-
Boxed (OKTA-449140)
-
Google Tag Manager (OKTA-448703)
-
HireFire (OKTA-448711)
-
Instacart Canada (OKTA-442943)
-
International SOS Assistance (OKTA-447156)
-
LinkedIn (OKTA-443788)
-
Mural (OKTA-443063)
-
Payroll Relief (OKTA-447159)
-
Safari Online Learning (OKTA-448707)
-
The Hartford EBC (OKTA-448956)
-
Twitter (OKTA-448961)
-
XpertHR (OKTA-449721)
Applications
Application Update
The Jive application integration is rebranded as Go To Connect.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- ContractS CLM: For configuration information, see ContractS CLM SCIM provisioning configuration with Okta.
- MURAL: For configuration information, see Configuring Provisioning for MURAL.
SAML for the following Okta Verified applications:
-
Chatwork (OKTA-449761)
-
ContractS CLM (OKTA-446453)
-
Elate (OKTA-448860)
-
WAN-Sign (OKTA-448922)
OIDC for the following Okta Verified applications:
- Ashby: For configuration information, see Configure an OIDC connection to Ashby.
-
Drata: For configuration information, see Connecting Okta to Drata (Note: you need to sign in to Drata to view this documentation).
-
TripleBlind: For configuration information, see Okta Configuration Guide.
Weekly Updates
Generally Available
Sign-In Widget, version 5.14.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-328461
The footer in some email templates contained an incorrect link to Okta.
OKTA-410446
DebugData in the System Log didn’t include ClientSecret information.
OKTA-428685
Errors occurred when admins attempted to assign DocuSign to users.
OKTA-440608
Some admins couldn't view groups that were assigned to an app, even though their custom role had permission to view them.
OKTA-447471
Duplicate reactivation requests for the Org2Org app caused 400 errors in the System Log.
OKTA-447916
Admins received the wrong error message when they attempted to delete a custom domain.
OKTA-448321
When the Custom Admin Roles feature was enabled, groups with “#” in the group name couldn’t be assigned to a role.
OKTA-449880
When Enhanced Email Macros was enabled, the text in some default email templates was incorrect.
OKTA-451075
Security fix for the Okta Provisioning Agent. For this fix, download Okta Provisioning Agent version 2.0.6.
OKTA-451868
In new developer orgs, admins weren’t provisioned for Salesforce Help.
OKTA-452041
Attempts to sign in to the Admin Console using Safari on an iOS device were prevented by the popup blocker.
OKTA-452099
The QR verification form in the device authentication flow wasn’t pre-filled with the user code.
OKTA-454767H
Some app labels were missing in the redesigned OIN App Catalog.
App Integration Fix
The following SWA app was not working correctly and is now fixed:
-
GoDaddy (OKTA-449141)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Keepabl: For configuration information, see Set up SSO with Okta.
-
ValidSoft VoiceID: For configuration information, see the Validsoft VoiceID Provisioning Configuration Guide.
Fixes
General Fixes
OKTA-441896
Group attribute statements added in a SAML 2.0 integration app (AIW) didn’t appear in the Preview the SAML Assertion section.
OKTA-444246
Some SAML doc links in the Admin Console didn’t work.
OKTA-447069
End-users encountered a 403 error when accessing a bookmark app after being migrated to the new Okta End-User Dashboard.
OKTA-447885
When adding a custom domain, admins received the wrong error message if they left the Domain field blank.
OKTA-448560
New users received an activation email with Velocity macros instead of their name. This occurred if the org’s profile enrollment policy didn’t require first and last names.
OKTA-448936
The Create a new resource set page couldn't display groups with & in the group name. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-448940
The Edit resources to a standard role page displayed an error when admins searched for a group. This occurred for orgs with the Custom Admin Roles feature enabled.
OKTA-451345
The Velocity parsing engine failed when email templates contained a variable that was followed by (.
OKTA-452680
Application usage reports created asynchronously for specific groups included users that didn’t belong to the groups selected for the reports.
OKTA-454197
On the Add domain page, the Next, Remove, and Verify DNS buttons were clickable while the addition was in progress.
OKTA-456383H
CSV imports failed when using Okta Provisioning Agent, version 2.0.6. For this fix, download Okta Provisioning Agent, version 2.0.7.
OKTA-458089H
Some Netsuite imports into Okta failed with the following error failure: A SOAP message cannot contain entity references because it must not have a DTD.
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Regal Voice: For configuration information, see Okta SCIM: Manage Regal Voice users from your Okta organization.
SAML for the following Okta Verified applications:
-
Imprivata Privileged Access Management (OKTA-450222)
-
Lucca (OKTA-450219)
-
PowerDMS (OKTA-454504)
-
Rybbon (OKTA-451438)
November 2021
2021.11.0: Monthly Production release began deployment on November 8
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 5.13.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta LDAP agent, version 5.10.0
This version of the agent contains:
-
Range attribute retrieval for group membership attributes (full support will be available in a future release)
-
Real-time synchronization for user profiles, groups, and group memberships (full support will be available in a future release)
-
Expired password reset support for the eDirectory LDAP service (Okta Identity Engine)
-
Bug fixes
Okta RADIUS Server agent, version 2.16.0
This version of the agent contains:
-
Government Community Cloud support
-
Internal and security fixes
Okta MFA Credential Provider for Windows, version 1.3.4
This version of the agent contains:
-
Government Community Cloud support
-
Internal fixes
See Okta MFA Credential Provider for Windows Version History.
Okta ADFS Plugin, version 1.7.9
This version of the agent contains:
-
Government Community Cloud support
-
Internal fixes
Okta On-Prem MFA agent, version 1.4.5
This version of the agent contains:
-
Government Community Cloud support
-
Internal fixes
Okta Browser Plugin, version 6.5.0 for all browsers
Internet Explorer local storage size for the Okta Browser Plugin has been increased. See Okta Browser Plugin version history.
Brands API support for auto-detecting contrast colors
The Brands API Theme object properties primaryColorContrastHex and secondaryColorContrastHex automatically optimize the contrast between font color and the background or button color. The auto-detection feature can be disabled by updating either property value with an accepted contrast hex value. See Brands.
New default selection for MFA enrollment policies
For MFA enrollment policy rules, the Any application that supports MFA enrollment option is now selected by default. See Configure an MFA enrollment policy.
New error page macros for themed templates
Custom error page templates include new macros to customize the URL (href) in addition to the button text for themed templates. See Use macros.
Custom domain SSL certification expiration warnings
To prevent service disruptions, Okta now sends admins a warning email 30, 15, and 7 days before their custom domain’s SSL certificate expires. If no action is taken, an expiration notice is sent when the certificate expires.
Token-based SSO between native apps
Single Sign-On (SSO) between browser-based web applications is achieved by leveraging shared cookies. Unlike web applications, native applications can’t use web cookies. With Native SSO, Okta offers a token-based approach to achieve SSO between native applications.
Native SSO allows you to protect native OpenID Connect applications, such as desktop apps and mobile apps, and achieve SSO and Single Logout (SLO) between these applications. See Configure SSO for native apps.
Wildcards for OAuth redirect subdomains
Developers can now use the Apps API to set multiple redirect URI subdomains with a single parameter using the asterisk * wildcard. This feature provides convenience and flexibility in cases where subdomains vary by only a few characters. For example: https://subdomain*.example.com/oidc/redirect may be used to represent subdomain1, subdomain2, and subdomain3.
Sort applications on End-User Dashboard
End users can now sort applications alphabetically or by last added on the new Okta End-User Dashboard.
Asynchronous Application Reports
When enabled, this feature turns the generation of the Application Usage and the Application Password Health reports into an asynchronous process. Okta generates a report with the results and sends an email to the admin containing a download link for the CSV file. This enhancement is ideal for orgs with large amounts of user activity, as the generated reports can cover a greater range without timing out. See Application Usage report and App Password Health report.
Risk scoring improvements
Risk scoring improvements are being slowly deployed to all organizations. See Risk scoring.
Password expiry warning for LDAP group password policies
You can now configure an LDAP group password policy to provide users with a password expiry warning when their LDAP password is about to expire. Providing a password expiry warning in advance prevents users from losing access to shared resources and reduces the likelihood that you’ll need to reset passwords. See Configure a password policy.
Create and manage group profiles
You now have the flexibility to manage the default profile for Okta groups in the Profile Editor. This new functionality simplifies group management and lets you quickly add, edit, or remove custom profile attributes to groups. See Work with profiles and attributes. This feature will be gradually made available to all orgs.
Litmos supports Advanced Custom Attributes
We’ve enriched our Litmos integration to support Advanced Custom Attributes for the user profile. This allows you to add fields into the Okta user profile. See Litmos Provisioning Guide.
AES-GCM encryption support for SAML assertions
To secure SAML assertions from attacks and to adopt a stronger security mechanism, Okta now supports AES128-GCM and AES256-GCM encryptions modes in addition to AES-128 and AES-256 for SAML applications.
Enhancements
New System Log events for custom domain setup
The following events are added to the System Log:
system.custom_url_domain.cert_renew 3
system.custom_url_domain.delete
Existing events now include CustomDomainCertificateSourceType.
OIN App Catalog user interface changes
The following text has been updated for consistency:
-
FILTERS is now Capabilities
-
Apps is now All Integrations
-
Featured is now Featured Integrations
-
OpenID Connect is now OIDC
-
Secure Web Authentication is now SWA
Hash marks added to hex code fields
On the Branding page, hash marks are automatically added to the hex codes in the Primary color and Secondary color fields.
Event Hooks daily limit
The maximum allowable daily limit of Event Hooks for all orgs has increased from 100,000 to 200,000. A higher daily allocation of Event Hooks reduces the likelihood orgs will exceed their daily limits. See Workflows system limits.
Improved Branding preview
Branding previews now display correct text colors.
Sign-In Widget button colors standardized
To comply with accessibility contrast ratios, the default variant colors for buttons on Okta sign-in and error page have been standardized to use the Okta design system.
Early Access Features
New Features
Log Streaming
While Okta captures and stores its System Log events, many organizations use third-party systems to monitor, aggregate, and act on event data.
Log Streaming enables Okta admins to more easily and securely send System Log events to a specified system such as Amazon Eventbridge in real time with simple, pre-built connectors. They can easily scale without worrying about rate limits, and no admin API token is required. See Log Streaming.
Enhancements
Manage email notifications for custom admin roles
Super admins can configure the system notifications and Okta communications for custom admin roles. Configuring the email notifications helps ensure admins receive all of the communications that are relevant to their role. See Configure email notifications for an admin role.
Fixes
General Fixes
OKTA-243898
When multiple factors were required in the MFA for Active Directory Federation Services (ADFS) enrollment flow, only a single factor was enrolled before the user was allowed to sign in.
OKTA-409578
After the Microsoft ADFS (MFA) app Sign-On setting was changed to MFA as a Service, the app no longer appeared on the end-user home page.
OKTA-411306
Users weren't instructed to sign out and then sign in again when the mobile device management (MDM) remediation screen appeared during Intune setup.
OKTA-412100
The Identity Provider factor name wasn’t updated when the admin changed the Identity Provider name.
OKTA-412459
The YubiKey report didn’t list all YubiKeys when the user sorted the entries by Status.
OKTA-417499
When the Remove Group endpoint was called with an invalid group profile attribute, the group wasn't removed.
OKTA-418219
Sometimes when a super admin assigned several standard roles to a group at a time, some of those roles didn’t appear on the Groups page.
OKTA-422328
Screen Readers didn't interact properly with the search bar on the Okta End-User Dashboard.
OKTA-422586
On the Suspicious Activity User Report, the Login field was incorrectly labeled Email and didn't display the primary email address of the user who reported the activity.
OKTA-425318
Admins weren't able to use the Expression Language to compare a user's status to a string.
OKTA-428079
Admins weren’t able to add multiple custom attributes to an app on the Okta End-User Dashboard.
OKTA-430675
When the super org admin role was revoked from a user, the resulting email notification didn’t include the org name or URL.
OKTA-432942
Selecting the ellipses on an app card on the Okta End-User Dashboard incorrectly opened the app instead of accessing its settings.
OKTA-434233
Users attempting to enroll an MFA factor while signing in to an OIDC app received server error messages and couldn’t complete the enrollment.
OKTA-440551
The Sort Apps function didn't work when the Okta End-User Dashboard was displayed in Dutch, Brazilian, Portugese, Simplified Chinese, or Traditional Chinese.
OKTA-440618
For some orgs with Branding enabled, the theme was reset after an admin’s role changed.
OKTA-440816
Sometimes, when deactivated LDAP-sourced users attempted to sign in to Okta, an incorrect message appeared.
OKTA-440695
Some users saw an error when signing in to the new End-User Dashboard or OIDC apps for the first time.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Cloze (OKTA-440336)
Applications
Application Updates
-
The configuration guide for the Vable SCIM integration is updated: Okta Users Provisioning For The Vable Platform.
-
The American Express Work was a duplicate integration and has been removed from the OIN Catalog. Customers should use the American Express - Work integration.
New Integrations
New SCIM Integration Application:
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Blue Ocean Brain: For configuration information, see Configuring Provisioning for BlueOceanBrain.
OIDC for the following Okta Verified applications:
-
AIB Inc: For configuration information, see How do I use Okta to log in to AIB?
-
FortifyData: For configuration information, see FortifyData documentation here (you'll need a FortifyData account).
-
Sonarapp: For configuration information, see Okta Single Sign-On configuration guide.
-
WordPress OAuth Single Sign-On (SSO) by miniOrange: For configuration information, see Okta Single Sign-On (SSO) WordPress OAuth| Okta SSO Login.
Weekly Updates
Early Access
Okta Provisioning agent, version 2.0.4
This release of the Okta Provisioning agent contains vulnerability fixes. See Okta Provisioning agent and SDK version history.
Fixes
General Fixes
OKTA-429081
When an admin deleted an app with Federation Broker Mode enabled, users could continue to sign in to the app.
OKTA-429782
Sometimes when the app group membership for a user was deactivated, any role assignments that were revoked from that user still appeared on the Administrators page.
OKTA-429868
API tokens for group admins didn't have the role displayed in the Security > API > Token section.
OKTA-431083
An error occurred when admins attempted to upload an IPA file to the Upload Mobile App page.
OKTA-434925
Email address change notifications were incorrectly sent to the new email address and not the old email address.
OKTA-435431
On the new Okta End-User Dashboard, end users were still able to request apps after an admin had disabled the app request feature.
OKTA-436761
End users were incorrectly prompted to copy password credentials to their clipboard when accessing SWA apps that were shared between users with admin-controlled passwords.
OKTA-439047
Sometimes, the System Log displayed Grant user privilege success events for admins when there were no changes to their privileges.
OKTA-439196
The Okta End-User Dashboard displayed a blank screen to users whose clocks were incorrectly set.
OKTA-441222
When a super admin changed the role notification settings for an admin, some third-party admins with that role were included in the notification subscription.
OKTA-441434
The View Setup Instructions link was broken on the Add Identity Provider page.
OKTA-444012
Branding features weren’t visible in the navigation menu of the legacy Admin Console.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Alibaba Cloud (Aliyun) (OKTA-439430)
-
Apple Store for Business (OKTA-439233)
-
ID90 Travel (OKTA-435212)
-
MessageBird (NL) (OKTA-440295)
-
Screen Leap (OKTA-440292)
-
TD Ameritrade (OKTA-436146)
Applications
New Integrations
SAML for the following Okta Verified applications:
-
Agencyzoom (OKTA-436124)
-
Altruistiq (OKTA-440339)
-
Auvik (OKTA-435860)
-
Ceresa (OKTA-437597)
-
Clumio (OKTA-440285)
-
Workstream (OKTA-441160)
SWA for the following Okta Verified application:
-
Greene King (OKTA-441236)
OIDC for the following Okta Verified application:
-
Luma Brighter Learning: For configuration information, see Okta/Luma SSO.
Fixes
General Fixes
OKTA-419946
When an admin assigned an app to a user, the Edit User Assignments window appeared too small.
OKTA-428017
When the Custom Admin Roles feature was enabled and an admin searched for a group to assign to a role, the list of groups didn’t display their respective app logos.
OKTA-436016
In orgs with deleted groups, admins couldn't run the Admin role assignments report.
OKTA-438793
On the Admin Dashboard, the Overview section displayed an incorrect Updated at time between 12:00 AM and 1:00 AM.
OKTA-441161
When a super admin edited the User Account customization settings, an error occurred after they verified their password.
OKTA-443995
End users were unable to add org-managed apps to the Okta End-User Dashboard after admins had enabled self-service.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
HelpSpot Userscape (OKTA-440296)
-
Instacart Canada (OKTA-442946)
-
Moffi (OKTA-442915)
Applications
New Integrations
SAML for the following Okta Verified applications:
-
Autodesk (OKTA-425911)
-
YesWeHack (OKTA-443624)
OIDC for the following Okta Verified applications:
- Autodesk: For configuration information, see Okta SCIM Setup.
- Clearwage: For configuration information, see Single Sign-On configuration guide.
- Moqups: For configuration information, see Set up SCIM for Okta.
- Profit.co: For configuration information, see Configure OKTA User Provisioning for Profit.co.
Generally Available
Sign-In Widget, version 5.13.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-373558
App approval forms incorrectly listed deactivation options and available licenses for Google Workspace.
OKTA-414394
On the Applications page, some admins with a custom role could view the buttons for actions that they didn’t have permission to perform.
OKTA-414517
Users who self-registered but hadn’t completed activation were deactivated if they attempted to sign in with a Google IdP.
OKTA-424842
On the Select assignments to convert page, eligible users didn't appear in the user list.
OKTA-424897
When using the Self-Service Registration feature, users with slower internet connections could click Register again while the account was being created.
OKTA-431945
Sometimes when a third-party admin role was assigned though the public API, the admin's status didn't change in the Okta Help Center.
OKTA-433439
Push Profile updates sometimes failed due to a missing Effective Date value.
OKTA-434556
In Try Okta Free orgs, the Days left in your trial banner didn’t always display the correct number of days.
OKTA-434789
When Veeva Vault was provisioned, the authentication rate limit was incorrectly applied to bulk operations.
OKTA-435148
Unique attributes were retained when admins used a CSV file to import user attributes and the import was unsuccessful.
OKTA-438657
When a custom admin role had the View application and their details permission, admins with that role couldn’t access OIDC applications.
OKTA-441490
When previously deactivated users with expired passwords were reactivated and allowed to sign in using their Personal Identity Verification (PIV) cards, they were required to reset their passwords.
OKTA-442991
When the Custom admin roles feature was enabled, the Administrator assignment by admin and Administrator assignment by role pages displayed the Edit button for admin roles that couldn’t be constrained to a resource.
OKTA-443494
When MFA for Active Directory Federation Services (ADFS) was in OIDC mode and two users were assigned the same custom name, an incorrect error was returned.
OKTA-445826
The help link was incorrect for Settings > Customization > Configure a custom URL domain.
OKTA-453056H
When accessing reports, report admins received a 403 error.
OKTA-453535H
An older library for the RSA and RADIUS agents caused potential security issues in certain situations.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
American Funds Advisor Client Login (OKTA-442550)
-
Bank of America CashPro (OKTA-444481)
-
M&T Bank - Commercial Services (OKTA-447154)
-
Nimble (OKTA-444703)
-
The Trade Desk (OKTA-445291)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Aerofiler: For configuration information, see AEROFILER SINGLE-SIGN ON GUIDE.
-
Clearwage: For configuration information, see Single Sign-On configuration guide.
-
NeuraLegion: For configuration information, see Enabling SCIM Provisioning between Okta and NeuraLegion.
-
ValueCloud by DecisionLink: For configuration information, see Configuring Okta Provisioning for ValueCloud.
SAML for the following Okta Verified applications:
-
ParkOffice (OKTA-445142)
-
SecZetta (OKTA-446467)
October 2021
2021.10.0: Monthly Production release began deployment on October 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 5.12.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Okta Active Directory agent, version 3.7.0
This version of the agent contains:
-
Government Community Cloud support
-
Improved logging functionality to assist with issue resolution
-
Bug fixes
Okta LDAP agent, version 5.9.0
This version of the agent contains:
-
Government Community Cloud support
Okta SSO IWA Web App agent, version 1.14.0
This version of the agent contains:
-
Government Community Cloud support
-
Internal fixes
Okta Active Directory Password Sync agent, version 1.4.0
This version of the agent contains:
-
Government Community Cloud support
-
Security enhancements
-
Internal fixes
See Okta Active Directory Password Sync Agent version history.
Okta Browser Plugin, version 6.4.0 for all browsers
-
For orgs that enable this feature through self-service EA, end users can now generate passwords from the Okta Browser Plugin pop-up window.
-
For orgs that enable this feature through self-service EA, the Okta Browser Plugin now recommends strong passwords during SWA app sign-up.
-
Plugin extension architecture for Safari has been updated to WebExtension.
SAML 2.0 Assertion grant flow
You can use the SAML 2.0 Assertion flow to request an access token when you want to use an existing trust relationship without a direct user approval step at the authorization server. The flow enables a client app to reuse an authorization by supplying a valid, signed SAML assertion to the authorization server in exchange for an access token. This flow is often used in migration scenarios from legacy Identity Providers that don't support OAuth. See Create Rules for Each Access Policy.
Password management on the new Okta End-User Dashboard
Users who access the new Okta End-User Dashboard from mobile or desktop can now show and copy passwords for their apps to their clipboard. They can also use a new password management modal to edit the username or password fields for their apps.
Okta Provisioning agent incremental imports
The option to incrementally import user data is now available for the Okta Provisioning agent. Incremental imports reduce the time required for synchronization by only downloading user information that has changed since the last successful import. See Okta Provisioning Agent incremental import.
Schemas API unique attributes
The Schemas API now includes unique attributes for custom properties in Okta user profiles and the Okta group profile. You can declare a maximum of five unique properties for each user type and five unique properties in the Okta group profile. This feature helps prevent the duplication of data and ensures data integrity.
Org Under Attack for ThreatInsight
Okta ThreatInsight now has enhanced attack detection capability. “Org under attack” establishes a base line traffic pattern and adjusts based on legitimate changes in traffic patterns. When a threat is detected, the algorithms are optimized to block all malicious requests while creating a System Log event to alert on the attack. After the attack subsides, threatInsight returns into its normal mode of operation. This capability enables quick blocking action during an attack. See About Okta ThreatInsight. This feature will be gradually made available to all orgs.
Enhancements
Custom footer enhancement
With Branding enabled, admins can now hide the Powered by Okta message in the footer of their Okta-hosted sign-in page and End-User Dashboard. See Configure the footer for your org.
Routing Rules performance enhancements
Performance enhancements on the Routing Rules page include optimized adding, editing, dragging, and deactivating of rules, and improved loading when the number of rules exceeds 1,000. See Configure Identity Provider routing rules.
Log per client mode for client-based rate limits
Client-based rate limits are now in Log per client mode for all orgs for both OAuth 2.0 /authorize and /login/login.htm endpoints. This offers additional isolation to prevent frequent rate limit violations.
Fixes
General Fixes
OKTA-325592
When LDAP delegated authentication was enabled, an incorrect event type was used to process user profile updates.
OKTA-372064, OKTA-430527, OKTA-431382
Accessibility issues occurred on the new Okta End-User Dashboard.
OKTA-420524
A password change notification email wasn’t sent to users after their password was changed by an administrator.
OKTA-421812
A Download Latest button wasn’t available for Okta LDAP agents on the Admin Console Downloads page.
OKTA-426923
When users were deleted asynchronously, the entries associated with the user weren't removed from the UniqueEntityProperty table.
OKTA-427016
When Self-Service Registration was enabled, a change to a user's email address in their profile source caused their UPN (user principal name) in Okta to also change, despite it being mapped to the username.
OKTA-427932
When Branding was enabled, the Sign-In Widget was distorted on custom sign-in pages.
OKTA-428268
When an LDAP interface (LDAPi) client had Custom Admin Roles enabled, time-out errors sometimes occurred during group member queries.
OKTA-431349
Translated versions of AD and LDAP configuration validation messages weren’t provided.
OKTA-431868
In the UI for the SuccessFactors app, options for Active User Statuses weren't displayed.
OKTA-432400
Some dialogs didn't appear on the new Okta End-User Dashboard for some users.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Amplitute (OKTA-429432)
Applications
Updates
-
The configuration guide for the Asana SCIM integration is updated: Asana SCIM configuration guide for Okta.
-
The following attributes are added to the KnowBe4 SCIM app:
-
customDate1 -
customDate2
-
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Lucca: For configuration information, see Synchronize Lucca users and groups with Okta.
-
Seculio: For configuration information, see Okta user provisioning and SCIM integration.
OIDC for the following Okta Verified application:
- Extole: For configuration information see Okta Instructions.
Weekly Updates
Fixes
General Fixes
OKTA-383501
When a custom admin role was assigned to an existing group with standard roles, the System Log displayed duplicate Grant user privilege events for the members of the group.
OKTA-399667
Provisioning to Zendesk failed when a user with the same email already existed in Zendesk.
OKTA-414295
For orgs with Custom Administrator Roles enabled, the page filters on the Roles, Resources, and Admins tabs of the Administrators page were labeled incorrectly.
OKTA-414339
Org2Org Push Groups sometimes failed.
OKTA-415370
On OIDC app creation, if no locale was specified, it defaulted to an invalid value (en-US).
OKTA-423420
After Branding was enabled, admins could still navigate to original Settings > Customization pages.
OKTA-426692
Provisioning (create/update) users to NetSuite failed with a Null Pointer Exception (NPE).
OKTA-427646
Group rule Okta Expression Language IF statements couldn’t include integer array attributes.
OKTA-429330
Sometimes, when an org used the Okta IWA Web Agent for Desktop Single Sign-on (DSSO), a missing objectGUID caused a 500 Internal Server Error when users attempted to sign in to Okta.
OKTA-431920
Clicking ASN Lookup when configuring a dynamic zone in the Admin Console didn't open a valid autonomous system number (ASN) lookup service.
OKTA-433981
When an admin role was constrained to a group, users with that role sometimes experienced time-out errors on the People page.
Applications
Application Updates
-
The Airtable SCIM app is updated to support Group Push and Import Groups.
-
The configuration guide for the Acronis Cyber Cloud SCIM integration is updated: Acronis Cyber Cloud SCIM configuration guide for Okta.
New Integrations
New SCIM Integration Application:
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Loom: For configuration information, see Configuring Okta provisioning for Loom.
SAML for the following Okta Verified applications:
-
Docutrax (OKTA-433521)
-
Testsigma (OKTA-405606)
OIDC for the following Okta Verified applications:
- KeepTruckin: For configuration information, see KeepTruckin SSO Guide.
- Sora: For configuration information, see [Okta] Sora configuration guide.
Generally Available
Sign-In Widget, version 5.12.2
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-329002
The Custom Administrator Roles Early Access feature wasn’t available for Developer orgs.
OKTA-335217
OAuth applications granted authorization tokens on accounts for which users had not yet completed registration.
OKTA-419163
Some admins who were assigned a custom role could convert app assignments for users they weren’t constrained to.
OKTA-419532
The System Log didn’t display Client IP for user.lifecycle.create events from users created through self-service registration.
OKTA-421451
Permission attributes for the Dropbox application weren’t displayed correctly.
OKTA-421698
Password-reset failures due to sign-in policy violations didn't appear in the System Log.
OKTA-425798
The endUserDashboardTouchPointVariant property on the Brands API Theme object didn’t include a variant for LOGO_ON_FULL_WHITE_BACKGROUND.
OKTA-425804
Admins who viewed completed tasks on the new Okta End-User Dashboard couldn't see who approved or rejected the tasks.
OKTA-426548
A 500 Internal Server error appeared when sensitive attributes were included in attribute search results.
OKTA-428163
When using the Firefox browser, users were unable to edit the Forgot Password Text Message section of the Settings page.
OKTA-428329
Some admins who were assigned more than one custom role could manage the app assignments for users and groups they weren’t constrained to.
OKTA-431377
End users couldn't customize how long pop-ups were displayed on the new Okta End-User Dashboard.
OKTA-431675
When admins used the Add Person dialog in the new Admin Console to add users, automatic resizing of the dialog resulted in a "The field cannot be left blank" error message.
OKTA-431879
If admins edited their Branding theme after it had been applied to an Okta page, the changes weren’t applied until they performed a hard refresh.
OKTA-432829
With Enhanced Email Macros enabled, email templates that were previously customized or translated with Expression Language (EL) couldn’t be edited and saved due to invalid EL expressions.
OKTA-433352
Some end users lost access to the Pressbox and Genny apps when accessing them from the new Okta End-User Dashboard.
OKTA-434859
SAML Org2Org didn't work on the new Okta End-User Dashboard.
OKTA-435293
After Branding was enabled, admins couldn’t use their org logo on a white background for the End-User Dashboard.
OKTA-436513
After Branding was enabled, some orgs were unable to update their existing subdomain names.
OKTA-436732
After the MFA Factor Enrolled email template was customized with Enhanced Email Macros, its default template continued to be sent to users.
OKTA-436949
The Recently Used Apps section wasn't translated on the Settings page of the new Okta End-User Dashboard until the page was refreshed.
OKTA-437664
An Event Hook for group-based privilege change events sometimes didn't include the Okta subdomain events in the JSON response.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Alabama Power (OKTA-437660)
-
Ally Bank (OKTA-435214)
-
American Express - Work (OKTA-438301)
-
Azure Portal Login (OKTA-436740)
-
Booking Admin (OKTA-436792)
-
Cat SIS (OKTA-436148)
-
Cronitor (OKTA-438303)
-
Exact Online (OKTA-435209)
-
Grove (OKTA-438304)
-
Key Bank (OKTA-438305)
-
Redis Labs (OKTA-436147)
-
SiteGround (OKTA-437897)
-
UBS (OKTA-436149)
-
Vitality (OKTA-436145)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
Deel: For configuration information, see SCIM Provisioning of Users with OKTA.
-
embed signage: For configuration information, see Single Sign-On & User provisioning with Okta.
-
Parkable: For configuration information, see SCIM configuration.
-
SecureFlag: For configuration information, see Okta Single Sign-On Integration.
-
Smarp: For configuration information, see Manage users with SCIM provisioning.
SAML for the following Okta Verified applications
-
Level AI (OKTA-435557)
-
Loom (OKTA-398082)
-
Pima.app (OKTA-435601)
-
Polytomic (OKTA-435605)
-
Smarp (OKTA-415875)
OIDC for the following Okta Verified applications
-
Deepnote: For configuration information, see Okta SSO.
-
Inbox Monster: For configuration information, see Okta Single Sign On Integration.
-
TextUs: For configuration information, see TextUs Next + Okta SSO Process.
-
Waiter.com: For configuration information, see Okta Integration.
September 2021
2021.09.0: Monthly Production release began deployment on September 7
* Features may not be available in all Okta Product SKUs.
Sign-In Widget, version 5.10.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
MFA Credential Provider for Windows, version 1.3.3
This version includes hardening around certain security vulnerabilities. See Okta MFA Credential Provider for Windows Version History.
Improved new device behavior detection
Stronger signals are now used for the detection of new devices. Devices with web browsers that don't store cookies are treated as new and trusted applications must send a unique identifier for each device as a device token. See Behavior detection and evaluation. This feature is made available to all orgs.
Enhancements
ThreatInsight default mode for new orgs
For new orgs, the default mode for ThreatInsight is now set to Audit mode. Previously, with no mode set by default, events weren't logged unless Audit mode or Block mode was enabled manually. Now with Audit mode set by default for new orgs, the security.threat.detected event is logged once a malicious request is detected. See Okta ThreatInsight.
OIN Manager enhancements
- The UI text has been clarified for the group patch batching process in the OIN Manager for SCIM submissions. See the Submit an app integration guide.
- Partners can now provide multiple support contacts, such as email addresses, support URLs, and phone numbers for customers who need assistance when installing or configuring their app integration. This information is shared with users through the app integration’s details page in the OIN catalog. See the Submit an app integration guide.
PagerDuty SSO Domain Support
Base URL is now used instead of Organization Subdomain for PagerDuty SSO configuration. This enables customers with EU domains to input their URL when they set up SSO.
Updated End-User Dashboard icon for mobile users
The End-User Dashboard icon has been updated for mobile users.
Updated Delete Person and Delete Group dialogs
The Delete Person and Delete Group dialogs now include statements to clarify what is removed when a person or group is deleted. This can include application assignments, sign-on policies, routing rules, and user profiles. This change helps admins better understand the ramifications of deleting people and groups. See Deactivate and delete user accounts and Manage groups.
Early Access Features
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-364848, OKTA-364849, OKTA-364921, OKTA-382725, OKTA-382848, OKTA-382907
Some accessibility issues occurred on the Okta End-User Dashboard.
OKTA-386820
Group Push tasks weren't displayed on the Admin Dashboard.
OKTA-391032
Custom admins with Manage group permissions could view the Add Rule button on the Groups > Rules tab.
OKTA-393077
The View IDP Metadata link incorrectly required an active session when application-specific certificates were enabled.
OKTA-408184
A gap between the deactivation of a contractor and the activation of that user to a full-time employee caused incremental imports for Workday to fail.
OKTA-408562
On the Directory > Groups page, an icon didn’t appear for the Zendesk application.
OKTA-409182
Translations weren't provided for some unsuccessful LDAP password update error messages.
OKTA-409388
Users weren't added to groups when the locale attribute filter was set to equals in the group rule.
OKTA-411252
If an admin added an app integration but didn't complete the process and subsequently assigned it to a group, then clicking the link for the app integration through the Groups directory opened the Add app integration process instead of the settings page for that app integration.
OKTA-416414
Sign-in redirect URI requests failed due to wrapping of the designated URI in the Admin Console.
OKTA-416671
Wildcard OAuth redirect URIs failed if subdomains included underscores.
OKTA-417982
During an OAuth client lifecycle event, the debug data section of the System Log logged incorrect client IDs.
OKTA-420534
While loading, the side navigation on the new Okta End-User Dashboard was misaligned.
OKTA-421801
Some users with a custom domain URL couldn't add or edit resource sets for custom admin roles.
OKTA-421951
Adding an expiration date macro to the Password Reset email template resulted in an Invalid Expression error.
OKTA-422282
End users were able to add bookmark apps after their admins configured the App Catalog Setting to allow org-managed apps only.
OKTA-422340
The number of groups displayed in the Admin Dashboard Overview differed from the correct number of groups reported on the Directory > Groups page.
OKTA-422782
Text didn't wrap properly in the Note for requester field for app approval requests.
OKTA-425921H, OKTA-425993H
Sometimes, when users signed in to Okta and Agentless Desktop Single Sign-on (ADSSO) was enabled, groups outside of the selected organizational units were retrieved.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Avalara (OKTA-415081)
-
Fisher Scientific (OKTA-422646)
-
Microsoft Volume Licensing (OKTA-420160)
-
Quadient Cloud (OKTA-422635)
-
RescueAssist (OKTA-422643)
-
WeWork (OKTA-423570)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Acronis Cyber Cloud: For configuration information, see Configuring Provisioning.
- LoopVoc: For configuration information, see Okta (Enterprise version only).
- Qooling: For configuration information, see Configuring SCIM in OKTA for Qooling.
SAML for the following Okta Verified applications:
-
Anomalo (OKTA-421527)
-
Paradime (OKTA-420444)
OIDC for the following Okta Verified application:
- Statsig: For configuration information, see Single Sign-On With Okta.
Weekly Updates
Fixes
General Fixes
OKTA-407869
Some error messages in the Sign-In Widget were translated from English to other languages when the user's language was English.
OKTA-417450
LDAP-sourced users weren’t able to sign in to the Okta Admin Console when their passwords expired and a password policy allowed passwords to be updated.
OKTA-418723, OKTA-420397
New Okta branding didn’t appear on some default error page templates.
OKTA-421227
On the Administrator assignment by admin page, the Copy groups and Paste groups buttons didn’t appear for standard roles that were constrained to one or more groups.
OKTA-421767
The User Profile > Admin roles tab was visible for deactivated users. For active users with no assigned roles, the button to add privileges was mislabeled Edit individual admin privileges.
OKTA-422485
Searches in the LDAP Interface didn’t return results when the search terms were capitalized.
OKTA-423616
The Push Groups page became unresponsive when admins created new group push mappings.
OKTA-424357
ThreatInsight didn't always block IP addresses that were identified as the source of password spray attacks.
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
-
Pop: For configuration information, see Pop: Okta Integration.
SAML for the following Okta Verified application:
-
Wiz (OKTA-422626)
Fixes
General Fixes
OKTA-399959
Session timeout policy wasn't enforced during IdP-initiated login to the Admin Console.
OKTA-412102
If an admin added a rule to an app sign-on policy and named it Default sign on rule, they were unable to edit or delete the rule.
OKTA-414089
Admins with the Manage Applications custom admin permission couldn’t access the Profile Editor, Directory Integrations, or Profile Sources pages.
OKTA-414564
A Sign-in Widget message was translated into Russian incorrectly.
OKTA-420154
If client-based rate limiting was enabled, end users were sometimes presented with a 429 error instead of the sign-in page when their session expired or they signed out.
OKTA-421356
LDAP-sourced user profiles weren’t updated when an admin changed the user profile status from suspended to unsuspended.
OKTA-423419
When Enhanced Email Macros was enabled, using required variables without brackets resulted in a validation error.
OKTA-423470
Org logos on the new Okta End-User Dashboard were sometimes oversized.
OKTA-424330
Some Preview org customers received an error when accessing end-user pages after they changed their browser language to Chinese-Traditional.
OKTA-425588
Rate limit enforcement for Voice-based MFA was not mitigating certain toll fraud attacks.
OKTA-427137
DocuSign deprovisioning sometimes failed with the following error: “Adding entity to http method DELETE is not supported.”
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
3Rivers (OKTA-424892)
-
Adobe Enterprise (OKTA-424893)
-
CallTower (OKTA-424894)
-
Parse.ly (OKTA-422625)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
-
KnowBe4: For configuration information, see here (you need to sign in to KnowBe4 to access their documentation).
-
Verint Community: For configuration information, see How Do I Setup User Provisioning Using SCIM?
SAML for the following Okta Verified application
-
Code Climate Velocity (OKTA-424882)
OIDC for the following Okta Verified applications
-
Auditrunner: For configuration information, see Auditrunner: How to Configure SSO between Auditrunner and Okta.
-
Verint Community: For configuration information, see How Do I Setup User Provisioning Using SCIM?
-
Workrunner: For configuration information, see Workrunner: How to Configure SSO between Workrunner and Okta.
Generally Available
Sign-In Widget, version 5.11.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-393693
If an app sign-on policy required re-authentication every 0 minutes, some users were unable to reset their passwords.
OKTA-419837
When Branding was enabled, custom code editor pages displayed an incorrect warning.
OKTA-423586
Function names that include blank spaces didn’t work with Enhanced Email Macros.
OKTA-425232
When Branding was enabled, the Go to Homepage button on the Okta error page didn’t use the default Okta variant color.
OKTA-425425
When a super admin tried to generate a Current Assignment report, Okta Admin Console didn’t appear as an available application.
OKTA-426446
When a third-party admin role was assigned, the admin's status didn't change in Salesforce and the Exclude admin from receiving all admin-related communications rule wasn't enforced.
OKTA-430127
When Branding was enabled and later disabled, the sign-in and error pages that were customized with HTML code editors during the enabled period could be reset to their defaults.
OKTA-430524
The default password policy was sometimes being evaluated for users instead of the configured password policy.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Frame.io (OKTA-427018)
-
Google Play Developer Console (OKTA-425775)
-
PNC Borrower Insight (OKTA-426061)
-
Tech Data (OKTA-427022)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Blue Ocean Brain (OKTA-426050)
-
Kintone.com (OKTA-421223)
-
Skypher (OKTA-426992)
OIDC for the following Okta Verified applications
-
APIsec: For configuration information, see How to Configure OKTA SSO for APISec.
-
Entromy: For configuration information, see Entromy Okta SSO Integration.
-
TRUCE: For configuration information, see TRUCE & Okta SSO Integration Guide.
Generally Available
Sign-In Widget, version 5.11.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-327544
An HTTP 500 Internal Server Error message appeared when users attempted to sign in to Okta and their username included an asterisk (*).
OKTA-417936
During an IdP Discovery flow, routing rules were no longer observed if users clicked Back to sign in from the MFA prompt.
OKTA-420946
When admins customized the MFA Factor Enrolled or MFA Factor Reset email templates, the default template was sent to users.
OKTA-423578
Admins could create ADSSO IdP routing rules when ADSSO functionality was enabled and then disabled.
OKTA-425321
When an admin had a custom role with the Manage users and Edit users' authenticator operations permissions, they couldn’t enroll users in the YubiKey factor.
OKTA-427145
When the Admin role assignments report was filtered by a group, it didn’t include group membership admins who were constrained to that group.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
- Autotask (OKTA-429728)
- Contract Express (OKTA-429434)
- DocsCorp Support (OKTA-425176)
- Google Play Developer Console (OKTA-425775)
- SAP Concur Solutions (OKTA-427469)
- Shipwire (OKTA-426103)
- Twitter (OKTA-430242)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN Catalog as partner-built:
- Productiv: For configuration information, see Okta SSO Provisioning Setup Guide.
SAML for the following Okta Verified applications
- Jooto (OKTA-429135)
- Merge (OKTA-430337)
OIDC for the following Okta Verified applications
- Cami.AI: For configuration information, see Okta Integration with Cami.AI.
- Provarity: For configuration information, see Okta configuration guide.
- Recollective: For configuration information, see Okta Integration (Identity Provider).
- Upward Agent: For configuration information, see SSO with Okta.
August 2021
2021.08.0: Monthly Production release began deployment on August 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Sign-In Widget, version 5.9.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta solution visible in footer
To help admins identify their Okta solution, the version number in the footer of the Admin Console is now appended with C for Classic Engine orgs and E for Identity Engine orgs. See Identify your Okta solution.
On-Prem MFA agent, version 1.4.4
This version includes bug fixes, security enhancements, and a new version of the Log4J library. See Okta On-Prem MFA Agent Version History.
ADFS Plugin, version 1.7.8
This version includes bug fixes and security enhancements. See Okta ADFS Plugin Version History.
Root signed PIV certificate support
Certificates signed directly from a root CA certificate, with no intermediates, can now be used for Personal Identity Verification (PIV) authentication.
Multiple active user statuses for SuccessFactors integration
Support for multiple active user statuses: When importing users from SuccessFactors into Okta, admins can now select more than one active user status, such as Leave of Absence. See Learn about SAP SuccessFactors Employee Central data provisioning.
Deleted schema property scrubber
All existing data associated with a schema property is now removed when a schema property is deleted. To prevent data corruption, the property cannot be recreated until the existing data is fully removed. Previous data is no longer restored when recreating a deleted schema property with the same definition. This new functionality prevents the corruption of profile data and the associated Elastic search issues. See Add or remove custom directory schema attributes.
This feature will be gradually made available to all orgs.
LDAP agent, version 5.8.0
This version of the agent contains:
-
Password expiry warning support for Oracle Directory Server Enterprise Edition (ODSEE), Oracle Unified Directory (OUD), OpenDJ, and SunOne 5.2 LDAP directory services
Enhancements
New warning for excessive IP addresses
A warning now appears if a gateway or proxy has an IP range with more than 5 million addresses. See Create zones for IP addresses.
Start time and end time of rate limit windows
The Rate Limit Dashboard now displays the start time and end time of the rate limit window for each data point. This helps you analyze each data point with more granularity. See Rate limit dashboard.
End-User Dashboard styling
On the new Okta End-User Dashboard, text color in the side navigation has been updated. See Control access to the Okta End-User Dashboard.
OIN Manager enhancements
The Apps for Good category has been added to the selectable categories list. Also, other category names have been adjusted to match those shown in the OIN App Catalog.
OIN App Catalog UI improvements
If available, support contact information now appears on the details page for app integrations.
Early Access Features
New Features
Third-Party Risk
Okta Risk Eco-System API / Third-Party Risk enables security teams to integrate IP-based risk signals to analyze and orchestrate risk-based access using the authentication layer. Practitioners can step up, reduce friction or block the user based on risk signals across the customer’s security stack. Apart from improving security efficacy, this feature also enhances the user experience by reducing friction for good users based on positive user signals. See Risk scoring.
Fixes
General Fixes
OKTA-381874
On the Agents page, admins couldn't remove deleted RADIUS agents or hide the ones that weren't in use.
OKTA-386797
Users were able to make too many attempts to enter an SMS one-time passcode when performing a self-service unlock.
OKTA-388903
Using an Office 365 thick client to open documents from the SharePoint Server didn't work consistently.
OKTA-399414
A link was broken on the OIDC Identity Provider profile mapping page.
OKTA-404612
When updating the provisioning settings for an app integration, some admins had to reload the page because the Admin Console showed a verification message and then stopped responding.
OKTA-404620
Workflow URLs with the okta-emea subdomain weren’t automatically verified when used as an Event Hook URL.
OKTA-406499
On the Admin Console Tasks page, the first 10 tasks were duplicated when Show more tasks was selected and 10 or more tasks were already listed.
OKTA-409514
If an app integration with provisioning enabled was upgraded to support the Push Groups feature, admins were repeatedly prompted to enable provisioning.
OKTA-415772
The Tasks view was missing from the new Okta End-User Dashboard.
App Integration Fixes
The following SWA apps weren't working correctly and are now fixed:
-
Azure Portal Login (OKTA-411455)
-
Cisco WebEx Meeting Center - Enterprise (OKTA-411543)
-
Matrix Teams (OKTA-415413)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN catalog as partner-built:
- Paylocity: For configuration information, see Configure SSO and User Provisioning with Paylocity and Okta.
SAML for the following Okta Verified application:
-
Neptune (OKTA-393740)
Weekly Updates
Generally Available
Sign-In Widget, version 5.9.4
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-386084
Error page templates were inconsistently formatted.
OKTA-409142
The Registration Inline Hook didn’t correctly display error messages to the user during user self-registration.
OKTA-411448
Users who enrolled in multifactor authentication using the Active Directory Federation Services integration were unable to download the Okta Verify app from the Apple App Store and the Google Play store during enrollment.
OKTA-415642
Theme colors weren’t applied to custom pages in Internet Explorer 11.
OKTA-416292
The password management modal was incorrectly minimized on the new Okta End-User Dashboard after an end user responded to the copy confirmation modal.
OKTA-417651
When admins attempted to delete or revoke a YubiKey from the Okta Admin Console, the Done button didn’t appear upon completion.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Fannie Mae Desktop Underwriter (OKTA-416904)
-
Frame.io (OKTA-416896)
-
i-Ready (OKTA-416899)
-
InternationalSOS (OKTA-415410)
-
LifeLock (OKTA-413854)
-
Milestone Xprotect Smart Client (OKTA-416893)
-
SDGE (OKTA-416903)
-
ShipStation (OKTA-416897)
-
Simple Sales Tracking (OKTA-416906)
-
Washington Post (OKTA-416908)
-
Yodeck (OKTA-415411)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
- GitHub AE: For configuration information, see Configuring Provisioning for GitHub AE.
- LoopVoc: For configuration information, see Single Sign On (SSO): Okta (Enterprise version only).
- MaestroQA: For configuration information, see MaestroQA/Okta SCIM configuration guide.
- MaestroQA-Enterprise: For configuration information, see MaestroQA-Enterprise/Okta SCIM configuration guide.
- Sentry: For configuration information, see Okta SCIM Provisioning.
SAML for the following Okta Verified application
-
Hiretual (OKTA-413861)
OIDC for the following Okta Verified application
-
Seamless.AI: For configuration information, see Connecting and Setting up Okta SSO.
Fixes
General Fixes
OKTA-309646
The scroll bar didn't function as expected while adding a new access policy to an authorization server.
OKTA-364838
Some accessibility issues occurred on the Okta End-User Dashboard.
OKTA-392409
Office 365 silent activation sometimes failed if the sign-on policy required re-authentication.
OKTA-407591
Prompts initiated by an admin to reset an end user’s password for an SWA app weren't displayed on the Okta End-User Dashboard.
OKTA-410027
When a user was deleted, the AlternateId field in the System Log displayed the user’s Okta identification number and not their email address.
OKTA-412526
The Note for requester field within the self-service app request approval settings didn't properly display messages.
OKTA-414136
The Office 365 integration in the Okta App Catalog showed a Group Linking option that wasn't available for Office 365.
OKTA-414387
End users who attempted to use a custom sign out URL were presented with a blank page on Internet Explorer 11.
OKTA-418656
Users weren’t prompted for additional authenticators after self-service password resets even though their sign-on policy required them.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed:
-
Alerus (OKTA-418805)
-
BenXcel (OKTA-418794)
-
Inbox by Gmail (OKTA-412080)
-
IBM MaaS360 (OKTA-418799)
-
Redis Labs (OKTA-418789)
Applications
Application Updates
-
We have added the
userTypeattribute to the Slab SCIM schema. For details see the Slab Okta SCIM Integration Guide. -
The FIS Global Client integration is deprecated from the OIN Catalog.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN Catalog as partner-built:
- Documo: For configuration information, see Okta Scim Configuration Guide.
- DocuSign CLM UAT: For configuration information, see Okta SCIM and SAML Integration.
SAML for the following Okta Verified applications:
-
Blingby Inline (OKTA-410691)
-
Panzura Data Services (OKTA-419287)
-
RudderStack (OKTA-413572)
OIDC for the following Okta Verified applications:
-
EZGIT: For configuration information, see Logging in with Okta single sign-on.
-
Joyous: For configuration information, see Okta Single Sign-On.
-
XY Sense: For configuration information, see How to add SSO Okta integration.
Fixes
General Fixes
OKTA-295856
Buttons and text were misaligned on the API > Trusted Origins tab.
OKTA-382908
A confirmation message wasn’t displayed when an admin removed the last resource from a resource set or the last permission from a role.
OKTA-385343
Group attributes weren't pushed from Okta to Active Directory (AD) as expected.
OKTA-387007
When an admin clicked Custom roles from the Overview section on the Administrators page, the Roles tab opened with the incorrect filters applied.
OKTA-402814
Users didn't receive a verification email after updating a secondary email address.
OKTA-402856
In the redesigned Admin Console, import safeguard warning messages didn’t appear on the Dashboard.
OKTA-412025
Users didn't receive a verification email after they were activated on the People page.
OKTA-413954
Certain YubiKey device make and model names didn't appear correctly on the Okta End-User and Admin Dashboards.
OKTA-417326
Some tabs and buttons on the user and group profile pages of the Custom Administrator Roles user interface were labeled incorrectly. Also, the Admin role assignment report page was called Custom reporting.
OKTA-418039
Enhanced email macros didn’t work with Branding.
OKTA-418150
On the People page, the last user with super admin permissions could be deleted without generating an error.
OKTA-418922
When a user was deleted on the People page, the PostDeleteUserEvent event type was Initiated and not Completed.
OKTA-420122
In the redesigned Admin Console, the Actions drop-down menu for SAML app certifications didn’t expand correctly.
OKTA-420740
When a theme was applied to the Okta-hosted sign-in page, the Sign in button didn’t change to the selected primary color.
OKTA-421446
The Administrator assignment by admin page didn’t load properly when the delegated admin had a standard role that was constrained to specific apps or groups.
OKTA-421481
Some Expression Language email templates didn’t work with Branding.
App Integration Fixes
The following SWA app was not working correctly and is now fixed:
-
Vitality (OKTA-420790)
Applications
Application Update
The following integrations are deprecated from the OIN Catalog:
-
Hiveed
-
BenXcel
-
FIS Global
-
Nanigans
New Integrations
SAML for the following Okta Verified applications:
-
Blingby Programmatic (OKTA-421181)
-
Perimeter 81 (OKTA-415079)
-
Snackmagic (OKTA-419393)
-
Suveryapp (OKTA-420053)
SWA for the following Okta Verified application:
-
Integromat (OKTA-420293)
OIDC for the following Okta Verified application:
-
Hone: For configuration information, see Logging in with Okta single sign-on.
July 2021
2021.07.0: Monthly Production release began deployment on July 12
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Dedicated help sites for Okta products
Three of Okta’s products — Access Gateway, Advanced Server Access, and Workflows — now have their own dedicated help sites:
This enhancement offers direct access to independent online help sites for these products from help.okta.com. The new sites provide several benefits:
- Compactly designed, product-centric content
- Streamlined navigation
- More efficient content updates and responsiveness to customer feedback
Okta Device Registration Task, version 1.3.2
This release includes internal code refactoring. You can download this version from the Settings > Downloads section of the Admin Console.
New Domains API response properties available
The Domains API includes the new response object properties of certificateSourcetype and expiration. The certificateSourcetype is a required property that indicates whether the Certificate is provided by the user. The accepted value is Manual. The expiration property on the DNSrecord object is an optional property that defines the TXT record expiration. See Domains API.
Default end-user experience
New orgs, including those created through the org creator API or the developer.okta.com website, will have the new end-user experience enabled by default in preparation for the old end-user experience deprecation starting on October 13. Learn more about this migration and other frequently asked questions in our support article.
Disable Import Groups per SCIM integration
Admins can now choose whether or not to import groups with all SCIM integrations. This new option is available when you set up provisioning for a SCIM integration.
Note that you can't disable group imports for an app if:
-
Import New Users and Profile Updates isn't enabled.
-
App Assignments based on Group exist.
-
Group policy rules exist.
-
Group Push mappings exist.
In these cases, an error is displayed.
Nutanix support
Okta Access Gateway customers can now download and deploy the Access Gateway virtual appliance on Nutanix Acropolis Hypervisor (or Nutanix AHV), a hyper-converged infrastructure platform popular among larger organizations. This provides customers with more options for infrastructure services supported by Access Gateway, including AWS, OCI, VMWare, and now Nutanix.
Remove the ability to disable Admin Experience Redesign
You can no longer disable the Admin Experience Redesign feature for your orgs.
Note: This is not applicable for orgs that didn't have Admin Experience Redesign enabled and used the legacy experience until 2021.06.4.
Windows Hello as an MFA factor is not supported for new orgs
Windows Hello as an MFA factor is no longer supported for new orgs. Existing orgs already using this feature can continue using it.
Test custom email templates
Admins can send themselves a test email to see how their custom email templates will look and function. This allows them to validate macro attributes and translations in the customized template and to see how the template will render in different email environments. Sending the test email to their primary email address eliminates their need to create a real end-to-end workflow to test customization. For more information, see Test a customized email template .
Create LDAP group password policies
You can now create group password policies for LDAP sourced users. This gives you the flexibility to provide users with the same password policy requirements as your local LDAP directory, easing the user experience of an LDAP integration with Okta. See About group password policies and Sign-on policies.
Event Hook preview
Event Hook preview lets admins easily test and troubleshoot their Event Hooks, as well as send sample requests without manually triggering an actual event. This means admins can preview the payload of a specific Event Hook type and make sure that it's what they need to move forward before a full deployment to production. See Event hook preview.
Enhancements
Workplace by Facebook new custom attribute
Okta now supports the is_frontline custom attribute in Workplace from Facebook. Supporting user type designations enables access for frontline and deskless workers.
OIN App Catalog UI improvements
For each app integration in the OIN App Catalog, the details page has been updated to use tabs that display the overview and the specific capabilities of the app integration. The details page also shows the Capabilities in the side navigation. Clicking a specific capability returns the administrator to the main Add Application page with that capability pre-selected in the filter. When an admin searches for app integrations, the filter is now persistent through category changes or when they refresh the page.
OIN Manager category selections
For app submissions in the OIN Manager, the category designations have been updated to match the categories available in the OIN App Catalog.
Changes to group assignment options for OIDC apps
Admins can create new OIDC applications without assigning them to a group. See Create OIDC app integrations using AIW.
HTML sanitizer for email templates
Velocity-based email templates are now processed by an HTML sanitizer. Templates that don’t conform to the rules of the sanitizer are corrected before they are sent. See Customize an email template.
Email template events
The creation and deletion of email templates are now logged as events in the System Log.
Rate limit violation event logging
Session-user and User rate violation events are now logged as operation-level events instead of org-wide events. This allows you to distinguish between rate limit violations at an org level and individual level.
Updated branding for End-User Dashboard
Okta branding on the Okta End-User Dashboard has been updated.
Early Access Features
New Feature
FIPS compliance for iOS or Android devices
Federal Information Processing Standards (FIPS) compliance is now available for iOS or Android devices. FIPS can be enabled on the Okta Verify configuration page. When FIPS compliance is enabled, admins can be confident that only FIPS-compliant software is used. See About FIPS-mode encryption.
Fixes
General Fixes
OKTA-274754
When an admin attempted to add an app integration to their org for which the org was not entitled, the error message didn't display the org's edition name.
OKTA-380653
A user-created on-the-fly app incorrectly appeared on the Tasks page under Number of apps that can have provisioning enabled.
OKTA-397607
Sometimes the failed-sign-in counter didn’t reset to zero after an end user successfully signed in, which resulted in improper lockouts.
OKTA-400220
When OpenLDAP was used with delegated authentication, an error message containing unnecessary information appeared if users attempted to change their password and it didn't meet the LDAP complexity requirements.
OKTA-401490
LDAP import schedules weren't updated when Relative Distinguished Name (RDN) attribute mapping from Okta to LDAP was missing.
OKTA-402247
New device notifications weren't sent during passwordless sign-in flows.
OKTA-404865
Group Push for Slack caused group members to be reset and gradually re-added, during which time group members couldn't access the app.
OKTA-405351
Some deactivated SAML IdP users whose attributes were updated with Just-in-time Provisioning were activated even though the reactivation JIT setting wasn't selected.
OKTA-407292
Some users were deactivated instead of deleted in Automations.
OKTA-408802
Sometimes, during SAML app configuration, the metadata link improperly required a sign-in session.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
San Diego Gas and Electric (OKTA-407572)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- PowerDMS: For configuration information, see Configuring Provisioning for PowerDMS.
- Redprint: For configuration information, see User Provisioning with Okta.
- SkillsHood: For configuration information, see How to Configure Provisioning for SkillsHood.
- Squarespace: For configuration information, see Logging in with single sign-on through Okta (Enterprise).
SWA for the following Okta Verified applications
-
Headspace (OKTA-403509)
-
Redprint (OKTA-394718)
-
SCOPE (OKTA-405791)
OIDC for the following Okta Verified applications
-
QFlow.ai: For configuration information, see How does your Okta Integration work (you need a QFlow.ai account to access this documentation).
-
ReputationDefender: For configuration information, see OIDC Configuration Guide for Okta.
-
smart technology group: For configuration information, see smart technology group and Okta OIDC Integration.
Weekly Updates
Generally Available
Sign-In Widget, version 5.8.2
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-405084
Long-running deactivation jobs didn't overwrite user status changes after a user was deleted.
OKTA-409081
Google Chrome users saw a session lifetime warning if they accessed an end-user dashboard embedded in an iFrame.
OKTA-409227
In the OpenID Connect (OIDC) app wizard, the default Assignments selection was Allow everyone in your organization to access.
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
- Inspectify: For configuration information, see User Provisioning with Okta.
-
Reftab: For configuration information, see How do I configure SCIM with OKTA?
SAML for the following Okta Verified applications
-
4Degrees (OKTA-405438)
-
SkillsHood (OKTA-404888)
Generally Available
Sign-In Widget, version 5.8.4
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-382511
Users saw the wrong error message if they attempted self-service registration with a unique attribute (such as Customer Account Number) that was already in use.
OKTA-383402
In Identity Provider routing rules, the User attributes input field for the AND User Matches condition was narrow and misaligned.
OKTA-394734
The Admin Console Search field was unavailable with Lightweight Directory Access Protocol integrations.
OKTA-398165
Admins who selected the Users Locked Out task on the Admin Dashboard were redirected to the Reset Password page instead of the Unlock People page.
OKTA-399643
Org groups didn't appear as expected on the Admin Console Groups page.
OKTA-401969
Active Directory Single Sign-On users who were prompted to upgrade to Okta Verify with Push Authentication received an error 403 Forbidden message.
OKTA-404295
When an app request email was sent to an admin, the encoded URL was listed instead of its punycode URL.
OKTA-404488
During searches for Lightweight Directory Access Protocol-sourced users, concurrency limit violations caused 429 Too Many Requests errors.
OKTA-405064
Deleted user profiles were permanently removed when they were reactivated.
OKTA-405259
Sometimes, an agent status email wasn’t sent when the Okta IWA Web agent was unavailable.
OKTA-406581
End users who were unable to sign in successfully with Just-in-Time provisioning were sometimes redirected back to the sign-in page without seeing an error message.
OKTA-410072
Sample app bundle downloads didn’t use the current SDK version.
OKTA-411109
The Russian translation for an expired token was inaccurate.
OKTA-413703
Some orgs experienced an issue where the More Integrations section of the Okta App Catalog appeared empty.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Addison Lee (OKTA-410400)
-
Business Insider Prime (OKTA-411534)
-
Calxa (OKTA-411523)
-
CB Insights (OKTA-410399)
-
Cloudapp (OKTA-411535)
-
Dashlane Business (OKTA-410403)
-
Dealer Daily Lexus (OKTA-411531)
-
eFlex Employee (OKTA-411513)
-
Fresh Direct (OKTA-410395)
-
Instacart (OKTA-411491)
-
Instacart Canada (OKTA-411510)
-
Ned Davis Research (OKTA-409608)
-
New York Times (OKTA-410985)
-
Office Tools Portal (OKTA-410397)
-
Passkey (OKTA-411526)
-
Samsara (OKTA-410392)
-
Skillsoft (OKTA-410402)
-
Soundcloud (OKTA-411532)
-
Trustwave (OKTA-410406)
-
United Tranzactions (OKTA-411519)
-
Untangle (OKTA-411520)
-
Wall Street Journal (OKTA-410396)
-
Zocdoc (OKTA-410398)
-
Zscalerbyz (OKTA-410405)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
- KloudHybrid: For configuration information, see Configuring Okta Provisioning for KloudHybrid using SCIM 2.0.
- PrivaceraCloud: For configuration information, see SCIM Server User-Provisioning.
- Twingate: For configuration information, see Configure SCIM User & Group Sync.
SAML for the following Okta Verified applications
-
Bonsai (OKTA-409442)
-
Cafe (OKTA-405554)
-
Dashlane (OKTA-407393)
-
eSuite (OKTA-405607)
-
FileFlex (OKTA-410143)
-
ShopRun (OKTA-411470)
-
TeamPay (OKTA-393790)
-
Transcend Engagement (OKTA-409454)
SWA for the following Okta Verified application
-
Samsara (Driver Sign In) (OKTA-414275)
OIDC for the following Okta Verified applications
- Macorva: For configuration information see Okta SSO Conguration Guide.
- Muzeek: For configuration information see Logging in with Okta single sign-on.
- SaaS.de: For configuration information see Sign-in with Okta.
- Sensor Tower: For configuration information see Sign on Securely to Sensor Tower with Okta - You will need a Sensor Tower account to access this documentation.
June 2021
2021.06.0: Monthly Production release began deployment on June 7
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta Sign-In Widget, version 5.7.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
MFA Credential Provider for Windows, version 1.3.1
The MFA Credential Provider for Windows version 1.3.1 includes hardening around certain security vulnerabilities, support for Windows 2019, and other general bug fixes and improvements. See Okta MFA Credential Provider for Windows Version History
Okta Device Registration Task, version 1.3.1
This release is based on Python 3, to support macOS 10.15.xx (Catalina) and above. It addresses the known issue of device enrollment failures. You can download this version from the Settings > Downloads section of the Admin Console. See Enforce Okta Device Trust for Jamf Pro managed macOS devices and Okta Device Trust for macOS Registration Task Version History.
LDAP Interface sign on policy
When creating a sign on policy, you can now create rules that apply only to LDAP Interface user authentications. With this change, you can apply a sign on policy to LDAP Interface authentications and exclude other authentication methods. See Sign-on policies.
Import Safeguard Event Hook
The Import Safeguard event is available for use as an Event Hook. Admins can use the Import Safeguard event to generate a notification when an import safeguard occurs. See Import safeguards and Event Types.
App Integration Wizard improvements
The App Integration Wizard has been updated with several usability improvements. For quicker access, you can now launch the wizard from either the Applications page or the Browse App Integration Catalog page. The platform and sign-on method selection process has been streamlined to remove unnecessary inputs. Help hints in the wizard have been improved to eliminate the need to look up definitions and guidance from the documentation. To save time, trusted origins and group assignment tasks can now be completed as part of the process rather than after the wizard creates the app integration. See Create custom app integrations.
Polling support for Agentless Desktop Single Sign-on and Integrated Windows Authentication authentication sessions
Agentless Desktop Single Sign-on (ADSSO) and Integrated Windows Authentication (IWA) authentication sessions now include polling to reduce the likelihood of service disruptions during periods of high bandwidth use. For users authenticating with ADSSO or IWA during peak periods, this change increases the likelihood that a server will be available to process their authentication request. See Active Directory Desktop Single Sign-on.
Okta Verify support for risk-based authentication
Okta Verify with Push now supports risk-based authentication. With this feature, admins can assess the level of risk when an end user signs in to their org and attempts to authenticate with Okta Verify. See . This feature will be gradually made available to all orgs.
RADIUS support for EAP-TTLS
The RADIUS agents now support the EAP-TTLS network authentication protocol. See the supported factors section in any RADIUS Integrations. This feature is made available to all orgs.
Recently Used Apps
A Recently Used apps section has been added to the top of the Okta End-User Dashboard and the Okta Browser Plugin to make it easier for end users to access their applications. End users can enable and disable the Recently Used setting in their Preferences panel or Account Settings on the Okta End-User Dashboard.
When enabled, the Recently Used apps section is visible at the top of the Okta End-User Dashboard regardless of the number of apps assigned to the end user or whether any apps have been launched. If an end user re-enables the Recently Used apps section, apps that were used when the feature was previously enabled are not preserved. See Recently used applications. This feature will be gradually made available to all orgs.
Enhancements
OIN Manager category selection changes
The choices in the OIN Manager App category selection list have been updated to match the categories available in the public OIN catalog. For existing submissions, the category choice isn't changed until the ISV updates the app submission in the OIN Manager. ISVs can also now select up to three categories for their app integration. See Submit an app integration.
OIN Manager OIDC enhancements
ISVs can now select which OpenID Connect modes their application supports: Single-Page Application (SPA) or Web. See OIDC settings.
Rate limit System Log Event Hook enhancements
The system.operation.rate_limit.warning event has been updated and now notifies administrators when their org is approaching an Event Hook rate limit.
The system.operation.rate_limit.violation event has been updated and now notifies administrators when their org has exceeded an Event Hook rate limit.
See Event Types.
OAuth scope flexible consent
When user consent is required for an OAuth scope, a new check box is available to enable Flexible consent, which blocks services from requesting the scope. See Create Scopes.
Combined OAuth claim evaluation events
To reduce system load and operational cost, a single app.oauth2.as.evaluate.claim event is now recorded per request, instead of separate events for access tokens and ID tokens.
Updated UI for provisioned username options
If an app integration doesn't support the Create only option in the Application username format drop-down menu, the option is now disabled rather than hidden.
Session synchronization
All browser tabs that access the Okta End-User Dashboard now maintain the same session lifetime.
Hidden fields in Sign-In Widget
Hidden username and password fields in the Sign-In Widget are no longer identifiable by screen readers.
File upload tool tips
Tool tip text formatting has been standardized on the App Instance page.
Active SAML certificate warning
A warning now appears when currently active SAML certificates are set as inactive in the Okta Admin Console.
Fixes
General Fixes
OKTA-371017
Assigning attributes when provisioning to Webex sometimes resulted in errors.
OKTA-374204
When a custom sign-out page was configured, users who reset their password with SMS and then clicked Back to sign in were redirected to the custom page.
OKTA-386816
Some app tasks that weren't mapped to Okta users didn't appear on the Admin Dashboard.
OKTA-387918
Admins were unable to view the Import Monitoring dashboard for applications when the application admin role was assigned to specific applications.
OKTA-388914
Okta erroneously pushed profile updates to Rally upon user reactivation when updates to user attributes were disabled.
OKTA-389233
The Sign-In Widget appeared blank for users who attempted to sign in while using multiple WebAuthn authenticator enrollments.
OKTA-393663
Some Firefox 88.0 users on Mac devices were presented with a blank page after signing in to Okta.
OKTA-395953
An incorrect error message was displayed when a user was created with a duplicate unique property.
OKTA-396812
If a user tried to re-enroll via RADIUS after their SMS factor was reset, they weren't prompted to verify their phone number.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Addepar (OKTA-396929)
-
Ustream (OKTA-396921)
Applications
Application Updates
Adobe Sign now supports OAuth and REST API mode for provisioning for new app instances. Existing app instances should be migrated to the new app, see the Adobe Sign Migration Guide for details.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Icertis Contract Intelligence App: For configuration information, see ICI OKTA SCIM App: Configuration Guide for SCIM Integration.
SAML for the following Okta Verified applications
-
AlphaSense (OKTA-394744)
-
cloudtamer.io (OKTA-399136)
Weekly Updates
Generally Available
Sign-In Widget, version 5.7.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-386890
Automation rules that were created to delete inactive users sometimes failed due to deprovisioning errors.
OKTA-388300
When the new Admin redesign experience was enabled, the Agents Dashboard displayed incorrect version information about upgraded RADIUS agents.
OKTA-388727
The Clear Unconfirmed Users button didn't work consistently on the Active Directory (AD) Import page.
OKTA-389975
The Sign On page was unresponsive after the Credentials Details section of Bookmark apps was updated.
OKTA-391272
Provisioning errors occurred when email addresses were pushed from Okta to UltiPro after being updated in Active Directory.
OKTA-398218
Syncplicity couldn't be provisioned for EU-based domains.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
1Password Business (OKTA-398705)
-
Eden Workplace (OKTA-398670)
-
Gong (OKTA-394257)
-
Instagram (OKTA-398090)
-
Schwab Advisors (OKTA-401549)
Applications
Application Update
The existing Cacoo integration is deprecated and renamed Cacoo (deprecated). Customers should now use the Nulab Pass (Backlog Cacoo Typetalk) (SAML) integration in our OIN catalog.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
- MindTouch: For configuration information, see User and Group Provisioning with Okta.
-
Amplitude: For configuration information, see Setting Up SCIM Provisioning in Amplitude.
OIDC for the following Okta Verified applications
-
Quantum Whisper: For configuration information, see Okta Single Sign-On Setup.
-
Worklytics: For configuration information, see Okta as SSO provider for Worklytics.
Generally Available
Sign-In Widget, version 5.7.2
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-381119
Silent Activation was blocked for certain orgs if the app sign on-policy required MFA reauthentication.
OKTA-383213
Admins could create an app using the App Integration Wizard even when their trusted origin configuration was incorrect.
OKTA-384020
The Active Directory Self-Service Unlock Account email template didn't recognize ${samAccountName} as a valid input.
OKTA-391097
Admins couldn't clear the Auxiliary Object Class attribute for an LDAP integration after setting the attribute's value.
OKTA-392165
Pushing a group from Okta to Slack failed if the group contained more than 15,000 users.
OKTA-393207
End users with custom user types couldn't modify their personal information from End-User Dashboard > Settings.
OKTA-393223
Admins weren't able to use the tab key to navigate in the Upload Logo section of the App Integration Wizard.
OKTA-395044
Factor enrollment with Device Trust failed for some users when they attempted to sign in to Airwatch Workspace One for the first time.
OKTA-398676
Admin permissions were sometimes revoked unexpectedly when new permissions were assigned to the admin.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
8x8 Account Manager (OKTA-402020)
-
Airbnb (OKTA-400493)
-
Certify (OKTA-401731)
-
Dodge Company Shop (OKTA-402526)
-
Enterprise (OKTA-402529)
-
LiveWell (OKTA-402511)
-
Recorded Future SSO (OKTA-402503)
-
Shopify (OKTA-401733)
-
Techsmith (OKTA-400221)
Applications
Application Updates
-
The Boardvantage Meetx/Director app integration is renamed to Nasdaq Boardvantage.
-
The Udemy for Business SCIM app is updated as follows:
-
The Separate Group and Membership Creation setting is enabled.
-
Batch size is updated to 500
-
-
The Zoom SCIM app integration schema is updated. For details, see Okta user management with Zoom.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
-
Hoxhunt: For configuration information, see Okta SSO and SCIM configuration.
-
Vimeo: For configuration information, see Configuring SCIM for Vimeo and OKTA.
SAML for the following Okta Verified applications
-
Muck Rack (OKTA-399126)
-
Pave Commute (OKTA-399131)
SWA for the following Okta Verified application
-
HomeTagz (OKTA-402746)
OIDC for the following Okta Verified applications
-
ClicData: For configuration information, see Configuring SSO with Okta Open ID from App Catalog.
-
Hi5: For configuration information, see Hi5 integration with Okta - OpenID Connect.
-
Jeli: For configuration information, see Jeli and Okta Integration Guide.
-
Sevanta Dealflow: For configuration information, see the Sevanta Okta Configuration Guide.
-
True IP Integration Portal: For configuration information, see TrueI IP Solutions Okta Portal Integration.
Generally Available
Sign-In Widget, version 5.7.3
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Fixes
General Fixes
OKTA-372803
When set to custom, Okta Username format was autofilled with an invalid SpEL expression in the AD General Settings.
OKTA-386004
Some text strings in the End-User Dashboard weren't translated.
OKTA-386545
Exchange ActiveSync Settings in the Office 365 app > Mobile tab couldn't be saved.
OKTA-386841
When admins clicked the Application requests waiting task in the new Admin Dashboard, nothing happened.
OKTA-388959
The app import status showed as In Progress even when the import job had failed.
OKTA-395489
The Create new app integration and CAPTCHA integration forms used the term sign-on instead of sign-in.
OKTA-398094
The new End-User Dashboard displayed options to download Okta Mobile.
OKTA-399667
Some new Zendesk users weren't correctly provisioned in Okta.
OKTA-402379
Some admins could add apps to their orgs after the app limit was reached.
OKTA-402547
Users were prompted for MFA after they reset their passwords using Okta Windows Credential Provider.
OKTA-404379
The OIDC default scopes link sometimes added non-default scopes to access policy rules for authorization servers.
OKTA-407122H
Routing rules were ignored when using the user matches expression.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
CarGurus (OKTA-404542)
-
Delivery Slip (OKTA-402517)
-
SAP Concur Solutions (OKTA-404533)
-
Small Improvements (OKTA-402942)
-
Spectrum Business: Time Warner Cable (OKTA-402523)
-
SquareSpace Template (GT) (OKTA-404538)
-
Staples Advantage (OKTA-402525)
-
Workday Community (OKTA-404532)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN catalog as partner-built:
- Postman: For configuration information, see Configuring Provisioning for Postman on Okta.
SAML for the following Okta Verified application
-
Vimeo (OKTA-403474)
OIDC for the following Okta Verified applications
- Mursion: For configuration information, see Configuring OpenID Connect with Okta.
-
DelightIQ: For configuration information, see How to configure Okta for Single Sign-On?
Fixes
General Fixes
OKTA-294735
Some text strings in the default email template editor weren’t translated.
OKTA-378363
When a user signed in over the Cisco Meraki network, using the RADIUS agent and Cisco Meraki app, and then changed their password, their account became locked.
OKTA-383559
Profile updates failed to push to the G Suite app and no error information was logged.
OKTA-386081
Error page templates for default and custom domains had inconsistent styling.
OKTA-387154
After the Content Delivery Network (CDN) was disabled for an org, the Sign-In Widget was still served from their custom domain.
OKTA-397685
On the Applications page, the cursor changed to show an extended hand cursor for non-clickable items.
OKTA-400622
The Browse App Catalog button on the Applications page was disabled for app admins.
OKTA-404562
The password policy requirements for LDAP-sourced user passwords were shown in a sentence format instead of a list.
OKTA-408809H
The MS Dynamic application icon didn't work as expected.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Akamai EdgeControl (OKTA-406128)
-
AutoEntry (OKTA-406126)
-
AxurePortal (OKTA-405442)
-
Lincoln Financial Group (OKTA-404686)
-
Recorded Future (OKTA-405697)
-
SharePoint (OKTA-405464)
-
WealthEngine (OKTA-405780)
Applications
Application Update
-
The Bluecross Member Central - Massachusetts integration is deprecated and has been removed from the OIN catalog.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN catalog as partner-built:
-
AlexisHR: For configuration information, see SAML & SCIM Configuration Guide for Okta.
-
Headspace: For configuration information, see Configuring Provisioning for Headspace.
-
Malt: For configuration information, see Configuring Okta Provisioning for Malt.
-
Outreach: For configuration information, see Automated User Provisioning Guide for Okta.
SAML for the following Okta Verified application
-
TrueCare (OKTA-405039)
OIDC for the following Okta Verified application
-
Robocorp Control Room: For configuration information, see the Robocorp Okta installation guide.
May 2021
2021.05.0: Monthly Production release began deployment on May 10
* Features may not be available in all Okta Product SKUs.
Okta Sign-In Widget, version 5.6.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta Browser Plugin, version 5.45.0 for all browsers
-
The Recently Used apps section is now visible and accessible from the plugin popover.
-
The Recently Used apps section can be configured by end users on the Okta End-User Dashboard.
-
Plugin popover loading times have been decreased.
-
The plugin’s design and images have been updated.
Agentless Desktop Single Sign-on authentication progress screen updates
Agentless Desktop Single Sign-on (ADSSO) authentication progress screens have been updated to make authorization and verification progress more visible and improve the user experience. See Configure agentless Desktop Single Sign-on.
Group push mapping change
When admins create a group push mapping and link it to a group whose members were imported through another method, those users are now Okta sourced. See About Group Push.
New Select assignments to convert screen
The addition of a Select assignments to convert screen to the Okta Admin Console makes the conversion of app assignments from individually-managed to group-managed easier. With the click of a button you can now quickly locate, select, and then convert individual users, or convert all eligible assignments. See Convert an individual assignment to a group assignment.
Generally Available Enhancements
System Log enhancements
OAuth refresh token event details
System Log events now display information that indicates whether an OAuth refresh token is rotating or persistent.
System Log debug field changes
System Log Advanced Filters no longer support the Contains operator for the following fields:
debugContext.debugData.url
debugContext.debugData.requestUri
This is to ensure that service stability and operations aren't impacted.
actionId value now available in the System Log
To identify the Okta Active Directory agent used to process a delegated authentication request, the actionId value has been added to the user.authentication.auth_via_AD_agent event in the System Log . For orgs that use multiple agents, this value makes it easier to identify the specific location of log data used to resolve authentication issues. See System Log.
OIN Manager - SCIM submission enhancement
When submitting a SCIM app in the OIN Manager, ISVs can now specify the maximum number of group membership changes that can be included in a single PATCH request. See Configure protocol-specific settings.
Open On-Prem MFA and RSA SecurID page on select
When admins select either On-Prem MFA or RSA SecurID token names from Security > API, the associated MFA factor page now opens.
New help text for Initiate Login URI field
The Initiate login URI field, available in an application’s General Settings tab, now includes additional inline help text to clarify the correct URI to add to this field.
TLS certificate update for okta.com
The TLS certificate for okta.com will be updated beginning on May 6th, 2021, US Pacific Time. The updated certificate will be signed with a new trust chain and Root Certificate Authority (CA) trust anchor. The Root CA will change from the DigiCert High Assurance EV Root CA to the DigiCert Global Root CA. To avoid negative impact and service outages, customers who have a limited or non-standard set of certificates in their trust stores must take action prior to May 6th, 2021. See FAQs.
Password Health Report enhancement
Date columns in the Password Health Report are now in ISO 8601 format to improve readability.
Increased authorization code lifetime
The OAuth authorization code lifetime is increased from 1 to 5 minutes.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-379813
In some cases, end users who verified with IdP as a factor and selected the option to Remember this device were unable to save their configuration.
OKTA-379879
When signing in to a third-party identity provider (IdP), the sign in hint wasn’t provided as a request parameter to the IdP.
OKTA-380784
In some cases, the security.threat.detected event type in the System Log was missing geographic information when ThreatInsight was enabled.
OKTA-387800
Vanity URLs for deleted users incorrectly included stack trace information with the 404 error.
OKTA-390301
Radius authentication with Duo sometimes failed if Single-line MFA prompts were disabled.
OKTA-391166
The link from the OIN Manager to the OIDC concepts document was broken.
Applications
Application Updates
The catalog descriptions for many OIN app integrations have been updated to improve accuracy and show available capabilities.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Hubspot: For configuration information, see Configuring SCIM Provisioning with OKTA for HubSpot.
OIDC for the following Okta Verified applications
-
Reply.io: For configuration information, see the Reply Okta Configuration Guide.
-
Signicat: For configuration information, see the Signicat Okta Integration Guide (OIDC).
-
K2 Cloud Low-code process automation: For configuration information, see Configuring Okta SCIM integration for K2 Cloud.
-
DPOrganizer: For configuration information, see DPOrganizer – Single Sign-On with Okta.
Weekly Updates
Generally Available
Okta Sign-In Widget, version 5.6.1
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Fixes
General Fixes
OKTA-215049
When an OpenID Connect application was created using a deactivated application's name, a Duplicate Client Name error appeared.
OKTA-374204
End users were incorrectly redirected to the sign-out page if they reset their password through SMS and clicked the Back to Sign In link on the Code Verification page.
OKTA-380326
When an application was edited, the Initiate login URI field was erroneously auto-populated with a default value.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Vantage HCM (OKTA-390470)
-
ISACA (OKTA-391074)
-
ServiceNow (OKTA-390773)
-
Ticketmaster Account Manager (OKTA-390224)
-
United Health Care Member Login (OKTA-390993)
-
Xandr (AppNexus) (OKTA-390469)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Calendly: For configuration information, see How to set up SCIM on Okta.
-
Qualified: For configuration information, see Provisioning Okta SSO Users.
SAML for the following Okta Verified applications
-
Assembly (OKTA-387208)
-
Calendly (OKTA-390432)
-
Crosschq (OKTA-392449)
-
Ground Truth Intelligence (OKTA-385029)
-
ICI App (OKTA-391167)
-
Kaonavi (OKTA-389262)
-
Listrak (OKTA-386611)
-
MaestroQA-Enterprise (OKTA-393110)
-
Malt (OKTA-389581)
-
Officebooking (OKTA-389582)
-
QueryPie (OKTA-388315)
-
Webcasts.com Admin (OKTA-391005)
OIDC for the following Okta Verified applications
-
Axway - AMPLIFY Platform: For configuration information, see Configuring an OpenID Connect (OIDC) IdP.
-
ICI App: For configuration information, see ICI OKTA OIDC App Configuration Guide for OIDC.
-
Noticeable: For configuration information, see Configuring Okta Single Sign-On with OpenID Connect.
-
ReeferConnect: For configuration information, see ORBCOMM ReeferConnect Okta Configuration Guide.
-
Sheetgo: For configuration information, see the Sheetgo Okta configuration guide.
Generally Available
Okta Sign-In Widget, version 5.6.3
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Fixes
General Fixes
OKTA-362581
End users who attempted to sign in to the new Okta End-User Dashboard while access was prevented were not redirected to the proper error page.
OKTA-369101
Admins couldn't save login mappings for some OIDC Identity Providers.
OKTA-376269
When some users updated their recovery question, the password import inline hook was erroneously triggered.
OKTA-379913
Admins couldn't use the Tab key to advance to the next text field in the Test Delegated Authentication modal.
OKTA-383803
Creating new users in Coupa through Okta provisioning failed with a password length error even though the Sync password option was not selected.
OKTA-386927
The Light Agent role was not available to the users assigned to the Zendesk app.
OKTA-387820
The Current Assignment report in Application Access Audit sometimes failed to load and returned a 500 error.
OKTA-389874
The Client Credentials Flow could not implement a custom claim named scope.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
1Password Business (OKTA-392758)
-
Concur - ProTrav (OKTA-394860)
-
Cradlepoint NetCloud (OKTA-392389)
-
Lifeworks (OKTA-395025)
-
SAP Concur Solutions (OKTA-395184)
-
The Washington Post (OKTA-393397)
Applications
Application Updates
The following SWA integrations are deprecated from the OIN:
-
Mindtickle - Admin
-
Lead Apparel
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Icertis Contract Intelligence App: For configuration information, see Configuration Guide for SCIM Integration.
-
WordPress SSO with SCIM Provisioning: For configuration information, see Okta User Provisioning Into WordPress Using SCIM Standard.
SAML for the following Okta Verified applications
-
Acronis Cyber Cloud (OKTA-393653)
-
Emerge (OKTA-393802)
OIDC for the following Okta Verified applications
-
Authress: For configuration information, see the Authress Okta integration guide.
-
Hip For Business: For configuration information, see the Hip Okta Configuration Guide.
Generally Available
Sign-In Widget, version 5.6.4
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Sign-In Widget Guide.
Content security policy enforcement on end-user pages
Content security policy is now enforced for end-user pages. Content Security Policy headers provide an additional layer of security that helps to detect attacks such as cross-site scripting and data injection by ensuring browsers know what kind of actions the webpage can execute. We already had a policy enforced in our admin pages from last year and in report-only mode for end-user pages. We plan that future iterations of our Content Security Policy enforcement for end-user pages will become stricter than this first release.
This feature will be gradually made available to all orgs.
Fixes
General Fixes
OKTA-330390
On the Onboarding tasks page, the Create an app integration task wasn’t marked Complete after an OIDC or OIN app was added.
OKTA-363972
The RelayState value sent from Jira on-prem to Okta was invalid.
OKTA-378981
SAML requests and responses weren't logged in the System Log as distinct event fields and lacked detail about the SAML assertion.
OKTA-385091
Attempts to push blank values from Okta to any custom app attributes in Google Workspace failed.
OKTA-386112
Imports of more than 2,000 users from Adobe Experience Manager sometimes failed.
OKTA-390477
Suspended users were automatically unlocked but appeared as suspended in the Admin Console.
OKTA-393682
Automatic provisioning of users to Google Workspace sometimes failed with a java.io.IOException error.
OKTA-396391
Some Internet Explorer users received a ScriptError alert when signing in to apps.
OKTA-398081
If the users and groups in an app-level policy were deleted, the Admin Console incorrectly showed the policy as applied to all users and groups.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Airbnb (OKTA-395954)
-
Boxed (OKTA-396919)
-
CultureIQ (OKTA-396932)
-
Eden (OKTA-395029)
-
Fortune (OKTA-395031)
-
Gong (OKTA-394257)
-
Granite Rock Reports (OKTA-393958)
-
LivePerson Expert (OKTA-390448)
-
Moffi (OKTA-395032)
-
MURAL (OKTA-395023)
-
Notion (OKTA-395035)
-
Odoo (OKTA-394706)
-
Traackr (OKTA-396931)
Applications
Application Updates
The following SWA integrations are deprecated from the OIN:
-
EverFi NEXT
-
AppNexus (replaced by Xandr)
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
Sisense for Cloud Data Teams: For configuration information, see Sisense SCIM documentation.
SAML for the following Okta Verified applications
-
iHASCO Training Suite (OKTA-396044)
-
Mursion (OKTA-394726)
-
PoliteMail (OKTA-393990)
-
Soveren (OKTA-389257)
-
Writer.com (OKTA-393658)
SWA for the following Okta Verified applications
-
IDEE MFA (OKTA-393819)
-
Xandr (OKTA-394701)
OIDC for the following Okta Verified applications
-
Clozd: For configuration information, see Configure OIDC for authentication with Okta.
-
Impero: For configuration information, see How do I use Okta to log in to Impero?
-
Koopid AI: For configuration information, see How To Setup Okta Single Sign-On Integration.
April 2021
2021.04.0: Monthly Production release began deployment on April 12
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Okta Active Directory agent, version 3.6.1
This version of the agent contains:
-
Improved query performance for customers with a large number of organizational units.
-
Security enhancements.
-
Improved logging functionality to assist with issue resolution.
-
Managed service account support for the Okta Active Directory agent.
-
Bug fixes.
New operators available in Advanced Filters for System Log
Admins can now filter using new Advanced Filters operators:
-
ends with
-
not equal
-
is present (value exists)
-
greater than
-
greater than or equal to
-
less than
-
less than or equal to
Additionally, admins can now use the not equal, ends with, and is present operators in the System Log search bar. These operators provide greater flexibility when filtering System Log events. See System Log filters and search.
Admin Experience Redesign
With the Admin Experience Redesign feature, the Okta Admin Console now has:
-
A modern look and feel with improved responsiveness for the new navigation side bar.
-
A redesigned Okta Admin Dashboard that displays more practical insights for admins.
-
An Agents page in the Okta Admin Dashboard that shows the status and version of every Okta agent that is connected to customers' on-premises servers.
This improves the accessibility of the product, improves admin productivity, and helps admins to be more proactive with security issues.
Okta Applications
Okta admins can now create app-based sign-on policies for the Okta Dashboard, Okta Admin Console, and Okta Browser Plugin.
Previously, sign-on policies couldn't be configured for these first party applications. With this release, policy based on context such as user location, device, behavior, risk level, group membership, and more is included. This gives admins more flexibility and granular control over sign-on requirements for these first party apps. For example, different MFA requirements might apply to the Okta Admin Console for different groups of people.
See Control access to the Okta End-User Dashboard.
Generally Available Enhancements
TLS certificate update for okta.com
The TLS certificate for okta.com will be updated beginning on May 6th, 2021, US Pacific Time. The updated certificate will be signed with a new trust chain and Root Certificate Authority (CA) trust anchor. The Root CA will change from the DigiCert High Assurance EV Root CA to the DigiCert Global Root CA. To avoid negative impact and service outages, customers who have a limited or non-standard set of certificates in their trust stores must take action prior to May 6th, 2021. See FAQs.
Email notification settings
Email notification settings for New sign-on, MFA enrolled, and MFA reset are no longer enabled by default for new orgs. This change prevents new orgs from unintentionally sending email notifications to end users. See General Security.
NetSuite integration enhancement
Okta can now import the supervisor/manager ID for an employee from NetSuite, removing the dependency on Active Directory.
OIN Manager supports variable SAML ACS URLs
SAML app integrations that support multiple ACS URLs can now use app instance property variables to create non-static single sign-on URLs in their submissions.
Okta ThreatInsight free trial
Orgs that use free trial editions now see a limited functionality notification in the Okta ThreatInsight Settings section of the Security > General page. See General Security.
End users on new dashboard can request apps
End users can now request an app through the link in the footer of the new Okta End-User Dashboard. To turn this setting on, go to the Okta Admin Console > Applications > Self Service and enable Allow users to email "Technical Contact" to request an app.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-336939
For some orgs, the user activation page didn't display logos correctly if it was accessed through the redirect link in the User Activation email.
OKTA-337030, OKTA-375978, OKTA-378809, OKTA-379613, OKTA-380069, OKTA-380636, OKTA-381076, OKTA-381639
Some orgs that have the Admin Redesign Experience feature enabled had the following issues:
-
Scrolling functionality didn’t work as expected on some pages.
-
The Okta Admin Dashboard reached the rate limit threshold rapidly, causing a failure to load data in the Admin Dashboard widgets.
-
The spotlight search input field had extra padding.
-
Some pages had layout issues.
-
Some dialog boxes had unwanted scrollbars.
-
Some conditions in group rules were unreadable.
-
Group icons weren't display properly on the Group Assignment page.
OKTA-362647
Self-Service Registration incorrectly appeared in the Directory menu for group admins. This feature is available to super admins only.
OKTA-363849
The 12-hour timestamp on the Import Monitoring Dashboard didn’t display AM or PM.
OKTA-369992
The Report Suspicious Activity page didn’t display the geolocation and the IP address of the suspicious request.
OKTA-373689H
Sometimes the public OAuth metadata API responses did not include a Vary: Origin header, resulting in some browsers incorrectly caching the response across Origins.
OKTA-373957
Some iPhone and iPad users using Okta Mobile couldn’t sign in to Microsoft Teams.
OKTA-375702
The Okta Workflows app erroneously counted towards an org's app limit.
OKTA-375878
The Import Safeguard help documentation link on the Directories page was broken.
OKTA-376041
Some pop-up messages during the OAuth validation process incorrectly had scrollbars.
OKTA-376281
During creation of a new SPA app integration, the App Integration Wizard incorrectly enabled the Allow Access Token option under the Implicit grant type by default.
OKTA-376795
Registration Inline Hook sometimes failed during the self-service registration process.
OKTA-378045H
The Applications page in Developer orgs didn't have clear instructions about how to create more custom apps by upgrading to an Enterprise plan.
OKTA-378989
For some orgs, SAML inline hooks didn’t work as expected.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
AlertLogic (OKTA-380563)
-
Blacklane Car Service (OKTA-380186)
-
Bookmark App (OKTA-377640)
-
DHL Express (OKTA-380565)
-
Fortune (OKTA-380576)
-
ImpactOffice (OKTA-380575)
-
Music Vine (OKTA-380580)
-
mySE: My Schneider Electric (OKTA-375671)
-
Tumblr (OKTA-380562)
-
WordFly (OKTA-380953)
The following SAML app was not working correctly and is now fixed
-
Mimecast Personal Portal v3 (OKTA-381518)
Weekly Updates
Generally Available Features
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Generally Available Enhancements
Password Health Report enhancement
Date columns in the Password Health Report are now in ISO 8601 format to improve readability.
Increased authorization code lifetime
The OAuth authorization code lifetime is increased from 1 to 5 minutes.
Fixes
General Fixes
OKTA-360669
Errors on the App Sign On Policy page were displayed at the top of the page rather than near the respective fields.
OKTA-360937
In some cases, Okta didn't import all users from ServiceNow.
OKTA-362325
Attributes with the number data type were reported to have been updated after CSV Directory imports even if nothing had changed.
OKTA-362647
Self-Service Registration, a super admin feature, incorrectly appeared in the Directory menu for group admins.
OKTA-375536
Developer org admins were incorrectly redirected to the user app page instead of the Admin Dashboard.
OKTA-375698
In some cases, the OAuth access token for Salesforce expired daily, which caused issues with provisioning.
OKTA-377265
In some cases, admins received a 500 error while creating a new user with JIT provisioning.
OKTA-380356
The Trusted Origin field in the new App Integration Wizard appeared even if the user didn't have the permission to manage the field.
OKTA-380892
Some help documentation links in the Agentless Desktop SSO and Silent Activation section didn't work.
OKTA-382214
In some cases, Group Administrators were incorrectly displayed as User Administrators in the Email Notification dropdown on the Account Settings page.
OKTA-382433
The text in the App Embed Link section of the Custom SAML App page was misaligned.
OKTA-385342
The new App Integration Wizard showed an error when creating an API Services app due to incorrect response type validation.
OKTA-388027
The Email Change Confirmed Notification configuration (part of Email & SMS Customization) didn’t have an option to specify whether admins only, or admins and end users received the notification.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Carta (OKTA-380324)
Applications
Updates
-
The Nature.com SWA integration is deprecated from the OIN.
Use the Nature Research SAML app instead.
New Integrations
SAML for the following Okta Verified applications
-
Productive.io (OKTA-377469)
-
TigerConnect (OKTA-382369)
OIDC for the following Okta Verified application
- Tera: For configuration information, see Logging in with Single Sign-On (SSO) through Okta.
Generally Available
Okta Sign-In Widget, version 5.5.4
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Fixes
General Fixes
OKTA-355894
The Recently Used tab on the Okta End-User Dashboard wasn't translated for all languages.
OKTA-361861
During a full import, profile updates occurred in Workday even if no attributes were changed for the user in Okta.
OKTA-369527
AD-sourced users received misleading error messages when they attempted to reset their passwords while the AD agent was down.
OKTA-371158
Some LDAP-sourced users' temporary passwords became their main passwords after they used them to sign in.
OKTA-373409
Some AD-sourced users were redirected to the default Okta org when they clicked the activation link in their welcome email.
OKTA-373578
Some Dynamic Network zones didn't block traffic as configured.
OKTA-375317
Some users received errors when they authenticated to Okta from ADFS with a custom domain.
OKTA-376991
After reactivation, some users weren't properly reassigned their applications.
OKTA-377853, OKTA-379764
International phone numbers were incorrectly parsed during profile updates in Workday.
OKTA-378405
Pushing AD-imported groups from one Okta instance to another failed.
OKTA-379707
The ThreatSuspected field in the System Log wasn’t consistently updated.OKTA-380165
Previously scheduled Workday imports were still shown on the Import Monitoring dashboard after provisioning was disabled.
OKTA-381764
Some admins couldn't save settings for Incremental Import Schedule when they integrated a new CSV Directory.
OKTA-382686
The Upload CSV button wasn't clearly visible on the Application Import page of the new Okta Admin Console.
OKTA-382711
Syntax highlights were not correct in the Okta Admin Console code editors for the Custom Sign-In Widget and the Custom Error pages.
OKTA-383630
Preview and test emails in the Okta Admin Console didn’t render customization variables in the email subject field.
OKTA-383632
After a custom domain was configured, the test email dialog in the Okta Admin Console displayed the default email sender details as Okta <noreply@okta.com>.
OKTA-383647
Admins received timeout errors when they deactivated AD-sourced users through imports from Active Directory.
OKTA-384306
Icons in the Okta API Scopes tab were misaligned for OAuth apps.
OKTA-385297
Text on the Sign On tab was misaligned for some apps.
OKTA-389502H
In some cases when the new Okta End-User Dashboard was enabled, Okta incorrectly made hourly token renewal requests that caused user sessions to be active longer than configured.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Accertify (OKTA-388719)
-
Adobe (OKTA-385008)
-
ADP IPayStatements (OKTA-389106)
-
Apollo (OKTA-382989)
-
Beeline TMS (OKTA-383007)
-
Calendly (OKTA-382474)
-
Citi Credit Cards (OKTA-385007)
-
Cradlepoint NetCloud (OKTA-388566)
-
Delta Dental (OKTA-379327)
-
Dow Jones Private Equity and Venture (OKTA-388720)
-
Federal Procurement Data System (OKTA-382991)
-
Grammarly (OKTA-388717)
-
Jitterbit (OKTA-385006)
-
KeyBank (OKTA-385011)
-
LastPass Sync (OKTA-386955)
-
Milestone XProtect Smart Client (OKTA-386601)
-
MongoDB Cloud (OKTA-385010)
-
Portal Nutanix (OKTA-386598)
-
Shatswell MacLeod (OKTA-386604)
-
WEX Health Cloud (OKTA-385013)
-
WorkFlowy (OKTA-386597)
-
XpertHR (OKTA-382990)
-
ZeeMaps (OKTA-388718)
Applications
Application Updates
-
Our Dynamic Signal integration has been updated as follows:
-
The existing Dynamic Signal integration is deprecated and renamed Dynamic Signal (Deprecated).
-
A new Dynamic Signal integration is now available, without provisioning functionality.
-
-
The following SWA integrations are deprecated from the OIN:
-
Crazy Egg
-
Dow Jones Private Equity and Venture
-
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- BombBomb: For configuration information, see Configuring user provisioning with Okta.
- Cato Networks Provisioning: For configuration information, see Cato Networking documentation here. Note that this documentation is only available for Cato authenticated users.
- Dooly: For configuration information, see Configure user provisioning with Okta.
- eFront: For configuration information, see Configure SCIM with Okta.
- Exium: For configuration information, see Integration with OKTA SCIM.
- Mantra: For configuration information, see Okta SCIM Provisioning.
- Thrive LXP: For configuration information, see Configuring User Provisioning in the Thrive LXP Okta App.
SAML for the following Okta Verified applications
-
brandworkz (OKTA-380978)
-
Dooly (OKTA-384467)
-
Feroot (OKTA-387002)
-
Folia (OKTA-369123)
-
Jobcan (OKTA-383754)
-
JoVE (OKTA-386197)
-
LINE WORKS (OKTA-387869)
-
MPulse 9 (OKTA-379463)
-
Open Practice Solutions (OKTA-379650)
-
Planisware Enterprise (OKTA-382573)
-
Propel PRM (OKTA-385027)
-
QReserve (OKTA-383759)
-
Thrive LXP (OKTA-385858)
-
Webcasts Admin (OKTA-382549)
SWA for the following Okta Verified applications
-
Atlanta Fine Homes (OKTA-383598)
-
Walkthechat (OKTA-385436)
-
WSRB (OKTA-385426)
OIDC for the following Okta Verified applications
-
BombBomb: For configuration information, see How Do I Configure the OpenID Connect Plugin to Work With Okta.
-
Internal OpenID Connect: For configuration information, see Okta Open ID Connect.
-
Mantra: For configuration information, see Okta SSO.
-
Palo Alto Networks Cloud Identity Engine Directory Sync: For configuration information, see Learn About Directory Sync.
-
Postalio: For configuration information, see Connecting With Okta.
-
Verint Community: For configuration information, see How to configure Single Sign On (OIDC) with Okta.
March 2021
2021.03.0: Monthly Production release began deployment on March 8
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
LDAP agent, version 5.7.2
This version of the agent contains:
-
Support for Lightweight Directory Access Protocol (LDAP) group password policies
-
Internal improvements and security fixes
-
Bug fixes
To view the agent version history, see Okta LDAP Agent version history.
RADIUS Agent, version 2.15.1
RADIUS agent version 2.15.1 GA contains all updates release since version 2.7.4 EA, including:
-
Support for EAP-GTC and EAP-TTLS to improve security and extend support network access vendors, such as Netmotion Mobility.
-
Support for TLS 1.2, which is required for all connections to Okta.
-
Support for internet proxies.
-
A simplified installer, which no longer requires shared secrets and ports.
And has been tested on new Linux operating systems:
-
CentOS 7.6.
-
Ubuntu 20.04.1 LTS.
-
Red Hat Enterprise Linux release 8.3.
-
Windows Server 2016.
-
Windows Server 2019.
In summary, the new agent provides admins with an easier installation, configuration, and run-time experience, and we recommend it for all Okta RADIUS customers.
Okta Sign-In Widget, version 5.4.0
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
New number challenge options in Okta Verify admin settings
New Okta Verify settings in the Admin Console now allow admins to control when users receive a number challenge. Number challenge is an existing Okta Verify feature in eligible orgs that helps Android and iOS users enrolled in Okta Verify with Push avoid accepting fraudulent push notifications when they try to access a protected app. Completing the challenge ensures that the sign-in attempt came from the user and not from an unauthorized person. Admins can now choose to never challenge users, challenge with all push notifications, or challenge only for high-risk sign-in attempts. See Push Notification and Number Challenge.
Option to switch between Admin Experience Redesign and the old experience
Super admins can now switch between Admin Experience Redesign and the old experience by using the option provided on the Okta Admin Dashboard. This gives admins time to adapt to the new user experience, which is on by default, and the option to revert to the old experience if required.
OIN Catalog enhancements
The OIN catalog adds several customer identity categories, highlights key app integrations, and now shows relevant Okta Workflow connectors and templates. Administrators can click Add integration to add a specific app integration directly to their org. These improvements make it easier for administrators and application developers to learn about Okta’s customer identity integrations. They can browse for relevant integrations like social identity providers and identity proofing solutions and add these integrations to their Okta org.
This feature will be gradually made available to all orgs.
Deleted schema property scrubber
All existing data associated with a schema property is now removed when a schema property is deleted. To prevent data corruption, the property cannot be recreated until the existing data is fully removed. Previous data is no longer restored when recreating a deleted schema property with the same definition. This new functionality prevents the corruption of profile data and the associated Elastic search issues. See Add or remove custom directory schema attributes.
This feature will be gradually made available to all orgs.
OIDC App tab improvements
The following improvements have been made to the OIDC App tab:
-
The default tab is now General instead of Assignments.
-
Client Credentials moved to the top of the page.
-
Downloaded sample apps now have pre-populated environment variables.
See Create OIDC app integrations using AIW.
This feature is available for all new Production orgs.
LDAP self-service password reset
End users can now perform a self-service reset of their LDAP password using SMS (Short Message Service). Without compromising security, this functionality simplifies the password reset process and removes the need to involve IT Help Desk for credential management. Using SMS for password resets reduces the Help Desk workload and support costs. See Manage self-service password reset.
Improved auto-complete functionality
To improve the accuracy and speed of user searches, the auto-complete functionality on the Okta Admin Console administrator pages is updated.
Generally Available Enhancements
Improvements to the OIN Manager submission QA process
The Okta Operations team now conducts a final internal QA test for app integration submissions in the OIN Manager Portal and sends an email when the final review is complete. If the review is successful, your submission is automatically published in the OIN. These changes streamline the QA and approval process for OIN app integrations.
OIN Manager additional fields
The OIN Manager portal now accepts encrypted SAML assertion certificates. Also, fields are added to clarify OIDC configuration requirements and to confirm that SCIM app integrations are prepared properly for submission. See Configure protocol-specific settings. These changes simplify the ISV submission process, reducing unnecessary communications with the Okta Operations team.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-209671
Updating a user address field with a string that was too long returned a 500 error response instead of a 400 error with appropriate details.
OKTA-335776
In rare cases when an admin re-typed their password in the Office 365 Admin Password field and then clicked Fetch and Select on the Sign On tab, the Fetch and Select command failed with an error.
OKTA-336326
Sometimes, when the Office 365 Provisioning option was selected to Licenses/Roles Management Only, roles and licenses assigned to Office 365 users in Okta didn't sync in Microsoft.
OKTA-346766
Text on some AD Import pages in the new Okta Admin Console was misaligned.
OKTA-352294
Workday incremental imports sometimes failed with a NullPointerException error.
OKTA-359091
Expanding Admin Tasks on the Admin Dashboard changed the index value of the tasks.
OKTA-367327
When IDP as Factor was enabled, some users received the Invalid Token error on stale sign-in pages.
OKTA-367834
The QR code image in the Setup Okta Verify flow didn't include alt text, which caused screen readers to not recognize the image.
OKTA-367844
The SCIM provisioning feature was not enabled for the Lifecycle Management SKUs included with API products.
OKTA-367999
Some end users were stuck in an authentication loop when trying to sign in to Okta.
OKTA-370037
Text on some pages in the new Okta Admin Console was misaligned.
OKTA-371599
Text on the LDAP tab of the Delegated Authentication page was not rendered properly.
OKTA-372049
Text on the Sign On tab of the App Settings page was misaligned.
OKTA-372436
An issue with ThreatInsight was resolved for some organizations who upgraded a free trial edition to Production.
OKTA-372678
Sometimes the sign-in page didn't refresh if the token was expired.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Aflac (OKTA-372087)
-
Alarm (OKTA-372091)
-
CBRE (Employee Login - The Navigator) (OKTA-370216)
-
Frontier Communications (OKTA-370218)
-
GoCompare (OKTA-370219)
-
MX Merchant (OKTA-370217)
-
MxToolbox (OKTA-370503)
-
Premium Audit Advisory Service (PAAS) (OKTA-368399)
-
Rippe and Kingston LMS (OKTA-372081)
-
ShopAtHome (OKTA-372067)
-
The Economist (OKTA-372207)
-
Visage MobilityCentral (OKTA-372095)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Banyan Command Center (OKTA-370640)
-
Five9 Plus Adapter for Microsoft Dynamics CRM (OKTA-367992)
-
Noticeable (OKTA-370631)
SWA for the following Okta Verified application
-
Clarizen One (OKTA-371928)
OIDC for the following Okta Verified application
-
AFAS by FuseLogic: For configuration information, see Configuring OpenID Connect for AFAS.
Weekly Updates
Fixes
General Fixes
OKTA-337155
Sometimes, if a refresh token flow contained an invalid refresh token, the hash was not logged in the System Log.
OKTA-340754
In some cases, users couldn't be assigned to or removed from a group from their Okta Profile.
OKTA-347379
The Okta Browser Plugin incorrectly suggested a new password for the ServiceNow app.
OKTA-362310
The Dutch translation for password requirements on the password reset screen was incorrect.
OKTA-369737
Search boxes on some pages under Security had a CSS issue.
OKTA-370192
Some admins couldn't create users for Box if the default input value for the parent folder path was left empty in Okta.
OKTA-370944
In some cases, after a user deletion legitimately failed, admins were unable to delete other users.
OKTA-378843H
Invalid token requests resulted in a 500 error.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Benchmarking (OKTA-375324)
-
Forbes (OKTA-372724)
-
Fusion MortgagebotLOS (OKTA-373862)
-
Google Workspace (OKTA-374871)
-
Hawaiian Airlines (OKTA-375320)
-
Papertrail (OKTA-375327)
-
Pingdom (OKTA-375323)
-
Schwab Advisors (OKTA-358544)
-
Taboola (OKTA-371937)
-
WorkdayCommunity (OKTA-374314)
-
Zapier (OKTA-374811)
-
Zoom (OKTA-372449)
Applications
Application Updates
Our OrgWiki integration has been updated as follows:
-
The existing OrgWiki integration is renamed OrgWiki (Deprecated).
-
Customers should now use the OrgWiki (SCIM) integration in our catalog.
New Integrations
SAML for the following Okta Verified applications
-
Admin By Request (OKTA-372458)
-
Fortanix Self Defending Key Management Service (OKTA-373374)
-
Taskize Connect (OKTA-369898)
Generally Available Features
Okta Sign-In Widget, version 5.4.3
For details about this release, see the Sign-In Widget Release Notes.
For more information about the Widget, see the Okta Sign-In Widget Guide.
Fixes
General Fixes
OKTA-297743
Apps weren't highlighted automatically if they matched a user’s search terms in the App Catalog.
OKTA-319109
In orgs with the Admin Experience Redesign feature enabled, the Imports Paused task was missing from the Dashboard page in the Okta Admin Console.
OKTA-345217
Some user interface elements on sign-on policy pages for apps were formatted incorrectly.
OKTA-355148
LDAP-sourced users received a 500 error error while attempting a self service password reset that violated common password patterns.
OKTA-362677
In orgs with the Admin Experience Redesign feature enabled, when admins clicked Workflow > Workflow console, the page didn't open in a new browser tab.
OKTA-368354H
Some Adobe Experience Manager imports failed.
OKTA-370306
The side navigation in the Okta Admin Console didn't scroll automatically to a selected item.
OKTA-371058
In some cases, users experienced performance issues on the Okta End-User Dashboard and had to refresh the page manually.
OKTA-372440
The Add Section button was missing from the new Okta End-User Dashboard app list when embedded in an iframe.
OKTA-373004
The Upload button for Encryption Certificates was missing from the Sign-On settings tab in the Okta Admin Console.
OKTA-373729
In some cases, importing users from Active Directory to Okta failed and app assignment didn't complete if a single user failed to import.
OKTA-373944
In orgs with the Admin Experience Redesign feature enabled, admins who didn't have search permissions could see the search box in a deactivated state.
OKTA-375432
In some cases, the onboarding checklist for new developer orgs wasn't populated correctly upon registration.
OKTA-375541
Some app sign-on policy pages had display issues.
OKTA-375953
Smart Card authentication failed if an org had multiple Smart Card Identity Providers (IdPs) configured.
OKTA-375998
The Help documentation link on the Active Directory introductory page redirected users to the wrong documentation page.
OKTA-376620
The error message shown to end users when the login page had an expired token was unclear.
OKTA-379196
End users that belonged to environments without the new Okta End-User Dashboard self-service feature enabled were presented with a blank page after signing onto a custom domain.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Domo (OKTA-373343)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Communifire: For configuration information, see Okta SCIM Configuration Guide.
-
Gamesight: For configuration information, see Okta SCIM Configuration.
-
Lucid: For configuration information, see Okta SAML and SCIM Integration.
-
Taskize Connect: For configuration information, see SCIM Configuration Guide for Okta with Taskize.
-
TelemetryTV: For configuration information, see Configuring SCIM for TelemetryTV with Okta.
SAML for the following Okta Verified applications
-
JustCall (OKTA-375104)
-
Rent Dynamics (OKTA-373350)
-
Roadster (OKTA-359604)
-
Vonage (OKTA-373104)
EA Enhancement
Dashboard and Browser Plugin apps available in Admin Console
Admins of the orgs that have enabled the new Okta End User Dashboard and First Party Applications can now see the Okta Dashboard and Okta Browser Plugin apps in Okta Admin Console > Applications. They can also set up sign-on policies for these apps. See Control access to the Okta End-User Dashboard. This feature will be gradually made available to all orgs.
Fixes
General Fixes
OKTA-333391, OKTA-362811, OKTA-372138, OKTA-372662, OKTA-372959, OKTA-375504, OKTA-375682, OKTA-375977, OKTA-376890, OKTA-376908, OKTA-376985, OKTA-376988, OKTA-377189
Orgs with the Admin Experience Redesign feature enabled had the following issues on some pages:
- Text or UI elements were misaligned or didn’t wrap correctly.
- Drop-downs didn’t work properly.
- Old UI elements replaced the new ones.
- Font or font color was inconsistent.
- The scroll functionality didn’t work properly.
OKTA-354628
The RADIUS app didn't have a configuration option to permit MFA-only configuration to allow access-challenge responses.
OKTA-372692
If multiple users matching a UPN or SAM Account Name existed, the authentication process failed even if only one of those users was assigned the RADIUS app.
OKTA-373288
In rare cases, during multifactor authentication (MFA) enrollment with SMS as a factor, users could have multiple unverified phone numbers and weren't able to verify any of them.
OKTA-373963
Group memberships were still being synced to an app even when API integration for the app was disabled.
OKTA-377201
After the local numbers were changed to 10 digits, users in Ivory Coast enrolling in SMS and Voice Call authentication received a warning about the phone numbers not being valid, and they had to retry the same number to complete the enrollment.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Azure Manage (OKTA-377470)
-
Baystate Benefits - Employee (OKTA-377235)
-
Brainerd Dispatch (OKTA-377232)
-
Chase Bank - Personal (OKTA-377215)
-
Domo (OKTA-377226)
-
GuideStar (OKTA-377224)
-
IBM Blueworks Live (OKTA-377219)
-
IntraLinks (OKTA-377496)
-
Iola (OKTA-377217)
-
Jack Henry & Associates Client Portal (OKTA-377212)
-
Lucidchart (OKTA-376367)
-
SAP Concur Solutions (OKTA-375460)
-
Skykick (OKTA-377845)
-
Staples (OKTA-377474)
-
Texas Mutual (OKTA-355698)
-
The Information (OKTA-372438)
-
TSheets QuickBooks (OKTA-372937)
Applications
Application Updates
-
The Fastly application is now private and is renamed Fastly (Deprecated)
-
The Signal Sciences application is now private is renamed Signal Sciences (Deprecated)
-
The Fastly SAML is renamed Fastly and is updated with SWA Sign On mode.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
GitHub Enterprise Managed User: For configuration information, see Configuring Provisioning for GitHub Enterprise Managed User.
SAML for the following Okta Verified applications
-
EVA Voice Biometrics (OKTA-379067)
-
FortiSASE SIA (OKTA-379066)
-
GitHub Enterprise Managed User (OKTA-379065)
-
IDrive360 (OKTA-378511)
-
Lucid (OKTA-377238)
-
SecureFlag (OKTA-377229)
February 2021
2021.02.0: Monthly Production release began deployment on February 8
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Option to activate and deactivate rate limit warning and violation notifications for all orgs
All admins now receive the warning and violation notifications for rate limits. Additionally, you have the option to activate and deactivate the notification from the Admin Console.
Additional events available for use as Event Hooks
The following event types are now available for use as an Event Hook:
- The
user.account.lockevent makes admins aware of accounts that are locked because of suspicious activity or due to multiple incorrect sign-in attempts. Admins can also use this Event Hook to take action against affected accounts. - The
user.account.unlockevent makes admins aware of accounts that are no longer locked. Admins can also notify users of appropriate next steps to prevent future account locking. - The
group.lifecycle.createevent notifies admins when new Okta groups are created. Thegroup.lifecycle.deleteevent notifies admins when new Okta groups are deleted. Admins can use Event Hooks based on these events to initiate automated custom flows. - The
system.org.rate.limit.warningevent notifies admins when their org is approaching an org-wide rate limit. Thesystem.org.rate.limit.violationevent notifies admins when their org has exceeded an org-wide rate limit. Admins can use Event Hooks based on these events to trigger a real-time alert to a downstream system, such as PagerDuty. - The
system.import.group.createevent helps admins to automate IT processes, such as providing members of the imported group with access to applications. - The
system.import.group.deleteevent helps admins use these events to trigger actions in downstream systems, such as an Okta Workflows Flow that creates a Slack notification. - The
user.mfa.factor.suspendanduser.mfa.factor.unsuspendevents notify your service when enrolled MFA factors are suspended or unsuspended. This typically occurs when a registered device associated with the factor is suspended or unsuspended either through the Okta Admin Console or the Okta API.
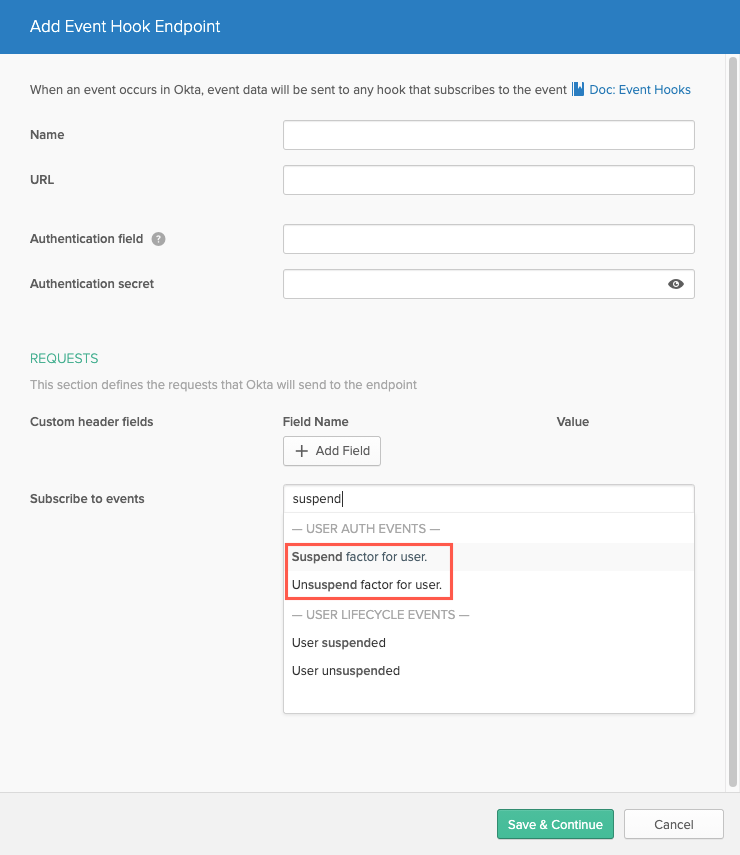
New System Log events for MFA factor activity and for importing users through CSV
The following System Log event types are now available:
-
The system.mfa.factor.activate event indicates that the MFA factor is activated.
-
The system.mfa.factor.deactivate event indicates that the MFA factor is deactivated.
These events help admins collect metrics for MFA factor activity and track user action for activating and deactivating an MFA factor. These events are triggered when an MFA factor is activated and when it is deactivated.
-
The system.import.user_csv.start event indicates that the process to import users from CSV is started.
-
The system.import.user_csv.complete event indicates that the process to import users from CSV is completed.
These events help admins track user activity of batch importing users through CSV. These events are triggered when the process to import users from CSV is started and when it is completed.
Support for Safari user interaction requirement for WebAuthn flows
Okta now supports Safari's user interaction security requirement for WebAuthn flows. When accessing resources protected by an Okta WebAuthn MFA policy, end users now must tap Verify before they're challenged to provide biometrics or a security key.
General Availability of Workflows
Okta Workflows is now Generally Available for additional customers in the APAC cell.
Okta Workflows is an interface-driven, no-code platform for business process automation that provides integration with some of the most widely used third-party APIs in the industry, including Box, Slack, Salesforce, and Google Workspace. See Okta Workflows.
Deployment is taking place over the course of several days to entitled orgs with the following SKUs:
-
IT Products - Advanced Lifecycle Management
-
Legacy SKU: IT Products - Lifecycle Management, Unlimited
-
Legacy SKU: IT Products - Lifecycle Management, Unlimited OIN Apps
-
Legacy SKU: IT Products - Lifecycle Management, 10 OIN Apps
To access Workflows, select the Workflow > Workflows console menu option from the Okta Admin Console.
Limit group stats when searching for user groups during admin assignment
In search results, groups with more than 10,000 users or apps now appear with a count of 10,000. This speeds up results when super admins search for groups to assign admin privileges. The actual totals are not impacted and can be viewed on the group's page.
New System Log delAuthTimeout and LDAP delAuth values
The following values now appear in the System Log:
-
The
delAuthTimeoutvalue identifies the authentication timeout value. The delegated authentication timeout value is the time in milliseconds that Okta waits for delegated authentication responses. Knowing this value can help identify when timeout values are too high and consuming system resources unnecessarily. See System Log. -
The
Ldap delAuthvalue identifies the delegated authentication type. The values returned are LDAP or AD. Knowing this value can help you identify and resolve delegated authentication issues. See Delegated authentication.
Generally Available Enhancements
Admins only receive rate limit warning and violation notifications for org events
All admins are notified for rate limit warning and violations for their orgs in the Admin Console and by email. These notifications are for org-wide events and not for client and operations-based events. This reduces unnecessary email notifications.
Updates to the text in rate limit warning and violation notifications
The text in the rate limit warning and violations notification in the Admin Console and email has been updated to make it more user-friendly. Now, the email notification also contains a link to the Rate limit overview document to boost your understanding of rate limits. See Rate limits.
Link to Okta agent support policies
The Downloads page in the Admin Console now has a direct link to the latest Okta agent support policies. See Okta agent support policies.
Enhancement to the OIDC app creation message
After an OIDC application is created, the Application created successfully notification is frequently missed because it only appears briefly after an app is saved. The message now appears after the UI redirects to the new application's main page.
Okta Workflows URL verification in Event Hooks
Admins can now enter a Workflow API Endpoint URL as an Event Hook URL without the need for verification. This helps admins easily configure a Workflow to be triggered from an Event Hook for multiple events or for events not yet available in Workflows.
See Event hooks.
Enhancements to policy scheduled execution System Log events
The policy.scheduled.execute event has been updated. When triggered by Okta Automations, this event now displays the number of user lifecycle state changes for deactivations, deletions, and suspensions in the SuccessfulDeactivations, SuccessfulDeletions, and SuccessfulSuspensions fields under the DebugContext object. This event is useful for admins to measure the number of user accounts that have been affected by Okta Automations.
New color scheme for the map view in System Log
The mapview in the System Log now has a new color scheme that increases visibility and clarity.
Early Access Features
New Features
Enhanced Admin Console search
Admins can now search for end user email addresses in the Spotlight Search field in the Admin Console. You can also view the user's status in the search results when you search by username and email address. This robust global search helps you find what you need in the Admin Console quickly, thereby, saving time and increasing productivity. See Admin Console search.
Fixes
General Fixes
OKTA-336933
Some Office 365 users were deprovisioned with an incorrect localization error.
OKTA-347240
During account creation, if a user's input violated the length constraints, the error message didn't include the value of the length constraint.
OKTA-348024
SuccessFactor users weren't deactivated by timezone.
OKTA-351180
SAML Preview returned the 400 Bad Request error if the SAML sign-on mode for an app was configured with Single Logout.
OKTA-353734
Some users who had successfully authenticated received a sign-in failed error when they attempted to sign in to an app that wasn't assigned to them.
OKTA-355854
The Okta Admin Dashboard wasn't properly aligned in Internet Explorer 11.
OKTA-358580
Admins couldn't approve or deny app access requests in the new Okta End-User Dashboard.
OKTA-358736
Resend SMS factor sometimes resulted in a 400 error upon app sign-in.
OKTA-359104
Some base attributes were missing from the User Profile.
OKTA-359189
The Preview banner in Preview orgs wasn't properly displayed.
OKTA-361024
The new Okta End-User Dashboard didn't show all company-managed apps or the Show More button.
OKTA-361741
In an IdP-initiated flow, end users were prompted to verify the IdP factor when they accessed an app even if they'd verified a factor when they signed in to the Okta End-User Dashboard.
OKTA-362034
In some browsers, extra scroll bars appeared on the Okta Admin Dashboard.
OKTA-362764
The Tasks card on the Okta Admin Dashboard didn't load properly in Internet Explorer 11.
OKTA-363398
The Help documentation link under Customization > New End User Experience was broken.
OKTA-364583
In the SmartSheet provisioning profile, when admins tried to change the Group Priority setting to Combine values across groups for the variable smartsheet.userPermissions, the error message: Not allowed to modify property userPermissions from the base schema was returned.
OKTA-366948H
Some imports from AD were delayed, especially when large number of import jobs were being run.
OKTA-367152H
In some cases, MS Office authentication did not prompt for MFA and failed.
Applications
-
The Okta SAML Toolkit is deprecated and removed from the Okta Downloads page.
-
Google Apps is rebranded as Google Workspace. We have updated the OIN Application and associated documentation.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Airbase: For configuration information, see Airbase documentation. (You need to sign in to access this documentation.)
- Proxy: For configuration information, see Configuring OKTA Provisioning for Proxy.
SAML for the following Okta Verified applications
-
TravelPerk (OKTA-362457)
Weekly Updates
Fixes
General Fixes
OKTA-348508
During Okta to Box provisioning, if the Create personal Box folder when new user account is provisioned option was selected, the admin was sometimes added to the folder with the user.
OKTA-350375
Some profiles were not updated when Active Directory (AD) attributes were pushed to custom attributes in Okta.
OKTA-358884
During CSV import, attempts to add and update User Profile attributes failed.
OKTA-359569
During password reset, an incorrect error message was reported if security requirements were not met.
OKTA-360989
Admins couldn't enable the Okta Browser Plugin toolbar for specific groups.
OKTA-361726
In the new Okta Admin Console, the Overview section of the Admin Dashboard didn't reflect the correct last-updated date for reports.
OKTA-362107
A non-functioning Learn More link was displayed under Status in the Agents panel.
OKTA-363845
In the new Okta Admin Console, the number of apps displayed on the dashboard was different from the number of actual apps.
OKTA-365531
The Russian translation for the Show More button in the App Catalog was inaccurate.
OKTA-366755
In Internet Explorer 11, the left navigation menu was missing from the new Okta Admin Dashboard.
OKTA-367191
The word Authenticator was not translated on the new Okta End-User Dashboard or in the security enrollment flow.
OKTA-367776
When using a browser other than Safari to access resources protected by an Okta WebAuthn MFA policy, end users were required to tap Verify before they were challenged to provide biometrics or a security key.
OKTA-370361H
Admins sometimes encountered errors when attempting to update O365 app settings or with provisioning related operations to AAD.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
123RF (OKTA-365452)
-
Avery (OKTA-361758)
-
Chrome River (OKTA-364083)
-
CSI - WatchDOG Elite (OKTA-362468)
-
Exclusive Resorts (OKTA-364063)
-
mySE: My Schneider Electric (OKTA-364080)
-
Nationwide Evictions (OKTA-367116)
-
Notion (OKTA-366913)
-
Skrill (OKTA-366912)
-
SmartyStreets (OKTA-361757)
-
vAuto (OKTA-361755)
-
Visionplanner (OKTA-360707)
-
Wayfair (OKTA-366424)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Slab: For configuration information, see Okta SCIM Integration.
- OpsRamp: For configuration information, see Configuring Provisioning for Okta.
-
Sigma on GCP: For configuration information, see Manage Users and Teams with SCIM and Okta.
SAML for the following Okta Verified applications
-
A Cloud Guru (OKTA-361798)
-
Genesys Cloud (OKTA-362719)
-
Onfido (OKTA-365910)
-
Strings (OKTA-364012)
-
zkipster (OKTA-364003)
Fixes
General Fixes
OKTA-344871
Although the Add Rule button on the Groups page appeared inactive, in some cases users accessed the Add Rule dialog box after clicking the button.
OKTA-345647
3-byte characters weren't readable in the Okta Password Health report.
OKTA-347025
Group admins could view all Okta tenant users and not just the ones in their group.
OKTA-354798
Sometimes, sign-in attempts with Just-In-Time provisioning using LDAP failed with an UNKNOWN_USER error when delegated authentication was enabled.
OKTA-356023
Importing users from SAP Litmos to Okta failed in some cases.
OKTA-358253
The Okta End-User Dashboard didn't display localized content when the web browser's default language was set to Indonesian.
OKTA-360983
Password requirement error messages shown during self-service registration weren't consistent.
OKTA-361189
In the new Okta Admin Console, the My Settings link erroneously redirected to the organization's Settings page instead of the end-user Settings page.
OKTA-364406
When creating a new app integration as part of the developer onboarding experience, users were redirected to the deprecated Okta Developer Console App Integration Wizard, instead of the App Integration Wizard in the Okta Admin Console.
OKTA-365037
Sometimes, Just-In-Time provisioning or Real Time Sync wasn't triggered during Active Directory delegated authentication.
OKTA-365205/OKTA-366761
Some pages in the new Okta Admin Console didn't display properly in Internet Explorer 11.
OKTA-365925
Sometimes, admins received a 500 Internal Server Error when they deleted a user.
OKTA-367666
When creating a new SAML 2.0 app integration, the Attribute Statement heading in the wizard wasn't grouped with the corresponding input fields.
OKTA-367941
On the Create OpenID Connect App Integration page in the Okta Admin Console, the yellow bar was missing from the side note.
OKTA-368138
In the new Okta Admin Console, removed app instances were identified as agent down on the Dashboard > Agents page.
OKTA-368828
In the new Okta Admin Console, selected child pages were sometimes not highlighted in the left navigation menu.
OKTA-370995
The Admin Console search didn't deliver expected search results when customers searched by the full name of the user. As part of this fix, the ability to search by email address and to view the user's status has been rolled back and is now only available as Early Access.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Arena Solutions (OKTA-366918)
-
CoderPad (OKTA-368916)
-
IBM Blueworks Live (OKTA-366917)
-
NewEgg (OKTA-366340)
-
UserVoice (OKTA-366920)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Ally.io: For configuration information, see Ally - Okta SCIM Provisioning.
-
Sigma on AWS: For configuration information, see Manage Users and Teams with SCIM and Okta.
-
TravelPerk: For configuration information, see Okta Provisioning with SCIM.
SAML for the following Okta Verified applications
-
Cybereason (OKTA-364009)
-
EmployerD Payroll and HR Solutions (OKTA-356069)
-
Exium (OKTA-367104)
-
HyperStore (OKTA-365050)
-
Samdesk (OKTA-367358)
SWA for the following Okta Verified applications
-
Beyond Identity (OKTA-354040)
-
Secret Double Octopus (OKTA-353300)
-
Silverfort (OKTA-352875)
-
Trusona (OKTA-352871)
-
Truu (OKTA-352866)
Fixes
General Fixes
OKTA-332375
Sometimes, admins received a generic 500 error for agentless Desktop Single Sign-On failures caused by request timeout.
OKTA-341050
Some banners in the new Okta Admin Console had inconsistent style.
OKTA-344854
The Sign-In Widget pages were missing language attributes required by screen readers.
OKTA-358773
For deactivated users, apps were still displayed in the Assigned Applications list although they had been unassigned.
OKTA-358826
In the new Okta Admin Console, after opening and closing the spotlight search window with the keyboard shortcut Control + Space, the window no longer opened when admins clicked the Search field or icon.
OKTA-363680/OKTA-371218
Sometimes, a user that was removed from a group wasn't unassigned from the apps assigned to that group, and was instead left with individual assignment.
OKTA-365542
In the new Okta End-User Dashboard, the check box for Lightweight Directory Access Protocol (LDAP) delegated authentication settings was misaligned.
OKTA-365604
Although the See Password and Update Credential settings shouldn't be available for bookmark apps, these settings were still displayed in the Okta End-User Dashboard.
OKTA-370942
Sometimes, a deactivated Office 365 app instance in Okta couldn't be deleted if the username and password for the app instance failed authentication in Microsoft.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Google Workspace (OKTA-368883)
-
Onfido (OKTA-368220)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Upwork: For configuration information, see Configuring Provisioning for Upwork Enterprise.
SAML for the following Okta Verified applications
-
Claim Leader (OKTA-369552)
-
FAX.PLUS (OKTA-370972)
-
Gamesight (OKTA-360548)
-
IBMid (OKTA-367991)
-
MyCarSpot (OKTA-355697)
-
Osano (OKTA-368805)
-
Sigma on AWS (OKTA-369098)
-
SmartHR (OKTA-368788)
-
Tanda (OKTA-352713)
-
Very Good Security (OKTA-369127)
-
Whil (OKTA-370655)
January 2021
2021.01.0: Monthly Production release began deployment on January 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
New phone rate limits
Users who attempt Voice and SMS enrollment can now be rate limited. Voice and SMS enrollment rate-limit events are now logged in the System Log. See Rate Limits.
WebAuthn feature validation updates with Trusted Origins API
The WebAuthn feature now supports trusted cross-origin and cross-Relying Party Identifier (RP ID) validation when using the Trusted Origins API. Trusted Origins are configured in the Okta Trusted Origins framework either through the Admin UI or the API. These Trusted Origins, configured with the CORS scope, now support orgs using WebAuthn for sign-in pages hosted at Trusted Origins distinct from the org's Okta URL (that is, different from the org's Okta or custom domain URL).
User authentication with MFA can be used as an Event Hook
The user.authentication.auth_via_mfa event type is now available for use as an event hook. See Event Types for a list of events that can be used with event hooks.
Browser Plugin notification expiration
Notifications for new features in the Okta Browser Plugin now expire after three months. See Okta Browser Plugin version history.
Okta Workflows is Generally Available
Okta Workflows is an interface-driven, no-code platform for business process automation that provides integration with some of the most widely used third-party APIs in the industry, including Box, Slack, Salesforce, and G Suite Admin. See Okta Workflows.
Deployment is taking place over the course of several days to entitled orgs with the following SKUs:
-
IT Products - Advanced Lifecycle Management
-
Legacy SKU: IT Products - Lifecycle Management, Unlimited
-
Legacy SKU: IT Products - Lifecycle Management, Unlimited OIN Apps
-
Legacy SKU: IT Products - Lifecycle Management, 10 OIN Apps
APAC and HIPAA cells are excluded.
To access Workflows, select the Workflow > Workflows Console menu option from the Okta Admin Console.
Reports delivered by email
Admins can now receive the following reports by email:
-
Okta Usage Report
-
Okta Password Health Report
-
Current Assignments Report
-
MFA Usage Reports
See Reports.
Workday Field Overrides support
The Workday integration now uses Field Overrides reports to fetch custom profile data information instead of custom reports. Field Overrides is a faster report type than custom reports, so using this method is much more efficient. Existing custom report configurations will work, but new app instances will not have these configuration options. See Workday Provisioning.
Import Monitoring dashboard
The Import Monitoring dashboard is now available and displays user attribute imports for a seven day period. You can use the dashboard to view import progress, status, details, and logs. See View the Import Monitoring dashboard.
Technical admin configuration
Admins can now disable UI prompts that allow for end-users to contact technical admins and report issues. This is enabled by default for existing orgs, and disabled for new orgs.
Email address change notifications
Email change confirmation notification emails can now be sent to admins or admins and users. By default, email change confirmation notification emails are sent to admin users only. These notifications not only make admins and users aware of email address changes, they can also act as an early warning of suspicious activity. See Customize an email template. This feature will be gradually made available to all orgs.
Generally Available Enhancements
Group Membership System Log enhancement
The Add user to group membership and Remove user from group membership events have been updated. When triggered by group rules, these events now display the group rule ID in the TriggeredByGroupRuleId field under the Debug Context object.
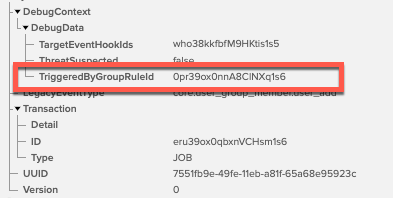
Extra Verification UI enhancement for end users
The Extra Verification section under End-User Dashboard Settings is now displayed in the right column.
Inclusive language updates
As part of the Okta inclusive language initiative, the following is changed:
-
Application provisioning documentation and UI elements have been updated with inclusive language.
-
Allow list has replaced whitelist, block list has replaced blacklist, and source has replaced master.
-
Instances of profile masters, profile master, and profile mastering on the Okta Admin Console Profile Masters page have been updated to profile source and profile sourcing. The administrator documentation has been updated to reflect this change.
Risk Scoring settings
When enabled, Risk Scoring settings now appear in the Okta sign-on policy rule. See Sign-on policies.
Early Access Features
New Features
Workplace by Facebook Push AD Manager functionality
Admins can choose to disable Push AD Manager functionality using this self-service Early Access feature. This enables admins to control the manager attribute using Okta Expression Language syntax to avoid being dependent on AD for the field. See Workplace for Facebook.
Enhancements
Skip to Content improvements
End users can now click Skip to Content on the new Okta End-User Dashboard to navigate directly to the Add Apps page.
Options relocation
The Recent Activity tab, End-User preferences, Admin View, and Sign Out options are now displayed in the user drop down menu on the Okta End-User Dashboard.
Fixes
General Fixes
OKTA-329862
Indonesian translations and templates were displayed in English.
OKTA-330432
The Okta Browser Plugin continued to recommend strong passwords for apps after the setting was disabled.
OKTA-345311
The sign-in page auto refresh sometimes didn't work when factor sequencing was used.
OKTA-347526
Information text in Settings > Update Credentials was incorrect for bookmarked apps.
OKTA-352737
Self-Service Registration with inline hooks failed for some orgs.
OKTA-354151
Some users were unable to enroll in Okta Verify through TOTP and PUSH methods in some orgs.
OKTA-354967
When defined for an MFA Enrollment policy, the App Condition was not enforced when a user signed in to an application.
OKTA-355035
Security methods for Safari web authentication did not allow for biometric authentication.
OKTA-355482
When super admins edited a group admin role in Security > Administrators, only the first 10 groups were displayed.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe Sign Provisioning (OKTA-352597)
-
FIS E-ACCESS (OKTA-346510)
-
Google Analytics (OKTA-348673)
-
Nationwide Financial (OKTA-355417)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- TerraTrue: For configuration information, see Configuring Provisioning with TerraTrue for Okta customers.
SAML for the following Okta Verified applications
-
Culture Connect (OKTA-354618)
-
hCaptcha (OKTA-352403)
-
LinkedIn Talent Solutions (OKTA-343875)
-
Process Bolt (OKTA-353096)
SWA for the following Okta Verified applications
-
Adweek (OKTA-350720)
-
Amazon Payee Central (OKTA-347803)
-
CenturyLink (OKTA-350562)
-
TechCrunch (OKTA-343939)
-
Vue Mastery (OKTA-342948)
OIDC for the following Okta Verified applications
- Deel: For configuration information, see How to Configure Okta SSO.
- Immuta: For configuration information, see Okta and OpenID Connect.
- Sapling: For configuration information, see How to use Okta OIDC with Sapling.
- Time Doctor: For configuration information, see Configure Okta OIDC for Time Doctor.
Weekly Updates
Fixes
General Fixes
OKTA-336092
The import of user accounts from Adobe Experience Manager to Okta failed if there were duplicate entries in the database.
OKTA-336966
The password requirements presented to LDAP-sourced users during password reset didn’t match the password policy definition.
OKTA-337515
In some cases, the link to activate an account through self-service registration led to an empty page.
OKTA-340836
When admins enabled password change notification, end users going through self-service registration erroneously received a password change notification in addition to the account activation email.
OKTA-341729
In some cases, when a role was deleted from the Amazon Web Services (AWS) console, refreshing the app data in Okta removed group assignments causing users to lose access to AWS.
OKTA-343739
Some users received notifications for new app assignments although no new apps had been assigned to them.
OKTA-346826
In the SmartSheet provisioning profile, when admins tried to change the Group Priority setting to Combine values across groups for the variable smartsheet.userPermissions, the error message: Not allowed to modify property userPermissions from the base schema was returned.
OKTA-354279
In some orgs, after account activation, Active Directory users were redirected to a blank page instead of the Okta End-User Dashboard.
OKTA-355574
Some generic or anonymized WebAuthn factors were inaccurately labeled YubiKey.
OKTA-358425
When evaluating risk using device token as a signal, some new users signing in to Okta were incorrectly marked as high risk.
OKTA-359363
Reactivated users from AD did not maintain their group memberships after import.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Cisco Webex Meetings (OKTA-356220)
Applications
Integration Updates
The Tableau Online SAML app has been updated to add support for Single Logout (SLO). Customers who previously added the integration should refer to the SAML Setup Instructions to enable this new feature.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
Modern Health: For configuration information, see Modern Health SCIM 2.0 Provisioning Guide.
SAML for the following Okta Verified applications
-
Communifire (OKTA-353568)
-
LabLog (OKTA-356012)
-
Ybug (OKTA-356075)
SWA for the following Okta Verified applications
-
eClinical Works (OKTA-349360)
-
SiteLink myHub (OKTA-354952)
Fixes
General Fixes
OKTA-303059
API calls to Workday sometimes removed the secondary email of a user when attempting to update the user information.
OKTA-324780
Failed Lightweight Directory Access Protocol (LDAP) sign-in attempts were logged as failed Active Directory (AD) sign-in events in the System Log.
OKTA-333518
Using SAML-based Device Trust with VMware for Identity Provider (IdP) initiated flows threw a 404 error for some users.
OKTA-334383
After entering an invalid username in the Okta Sign-In Widget, users sometimes received a 404 error after refreshing the browser.
OKTA-351888
When editing a user profile, the value of a custom attribute defaulted to the first value, rather than blank (null).
OKTA-353590
If end users accessed Okta by using a Sign-In Widget in Internet Explorer, their origin header wasn't logged in the System Log.
OKTA-354271
Removing a permission set in Salesforce sometimes caused provisioning failures in Okta even though that permission set was no longer selected for the Salesforce app assignment.
OKTA-354309
The EmailEncodingKey attribute in Okta orgs was sometimes incorrectly reported to Salesforce.
OKTA-355368
Profile sourcing and attribute-level sourcing functionality was erroneously not available for Universal Directory SKUs.
OKTA-356087
Send SMS button text was not displayed correctly if the text was too long for certain languages.
OKTA-357656
When using Agentless Desktop Single Sign-on (ADSSO), admins sometimes received scripting errors.
OKTA-358469
The client IP was sometimes missing from user.authentication and policy.evaluate_sign_on events.
OKTA-358970
The logo on the user activation page didn't display correctly if it included a redirect to an application.
OKTA-359173
Inactive users were sometimes erroneously displayed in the Current Assignments report.
OKTA-362398
If the username was different from the email address, Okta Password Health reports were sent erroneously to the username instead of the user's primary email.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Workforce Now (Employee) (OKTA-361462)
-
Angus (OKTA-360602)
-
Cisco Partner (OKTA-359699)
-
MessageBird (NL) (OKTA-361828)
-
Parallels (OKTA-360298)
-
RIMS (OKTA-360587)
-
Sylvania (OKTA-360624)
-
The Economist (OKTA-360588)
-
Xero (OKTA-361732)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Appaegis Access Cloud: For configuration information, see Appaegis Accces Cloud configuration guide (note you will need an Appaegis account to view this documentation).
-
IQVIA SmartSolve: For configuration information, see Configure user provisioning with Okta.
-
Kisi Physical Security: For configuration information, see Kisi SCIM Setup documentation.
SAML for the following Okta Verified applications
-
Airbase (OKTA-356338)
-
Kandji (OKTA-360958)
-
Pactflow (OKTA-355531)
-
Partnerize (OKTA-345643)
-
Pave Total Comp (OKTA-359579)
-
Pilgrim SmartSolve (OKTA-359054)
-
Sapling (OKTA-358186)
-
Sociabble (OKTA-355695)
-
Tax1099 (OKTA-355507)
-
ThankYouKindly (OKTA-354613)
-
WhosOffice (OKTA-355012)
-
Yonyx Interactive Guides (OKTA-355527)
December 2020
2020.12.0: Monthly Production release began deployment on December 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Admin Privilege events can be used as Event Hooks
Admin Privilege events are now available for use as Event Hooks. See Event Types for a list of events that can be used with event hooks.
Application Access Request Workflow Event Hooks
Application Access Request Workflow events are now available for use as an external Event Hook. Admins can use Application Access Request Workflow events to designate approvers for app access requests. See Event Types for a list of Events that can be used with Event Hooks.
The map view is again available in the System Log
The System Log map view, which was temporarily removed, is again available.
System Log events
-
The system.custom_error.update event indicates that the Custom Error page has been updated.
-
The system.custom_signin.update event indicates that the Custom Sign-In page has been updated.
-
The system.custom_url_domain.initiate event indicates that the Custom URL Domain setup has been initiated.
-
The system.custom_url_domain.cert_upload event indicates that a Custom URL Domain HTTPS certificate has been uploaded.
-
The system.custom_url_domain.verify event indicates that the Custom URL Domain has been verified in the DNS.
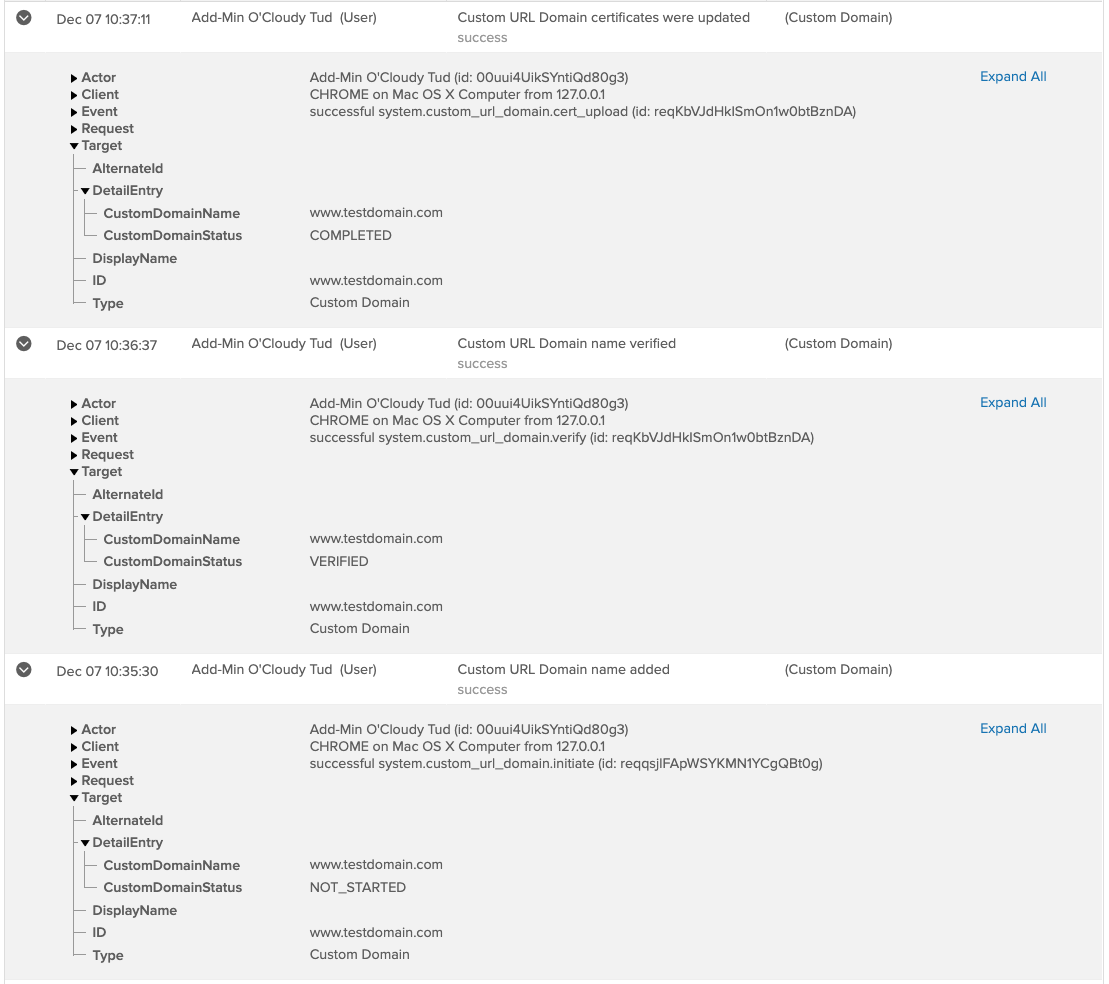
Recommendation text added to SSO IWA Agents section of the Downloads page
On the Okta Admin Console Downloads page, text has been added to the SSO IWA Agents section recommending that Agentless Desktop Single Sign-on (ADSSO) should be used to implement Desktop Single Sign-on (DSSO). This text has been added to highlight that ADSSO has a simplified configuration process and requires less maintenance. See Configure agentless Desktop Single Sign-on
Additional PIV IDP user profile mapping values
In Okta user profiles, three new attributes are available:
- idpuser.subjectAltNameUuid
- idpuser.subjectKeyIdentifier
- idpuser.sha1PublicKeyHash
These attributes are available to newly created Personal Identity Verification (PIV) identity providers and to identity providers that were marked inactive and then reactivated.
Okta SSO IWA Web App agent, version 1.13.2
This release of the Okta SSO IWA Web App agent includes security enhancements and internal fixes. See Okta SSO IWA Web App version history.
Jira Authenticator, version 3.1.5
This release contains bug fixes and logging improvements. See Okta Jira Authenticator Version History.
Confluence Authenticator, version 3.1.5
This release contains bug fixes and logging improvements. See Okta Confluence Authenticator version history.
State tokens in the Agentless DSSO authentication flow
An authentication state token has been added to the Agentless DSSO workflow to allow orgs to relay information such as fromUri. This change lets orgs shorten URLs and avoid HTTP 414 URI Too Long status code errors. See Configure agentless Desktop Single Sign-on.
SAML account linking
Admins can now enable or disable automatic account linking between SAML identity providers and Okta. They can also restrict the linking based on whether the end user is a member of any of the specified groups. See Identity Providers.
Generally Available Enhancements
Inclusive language updates
As part of the Okta inclusive language initiative, the following is changed:
-
Block list has replaced Blacklist in the HealthInsight Blacklist Proxies and Blacklist Zones documentation. See Blocklist proxies with high sign-in failure rates and Blocklist network zones.
-
Identity Provider features have been updated with inclusive language. Allow list has replaced whitelist and source has replaced master.
Usability enhancements for OIDC app wizard
The OIDC app integration wizard interface has been updated with usability improvements and clarified help text. See Create OIDC app integrations using AIW.
Sign-in Widget and accessibility improvements
Main landmarks and skip links have been added to the Sign-in Widget. Accessibility improvements for OAuth and Admin Consent pages include focus on input fields and Don’t Allow buttons. See Configure a custom Okta-hosted sign-in page.
Contact your administrator link removed
The Client/Device certificate error page no longer contains an email link to contact your administrator.
BambooHR integration enhancement
The following org properties have been added to the BambooHR application integration:
-
Timezone aware pre-hires: This enables users' Lifecycle Management based on their Timezone/Location. If it is disabled, Okta manages users' lifecycles according to UTC timezone.
-
Preferred timezone: This option allows admins to set the main location timezone the same as in the BambooHR instance (BambooHR Settings > General Settings > Timezone). This is available only when the Timezone aware pre-hires option is enabled.
UltiPro integration enhancement
In new instances of UltiPro, app user profile templates now contain a required EepPersonID field for external IDs. See UltiPro.
Group Password Policy enhancement
The Group Password Policies enhancement is now available for all Production orgs. By using Group Password Policies and associated rules, admins can configure and enforce password settings and set account recovery options for groups. See Sign-on policies.
Early Access Features
New Features
One Time Use Refresh Token
One Time Use Refresh Token, also called Refresh Token Rotation, helps a public client to securely rotate refresh tokens after each use. A new refresh token is returned each time the client makes a request to exchange a refresh token for a new access token. See Refresh Token Rotation.
Fixes
General Fixes
OKTA-325406
The Italian translation in the MFA Factor Enrolled email template was inaccurate.
OKTA-328882
The Japanese translation during the password reset process was inaccurate.
OKTA-329447
In the Integration settings of the LDAP Provisioning tab, the User Attribute help link was broken.
OKTA-335816
The password requirement message displayed to some users during the self-registration process was misleading.
OKTA-337663
The Hungarian translation during the sign-in process was inaccurate.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
GetFeedback (OKTA-348946)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Forcepoint Private Access: For configuration information, see Forcepoint Private Access: Okta app for single sign-on.
- Splashtop: For configuration information, see Provisioning setup - Okta (SCIM).
- IAM Connector: For configuration information, see IAMConnector Help.
SAML for the following Okta Verified applications
-
Adra by Trintech (OKTA-348038)
-
Authomize (OKTA-347099)
-
Axomo (OKTA-341694)
-
DefenseStorm (OKTA-345662)
-
Forcepoint Private Access (OKTA-338537)
-
IntelligenceBank (OKTA-347415)
-
KHA Online - SDS (OKTA-347435)
-
Rootly (OKTA-348648)
-
Smarklook (OKTA-346263)
-
TenForce (OKTA-338549)
-
Toggl Plan (OKTA-347528)
-
Upmarket (OKTA-344925)
-
Very Good Security (OKTA-348624)
-
WIREWAX (OKTA-347407)
Weekly Updates
Fixes
General Fixes
OKTA-303280
The ThumbnailPhoto attribute for Office 365 was hidden or uneditable, which prevented admins from making changes to Office 365 profile mapping.
OKTA-330732
The Japanese translation for password policy messages was inaccurate.
OKTA-333711
An incorrect error was returned when an admin tried to delete an app sign-on policy rule that was already deleted.
OKTA-338458
Routing rules were not honored for end users who attempted to access their orgs using an iPad.
OKTA-347185
End users couldn't sign in with Personal Identity Verification (PIV) cards when they were in a Password Expired state.
OKTA-351052
Language used in OIDC app creation was outdated.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Advanced MD (OKTA-351889)
-
Deloitte Connect (OKTA-349765)
-
RUN Powered by ADP (OKTA-351720)
-
Sigma Aldrich (OKTA-351026)
-
TSheets QuickBooks (OKTA-350027)
-
UMR (OKTA-351440)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Alchemer (OKTA-338554)
-
Bullseye TDP (OKTA-350352)
-
SQLDBM (OKTA-348943)
SWA for the following Okta Verified application
-
HomeStreet Bank Business (OKTA-343128)
OIDC for the following Okta Verified application
- Gong: For configuration information, see the Okta OIDC Configuration Guide.
Fixes
General Fixes
OKTA-312643
The Okta LDAP agent couldn't set the correct account enable/disable values for IBM LDAP accounts.
OKTA-334346
When admins attempted to approve Self Service app requests from users on the new Okta End-User Dashboard, they were unable to select values for the user assignment.
OKTA-338621
When a user with a CamelCase Okta username was provisioned to Google Workspace, their username was converted to lowercase and they were unassigned during the next import into Okta.
OKTA-340092
The System Log still used Daylight Savings Time for the America: Sao Paulo time zone.
OKTA-342401
If a Workday mobile phone number wasn't mapped to Okta, it was removed from Workday during the Okta to Workday updates.
OKTA-342757
New contingent users from Workday weren't imported and the existing users weren't updated during incremental imports.
OKTA-346242
On the new Okta End-User Dashboard, end users could make an app request even when Self Service was disabled.
OKTA-347247
Self-Service Registration form fields didn't apply minimum length requirements.
OKTA-348756
Pushing new user profiles to Google Workspace failed with an Invalid User error.
OKTA-349883
The first password wasn't included in the password history when an account was created through Self-Service Registration.
OKTA-351779
Some full imports from Active Directory and LDAP failed with a This choice creates a conflict error.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe Stock (OKTA-353598)
-
Express Scripts (OKTA-353604)
-
Visionplanner (OKTA-353502)
-
WebTimeClock (OKTA-353608)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Rewatch: For configuration information, see SCIM configuration.
SAML for the following Okta Verified application
-
GRAVTY (OKTA-349790)
SWA for the following Okta Verified applications
-
Bitrix24 (OKTA-354066)
-
Particle (OKTA-345520)
OIDC for the following Okta Verified application
- Tonkean: For configuration information, see Tonkean Okta OIDC Configuration Guide.
November 2020
2020.11.0: Monthly Production release began deployment on November 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta Browser Plugin, version 5.42.0
This version includes the following:
- Sign-in pages are opened in a new tab only after a user installs the plugin manually, and are not opened if the plugin is installed through a group policy for Chrome, Firefox, Legacy Edge, and Chromium Edge.
- Performance improvements.
You can download the plugin for Internet Explorer from the Okta End-User Dashboard, or for other web browsers, install through their respective stores. See Okta Browser Plugin version history.
OIN Manager - add app instance properties
In the OIN Manager portal, new functionality in OIDC, SAML, and SCIM submission steps allow ISVs to create custom per-tenant URLs and URIs for app integration submissions. See Configure protocol-specific settings.
Tor Anonymizer recommendation
Admins can see a new HealthInsight recommendation to view failed sign-in rates from IPs categorized as Tor Anonymizer Proxies. Okta recommends using Dynamic Zones to blacklist IPs that are categorized as Tor anonymizer proxies. See and HealthInsight.
Vendor-specific attributes
RADIUS agents now support vendor specific attributes. With this feature, admins can use optional settings to configure vendor specific attributes to include group membership. Note that no agent update is required for this feature. See Configure group response in the following topics:
Client-based rate limiting
Client-based rate limiting for the OAuth API /authorize endpoint is now available in Preview. It provides granular isolation between requests made to the /authorize endpoint by using a combination of the Client ID, user's IP address, and the Okta device identifier. This isolates rogue OAuth clients and bad actors, ensuring valid users and applications don't run into rate-limit violations. The client-based rate-limiting framework can exist in one of three modes set in the Admin console. See Account settings.
User Consent for OAuth 2.0 Flows in API Access Management
A consent represents a user’s explicit permission to allow an application to access resources protected by scopes. As part of an OAuth 2.0 or OpenID Connect authentication flow, you can prompt the user with a popup window to approve your app's access to specified resources.
Consent grants are different from tokens because a consent can outlast a token, and there can be multiple tokens with varying sets of scopes derived from a single consent. When an application comes back and needs to get a new access token, it may not need to prompt the user for consent if they have already consented to the specified scopes. Consent grants remain valid until the user manually revokes them, or until the user, application, authorization server or scope is deactivated or deleted.
See User Consent for OAuth 2.0 and OpenID Connect Flows.
Generally Available Enhancements
Inclusive language updates
The OIN Catalog has been updated with inclusive terminology. Attribute Sourcing has replaced Attribute Mastering.
Changes in rate limit utilization notifications
All Customer Identity org super admins now get a detailed notification in the Okta Admin Console and an email when their org’s rate limit utilization meets the following criteria:
- Crosses the threshold (60% for API products and 90% for Workforce products)
- Reaches 100%
These warnings help super admins take preventative action and avoid service disruptions. See Account settings.
Group Password Policy enhancement
The Group Password Policies enhancement is now available for all new production orgs.
By using Group Password Policies and associated rules, admins can configure and enforce password settings and set account recovery options for groups. See Sign-on policies. This feature was already released to a subset of orgs, we are now releasing it to all new Production orgs.
ThreatInsight security enhancements
ThreatInsight enhancements improve detection of credential-based attacks from malicious IPs. See About Okta ThreatInsight.
Fixes
General Fixes
OKTA-293251
In some cases, reactivated AD users signing in to Okta were presented an empty Welcome screen although no user actions were required.
OKTA-297744
On the new Okta End-User Dashboard, wide logos were cut off.
OKTA-313490
In Okta End-User Dashboard > Settings > Personal Information, some editable fields extended past their border if they contained too many characters.
OKTA-321737
In some cases, admins didn't receive the Import Summary Notification Emails from Workday when an import was completed.
OKTA-321999
In some cases, users signing into Okta through email MFA received an error message despite entering the correct passcode.
OKTA-323345
The email template for password change notifications didn't allow certain expressions used in other email templates.
OKTA-323919
Admins could exclude the mandatory email field from the self-service registration form.
OKTA-326781, OKTA-329842
Admins were stuck when attempting to load Group Rules in Directory > Groups > Group Rules for certain expressions.
OKTA-328856
The Okta Browser Plugin didn’t inject credentials into sign-in pages for Org2Org SWA apps added to dashboards.
OKTA-330549
Disabled users were imported erroneously from Confluence to Okta during provisioning.
OKTA-330615
Invalid error objects returned through a Registration Inline Hook caused the client to see a 500 error rather than a 400.
OKTA-334126
Scheduled imports failed when CSV Directory Incremental Imports was enabled.
OKTA-334163
In some cases, admins erroneously received a rate limit error when viewing Access Policies through Security > API > Authorization Servers > Access policies > Select the policy.
OKTA-334255
Enrollment and reset emails were still sent to secondary email addresses even if the admin had disabled secondary email addresses.
OKTA-334929
Due to differences in the way the new RADIUS app handles username attributes, authentication failed for some users depending on whether their username had a UPN or sAMAccountName format.
OKTA-335890
Some SWA apps in the OIN App catalog were categorized incorrectly.
OKTA-337462
In some cases, custom app names for Wizard apps weren't globally unique and caused collision issues with apps from other cells.
OKTA-338863
Admins were unable to add IP addresses to the BlockedIpZone list from the System Log.
OKTA-342006
In some cases, the footer on the new Okta End-User Dashboard didn't maintain its position at the bottom of the page.
OKTA-343802H
In the Okta Admin Console, the message displayed when a rate limit was reached was incorrect.
OKTA-345672H
The new Okta End-User Dashboard was enabled for some end users even though it was disabled by the admin. The dashboard now displays the correct version depending on whether the new dashboard is enabled or not.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
1Password Business (OKTA-340768)
-
ADP Portal (OKTA-339374)
-
ADP TotalSource (OKTA-339601)
-
CBT Nuggets (OKTA-340787)
-
Citrix Right Signature (OKTA-336890)
-
ECP (OKTA-340794)
-
FCO (OKTA-340785)
-
ISSUU (OKTA-340784)
-
Legrand Service Center (OKTA-340769)
-
Miro (OKTA-338110)
-
Sainsburys (OKTA-340792)
-
Schwab Advisors (OKTA-337947)
-
SEMrush (OKTA-340786)
-
SmartyStreets (OKTA-340781)
-
SunTrust SunView Treasury Manager (OKTA-338770)
-
vAuto (OKTA-340782)
-
Zurich Adviser Portal (OKTA-340770)
The following SAML app was not working correctly and is now fixed
-
Sentry (OKTA-332821)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Airbnb for Work: For configuration information, see Configuring Provisioning for Airbnb for Work.
- LimbleCMMS: For configuration information, see Configure Limble to sync with Okta.
- Clarizen One: For configuration information, see Cloud-Based User Provisioning with OKTA.
- Fletch: For configuration information, see Fletch SCIM Integration Configuration Guide for Okta.
SAML for the following Okta Verified applications
-
AlertEnterprise Guardian Access (OKTA-331898)
-
Cirrus Federation Bridge (OKTA-331296)
-
ERP Maestro 2.0 (OKTA-328139)
-
Helper Helper (OKTA-338542)
-
Nature Research (OKTA-337029)
-
Qualified (OKTA-336983)
-
Raketa (OKTA-336302)
-
Streams (OKTA-334367)
SWA for the following Okta Verified applications
-
Adyen (OKTA-337639)
-
BNP Paribas (OKTA-331531)
-
Freshbooks (OKTA-337319)
-
Schneider Electric (OKTA-330814)
OIDC for the following Okta Verified applications
- Eracent IT Management Center: For configuration information, see Eracent documentation here (note you need an Eracent account to access this documentation).
- Amplify: For configuration information, see Configuring and Managing Identity Providers (IdPs).
Weekly Updates
Fixes
General Fixes
OKTA-322372
Users were prompted to set up a Password Recovery Question every time they signed in to Okta when Self-Service Password Reset was enabled.
OKTA-325372
Single sign-on events for OIDC apps with Federation Broker Mode enabled didn't appear in the System Log.
OKTA-328845
In the Directories tab of the Okta Admin Console, existing app assignment settings for Groups couldn't be modified.
OKTA-328900
Some attributes sourced from NetSuite weren't imported into Okta.
OKTA-329029
Bookmark apps that were added by users didn't have See Password and Update Credentials options in the Settings tab.
OKTA-330495
Disabling the app conditions for MFA enrollment policies removed all app conditions from existing factor enrollment policies.
OKTA-334118
Some reactivated G Suite users were mistakenly deactivated in Okta.
OKTA-335769
Some POST requests to the /users endpoint incorrectly triggered Inline Hooks, which resulted in higher latency.
OKTA-336865
In some cases, redirects to the Okta Admin Console resulted in a 404 error.
OKTA-339228
In some cases, app membership changes made by Group Membership Admins weren't pushed to the app.
OKTA-346079H
In some cases, inbound federation to preview failed for Generic OIDC Idps.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Workforce Now (Admin) (OKTA-341914)
-
ADP Workforce Now (Employee) (OKTA-336993)
-
Barracuda Networks (OKTA-341592)
-
CareFirst (OKTA-341601)
-
CVS Caremark (OKTA-343161)
-
Earth Class Mail (OKTA-340804)
-
Fiserv - Client Workstation (OKTA-341610)
-
Grammarly (OKTA-341608)
-
Informatica (OKTA-341605)
-
Justifacts (OKTA-341595)
-
LexisNexis Insurance Solutions (OKTA-341583)
-
Optimal Blue (OKTA-343800)
-
Safari Online Learning (OKTA-340799)
-
ShipStation (OKTA-342680)
-
Staples (OKTA-343167)
-
Trustwave (OKTA-340797)
Applications
Application Updates
The following apps have been deprecated from the OIN catalog:
- Kato: Kato ceased to exist as of August 2015.
- Datasite: A new Datasite integration has been published to the OIN. The previous integration has been deprecated (renamed to Datasite Deprecated) and can no longer be added by customers. If you are using the now-deprecated Datasite app, there is no impact on you. We recommend moving to the new app to take advantage of new updates to the app we may add to it in future.
New Integrations
SAML for the following Okta Verified applications
-
Airbnb for Work (OKTA-329468)
-
Axway - AMPLIFY Platform (OKTA-335106)
-
Baker Hill NextGen (OKTA-336078)
-
Lumity 2.0 (OKTA-342160)
-
Stratafax (OKTA-339889)
OIDC for the following Okta Verified application
-
Beyond Identity User: For configuration information, see Beyond Identity User Portal integration with Okta.
Fixes
General Fixes
OKTA-293294, OKTA-293296
Some screen readers didn't read the elements on the new Okta End-User Dashboard correctly when tabbing over the sections or apps.
OKTA-302414
Profile mappings were not applied downstream for users after they were added to or removed from a group.
OKTA-316898
System Log messages for self-service account password reset events were misleading.
OKTA-324892
The Assignment tab on an app page was misaligned for some admins who filtered by Groups.
OKTA-325820
When an app that requires VPN was moved to a different section of the new Okta End-User Dashboard, the VPN dialog box didn't appear.
OKTA-327550
Re-authenticating API integration credentials for provisioning-enabled apps reset the app username format.
OKTA-330846
The report name was missing from reports delivered by email.
OKTA-336058
In some cases, the password reset workflow for end users failed if admins disabled the requirement for a security question.
OKTA-337304
Aliases in Office 365 were incorrectly removed when users were assigned to the app in Okta through Licenses/Roles Management Only provisioning.
OKTA-337563
Job requests to refresh app data for the Adobe Experience Manager timed out in Preview orgs.
OKTA-338055
Salesforce integration caches were not cleared if an admin authenticated using different credentials.
OKTA-343777
Enrolling in Okta Verify with SMS push sometimes failed.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe (OKTA-344942)
-
Adobe Admin Console (OKTA-345276)
-
Alaska Airlines (OKTA-344936)
-
American Express Online by Concur (OKTA-343173)
-
Autotask (OKTA-345338)
-
Backblaze (OKTA-343168)
-
Chatham Direct (OKTA-343202)
-
Citizens Bank accessOPTIMA (OKTA-343176)
-
Conservice (OKTA-343192)
-
DoorDash (OKTA-343177)
-
FullStory (OKTA-343704)
-
HelloSign (OKTA-342994)
-
International Air Transport Association (IATA) (OKTA-343209)
-
Linode (OKTA-343086)
-
Nice inContact Workforce Management (OKTA-343175)
-
One America (OKTA-344616)
-
Rakuten Advertising (OKTA-345250)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Datasite (OKTA-333536)
-
Hover, Inc. (OKTA-343149)
-
Mosio (OKTA-343051)
-
TVU Service (OKTA-344929)
-
uStudio (OKTA-342622)
OIDC for the following Okta Verified applications
- Intricately: For configuration information, see SSO Authentication for Intricately.
-
Vault Platform: For configuration information, see Vault Platform – Okta Integration.
Fixes
General Fixes
OKTA-311308
Admins couldn't configure LDAP instances unless usernames were formatted as email addresses.
OKTA-324213
Options to configure an inline hook for an AD instance were missing for some admins.
OKTA-325684
Some group admins received errors when they navigated to Directory > People.
OKTA-328593
After the Office 365 app was enabled, Outlook didn't appear on some end users' dashboards.
OKTA-333901
When base attributes were set as read-only, some attributes were missing from the user profile.
OKTA-336862
Admins who selected an LDAP instance with no connected agents were directed to the Agents tab instead of the Provisioning tab.
OKTA-337494
Some AD-managed users were incorrectly displayed as having admin roles.
OKTA-339859
When API Integration was enabled, some ServiceNow imports didn't import all active users.
OKTA-343355
The 3-number challenge that is part of the Okta Verify risk-based authentication feature appeared on end user mobile devices in LDAPi environments even though the feature isn't supported in those environments.
OKTA-344772
When an end user made two SMS or voice MFA enrollment requests, the second request was only sent to the backup provider if it was made within one minute of the first.
OKTA-347213
Email notifications sent through the report workflow incorrectly listed the report expiration as 30 days later, instead of 7.
OKTA-347218
The map view in the System Log still appeared even after the functionality was unavailable.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Workforce Now (Employee) (OKTA-343365)
-
Airtasker (OKTA-348075)
-
Akamai (OKTA-344943)
-
BSA E-Filing (OKTA-346870)
-
Dell Boomi (OKTA-348090)
-
Hartford Retirement (OKTA-346843)
-
Innovative (OKTA-348491)
-
Nextiva NextOS 3.0 (OKTA-346866)
Applications
Application Update
The Cloudvisor.io integration has now been deprecated from the OIN as Cloudvisor is now rebranded as Zesty. Use Zesty.co SAML app instead.
New Integrations
New SCIM integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- COR: For configuration information, see Configuring Okta Provisioning for COR.
- CrisisGo: For configuration information, see SCIM Integration With CrisisGo.
- Evergreen: For configuration information, see Configuring Okta SCIM Provisioning for Evergreen.
- Grammarly: For configuration information, see Configuring Provisioning for Grammarly.
- LawVu: For configuration information, see OKTA SCIM & SAML (SSO) Configuration Guide.
- Learnerbly: For configuration information, see Integrating the Learnerbly SCIM 2.0 application in Okta.
- Notion: For configuration information, see Provision Users and Groups with SCIM.
- Signal Sciences: For configuration information, see Signal Sciences SCIM Configuration Guide.
- Vonage: For configuration information, see Configuring Vonage Business Cloud with Okta.
SAML for the following Okta Verified applications
-
Animaker (OKTA-344080)
-
Clockwork Recruiting (OKTA-346859)
-
CrisisGo (OKTA-335097)
-
EureQa (OKTA-348851)
-
Immuta (OKTA-343150)
-
Lawvu (OKTA-336365)
-
Mooncamp (OKTA-344916)
-
Palo Alto Networks - Prisma Access (OKTA-343825)
-
Zesty.co (OKTA-340116)
SWA for the following Okta Verified applications
-
CitiDirect BE (OKTA-340862)
-
Inside Mortgage Finance (OKTA-335129)
-
NewRez Correspondent (OKTA-339224)
-
ProofPoint Community (OKTA-340034)
OIDC for the following Okta Verified applications
- Approval Studio: For configuration information, see Okta SSO Integration.
- Cerby: For configuration information, see How-To Configure SSO between Cerby and Okta.
- LegalDesk: For configration information, see How to Configure OIDC for LegalDesk.
- MPS Monitor: For configuration information, see OIDC configuration with the MPS Monitor Okta app.
- Ten Spot: For configuration information, see Ten Spot OIDC Configuration Guide.
October 2020
2020.10.0: Monthly Production release began deployment on October 12
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Inclusive language and terminology
Okta is focused on the adoption of inclusive language and communication. Some long-standing industry terminology and expressions have been updated in this release and will continue to be made in future releases. Click the Feedback button on any Okta Help page to share your suggestions on the use of inclusive language.
The following inclusive language changes have been made:
- Allow list has replaced whitelist
- Block list has replaced blacklist
See Network zones.
The following topics have begun to adopt the new inclusive language:
- Exempt an IP Zone from Okta ThreatInsight
- Block list a network zone
- Create zones for IP addresses
- Define an ASN for a dynamic zone
The network zones user interface has been updated with inclusive terminology:
- Add IP Zone
- Add Dynamic Zone
The OIN Manager user interface has been updated with inclusive terminology:
- Profile Sourcing has replaced Profile Mastering
API Access Management enables scope as a claim
Admins can now name a claim scope in API Access Management custom authorization servers. Admins can also use the EL expression access.scope in custom claims to return an array of granted scope strings. See API Access Management.
OIN Manager - enable profile sourcing
For developer orgs, the Profile Sourcing option (previously Profile Mastering) for SCIM apps must be enabled by Okta developer support. If you're an ISV and need this functionality temporarily activated when you're testing and submitting a SCIM app integration, see Submission support.
Changes to removing personal app instances
When an end user adds an app from the OIN catalog that is not self-service within their org, a personal instance of the app integration is created. Previously, if the end user removed the app integration from their dashboard, then the app instance was kept but marked as deactivated in the System Log. Now, when the user removes the app integration, the personal instance is removed and it is marked as deleted in the System Log. See Common SSO Tasks for End Users.
On-Premise Jira versions confirmed for OKTA Jira Authenticator
The Okta JIRA authenticator has been certified to work with new On-Prem Jira versions. See Okta Jira Authenticator Version History .
Default sign on rule set to Deny in Client Access Policies for new Office 365 app instances
In Client Access Policies for new Office 365 app instances, the Default sign on rule is now set to Deny access (formerly set to Allow). Additionally, we've provided a rule above the Default sign on rule that allows access to only web browsers and apps that support Modern Authentication. This change is designed to help customers implement more secure policies by default. Note: Existing O365 app instances are unaffected by this change. For more information, see Get started with Office 365 sign on policies.
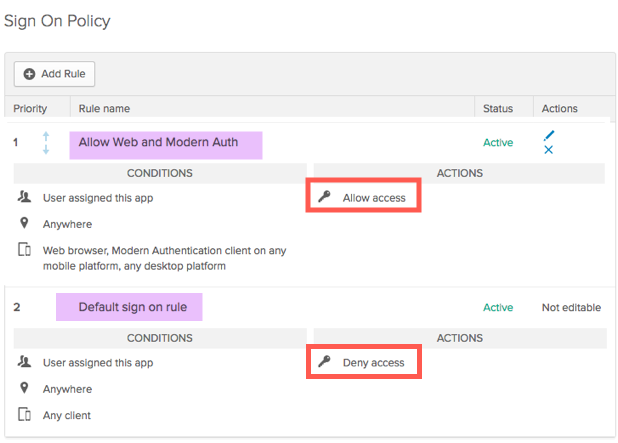
Self-Service improved plugin onboarding experience
The improved Okta Browser Plugin onboarding experience for new end users is now available on all web browsers except Safari. After installing the plugin, new end users will be automatically directed to the sign in page or will have their dashboard refreshed, and will be shown an introduction banner on their dashboard. See Install the Okta Browser Plugin.
Provision out of sync users
If you enable provisioning for an app that already has users assigned to it, Okta can sync these users so they now have provisioning capabilities. See Provision applications.
Email address change notification templates
Email address change notification templates are now available. These templates notify users of an email address change and let them confirm the change. See Customize an email template.
Password requirements formatting
When setting a password, requirements are now shown in a list format rather than a sentence format.
Generally Available Enhancements
Okta LDAP agent log enhancement
To help identify and correct latency issues between Okta and on-premises Okta LDAP agents, a delAuthTimeTotal field has been added to the Login Events section of the Okta LDAP agent log. This field displays the time in milliseconds taken to complete a delegated authentication request between Okta and the Okta LDAP agent. See Locate the Okta LDAP agent log.
Sign-In page auto refresh
In some cases, if end users don’t sign in on the Sign-In page and leave it idle until the authentication session expires, the Sign-In page now refreshes automatically to establish a new session.
NetMotion Mobility
The NetMotion Mobility (RADIUS) app is now available on the OIN. It supports the EAP-GTC protocol with RADIUS agent version 2.12.0 or later. See Configure NetMotion Mobility to interoperate with Okta via RADIUS.
OIN Manager - submission process improvements
The final processing step has been removed from the OIN app integrations submission process. Submitted app integrations that pass quality assurance (QA) testing by the OIN Operations team don't require further ISV input and are now automatically approved and published to the OIN.
OIN Manager - update submission email text
The email text sent to ISVs during the quality assurance (QA) portion of the OIN submission process has been clarified to make the information easier to understand.
Early Access Features
New Features
Custom IdP factor authentication with OIDC support
Custom IdP factor authentication now supports OpenID Connect. See Custom IdP factor .
Optional Display Preferences for new Okta End-User Dashboard
Users can now set Display Preferences on the new Okta End-User Dashboard. They can enable or disable the Recently Used section and organize their dashboard as a grid or a list. See The new Okta end-user experience.
Fixes
General Fixes
OKTA-277851
In some cases, removing tasks from the Okta Admin Dashboard failed.
OKTA-283085
When searching for apps on the new Okta End-User Dashboard, app logos included in the search results were too large.
OKTA-314990
In some cases, a user's DisplayName appeared as their user ID in the System Log.
OKTA-315076
For certain app admin operations, rate-limit error messages in the System Log erroneously suggested that admins retry failed operations manually instead of waiting for the operations to be rescheduled.
OKTA-315286
After selecting certain attributes in Advanced RADIUS settings, the On-Prem MFA agent returned the proxy IP instead of the IP address of the RSA agent.
OKTA-315638
Grammarly and Dragon extensions on Chrome caused issues for users who attempted to sign in to apps that required Okta MFA.
OKTA-321996
Users deactivated in Okta weren't deactivated correctly in the Salesforce app.
OKTA-322115
If an account was deleted while the user was in an active session, Okta presented an error instead of redirecting the user to the Sign-in page.
OKTA-322925
Certain custom attributes that were updated in Okta weren't subsequently updated in LDAP.
OKTA-325636
Admin privileges couldn't be removed from users who had an invalid email address.
OKTA-327165
When updating a security question for password recovery, end users could use the non-domain part of their email as an answer.
OKTA-327188
Some Japanese translations on the Sign-In page weren't displayed correctly.
OKTA-329289
Some email templates in Italian were inaccurately translated.
OKTA-329756
In some cases, the Pending email address change email sent to end users didn't include dynamic content.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Acronis Cloud (OKTA-333972)
-
Cisco Partner Login (OKTA-334409)
-
Flipboard (OKTA-332426)
-
Flock (helloflock.com) (OKTA-333132)
-
The Hartford EBC (OKTA-332871)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Brightflag: For configuration information, see Brightflag SCIM configuration guide.
- Estateably: For configuration information, see Configuring Okta Provisioning for Estateably.
- Learnerbly: For configuration information, see Integrating the Learnerbly SCIM 2.0 application in Okta for user provisioning.
New RADIUS integration
- The NetMotion Mobility RADIUS app is now available. Supported with RADIUS agent version 2.12.0 or later. See Okta RADIUS Server Agent Version History.
SAML for the following Okta Verified applications
-
CodeSignal (OKTA-333537)
-
Lexion (submitted via ISV Portal). SLA: 22/Sep/20 (OKTA-331539)
-
Mindtickle (OKTA-331529)
-
TerraTrue (OKTA-331899)
-
TransPerfect GlobalLink Dashboard (OKTA-331544)
-
Trotto Go Links (OKTA-330216)
-
WorkSafe (OKTA-334374)
Weekly Updates
Fixes
General Fixes
OKTA-296041
When searching for apps on the new Okta End-User Dashboard, all search results remained even after an app was selected.
OKTA-316869
The ShareFile app couldn't send the user.username attribute as NameID in SAML assertions.
OKTA-324814
The NetSuite app didn't display updated instance type URLs in the API integration drop down.
OKTA-330424
The Norwegian translation for the Send SMS Code MFA prompt was unclear.
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
uStudio: For configuration information, see Okta SCIM Configuration.
-
Trotto Go Links: For configuration information, see Provisioning for Trotto through Okta.
-
Verkada: For configuration information, see Okta SCIM Integration.
SAML for the following Okta Verified applications
-
Beautiful.ai (OKTA-333538)
-
Brightflag (OKTA-325633)
-
Gamma Data Leak Prevention (OKTA-335554)
-
Gremlin (OKTA-333666)
-
Learnerbly (OKTA-332872)
-
Profit.co (OKTA-321220)
-
Pudding (OKTA-333992)
-
RemotePC (OKTA-335105)
SWA for the following Okta Verified application
-
Pacific Western Bank - Business eBanking (OKTA-330791)
Fixes
General Fixes
OKTA-309244
Although users successfully signed in to a RADIUS app using Okta Verify, the System Log recorded a failed email factor event.
OKTA-322108
When self-service registration was enabled, adding a required attribute to a non-default User Type profile threw an error.
OKTA-324298
The tool tips on the Email and SMS Customization page were missing instructions on how to edit the email template.
OKTA-325353
The error message displayed when revoking the last individually assigned Super Admin was unclear.
OKTA-328337
In some cases, the new Okta End-User Dashboard wasn't translated properly.
OKTA-328953
Approval Action and Message requests were missing from the Request History section of the new Okta End-User Dashboard.
OKTA-329123
When updating user profile mappings for Okta-to-Slack provisioning, an internal server error was thrown in some cases.
OKTA-330017
In an org with self service registration enabled, a user pushed to an Active Directory group was sent two activation emails instead of one.
OKTA-332039
Okta returned a 500 Internal Server error when the LDAP agent was disconnected and users attempted to sign into Okta with an incorrect password.
OKTA-332891
One-time MFA Usage reports contained outdated information about user status and their enrolled MFA factors.
OKTA-336169
No warnings were displayed when disabling a custom URL domain.
OKTA-337002
In developer orgs, users who were trying to reset their password were sent an email that didn't contain a password reset link.
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Broadridge Website Manager: For configuration information, see Website Manager – Okta Integration – SCIM.
-
Bugsnag SAML: For configuration information, see Setup provisioning and deprovisioning (SCIM).
SAML for the following Okta Verified applications
-
Funnel.io (OKTA-335549)
-
Query.AI (OKTA-325342)
SWA for the following Okta Verified application
-
Moffi (OKTA-331031)
September 2020
2020.09.0: Monthly Production release began deployment on September 08
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
New features for SuccessFactors integration
The following new features have been added to the SuccessFactors integration:
- Time zone based pre-hires and deactivations: Admins can deactivate SuccessFactors users and import pre-hires into Okta based on the time zone of their location.
- Incremental imports: Incremental imports improve performance by importing only users who were created, updated, or deleted since the last import.
See Learn about SAP SuccessFactors Employee Central data provisioning.
Modern authentication support
We have extended our Office 365 Sign On policies to include the ability to distinguish between web browser and modern authentication clients, giving you even more granularity in controlling how users are accessing corporate data. You access this functionality by creating a new App Sign On Rule. See Get started with Office 365 sign on policies.
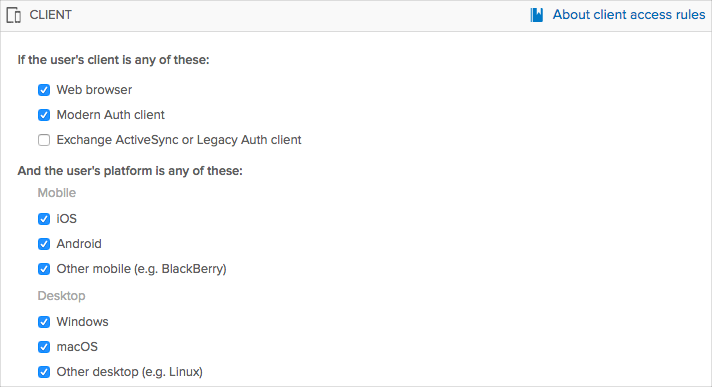
Inline Hook preview
The Inline Hook preview feature lets admins preview and validate Inline Hook requests before making them active. See Preview an inline hook .
Okta mastered attribute updates
Okta mastered attributes are now updated in a master app user profile when an org disables email customization.
Base attributes added to user profiles
When users access the Okta End-User Dashboard, all default base attributes are now added to their user profile.
Identity Provider Discovery
Using Identity Provider Discovery and routing rules, Okta directs users to different identity providers based on certain criteria. These criteria include location, device, the app being accessed, the user's domain, and specific user attributes. See Identity Provider Discovery. This feature will be gradually made available to all orgs.
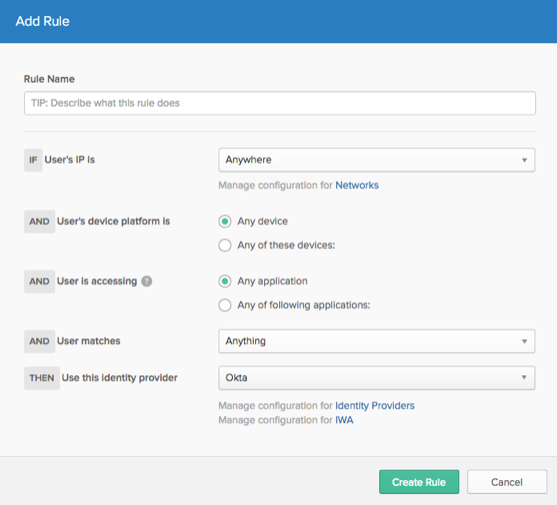
Fixes
General Fixes
OKTA-276604
Filtering groups that were pushed by group also displayed groups that were pushed by name.
OKTA-312642
On the Activate User page, Search by Group didn't work if the search term included the vertical bar sign |.
OKTA-319877
In some cases, creating a custom SAML or SWA app using a bearer token failed.
OKTA-323045
Okta Workflows didn’t restrict application assignment to super admins.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Autotask (OKTA-318506)
-
ccLink Provider Portal (OKTA-324140)
-
Chubb Personal Insurance (OKTA-323264)
-
Earth Class Mail (OKTA-322840)
-
Jobvite (OKTA-318586)
Applications
Application Updates
- The Zoom SCIM app schema is updated. See Configuring Zoom with Okta for more information.
- Provisioning support has been removed from the BigMachines and GoToMeeting apps due to their low customer usage, lack of standards based integration, and high supportability cost.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Zoom for Government: For configuration information, see Zoom for Government documentation here. Note you need appropriate Zoom permissions to view this information.
- Whimsical: For configuration information, see Setting up SCIM Provisioning with Okta.
- CultureAI: For configuration information, see Configuring OKTA.
- JumpCloud: For configuration information, see Configure Okta User Import and Password Mastery for JumpCloud.
SAML for the following Okta Verified applications
-
Australian Access Federation (OKTA-317867)
-
Estateably (OKTA-324912)
-
Hopin (OKTA-324248)
-
Signal AI (OKTA-322928)
-
SocialHP (OKTA-322572)
-
Thematic (OKTA-322576)
OIDC for the following Okta Verified applications
-
CultureAI: For configuration information, see Configuring OKTA (OpenID Connect).
-
LimbleCMMS: For configuration information, see Limble CMMS OIDC Okta Configuration Guide.
Weekly Updates
Fixes
General Fixes
OKTA-307089
When attempting to reset a user's password using the password reset link, admins received a 500 Internal Server error rather than the correct error message if the user's email address was invalid.
OKTA-318040
The voice call used for MFA with Twilio as the call provider wasn't translated in Simplified Chinese, Traditional Chinese, and Portuguese.
OKTA-321794
App Admins who were granted permissions through the group assignment API could see all apps in the OIN catalog when adding an app even though they didn't have the permissions to create them.
OKTA-324295
Inline hooks that should have updated multiple user attributes only updated one.
OKTA-326226
The Origin header value was missing from the System Log event for the user.session.start debug context.
OKTA-326955
When a geographical network zone that included Okta routers was added to an IP blacklist zone, all requests to the org were blocked.
OKTA-326962
The On-Prem MFA agent was inconsistent with other agents in how often it conducted system health checks.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Portal (Employee) (OKTA-325832)
-
Bananatag (OKTA-324700)
-
ClearCompany (OKTA-323156)
-
Ecogent (OKTA-324473)
-
Figma (OKTA-324979)
-
Fullstory (OKTA-324977)
-
LucidPress (OKTA-322083)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
Epic EMP Provisioning Connector by IDMWORKS: For configuration information, see the Okta Epic EMP Implementation Guide.
SAML for the following Okta Verified applications
-
Cloudvisor.io (OKTA-322418)
-
Indition (OKTA-321249)
-
KeySix (OKTA-322969)
-
Zenefits (OKTA-322575)
SWA for the following Okta Verified applications
-
BeyondID (OKTA-312394)
-
Tecnis (OKTA-309904)
OIDC for the following Okta Verified application
-
Leavedates: For configuration information, see Setting up Single Sign On (SSO) with Okta.
Fixes
General Fixes
OKTA-190533
Events were missing from the System Log when Identity Providers were added, updated, activated, deactivated, or deleted.
OKTA-284904
Some groups didn’t render properly under Directory > Groups after a group rule was deleted.
OKTA-328123
Importing users from SuccessFactors failed with a Java exception error.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
- SAP Litmos (OKTA-328160)
Applications
Application Update
- The AlertMedia SCIM app guide link has been updated.
- The Zepl OIDC app has been updated to include the Initiate Login URI value.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Segment: For configuration information, see System for Cross-domain Identity Management (SCIM) Configuration Guide.
- Tribeloo: For configuration information, see Okta User Provisioning Integration with SCIM.
SAML for the following Okta Verified applications
- Encoding (OKTA-296011)
- MediaPlatform (OKTA-328133)
- ProWriters Cyber IQ (OKTA-328138)
- Pubble (OKTA-322567)
- SparkPost (OKTA-326370)
- Vote.gov (OKTA-327834)
OIDC for the following Okta Verified applications
- SecurEnds: For configuration information, see SecurEnds OIDC Configuration Guide.
- Sensor Tower: For configuration information, see Sign on Securely to Sensor Tower with Okta SSO.
Fixes
General Fixes
OKTA-290250
The directNumber value wasn't correctly imported from RingCentral.
OKTA-309276
On the Add Apps page of the new Okta End-User Dashboard, the placeholder text in the search field was misleading.
OKTA-309423
On the Okta End-User Dashboard, app notes weren’t visible for bookmark apps that were assigned through self-service.
OKTA-318189
When using the LDAP interface to view user objects with empty middle names, additional spaces were present in the Common Name (CN) field even though they weren't present in the CN that was returned with an API call.
OKTA-320453
Updating a routing rule failed when a network zone was deleted before removing it from the routing rule.
OKTA-322271
On the new Okta End-User Dashboard, users could auto-launch SWA apps configured with the setting Administrator sets username, user sets password without being prompted to update their credentials.
OKTA-328536
For some orgs that stopped setting up a custom URL domain partway through the process, completing the setup later failed.
OKTA-329650
On the new Okta End-User Dashboard, some app card logos were oversized.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Alexa (OKTA-330529)
- Jobvite (OKTA-328688)
- TransUnion (OKTA-328858)
Applications
Application Update
- The Internap Portal app is deprecated. This app is rebranded as INAP.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
Shopify Plus: For configuration information, see SCIM user management for your organization.
SAML for the following Okta Verified applications
- Estateably (OKTA-324912)
- Optymyze (OKTA-326879)
- Query.ai (OKTA-325342)
SWA for the following Okta Verified applications
- Clarity (OKTA-301636)
- Horizon (OKTA-330251)
- TSheets (OKTA-322853)
OIDC for the following Okta Verified applications
- Chargifi: For configuration information, see Chargifi documentation here (you need a Chargifi account to access this documentation).
-
WarehouseTWO: For configuration information, see How to Enable Okta Login.
Fixes
General Fixes
OKTA-306373
Imports from UltiPro got stuck in the Queued status.
OKTA-309646
When adding an Access Policy to an Authorization Server, using scrollbars to navigate caused search criteria to be lost and scrollbars to disappear.
OKTA-310688
Searching groups by name on the Push Groups tab returned duplicate search results.
OKTA-315564
An internal server error was thrown and the System Log didn't record an event when sending a self-service account unlock or password reset email failed due to an invalid email recipient. A System Log event is now added to notify the admin.
OKTA-320265H
When a custom unique attribute from the Okta user profile was added to self-service registration, in certain instances user imports and creation failed.
OKTA-324204
Selecting Request Integration in the Okta Bookmark App Settings pane had no effect.
OKTA-325469
New users provisioned from Okta to DocuSign couldn’t send documents despite having correct permissions.
OKTA-325492
Reactivated users couldn’t access apps that were assigned their group while they were inactive.
OKTA-332102
User activations were logged erroneously as user.account.privilege.revoke in the System Log.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Kingsley Associates Portal (OKTA-331176)
-
MessageBird (NL) (OKTA-330524)
-
PaloAlto Networks Support (OKTA-329881)
-
Pond5 (OKTA-330614)
-
The Washington Post (OKTA-330607)
-
Trello (OKTA-330012)
-
Upwork (OKTA-331969)
-
Wells Fargo (Commercial Electronic Office) (OKTA-330311)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
-
Sparkpost: For configuration information, see SCIM User Provisioning Through Okta.
-
Gong: For configuration information, see Gong documentation here (you need a Gong account to access this documentation).
SAML for the following Okta Verified applications
- WorkSafe (OKTA-331532)
- Teubora (OKTA-330214)
-
Flock (helloflock.com) (OKTA-328135)
OIDC for the following Okta Verified application
-
Play Digital Signage: For configuration information, see OKTA Authentications with Open ID connect.
August 2020
2020.08.0: Monthly Production release began deployment on August 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
G Suite Role Management support
Admins can manage G Suite admin roles directly from the Okta Assignments tab during user create, update, or delete operations. See Google Workspace Provisioning.
Note: Customers need to contact Okta Support to migrate their Universal Directory profile template to enable this feature.
Delete OIN draft submissions
Draft submissions of app integrations in the OIN Manager portal can now be deleted. See Update your published integration.
Configurable email OTP lifetime
Admins can now set the expiration of one-time passcodes in email messages up to 30 minutes when email is enabled for multifactor authentication. See Multifactor Authentication in MFA.
Okta IWA Web agent Just-In-Time operation failures
When using Agentless Desktop Single Sign-on (DSSO) or the Okta IWA Web agent, Just-In-Time (JIT) operations fail when users are disconnected from Active Directory (AD) and the Profile & Life cycle Mastering settings don’t allow user reactivation. This behavior is expected, and consistent with JIT operations in non-IWA AD environments. See Install and configure the Okta IWA Web agent for Desktop Single Sign-on.
Group push for Active Directory
You can now use group push on the Okta Admin Console to copy groups and their members to Active Directory. See Push groups from Okta to Active Directory.
Custom TOTP Factor for MFA
Admins can now enable a custom MFA factor based on the Time-based One-time Password (TOTP) algorithm. See .
Apple as an Identity Provider
Adding Apple as an Identity Provider allows users to sign in to your app using their Apple ID. See Add an external Identity Provider.
PIV Card authentication option added to identifier first Sign In page
A PIV Card authentication option is now provided on the identifier first Sign In page when you configure a Smart Card Identity Provider and a corresponding IdP Routing Rule in the Okta Admin console. See Identity Providers.
Multiple Smart Card/PIV Card Identity Providers
Our Multiple Certificate Chain Support for PIV Auth feature allows you to leverage multiple Smart Card/PIV Card IdPs, each with different certificate chains, to allow access to a single Okta org. The correct IdP will be automatically selected based on matching the user's chosen certificate to a configured certificate chain. See Identity Providers.
End-user profile reauthentication
The Customization section has a new setting that allows an admin to set the re-authentication time when an end user edits their profile. See Configure general customization settings.
MFA for reactivated accounts
End users are now prompted for MFA before landing on the Welcome page if their accounts were reactivated and already enrolled in one or more MFA factors. This feature is currently available for new orgs only.
Extended Client Access policy capability for apps
When creating App Sign-On Policy rules to manage access to apps, admins can now specify additional granularity for platform types. Office 365 Client Access policies will continue to provide additional granularity for clients (that is, Web vs EAS). See Add Sign-On policies for applications and Office 365 Client Access Policies.
App condition for MFA enrollment policy
Admins can now use a new condition when setting a rule for an MFA enrollment policy. When this condition is configured, end users are prompted for factor enrollment when accessing all of their applications or only for those selected by their org admin. See App condition for MFA enrollment policies.
Generally Available Enhancements
System Log enhancement
When a System Log event contains more than two targets, they're now displayed in an expandable list.
Workday time zone-based user deactivation support check box
The feature that allows Workday users to be deactivated based on their local time zone is now enabled using a check box on the Workday Provisioning page. See Workday.
Improved AWS Provisioning
When a customer has an AWS instance that was configured to use the Amazon AWS IAM role as the Sign On mode, and removes an optional child account from that instance, they're warned in the UI that their role provisioning will be removed and an event is generated in the System Log.
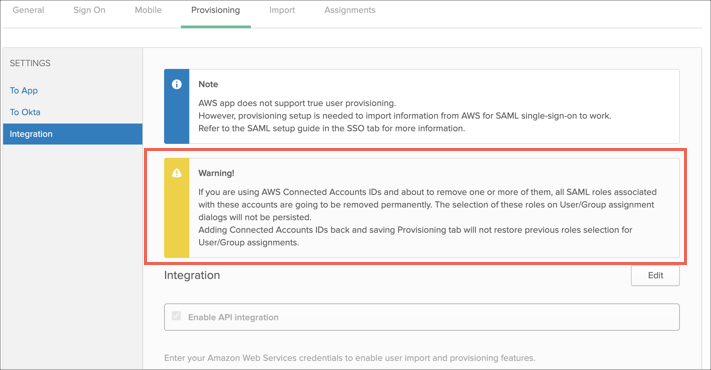
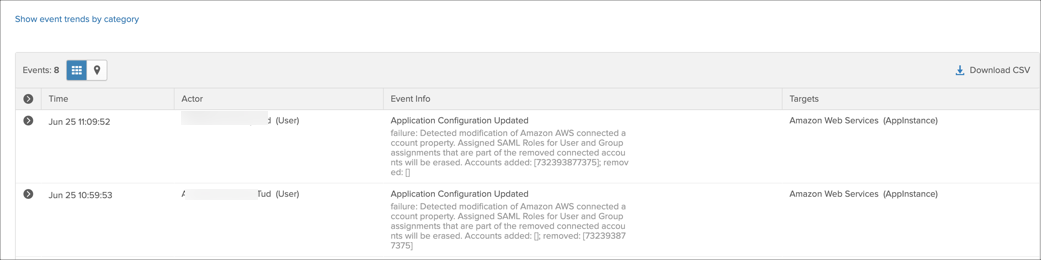
Add Administrator Group update
To prevent permission overrides, existing admin groups can only be granted new roles through the Edit option. The Add Administrator Group feature is available for new admin groups only.
OIN Manager improvements
The OIDC tab in the OIN Manager portal has been updated with new fields - a configuration guide link, additional URI tenant customization questions, and a sign-in flow option question. The improvements also include minor fixes to the UI text on the SAML tab. See Configure protocol-specific settings.
OIN Manager automated emails for discarded submissions
The OIN Manager sends an automated email to an ISV when an app integration submission is moved back to a draft state due to inaction by the ISV.
Fixes
General Fixes
OKTA-267328
Group members in a BambooHR-mastered group weren't correctly reflected into Okta after the group import.
OKTA-300889
The Remember me check box on the Sign On page didn't respond to the space key when using Firefox, Internet Explorer, or Edge.
OKTA-300957
The German translation of password policy requirements wasn't accurate.
OKTA-301352
Some Turkish characters in email templates didn't render correctly.
OKTA-303517
A user could be created without providing values for required custom arrays.
OKTA-310089
When the API Access Management feature was enabled, end users signing in to an OIDC app using Agentless Desktop SSO weren't correctly redirected to the app.
OKTA-313852
The position of the app logo was mis-aligned on the Add Application page.
OKTA-320854H
When existing apps that were incorrectly labeled as new were selected, errors occurred.
OKTA-321489H
L10N_ERROR[connector-agents] errors erroneously appeared in the UI in some Security > Multifactor sections.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Cloud Guru (OKTA-315734)
-
Google AdWords (OKTA-312421)
-
Vision Planner (OKTA-316019)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Dixa: For configuration information, see the Okta SCIM Configuration Guide.
- Netskope User Enrolllment: For configuration information, see Configuring Provisioning for Netskope.
SAML for the following Okta Verified applications
-
Coursera (OKTA-315355)
-
MediaValet (OKTA-313684)
-
Security Studio (OKTA-313793)
OIDC for the following Okta Verified application
- Map4health: For configuration information, see the Okta OIDC Configuration Guide.
Weekly Updates
Fixes
General Fixes
OKTA-265994
When, in the General tab of the Salesforce app, User Profile and Type was selected as Standard Salesforce, additional import options appeared erroneously on the Salesforce to Okta Provisioning tab.
OKTA-293366
The Profile Editor displayed incorrect length constraint instructions for usernames formats.
OKTA-301252
The Okta Browser Plugin didn't generate System Log events when users accessed an app through an SP-initiated flow.
OKTA-301760
In some cases, provisioning errors occurred in Box when selecting Group Push via User Attributes.
OKTA-304562
App admin assignments for groups weren't applied properly to RADIUS apps.
OKTA-305132
SMS messages in Chinese, Portuguese, and Dutch didn't support translation.
OKTA-310687
Groups created through Group Push erroneously showed up multiple times in the group list.
OKTA-310750
System Log events weren't logged when modifying Advanced RADIUS settings in the Sign On tab of the app.
OKTA-312588
Inbound federation for some orgs failed because metadata elements of the SAML specification were missing.
OKTA-316684
Admins couldn't create service clients without the API Access Management feature.
OKTA-317457
The User Search by first and last name on the People page didn't work as expected for all search keyword counts.
OKTA-318384
In some cases, deactivating users in Workday failed for scheduled imports.
OKTA-320235
The error message displayed when creating an admin group that already had existing admin roles was ambiguous.
OKTA-321665H
Provisioning to Office 365 using User Sync or Universal Sync failed in some cases.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe Sign Provisioning (OKTA-315230)
-
American Express - Work (OKTA-318244)
-
CenPOS (OKTA-320689)
-
Formstack (OKTA-318620)
-
PaloAlto Networks Support (OKTA-312790)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- AlertMedia: For configuration information, see How to set up SCIM-based User Provisioning with Okta.
- BrowserStack: For configuration information, contact the BrowserStack support team.
SAML for the following Okta Verified applications
-
Ally (OKTA-317614)
-
BirdEye (OKTA-314483)
-
Cequence Security (OKTA-315329)
-
Closing Folders (OKTA-315330)
-
Datasite (OKTA-313781)
-
Documo (OKTA-318832)
-
Dundas BI (OKTA-319258)
-
Ermetic (OKTA-318858)
-
Evergreen (OKTA-318831)
-
Five9 Plus Adapter for ServiceNow (OKTA-314639)
-
Jira SAML SSO by miniOrange (OKTA-304222)
-
Netskope Admin Console (OKTA-320867)
-
OwnBackup (OKTA-298672)
-
Qase (OKTA-317609)
-
Rstudio Server Pro (OKTA-312993)
-
SecureW2 (OKTA-313771)
-
TransPerfect (OKTA-303677)
-
Tribeloo (OKTA-319293)
-
Userflow (OKTA-318828)
-
Workable (OKTA-315969)
SWA for the following Okta Verified applications
-
Chubb Personal Insurance (OKTA-317081)
-
Nutanix Partner Login (OKTA-315291)
-
TerraTrue (OKTA-319285)
OIDC for the following Okta Verified application
- CloudM People Finder: For configuration information, see the CloudM configuration guide.
Fixes
General Fixes
OKTA-285972
Users encountered scrolling problems when dragging and dropping apps on the new Okta End-User Dashboard.
OKTA-313812
Help Desk and Read Only admins received false successful MFA reset confirmations for users they didn’t manage.
OKTA-318437
In orgs with Factor Sequencing enabled, customers always had password as one of the factor types in their ID token's amr claim, regardless of which factor was actually used.
OKTA-319515
On the Okta End-User Dashboard, some managed apps were listed more than once.
OKTA-320675
For some orgs with both Passwordless Authentication and Improved New Device Behavior Detection enabled, Okta treated all authentication attempts as though they came from new devices.
OKTA-325206H
Deleted Custom Domains also deleted OIDC client secrets.
OKTA-3253931H
Help Desk admins could not reset passwords.
App Integration Fixes
The following SAML apps were not working correctly and are now fixed
-
Netskope Admin Console (OKTA-322294)
-
RStudio Connect (OKTA-320865)
-
TeamzSkill (OKTA-321223)
The following SWA apps were not working correctly and are now fixed
-
Google AdWords (OKTA-319559)
-
New Relic by Account (OKTA-319755)
-
ShipStation (OKTA-319715)
Applications
Application Update
monday.com now supports the following Provisioning features (this is in addition to the other provisioning features that it already supports):
- Group Push
- Update User Attributes
- Password Sync
For configuration information, see Provisioning Configuration - Okta.
New Integrations
New SCIM Integration application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Oracle Identity Cloud Service: For configuration information, see User Provisioning from Okta to IDCS.
SAML for the following Okta Verified applications
-
Databox (OKTA-321227)
-
ENTOUCH (OKTA-321208)
-
Ramp (OKTA-312623)
-
Terraform Cloud (OKTA-315643)
OIDC for the following Okta Verified applications
-
Codestream: For configuration information, see Okta Authentication.
-
Capsule8: For configuration information, see Configuring 3rd party authentication for the Console.
Fixes
General Fixes
OKTA-294233
In some orgs configured with a custom URL domain, the password reset link provided in the custom email template redirected users to the Sign In page instead of the reset password flow.
OKTA-306130
The error message admins received when trying to add a second password inline hook was misleading.
OKTA-309244
Successfully authenticating into a Radius app using Okta Verify logged a failure event in the System Log.
OKTA-318932
Okta Confluence Authenticator dependencies caused problems with 3rd party Confluence Plug-ins using the javax.inject library. To obtain this fix, upgrade to the latest Okta Confluence Authenticator, version 3.1.4, see Okta Confluence Authenticator version history.
OKTA-323151
App notes on the Okta End-User Dashboard were misaligned.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Cisco Meraki Dashboard SAML (OKTA-322785)
-
Jobvite (OKTA-318586)
-
LucidChart (OKTA-320576)
Applications
New Integrations
SAML for the following Okta Verified applications
-
CloudSign (OKTA-316737)
-
MyCompliance (OKTA-318059)
SWA for the following Okta Verified application
-
Internap (OKTA-321035)
OIDC for the following Okta Verified applications
- Squarespace: For configuration information, see Logging in with single sign-on through Okta (Enterprise). Note: You need appropriate permissions from Squarespace to view this documentation..
- Swiftlane: For configuration information, see Swiftlane OKTA integration.
- my2be: For configuration information, see the my2be Okta Configuration Guide.
July 2020
2020.07.0: Monthly Production release began deployment on July 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
LDAP agent, version 5.6.6
This release provides the same functionality as release 5.6.5. Some default settings have been updated. See Okta LDAP Agent version history.
Reduced LDAP Interface inactive connection time out
The time out for inactive LDAP Interface connections that don't receive LDAP operations has been reduced from 120 seconds to 30 seconds, and they are now disconnected after 30 seconds of inactivity. Connections that receive an LDAP bind operation time out after 120 seconds.
Warning message added to the Import Settings page
A warning message now appears on the Active Directory Import Settings page to warn users that changing the user and group organizational unit settings can result in the deprovisioning of users.
App integration logos
The maximum size for an app integration logo has been increased from 100 KB to 1 MB. For best results, use a PNG file with a minimum resolution of 420 x 120 pixels, with landscape orientation, and with a transparent background.
Terms of Service acceptance required
Terms of Service acceptance is required from the first super admin to initiate access to OCC (Okta Cloud Connect), Developer, and Free Trial editions of Okta.
New Group Membership Admin role
The new Group Membership Admin role grants permission to view all users in an org and manage the membership of groups.
Dynamic authentication context for SAML apps
Admins can configure a custom attribute statement for SAML assertions to send user's authentication context to SAML apps during the app authentication process. The app uses this information to limit access to certain app-specific behaviors and calculate the risk profile for the signed-in user. See Pass Dynamic Authentication Context.
Prevent web browsers from saving sign-in credentials
You can prevent browsers such as Chrome from saving an end user's sign-in credentials for Okta as well as for third-party apps accessed through the Okta Dashboard. See Prevent web browsers from saving sign-in credentials.
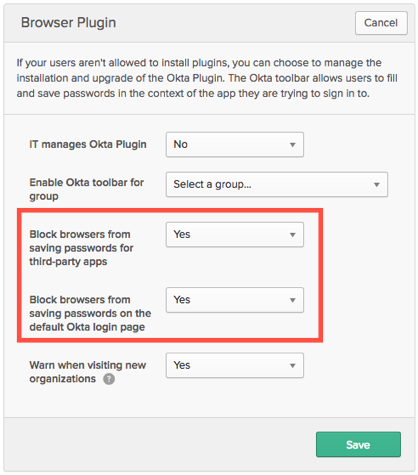
ASN Support for Dynamic Zones
Admins can now enter ASNs (Autonomous System Numbers) when creating or editing a dynamic zone. See Dynamic Zones.
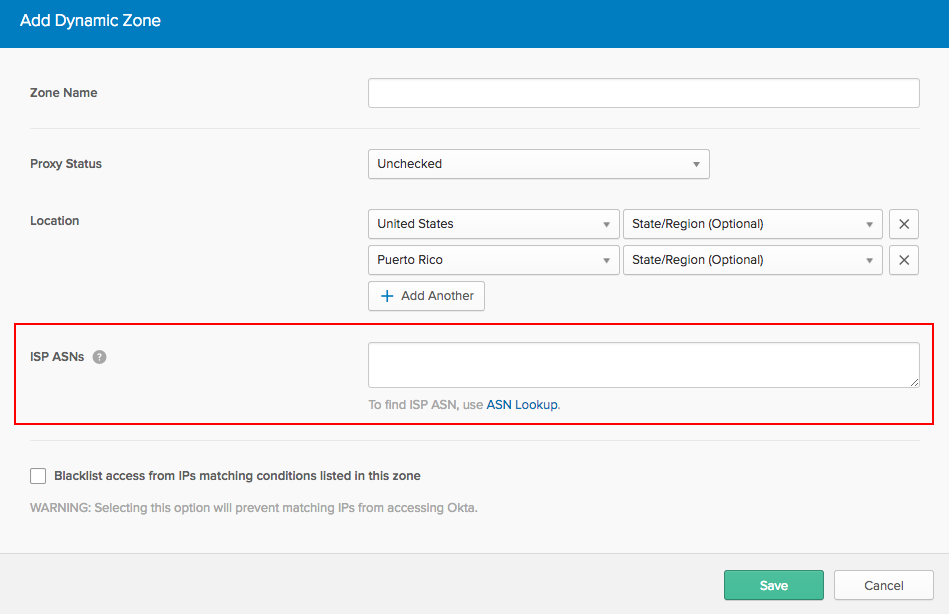
DocuSign support update
DocuSign now supports workers who have an Activation Sent status in DocuSign.
Schema Discovery for Cornerstone On Demand
The Cornerstone On Demand provisioning app now supports Universal Directory and Schema Discovery. See the Cornerstone On Demand Provisioning Guide.
Profile Sourcing and Push can be enabled together
Admins can enable both Profile Sourcing and Push for an app. This allows all Okta-to-App mappings to push, regardless of whether Active Directory is the Profile Source.
OIN Manager supports multiple application submissions
When submitting a new application integration for review by Okta, the OIN Manager now supports multiple concurrent application submissions:
Risk Scoring sign-on policy rule
Admins can now set a risk level as part of a sign-on policy rule. Setting a risk level helps determine potential security risks that are associated with an end user when they attempt to sign in to their org. This feature will be gradually made available to all orgs.
see Risk scoring.
Generally Available Enhancements
Okta Browser Plugin enhancements
The following improvements have been added to the Okta Browser Plugin:
- The plugin icon displays a green exclamation point (!) to alert users of new plugin features that have been added.
- The plugin settings highlights new opt-in features when they are made available.
- In Firefox, the Close tab button, shown to users after granting privacy-related permissions for the Okta Browser Plugin, is removed due to browser limitations.
- In Chrome, when the Offer to Save Passwords setting is controlled by a group policy, the popover setting to prevent the browser from prompting to save passwords is hidden from end-users.
Inline Hook links to Overview page
In the Okta Admin Console > Inline Hooks page, clicking an Inline Hook now directly opens the Overview page. See Inline hooks.
File size and file hash information for Okta Active Directory and LDAP agents
File size and file hash information is now provided for the Okta Active Directory and Okta LDAP agents on the Okta Admin Console > Downloads page.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-290791
Users who switched to a new app section in the Okta Browser Plugin weren't redirected to the top of that section.
OKTA-292056
The percentage listed in messages on the Okta Admin Dashboard occasionally contained an extra percentage symbol.
OKTA-292816
Group membership roles on the Assignments tab didn't reflect the actual membership roles of users in the Confluence app.
OKTA-296301
Users configuring voice call as an MFA factor were redirected to a wrong page if they refreshed the page during the setup.
OKTA-302908
Admins received a 404 error when opening the Rules tab on the Groups page in a new tab.
OKTA-304503
Users repeatedly received prompts to reinstall or update the Okta Browser Plugin regardless of its version and were given false warnings that the plugin was infected or unsafe.
OKTA-304770
The publisher for the Okta Browser Plugin for Internet Explorer was incorrectly listed as Internal Okta CA instead of Okta, Inc. in Internet Explorer > Tools > Manage add-ons.
OKTA-306546
The incorrect plugin version number was displayed for the Okta Browser Plugin in Internet Explorer > Tools > Manage add-ons.
OKTA-306663
Custom string attributes couldn't be updated for NetSuite.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Meraki Dashboard (OKTA-305864)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- ACALL: For configuration information, see User Provisioning with Okta.
- CodeSignal: For configuration information, see Configuring SCMI provisioning for Okta.
- AssetSonar: For configuration information, see Implement User Provisioning via SCIM with AssetSonar and Okta.
- eBenefitSync: For configuration information, see Configuring Provisioning for eBenefitSync.
- Horizon: For configuration information, see Setting up Horizon for Automatic Provisioning.
- Catalyser: For configuration information, see User Provisioning configuration for Okta.
- Prostore: For configuration information, see Okta Provisioning Integration.
- FaxLogic Advanced Web Client: For configuration information, see Configuring Provisioning for FaxLogic Advanced Web Client.
- FaxLogic Advanced Dashboard: For configuration information, see Configuring Provisioning for FaxLogic Administrator Dashboard.
New RADIUS integration
The Cisco Meraki RADIUS app is now available.
SAML for the following Okta Verified applications
-
Catalyser (OKTA-304474)
-
Flux (OKTA-306648)
-
InSights (OKTA-296073)
SWA for the following Okta Verified applications
-
Openpath (OKTA-296212)
-
United HealthCare Oxford (OKTA-306125)
OIDC for the following Okta Verified application
- Crelate: For configuration information, see Add Okta as a Single Sign-On Provider.
Weekly Updates
Fixes
General Fixes
OKTA-296243
Admins experienced significant delays when trying to load the Provisioning tab for custom SAML apps with SCIM provisioning.
OKTA-296456
Using the API to unlock a user that was also in a suspended state incorrectly returned a successful response.
OKTA-296598
When successfully authenticating using email as an MFA factor, users received an error message due to duplicate verification requests.
OKTA-303162
The Learn More documentation link in the Need more provisioning for this App? section of the SAML application settings was outdated.
OKTA-305486
Attributes weren't visible for some Okta-mastered users under Directory > People > User Profile > Profile.
OKTA-312218
Users using the new Okta End-User Dashboard received notifications that VPN was required when accessing apps that were configured to ignore VPN notification rules.
OKTA-312248
The Help documentation link for Office 365 Silent Activation was broken.
OKTA-312957
In some scenarios, the custom sign-in page did not properly encode all parameters.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Bloomberg (OKTA-310150)
-
Cisco Webex Meetings (OKTA-306061)
-
Concur - ProTrav (OKTA-309107)
-
Wrike (OKTA-305767)
Applications
New Integrations
SAML for the following Okta Verified applications
-
DeployGate (OKTA-305110)
-
Ebenefit Sync (OKTA-309219)
-
Procaire (OKTA-309779)
-
S&P Market Intelligence (OKTA-306170)
-
Skedda (OKTA-310320)
-
Textline (OKTA-306986)
-
User Interviews (OKTA-306649)
OIDC for the following Okta Verified application
- Nedap ONS: For configuration information, see Single Sign-On instructions.
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
NowSpace (OKTA-309446)
Mobile application for use with Okta Mobility Management (OMM) (Android)
-
AuthControl Mobile (OKTA-306981)
-
Twilio Authy (OKTA-306982)
Fixes
General Fixes
OKTA-275700
Updates to tabs managed by admins on the new Okta End-User Dashboard were incorrectly shown as banners, rather than notifications in the Notifications tab.
OKTA-294716
The Import Groups option couldn't be disabled when using Google Push Group functionality.
OKTA-296526
Report Admins were unable to view YubiKey reports due to insufficient permissions in Reports > YubiKey Report.
OKTA-298061
If an IP range was configured in a network zone that included IP addresses that are part of the Okta infrastructure, users coming from that range didn’t receive MFA prompts.
OKTA-298724
Adding an admin who already had admin roles resulted in that admin's permissions being overwritten rather than updated.
OKTA-299210
When using a custom URL domain, attempts to download metadata for an identity provider from the Okta Admin Console sometimes failed.
OKTA-302644
Address attributes from a generic OIDC identity provider weren't correctly mapped to an Okta user profile during social login.
OKTA-302876
Disabling the Import Groups option under Org2Org provisioning incorrectly created duplicate groups and threw timeout errors.
OKTA-304184
The Allow Pushing Null Values functionality of Salesforce failed when applied to the manager id field during SOAP integration.
OKTA-304895
UltiPro User Imports failed for users who were missing the External Id attribute in UltiPro.
OKTA-305272
The Group Membership Admin role was still available in the drop down under Settings > Account > Admin Email Notifications after the role was disabled.
OKTA-305287
A button linking to the Tasks page was incorrectly shown to users who had no pending tasks on the new Okta End-User Dashboard.
OKTA-306031
When setting up a custom domain that had previously been verified, uploading TLS certificates failed if the admin had skipped the domain verification step.
OKTA-307235
When trying to access an OIDC app using Desktop SSO in a Preview environment, some users experienced sign-in loops.
OKTA-313477
Some life cycle event hooks for user activation incorrectly failed because Certificate Authority endpoints were unrecognized.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Acronis Cloud (OKTA-313976)
-
Formstack (OKTA-314095)
-
Lucernex IWMS (OKTA-315510)
-
Timesheet (OKTA-311299)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Blogin: For configuration information, see Set up User Provisioning via SCIM for Okta.
- TripActions: For configuration information, see Okta SAML Provisioning. Note you need a TripActions account to access this documentation.
- Coralogix: For configuration information, see the Coralogix SCIM tutorial.
- Jostle: For configuration information, see Configuring User Provisioning with Okta.
SAML for the following Okta Verified applications
-
Appaegis Access Cloud (OKTA-310778)
-
BoostUp (OKTA-310661)
-
DEEM SAML (OKTA-291393)
-
Galaxkey (OKTA-304840)
-
Hub Planner (OKTA-312621)
-
Kiva (OKTA-303274)
-
Land Gorilla (OKTA-306647)
-
Marin One (OKTA-310324)
-
Proggio (OKTA-312282)
-
Reftab (OKTA-306646)
-
seoClarity (OKTA-312622)
-
Syxsense (OKTA-311073)
-
Zercurity (OKTA-311985)
SWA for the following Okta Verified application
-
John Hancock Pensions (OKTA-312845)
-
ManageEngine EventLog Analyzer (OKTA-309417)
-
TicketMaster (OKTA-309879)
OIDC for the following Okta Verified applications
- Hyvor Talk: For configuration information, see Hyvor Talk + Okta Integration Guide.
- Bezala: For configuration information, see Okta sign in Configuration Guide.
- Zepl OpenID Connect: For configuration information, see Configure an authentication provider in Zepl.
Mobile application for use with Okta Mobility Management (OMM) (iOS)
-
Microsoft Whiteboard (OKTA-312273)
June 2020
2020.06.0: Monthly Production release began deployment on June 8
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Deprecated metrics removed from the Okta Admin Dashboard
The following aggregated metrics have been removed from the Okta Admin Dashboard:
- Count users who have never signed in
- Count users who have signed in
- Count apps with unused assignments
- Count unused app assignments
All reports are still available. See Dashboard.
Okta Browser Plugin for Internet Explorer, version 5.38.1
This version includes the following:
- With the Okta Browser Plugin, end users can prevent browsers from prompting to save their sign-in credentials for Okta or any third-party apps accessed through the Okta End User Dashboard. See Prevent web browsers from saving sign-in credentials. Note that this feature is only available in Preview orgs.
- For the new Okta End-User Dashboard: Search in the Okta Browser Plugin is updated to have the same search accuracy as the Okta End-User Dashboard.
- Font sizes in the Okta Browser Plugin popover are updated.
Okta Browser Plugin: Password Suppression UI changes
The two plugin UI elements that configure blocking browsers from saving passwords are now managed by end users in the plugin popover, and have been removed from the Admin customization settings.
Old UI
New UI
Improvements to the Disconnect People from Active Directory page
In the Okta Admin Console, the Disconnect People from Active Directory page now displays all users and not just those from the first app instance. See Disconnect users from Active Directory.
ODSEE LDAP Support
Okta now supports Oracle Directory Server Enterprise Edition (ODSEE) LDAP integrations with the upgrade to LDAP agent version 5.6.3 and later. See Oracle Directory Server Enterprise Edition LDAP integration reference.
Extensibility Inline Hooks usage metrics
Hook metrics display all successful and unsuccessful executions of enabled Inline Hooks. Admins can use metrics to assess the performance of their hooks and troubleshoot unexpected behavior. See Inline hooks.
Generally Available Enhancements
Improved Risk Scoring model
Risk scoring evaluation has been enhanced to improve the detection of high risk sign-on activity. See Risk scoring.
Improvements to developer onboarding experience
The Okta developer site has enhanced the onboarding experience for new developers:
- Added task for customizing developer goals
- Updated text on the developer profile panel
- Added numbering to tasks
- Improved usability and process flow
File size and hash added to Downloads page
The Downloads page now displays the file size and SHA-512 hash for the RADIUS and OPP agents. Admins can use the file size and hash to verify the integrity of the files. See Install and configure the Okta RADIUS Server agent on Windows and Okta Provisioning agent and SDK version history.
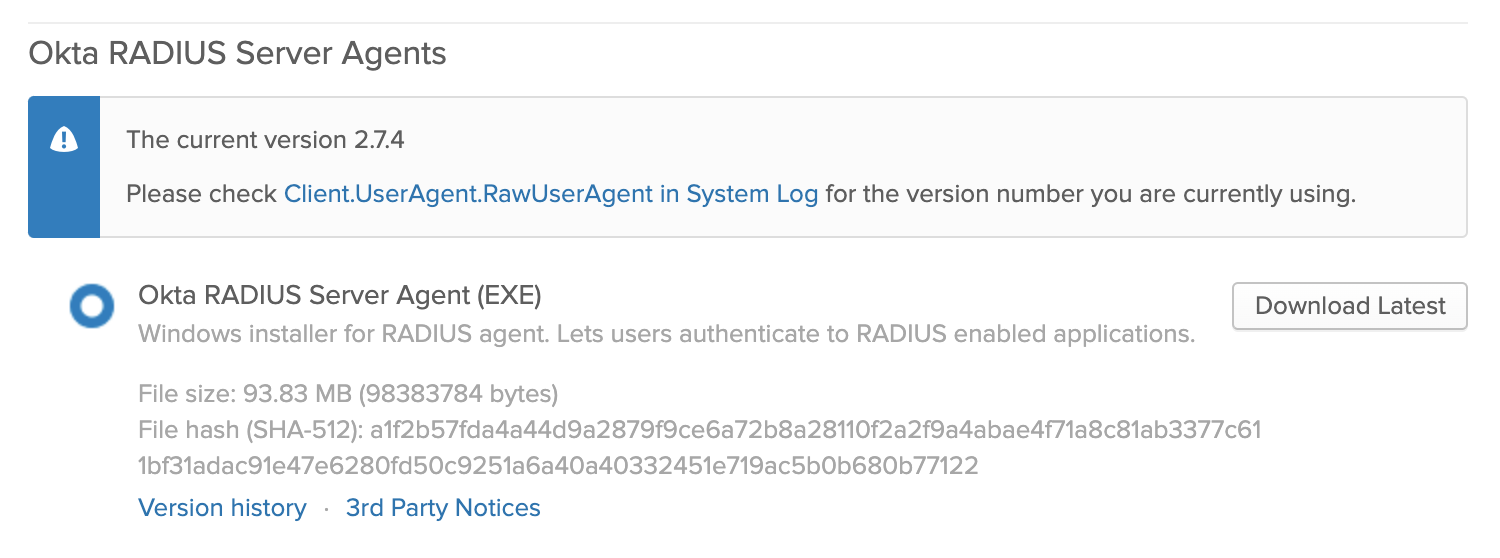
Box integration enhancement
When Box users are deactivated, and the option Transfer user’s files to account user is selected, the following warning is displayed: Caution: Files owned by the user will be inaccessible while they are being transferred. This also means that any shared content owned by the user may be inaccessible to all collaborators during the move. Depending on the volume of content, this operation may take a significant amount of time.
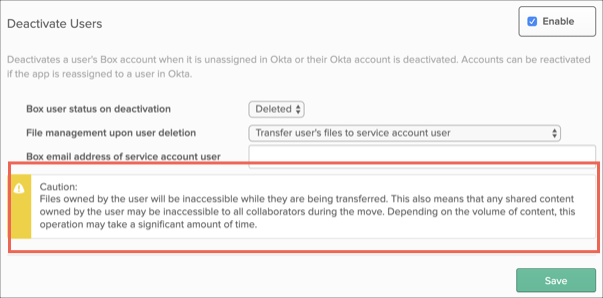
Fixes
General Fixes
OKTA-280844
In some Group Rules, if the User Attribute was very long, the value field didn't display properly.
OKTA-282532
In the new Okta End-User Dashboard, after dragging and dropping an app, end users were scrolled to the top of the dashboard.
OKTA-284835
The new Applications page used the term WS-Fed instead of WS-Federation.
OKTA-292924
User import from Workday failed if a username exceeded 100 characters.
OKTA-299093/299098
The Email as an MFA Factor for Authentication feature was not made available for some orgs when it was released earlier. Some customers who were eligible to use the Email factor with the factor API could not use the Email factor with the authentication API.
OKTA-299102
The Importing People page had the wrong documentation link.
OKTA-300069
When creating an event hook, if Subscribe to events was set to any of the Application life cycle events options, it resulted in the error Invalid list of events provided.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Acorns (OKTA-299038)
-
Adobe.com (OKTA-299039)
-
Aetna Health Insurance (OKTA-301364)
-
AT& T (OKTA-299679)
-
Bitdefender (OKTA-301600)
-
Chase (OKTA-299437)
-
Delighted (OKTA-300045)
-
Expensify (OKTA-299222)
-
iHeartRadio (OKTA-301357)
-
iOvation (OKTA-300980)
-
Jetblue (OKTA-301355)
-
Kace (OKTA-299033)
-
LucidPress (OKTA-300843)
-
Mathworks (OKTA-299040)
-
myuhc - United Healthcare (OKTA-301360)
-
Sophos Partner Portal (OKTA-300844)
-
Staples Advantage (OKTA-297714)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- AWS Single Sign-on: For configuration information, see the AWS Single Sign-on User Guide.
- Playvox: For configuration information, see Configure User Provisioning using SCIM with Okta.
SAML for the following Okta Verified application
-
Otter.ai (OKTA-298298)
OIDC for the following Okta Verified applications
- Topic: For configuration information, see How do I use Okta with Topic?
- Cato Portal: For configuration information, see Cato Networks documentation. Note: You need a Cato account to access this documentation.
- Klarity Revenue Recognition: For configuration information, see Klarity OIDC Configuration Instructions.
Weekly Updates
Fixes
General Fixes
OKTA-277693
When the Application Entitlement Policy feature was enabled and the admin was prompted to Reapply Mapping for some fields on the App Assignment page, the Username field appeared blank.
OKTA-282323
Editing the single sign-on URL for a custom SAML app sometimes resulted in an internal server error.
OKTA-286106
When the Application Entitlement Policy feature was enabled, some attribute types in the Provisioning tab of an app displayed incorrect values.
OKTA-287941
Group names and descriptions on the Assignments page were incorrectly auto-capitalized.
OKTA-287962
When using Okta Verify for MFA, users received duplicate error messages if they clicked the Verify button without entering a code.
OKTA-287972
Admins using Internet Explorer 11 didn't get user-reported suspicious activity notifications in the Okta Admin Dashboard.
OKTA-304082
Under specific conditions, a new user may have been able to login to Okta using an expired password only during the LDAP JIT flow.
OKTA-305356H
Default settings for the LDAP agent version 5.6.5 were incorrect. To obtain the new, correct default settings, please download LDAP agent version 5.6.6.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Markel Insurance (OKTA-302146)
-
Palo Alto Networks (OKTA-301935)
-
Replicon (OKTA-302143)
-
Sherweb (OKTA-302150)
-
Zscaler (OKTA-301359)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Clue: For configuration information, see SAML & SCIM Configuration Guide for Okta.
- GoLinks. For configuration information, see How to Configure SCIM Provisioning for GoLinks.
SAML for the following Okta Verified applications
-
Ally.io (OKTA-300334)
-
Clue (OKTA-299668)
-
VictorOps (Beta) (OKTA-299182)
SWA for the following Okta Verified application
-
CitiDirect BE (OKTA-298279)
OIDC for the following Okta Verified application
- Beyond Identity Admin Portal: For configuration information, see Okta SSO Access to Beyond Identity Admin Portal.
Fixes
General Fixes
OKTA-258780
Admins were unable to properly scroll in the Edit Group Assignment and Edit App User Assignment pop-up windows.
OKTA-285380
When using the override with mapping feature, username was incorrectly editable on the Profile Editor > Edit Mappings > App to Okta page.
OKTA-291912
For end user password resets, the Password is managed by a different application customization option didn't work if a custom URL domain was also configured.
OKTA-299448
When the new provisioning settings UI for Active Directory was enabled on the Active Directory Settings > Assignments tab, the Assign button was incorrectly displayed.
OKTA-299708
Some deactivated end users weren't deprovisioned from their applications.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Bank of America (OKTA-294552)
-
Barracuda Networks (OKTA-303543)
-
General Motors GlobalConnect (OKTA-303400)
-
LastPass (OKTA-303982)
-
Polygon (OKTA-304216)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- VNDLY: For configuration information, see SCIM Configuration Guide for Okta.
- Hootsuite: For configuration information, see Hootsuite SCIM Configuration Guide.
- Github Enterprise Cloud - Enterprise Accounts: For configuration information, see About SAML and SCIM with Okta.
SAML for the following Okta Verified applications
-
Greenhouse Recruiting (Subdomain) (OKTA-303238)
-
Kisi Physical Security (OKTA-303807)
-
Pymetrics (OKTA-299069)
-
TeamMood (OKTA-302178)
-
Valotalive (OKTA-298057)
OIDC for the following Okta Verified application
- Upwave: For configuration information, see the Upwave Okta Configuration guide.
Fixes
General Fixes
OKTA-292734
The System Log didn't log an entry when a push notification for MFA was sent to a user.
OKTA-297792
When using email as an MFA factor, for some languages the text on the Sign-In page didn't display properly.
OKTA-298362
Workday imports sometimes failed when the Incremental Imports feature was enabled and used with Constrained Security Users (not recommended by Okta) instead of Unconstrained Security Users.
OKTA-301607
The Cancel and Request buttons on the Request Apps dialog in the new Okta End-User Dashboard were placed too closely together.
OKTA-301654
Some icons for MFA factor resets and enrollment policies were outdated.
OKTA-305633
When requests to the /auth/services/devicefingerprint failed, users trying to authenticate got stuck on the Sign-In page.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Nice inContact (OKTA-303178)
Applications
New Integrations
SAML for the following Okta Verified applications
-
aapi (OKTA-303606)
-
Github (OKTA-304435)
-
Go Moment (OKTA-302199)
-
Ironclad (OKTA-305082)
-
ProProfs Knowledgebase (OKTA-297807)
-
Rewatch (OKTA-303581)
-
S&P CapitalIQ (OKTA-300125)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
1Password Business (OKTA-297855)
OIDC for the following Okta Verified applications
- Cortex: For configuration information, see Cortex OIDC Beta.
- Canny: For configuration information, see Okta SSO Integration.
Fixes
General Fixes
OKTA-289516
When configuring the AWS application with AWS China Connected Accounts, and then trying to save the Provisioning tab settings, the following error was displayed: The security token included in the request is invalid.
OKTA-298403
Users that were assigned custom SAML apps through group assignment incorrectly retained custom attributes in their user profiles after the group was deleted.
OKTA-300720
The interstitial page during the Agentless Desktop SSO sign-in flow incorrectly displayed a server status banner when the server was in read-only.
OKTA-303164
The Using Groups Claim documentation link in the OIDC Application Settings page was outdated.
OKTA-303168
The Learn more documentation link for SAML settings on a SAML app page > General Settings tab was outdated.
OKTA-306103
The password icon for the Okta sign-in widget was inconsistent with the look and feel of other authentication factors.
OKTA-306978
The password icon in the Okta Admin Console was outdated.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
App Store Connect (OKTA-302169)
-
YM Careers Partner (OKTA-304814)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Ironclad: For configuration information see the Ironclad + Okta + SCIM Configuration Guide.
SWA for the following Okta Verified applications
-
Kamer van Koophandel (OKTA-304857)
-
Snap-on B2B (OKTA-285600)
SAML for the following Okta Verified applications
-
Adaptive Shield (OKTA-306991)
-
Charthop (OKTA-305581)
-
Clarizen One (OKTA-306617)
-
Lightstep (OKTA-305088)
-
Segment (OKTA-304217)
-
Spendesk (OKTA-303931)
OIDC for the following Okta Verified applications
- NexPloit: For configuration information see Configure NexPloit OIDC with Okta.
- CompuMed Portal: For configuration information see the CompuMed Okta Configuration Guide.
May 2020
2020.05.0: Monthly Production release began deployment on May 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
LDAP agent, version 5.6.5
This version of the agent contains internal improvements, including updating the JDK to Amazon Corretto and eDirectory support. See Okta LDAP Agent version history.
Application Lifecycle Event Hook
Application Lifecycle events are now available for use as Event Hooks. See Event Types for a list of Events that can be used with Event Hooks.
Assign users to multiple groups in one group rule
Users can be assigned to multiple groups in one group rule. It is no longer necessary to set up multiple rules for the same criteria to accommodate different groups. See About group rules. This feature is now available for more orgs.
Rate limit behavior for SAML sign-ins
When Just-In-Time provisioning is enabled and the number of users attempting to sign in using SAML or a Social Identity Provider exceeds rate limits, Okta displays a message that it will automatically retry the JIT request after waiting a few seconds.
Disable Import Groups per app
Admins have the option to choose whether groups are included in imports from apps. This new option is available when setting up provisioning for an app.
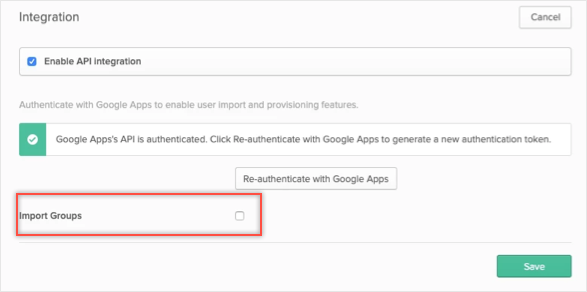
This feature should be used with care as disabling group imports will have the result of deleting all groups from the app you are configuring. As such, we provide a warning prior to disabling group imports:
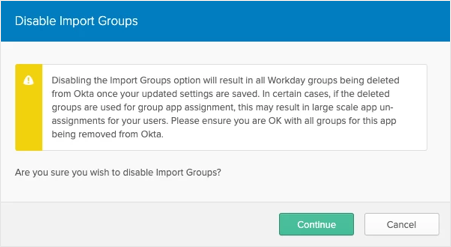
Note that you will be unable to disable group imports for an app if the following conditions exist:
- App Assignments based on Group exist
- Group policy rules exist
- Group Push mappings exist
In these cases, an error is displayed.
OIN App Catalog V2 available for Developer Edition and SKU Edition orgs
The enhanced OIN Catalog is now enabled for all new and existing Developer Edition or SKU Edition orgs.
This feature will be gradually made available to all orgs.
Enhancement: MFA phone-number enrollment restricted
End users are now prevented from enrolling premium numbers for SMS and phone multifactor authentication. Premiums numbers are those reserved for various services. In the U.S., they include numbers that begin with a zero or use area codes 900, 911, and 411. Internationally, the following phone-number types are restricted: Audiotext, Carrier selection, National rate, Premium rate, Shared cost, Satellite, and Short Code.
eDirectory LDAP support
Okta now supports eDirectory LDAP integrations with the upgrade to the LDAP agent version 5.6.2 or later. See eDirectory LDAP integration reference.
OUD LDAP Support
Okta now supports Oracle Unified Directory (OUD) LDAP integrations. See Oracle Unified Directory LDAP integration reference.
Deactivated admin users
When a user who has an admin role and privileges assigned to them is deactivated, their admin privileges are revoked. The deactivated user is removed from the Administrators page and from the CSV download list of administrators. See Administrators.
App-level safeguard
To guard against an unusual number of app un-assignments during user import, the admin can set the safeguard to org-level, app-level, or both. See Import safeguards.
This feature will be gradually made available to all orgs.
Generally Available Enhancements
New HealthInsight recommendation and updates
HealthInsight now recommends enabling Okta Verify for MFA. The existing recommendation to enable strong MFA factors now also recommends disabling weaker factors. See HealthInsight.
Copy and paste groups for admin permissions
You can now copy and paste group assignments when creating admin permissions.
Fixes
General Fixes
OKTA-210751
GitHub import into Okta only updated a subset of users.
OKTA-249695
The filter on the Directory > Profile Editor > Apps page didn't work for Org2Org and Bookmark apps.
OKTA-257761
Email templates that contain invalid or unknown expressions didn't display the right error message and were still saved.
OKTA-276226
Application group assignment windows didn't resize correctly when input was added.
OKTA-278184
In some cases, when a large number of groups were assigned to an application, assigning users to these groups took longer than usual.
OKTA-282594
Users couldn't use the arrow keys to navigate through app search results on the new Okta End-User Dashboard.
OKTA-282919
End users using the new Okta End-User Dashboard were incorrectly prompted to install or upgrade the Okta Browser Plugin even if it was IT-managed.
OKTA-284665
CSV files generated in the System Log sometimes incorrectly included carriage returns.
OKTA-284954
Search results were incorrectly sorted when searching for an app on the new Okta End-User Dashboard.
OKTA-286081
When Factor Sequencing was enabled and the authentication policy contained a method set to Password / Any IDP, the sign-in window froze when users reset their password.
OKTA-287673
Some users became stuck in an authentication loop when trying to access an app from the new Okta End-User Dashboard.
OKTA-288389
Some admins received errors when trying to approve app requests from end users made through the new Okta End-User Dashboard.
OKTA-289511
The Smart card sign-in button was visible without a Smart Card Identity Provider configured within the customer org.
OKTA-291259
Some identity providers didn't show up in the Device Identity Provider list when configuring Device Trust.
OKTA-291935
Users were prevented from disabling both app-level and org-level roadblocks.
OKTA-293240
When profile mastering was enabled, the Update application username field under the AD Provisioning settings tab didn't render correctly.
OKTA-294767
The Email as an MFA Factor feature was not made available for some orgs when it was released earlier. We are re-releasing it in 2020.05.0.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
1Password Business (OKTA-291540)
-
2020 Spaces (OKTA-293863)
-
Airship (OKTA-292749)
-
Bill.com (OKTA-292940)
-
CalPERS (OKTA-294342)
-
Cisco Webes (OKTA-292505)
-
IBM Cloud (OKTA-293426)
-
Sauce Labs (OKTA-292506)
-
Thomson Reuters MyAccount (OKTA-291630)
-
Twitter (OKTA-287886)
-
WP Engine (OKTA-293338)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- GitLab: For configuration information, see SCIM provisioning using SAML SSO for GitLab.com groups.
- Sobol: For configuration information, see Okta SCIM Setup Instructions.
- TeamMood: For configuration information, see Configure user provisioning with Okta.
SAML for the following Okta Verified applications
-
ACALL (OKTA-292094)
-
BigChange (OKTA-294316)
-
Freshworks (OKTA-290904)
-
Kintaba (OKTA-291174)
-
Lingotek (OKTA-292197)
-
Mapbox (OKTA-294374)
-
Odo (OKTA-294315)
-
Prezi (OKTA-293858)
-
Seculio (OKTA-293141)
-
Statusbrew (OKTA-292827)
SWA for the following Okta Verified application
-
Spreadshirt (OKTA-291601)
OIDC for the following Okta Verified application
- FiveToNine: For configuration information, see FiveToNine documentation (note you need appropriate permissions to view this doc).
Weekly Updates
Fixes
General Fixes
OKTA-288102
Non-Okta-mastered groups incorrectly appeared in the Application Access Audit, Okta Usage, and Application Usage reports that were intended only for Okta-mastered groups.
OKTA-294756
In some cases when the server was in Read Only mode, the interstitial page displayed an error message in the browser console log.
OKTA-298064H
Samanage (Solarwinds) changed their API for Fetch Custom Forms which resulted in errors during user import operations from Samanage.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Business Insider Prime (OKTA-295295)
-
Freshworks (OKTA-296513)
-
Hoovers (OKTA-296255)
-
HR Downloads (OKTA-295323)
-
John Hancock - MyLifeNow (OKTA-296484)
-
McMaster-Carr (OKTA-295420)
-
oDesk (OKTA-295425)
-
SEMrush (OKTA-292973)
-
Sophos Cloud (OKTA-294861)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Kintaba: For configuration information, see Okta User Provisioning (SCIM).
- LOLA: For configuration information, see Setting up SSO for Okta.
SAML for the following Okta Verified applications
-
Apperio (OKTA-294671)
-
Valimail for Twilio SendGrid (OKTA-293379)
SWA for the following Okta Verified applications
-
Amazon Marketing Services (OKTA-292908)
-
Palo Alto Networks (OKTA-291327)
OIDC for the following Okta Verified application
- Dragonboat: For configuration information, see Okta Integration: Open ID and Single Sign On.
Fixes
General Fixes
OKTA-283143
The default rule didn't follow the HealthInsight recommendation for the session lifetime for Default Policies to be two hours.
OKTA-289276
When launching Agentless Desktop Single Sign-on from a browser, the Japanese translation of the Verifying Desktop SSO message rendered incorrectly.
OKTA-296165
A banner that notifies users to trust the Okta account in the Okta Browser Plugin was missing from the new Okta End-User Dashboard.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
YardiOne Dashboard (OKTA-295097)
The following SWA apps were not working correctly and are now fixed
-
1Password Business (OKTA-298126)
-
Ebay (OKTA-296547)
-
Staples (OKTA-295631)
-
TriNet HR Passport (OKTA-296653)
The following Mobile app was not working correctly and is now fixed
-
MS Office (OKTA-296210)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Lattice: For configuration information, see Setting up SCIM with Okta.
SAML for the following Okta Verified applications
-
Blink (OKTA-296246)
-
edQuire (OKTA-295419)
-
ideiio (OKTA-293373)
-
Intercom (OKTA-292194)
-
Proggio (OKTA-278233)
-
Shopify Plus (OKTA-292196)
Fixes
General Fixes
OKTA-283868
The new Okta End-User Dashboard didn’t display the VPN Required prompt for any app that required VPN access.
OKTA-293415
Okta Support Services sign-in didn’t differentiate users based on their organization and their unique identifier.
OKTA-297532
Certificate chains that were set up with custom URL domains had key length restrictions.
OKTA-297833
The help link on the Profile Editor page on the Okta Admin Console was broken.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Cisco WebEx Meeting Center (OKTA-291966)
-
ComplianceDepot (OKTA-297545)
-
DoorDash (OKTA-297476)
-
John Hancock Pensions (OKTA-297543)
-
Lucidchart (OKTA-298005)
-
MINDBODY (OKTA-297847)
-
SalesLoft (OKTA-298142)
-
Siteimprove (OKTA-297116)
-
VSP (OKTA-297671)
-
Wayfair (OKTA-297401)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- AWS Single Sign-on: For configuration information, see What is AWS Single Sign-on.
SAML for the following Okta Verified applications
-
Anvil Riskmatics (OKTA-296063)
-
Bugfender (OKTA-297637)
-
Cirricula (OKTA-296050)
-
ComplySci (OKTA-299148)
-
Jedox (OKTA-296058)
-
Moqups (OKTA-297808)
-
MyAryaka (OKTA-285423)
-
Oracle Identity Cloud Service (OKTA-297793)
-
Roadmunk (OKTA-296251)
SWA for the following Okta Verified application
-
Template Frame Plugin App (OKTA-294358)
April 2020
2020.04.0: Monthly Production release began deployment on April 13
* Features may not be available in all Okta Product SKUs.
OAuth authentication for Workplace by Facebook
Workplace by Facebook now uses OAuth authentication instead of the custom Facebook authentication method that was used before.
Note: Existing customers have been migrated to use the new authentication method; new customers will only be able to use the new authentication method (OAuth).
Third-party admin role
Some organizations have a business need to to set up administrator roles in Okta for individuals who perform admin functions but are not direct employees of the organization. By introducing the concept of a third-party admin in Okta, we are able to treat these admins differently than the typical Okta admins who interact directly with the Okta Admin Console.
User Group Reassignments
When a user is moved to a different Okta group, that change is now reflected in Active Directory. See Enable Okta-sourced user Organizational Unit updates.
OAuth for Okta
With OAuth for Okta, you are able to interact with Okta APIs using scoped OAuth 2.0 access tokens. Each access token enables the bearer to perform specific actions on specific Okta endpoints, with that ability controlled by scopes that the access token contains. See OAuth for Okta guide.
Note that at this time, OAuth for Okta works only with the APIs listed in the Scopes & supported endpoints section of our developer docs. We are actively working towards supporting additional APIs. Our goal is to cover all Okta public API endpoints.
Dynamic SAML attribute statements for OIN apps
The Dynamic SAML feature allows admins to add and preview dynamic attribute statements to the SAML Assertion for existing OIN apps. For information how to use the SAML Attribute Statements, see Define Attribute Statements .
Email as a factor for MFA
Email is now an accepted factor for multifactor authentication for convenience and to expedite migration from legacy identity platforms. After setup, your end users receive a code in an email message to use during Okta sign in. For details on setting up this factor, see Multifactor Authentication.
User type support in Okta user profiles
Universal Directory now supports custom user types. You can customize the attributes in up to nine user types.
See About custom user types in Universal Directory.
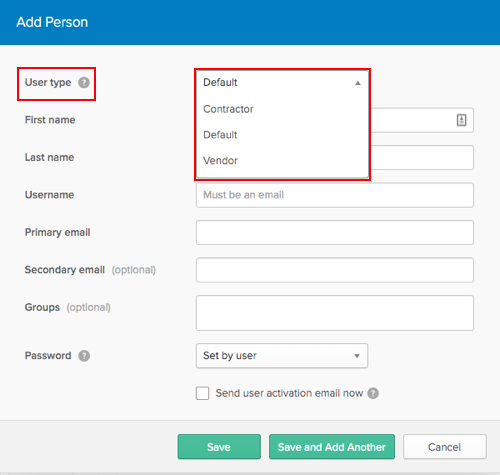
New developer on-boarding experience
An updated developer on-boarding experience has been rolled out for new development orgs. New signups will be asked a series of questions about their goals and the initial on-boarding tasks will be tailored to match these requirements.
Generally Available Enhancements
Improvements to App Search results
When searching for an integration, the App Catalog results now display the protocol and capabilities alongside the app name, rather than the associated categories. To expand the results, click See All Results.
HealthInsight recommendation for SAML-based apps
A new HealthInsight recommendation now notifies an admin of all existing SAML-based apps that aren't using SAML authentication. See Enable SAML or OIDC authentication for supported apps.
Admin CSV file name updated
The naming format for Administrator CSV files has been updated to contain the report type and the org ID.
Admin role descriptions added
Admin role descriptions have been added to the Add Administrator and Edit Administrator dialog boxes.
Google Push Group enhancement
Google Push Group functionality remains available even when the ability to import groups has been disabled. See About Group Push
Enhanced UI for network zones
The network zones UI has been enhanced to improve readability and flow for IP, location, and ASN data. See Network Zones.
New device behavior detection enhancement
The behavior detection of new devices has been updated to re-evaluate certain scenarios where a device fingerprint is missing when users sign in. See Behavior detection and evaluation.
Additional validation to curtail abuse
For free and paid developer orgs, we have added additional validation to the org name and some user profile fields to curtail abuse.
Fixes
General Fixes
OKTA-128110
When editing an administrator's roles, toggling the Super Administrator check box on and off sometimes caused the UI to mistakenly issue a warning that no roles were selected.
OKTA-262777
New SAML apps had an active SAML assertion Inline Hook assigned to them automatically.
OKTA-267840, OKTA-274937, OKTA-279424, OKTA-279458
Several UI elements contained minor translation errors (Dutch, Korean, French, and Portugese).
OKTA-274995
After an admin enabled and configured SCIM for a wizard app, then disabled SCIM, the UI element to enable SCIM disappeared.
OKTA-275270
When using the Token Preview tool, an access policy was sometimes incorrectly applied for the client credentials flow.
OKTA-278738
In some cases, a SAML assertion incorrectly included extra Attribute Statements.
OKTA-280692
The Update application username field under the Provisioning settings tab didn't render correctly when profile mastering was enabled.
OKTA-281236
The Admin CSV file didn't have the Third-Party Admin column for orgs that have enabled the third-party admin assignment settings.
OKTA-282208, OKTA-286053
Modifying the settings in the Profile and Lifecycle Mastering section of the new import and provisioning settings experience for Active Directory sometimes failed.
OKTA-282798
Error messages concerning SAML Inline Hooks sometimes didn't populate in the System Log.
OKTA-283605
Sometimes when Application Entitlement Policy and Import Sync Callback feature flags were enabled, AD-imported attributes were not updated by mapping.
OKTA-284589
The App Catalog page sometimes did not render properly when the resolution was 1024x768 or lower.
OKTA-284903
Okta internal logging didn't handle valid special characters in the log field, resulting in issues.
OKTA-286144
When Federation Broker Mode was enabled for a SAML app using encryption, attempts to SSO into that app failed with a 400 Bad Request error.
OKTA-286370
Search results for users with invalid profile data due to a schema change incorrectly resulted in a 500 error instead of a 409 conflict error.
OKTA-286419
Add Section and Edit Section Name buttons didn't function properly in the new Okta End-User Dashboard in Internet Explorer 11 and Edge. Dragging application icons functionality didn't work in Internet Explorer 11.
OKTA-286428
Some UI elements were missing from the app settings sidebar in the new Okta End-User Dashboard in Internet Explorer 11 and Edge.
OKTA-287667
The Install the plugin button didn't display consistently in Internet Explorer 11 and Edge.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Assure Sign (OKTA-284353)
-
AvaTax Admin Console (OKTA-285170)
-
Chase Mastercard (OKTA-284914)
-
Citi Credit Cards (OKTA-285965)
-
Citi Velocity (OKTA-286149)
-
Custom Report Sharing (OKTA-284638)
-
ezeep (OKTA-286381)
-
GoNoodle (OKTA-286382)
-
Meraki Dashboard (OKTA-286379)
-
Monster Hiring (OKTA-285556)
-
MyLexia (OKTA-286148)
-
Pinterest (OKTA-285778)
-
PremiumBeat (OKTA-284402)
-
Sagitta Propel Insurance (OKTA-285845)
-
Secureworks (OKTA-285995)
-
Service Channel (OKTA-286147)
-
Standout M (OKTA-284911)
-
TapInfluence (OKTA-286380)
-
TeamPassword (OKTA-286378)
-
The Business of Fashion (OKTA-280914)
-
Zapier (OKTA-284033)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Smallstep: For configuration information, see Okta isv quickstart.
- Juno: For configuration information, see Configuring Provisioning for Juno Journey.
- Contentful: For configuration information, see Okta user provisioning integration with SCIM.
- Harness: For configuration information, see Provisioning Users with Okta (SCIM).
SAML for the following Okta Verified applications
-
BlogIn (OKTA-284052)
-
DiversityEduLLC (OKTA-284062)
-
Doppler (OKTA-283629)
-
Inspire (OKTA-283636)
-
Lola (OKTA-284376)
-
MyRIACompliance (OKTA-279290)
-
Paylocity Web Pay (OKTA-285418)
-
Psono Password Manager (EE) (OKTA-284898)
-
SurveyGizmo (OKTA-282980)
-
TelemetryTV (OKTA-284380)
SAML for the following Community Created application
-
The Respond Analyst (OKTA-278325)
SWA for the following Okta Verified application
-
Membee (OKTA-268688)
Weekly Updates
Fixes
General Fixes
OKTA-267519
Several UI elements contained minor translation errors (Dutch and German).
OKTA-277075
Switching back to the old interface from the Okta End-User Dashboard didn't also switch back to the old interface for the Okta Browser Plugin as expected.
OKTA-284391
In some cases, stale data from a removed Beta feature affected the ability to toggle Okta Verify.
OKTA-284861
In some cases, where Office 365 app was configured with SWA SSO, the updated General Settings couldn't be saved.
OKTA-286132
In some cases, when Agentless Desktop SSO state token support was enabled, Agentless Desktop SSO stopped working.
OKTA-288059
When an end user enrolling in Okta Verify clicked scan the barcode again and scanned the code, an incorrect error message appeared instead of signing the user out.
OKTA-289620
In some cases, personal apps were incorrectly counted in SAML-capable apps in the HealthInsight recommendation.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Run (OKTA-283497)
-
AIA (OKTA-287940)
-
CUES (OKTA-287109)
-
Goldman Sachs Personal Financial Management (OKTA-287106)
-
Greenhouse (OKTA-288627)
-
HelloSign (OKTA-288637)
-
Microsoft Office 365 (OKTA-283156)
-
MyLevel3 (OKTA-287098)
-
MyRouteOnline (OKTA-287112)
-
Olapic (OKTA-288638)
-
RescueAssist (OKTA-287108)
-
Soundcloud (OKTA-287116)
-
Unity Asset Store (OKTA-288616)
-
Wells Fargo Funding (OKTA-286470)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Egencia (OKTA-287065)
-
k6 Cloud (OKTA-278242)
-
LogicGate (OKTA-286401)
-
MongoDB (OKTA-287432)
-
Pastel (OKTA-286360)
-
Splashtop (OKTA-284895)
-
Trelica (OKTA-288973)
SWA for the following Okta Verified applications
-
Aquera (OKTA-287101)
-
Foley (OKTA-286327)
-
Tenable.io (OKTA-287675)
-
TurboTax (OKTA-284883)
Fixes
General Fixes
OKTA-276722
Users imported from AD with a Staged status weren't automatically activated when they signed in with Just-in-Time provisioning and Interactive Windows Authentication.
OKTA-277814
Some directory logos (Directory > Directory Integrations > LDAP Integrations) didn't appear properly.
OKTA-277999
When all Behavior Detection policies for Adaptive MFA were set to Inactive, and the first rule in the sign-on policy included a risk condition, the first rule was applied without evaluating the risk score.
OKTA-279173
In some cases, when testing a SCIM connection on Okta, Okta returned an authentication error even when the certification was correctly installed on the server and was valid.
OKTA-281485
iPad versions 10 and above identified themselves as macOS devices and caused some Device Trust authentication flows to fail on those devices.
OKTA-281527
When a New Geo-location was enabled in Behavior Detection, some users received MFA prompts each time they signed in, even when they were signing in from the same location.
OKTA-282209
In some cases, the Okta Browser Plugin didn't auto-populate credentials for SWA apps using the basic authentication template.
OKTA-284330
Successful authentication responses didn't contain the sessionToken value when the response contained a state token.
OKTA-285857
When BambooHR SAML authentication was changed from API to OIDC, admins received an error when updating profiles for assigned users.
OKTA-286225
When the Workday Incremental Imports Early Access feature was enabled, incremental imports wrote null values to the uniquely mapped attributes when a user updated a Workday user profile.
OKTA-287647
A performance issue prevented Group Administrators, who manage a large number of groups, from saving additional groups in the Okta Admin Console.
OKTA-290828
Switching to another MFA factor verification sometimes failed if an Okta Verify push was already in progress.
OKTA-294630H
In some circumstances, changing an app's provisioning settings caused custom settings to revert to default values
OKTA-296659H
iPad using iOS 13.1 sometimes did not follow the login flow correctly.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
1Password Business (OKTA-288555)
-
Adobe Sign Provisioning (OKTA-285816)
-
Cisco AMP for Endpoints (OKTA-289504)
-
Cisco Webex (OKTA-291196)
-
Customer.io (OKTA-290633)
-
Drift (OKTA-290029)
-
GSA EBUY (OKTA-290030)
-
Optimal Workshop (OKTA-290827)
-
Technology Review (OKTA-290023)
Applications
New Integrations
New SCIM Integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Okta Advanced Server Access : For configuration information, see Install Advanced Server Access and create a team.
- Gong: For configuration information, see Provision team members (Okta) (you will need a Gong account to access this guide).
SAML for the following Okta Verified applications
-
Atscale (OKTA-291235)
-
AWS ClientVPN (OKTA-286416)
-
Lenses (OKTA-288610)
-
LIRNProxy (OKTA-289322)
-
Odo (OKTA-290019)
-
OpenAir (OKTA-290021)
-
Qualtrics XM (OKTA-286415)
-
Sobol (OKTA-289289)
-
SurveyGizmo (OKTA-290020)
-
Tradable Bits (OKTA-287954)
-
VNDLY (OKTA-284670)
-
Zenduty (OKTA-287957)
SWA for the following Okta Verified applications
-
Heritage Commercial Online Banking (OKTA-291006)
-
Immigration Connect by Fragomen (OKTA-286317)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Miro (formerly RealtimeBoard) (OKTA-284127)
OIDC for the following Okta Verified applications
- Edify: For configuration information, see Edify Okta Integration Setup Instructions.
- Customer.io: For configuration information, see Single Sign-on.
- infinipoint: For configuration information, see Single Sign-On to infinipoint’s platform.
March 2020
2020.03.0: Monthly Production release began deployment on March 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Changes to admin permissions
Super admins can no longer edit their own role assignment. The Edit and Delete actions are removed from their profile row on the Administrators page.
Pagination is now available when listing Authorization Servers
Pagination is now available for lists of authorization servers. See API Access Management.
Custom Email events added to the System Log
Updates to custom email templates are now tracked in the System Log.
Email verification added as optional enrollment factor
If admins configure email verification as an optional MFA factor, end users can select email as a factor during MFA enrollment. To complete enrollment, end users enter the code sent to their primary email address. The verification UI is redesigned.
Sign-in attempt behavior evaluation is logged when there is no client information
Sign-in attempt behavior evaluation is logged in the debugContext object of the user.session.start and policy.evaluate.sign_on events even when client information is missing for all behaviors.
Jira Authenticator, version 3.1.3
This release contains a bug fix for SAML SP-initiated flows, to ensure that all supported URLs redirect to Okta. See Okta Jira Authenticator Version History.
Active Directory improvements
To assist orgs with more than 10,000 Organizational Units (OUs), improvements were made to the User OUs connected to Okta and Group OUs connected to Okta fields on the Active Directory Settings page.
Mobile tab available for mobile-capable apps
The Mobile tab available in the Admin Console for mobile-capable OIN apps allows you to publish mobile applications to an App Store and deploy them to your end users. See Enable access to managed mobile apps.
Deleted admin users
When a user who has an admin role and privileges assigned to them is deleted, their admin privileges are revoked. The deleted user is removed from the Administrators page and CSV download list of administrators. For information about Admin roles, see Administrators.
Generally Available Enhancements
Salesforce integration supports pushing null values
The Salesforce integration supports pushing null values to user profile updates. To enable this functionality, select the Allow Pushing Null Values option on the Provisioning tab.
Veeva Vault integration update
The Veeva Vault integration has a new check box on the Provisioning tab that allows admins to choose whether to use Email instead of Username.
Spotlight search bar changes
The spotlight search bar is no longer visible to Report Admins because they do not have search permissions.
Accessibility enhancement for Okta Sign-in Widget
The Username and Password form fields on the Sign-In page now include the aria-required property. This property is not visible to end users, but indicates to screen readers that these fields are required.
Profile Editor improvements
The Profile Editor page has been improved to simplify navigation and clarify functionality.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-267829
App admins were able to modify all profiles in the Profile Editor even when the admin was limited to only administer certain apps.
OKTA-268943
The Okta Admin Console displayed options to delete or deactivate app instances that can't be deleted or deactivated.
OKTA-277589
When the App Catalog feature was enabled, app admins with required permissions received a blank page when they clicked the Add Application button.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Blanchard Exchange (OKTA-278301)
-
ConnectWise Automate (OKTA-278300)
-
Playbook (OKTA-279423)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- VMware Workspace ONE: For configuration information, see SCIM Provisioning from Okta to VMware Workspace ONE.
- Access LogicGate: For configuration information, see Configuring Provisioning for LogicGate.
SAML for the following Okta Verified applications
-
Halogen (OKTA-280008)
-
OneDesk (OKTA-276015)
-
Parabol (OKTA-278665)
SWA for the following Okta Verified application
-
Altair Eyewear (OKTA-277992)
Weekly Updates
Fixes
General Fixes
OKTA-235986
Searches for an app didn't yield any results in the Current Assignments report.
OKTA-259823
Password sync failed for the Org2Org app.
OKTA-263028
A 500 error instead of a 409 conflict error was thrown when searches for users failed due to invalid profile data.
OKTA-264155
In some cases, Event Hook verification failed when using certain Certificate Authorities.
OKTA-269534
Users saw an erroneous error message when they refreshed the page after completing self registration.
OKTA-271407
Admins assigned the App Admin role for selected apps were able to see private apps in the Add Application dialog.
OKTA-277954
For Preview orgs, User OUs and Group OUs failed to load the AD integrations Settings page.
OKTA-278961
Individual Admin Email Notification settings were not overwritten by global settings as expected.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
American Express Online by Concur (OKTA-281727)
-
Calpers (OKTA-281186)
-
Deltek Customer Care Connect (OKTA-281926)
-
Formstack (OKTA-280358)
-
Hippocmms (OKTA-281189)
-
MyFonts (OKTA-279931)
-
New York Magazine (OKTA-280591)
-
Office Vibe (OKTA-281190)
-
SAP Concur Solutions (OKTA-281180)
-
UserTesting (OKTA-280586)
Applications
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Retool: For configuration information, see the Retool Okta Specific Guide.
- Cisco Webex: For configuration information, see Synchronize Okta Users into Cisco Webex Control Hub.
SAML for the following Okta Verified applications
-
Axonius (OKTA-273528)
-
CrossKnowledge Learning Suite (OKTA-276017)
-
Keeni Operating Procedures (OKTA-279019)
-
Tevora Portal (OKTA-266963)
-
Virtru (OKTA-274953)
SWA for the following Okta Verified applications
-
Fisher Scientific (OKTA-279867)
-
Sagitta (OKTA-276292)
-
Thermofisher (OKTA-280605)
Fixes
General Fixes
OKTA-257061
Okta to DocuSign Provisioning mistakenly sent the same value for DocuSign attributes Title and JobTitle.
OKTA-263259
When Factor Sequencing was enabled, users that authenticated for the first time were incorrectly prompted for MFA enrollment.
OKTA-266146
Users with fewer than 13 apps were unnecessarily shown the Quick Access Apps page on the new Okta End-User Dashboard.
OKTA-267210
The new Okta End-User Dashboard redundantly displayed the Get the Plugin button.
OKTA-269649
When the meta data cache for an app was invalidated because the app was created or updated, the generated System Log event did not have a description.
OKTA-270685
When users searched for applications that didn't exist in the new Okta End-User Dashboard, the App catalog search result was empty with no message for the user.
OKTA-276950
Deleting pushed app groups in the Service Provider resulted in duplicate groups being created in Okta.
OKTA-277794
In some cases, testing a SCIM connection on Okta resulted in an authentication error.
OKTA-277802
The copyright year listed on the My Apps homepage on the new Okta End-User Dashboard was outdated.
OKTA-277898
After their session expired, end users on the new Okta End-User Dashboard were unable to access their apps instead of being prompted to sign in again.
OKTA-280874
The Edit App button on the new Okta End-User Dashboard was missing an ARIA attribute.
OKTA-282045
When a SWA app was set up with the sign-on policy Administrator sets username, password is the same as user's Okta password, end users that launched the app from the new Okta End-User Dashboard weren't properly redirected to the app sign-in page.
OKTA-282433
When apps were loading on the new Okta End-User Dashboard, end users incorrectly saw an Add apps to launcher message.
OKTA-282527
On the new Okta End-User Dashboard, the Help link in the footer incorrectly redirected to the Technical Contact even when the Help link was provided.
OKTA-283160
The Event Hook user.account.report_suspicious_activity_by_enduser was not visible in the Okta Admin Console UI.
OKTA-283333
Lists containing more than 10 IPs were not truncated in the Networks section in the Okta Admin Console.
OKTA-285079H
WebAuthN factors originally enrolled as U2F failed in some Preview orgs.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Intercom (OKTA-282204)
-
Zoho Personal (OKTA-282338)
Applications
Application Update
The SolarWinds (formerly SAManage) provisioning app now supports Token Authentication.
Note that SolarWinds will be deprecating username/password authentication support. See SolarWinds Provisioning Guide.
New Integrations
SAML for the following Okta Verified applications
-
Arkphire - Ordering Portal (OKTA-274302)
-
Clock PMS (OKTA-282395)
-
Databook (OKTA-281177)
-
HackEDU (OKTA-281019)
-
Shutterstock (OKTA-278237)
SWA for the following Okta Verified application
-
Department 31 (OKTA-277108)
Fixes
General Fixes
OKTA-245252
In some cases, the custom domain URL of an org was not honored during certificate-based primary authentication using a Personal Identity Verification (PIV) card.
OKTA-261138
In the new Admin App Catalog, expanding the search results and clicking Show more didn't correctly fetch both public and private apps.
OKTA-273907H
Some users imported from Workday using Real Time Sync were subsequently deactivated in Workday.
OKTA-282600H
Routing rules for Agentless Desktop SSO sometimes failed for OIDC apps.
OKTA-282659
The new App Catalog didn't load properly and displayed a blank page if an App Catalog endpoint was down.
OKTA-282925
In the new Admin App Catalog, the inactive Add button for an app was clickable.
OKTA-284290
The Extra Verification section on the Okta End-User Dashboard > Settings page sometimes displayed Email as a factor even when the end user's policy didn't allow it.
OKTA-284451
The download link for Okta RADIUS Server Agent for Debian (Linux) was missing from the Downloads page for orgs that had the EA agent enabled.
OKTA-286344H
The Windows Autopilot feature did not appear on the Open Betas page in Okta.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
MongoDB Cloud Manager (OKTA-282962)
Applications
New Integrations
SAML for the following Okta Verified applications
-
AssetSonar (OKTA-282381)
-
Blissfully (OKTA-280020)
-
Bridgecrew (OKTA-283634)
-
Planhat (OKTA-279291)
-
Reprise (OKTA-281179)
SWA for the following Okta Verified applications
-
1Password (OKTA-274741)
-
Saba TalentSpace (OKTA-283095)
February 2020
2020.02.0: Monthly Production release began deployment on February 18
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Active Directory, new import and provisioning settings experience
The AD settings user interface had been updated. It is now more consistent with how other application settings are configured. All orgs will now use the Okta expression language for the Okta username format field.
If your org was created before October 4th (Preview) or October 9th, 2017 (Production), a legacy expression language that is different than the Okta expression language was used for the Okta username format field. See Manage your Active Directory integration and Manage profile and attribute sourcing.
This feature will be gradually made available to all orgs.
Enhanced provisioning for Office 365
With additional enhancements to Microsoft Office 365 integration admins can now synchronize identities from on-premises to cloud-based Office 365, provision a user profile that is extended further to include over 100 attributes, as well as synchronize distribution groups, contacts, and resources such as conference rooms.
Admins can also manage user licenses and roles, independent of other provisioning flows. The new provisioning type for Office 365, License/Roles Management Only, allows admins to manage user license assignment and role delegation for existing Office 365 users and for users provisioned to Office 365 with third-party tools. For more details, see Okta Enhancements with Microsoft Office 365 Integration.
Password Import Inline Hook
The Password Import Inline Hook lets you interface with an external service to verify a user-supplied password when the user signs in to Okta for the first time. This supports scenarios in which users are migrated from an existing user store while allowing them to retain their passwords.
See Inline hooks
SAML Assertion Inline Hook now supports URI formatting in claims
Okta now supports URI claims with SAML assertion hooks. When you need to replace or add a URI claim, you must encode the claim name within the command based on the JavaScript Object Notation (JSON) Pointer specification. Specifically, this replaces ~ with ~0 and / with ~1.
See Inline hooks
Changes to admin permissions
Only super admins and org admins can edit their org's custom domain settings.
OAuth for Okta Enabled for Policy API
The Policy API now has OAuth for Okta enabled.
Sign-in widget error messaging
The error message Unable to sign in is now displayed if authentication fails when signing in to Okta.
Provisioning Capable Apps report
The Provisioning Capable Apps report contains data about available apps for orgs that can have provisioning enabled.
See Reports
Okta Browser Plugin, version 5.37.0 for all browsers
This version includes:
- New user experience for the plugin (available as an EA feature), see The new Okta end-user experience
- Fix for re-authentication modal getting stuck in some browsers
- Fix for the Firefox download link in the Okta Admin Console > Downloads page
- For Internet Explorer installer, the name Okta Secure Web Authentication Plugin changed to Okta Browser Plugin
- Back-end enhancements
Get User API Support for sort parameters
The Get User API now supports sortBy and sortOrder parameters.
New System Log event for user type changes
A new System Log event is added when the user type for an end user changes.
Send Device Context using Limited Access
Limited Access allows you to configure Okta to pass device context to certain SAML apps through the SAML assertion during app authentication. The app uses this data to limit access to certain app-specific behaviors. For more information, see Pass Device Context using Limited Access.
Enhancements to identify user addition and removal status and improve performance
The addition or removal of users from a group now runs as a background task. During the process, the Manage People button is inactive and a notification appears to indicate the progress of the request. For more information, see About group rules.
Enhancements to identify org user deactivation status and improve performance
Org user deactivation now runs as a background task. Notifications have been added to indicate request progress and successful request completion. See Activate user accounts and Deactivate and delete user accounts.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-193648
A user inadvertently retained access to an admin app when the only group/app assigned to the user was deleted.
OKTA-251904
Attributes with null or blank values were not updated to RingCentral.
OKTA-259534
When a user was locked out due to multiple failed password attempts, the UI incorrectly showed the following error message: Your account was locked due to excessive MFA attempts.
OKTA-260403
When an end user set their preferred language to Spanish, email notifications in English that were sent to the user contained a typo.
OKTA-263494
When using the SAML Assertion Inline Hook, if there was an optional attribute statement configured for the app and the attribute statement had no value specified, commands returned from SAML Inline Hook responses were not applied.
OKTA-268604
When using a custom domain, the PIV button look and feel was inconsistent on the sign-in page.
OKTA-269675
When batch imports were enabled, group memberships were sometimes not handled correctly.
OKTA-272601
Deleted OIDC App Instances still showed up as inactive in database.
App Integration Fixes
The following SAML apps were not working correctly and are now fixed
-
Qualys Guard (OKTA-270318)
-
Sage Intacct (OKTA-268392)
-
Socialbakers (OKTA-273050)
The following SWA apps were not working correctly and are now fixed
-
Adobe (OKTA-272864)
-
Adobe Creative (OKTA-272880)
-
Adobe Enterprise (OKTA-272879)
-
Apple Business Manager (OKTA-264263)
-
connectwise_automate (OKTA-272812)
-
Iola (OKTA-272811)
-
Statuspage (OKTA-272865)
Applications
Application Updates
Provisioning support has been removed from the Crashplanpro, Bloomfire, and Confluence apps due to their low customer usage, lack of standards based integration, and high supportability cost.
New Integrations
New SCIM Integration Applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Funnel: For configuration information, see Funnel Leasing OKTA SCIM Integration Guide.
- Front: For configuration information, see OKTA integration SCIM.
Note: The following apps were previously released as Early Access, but as part of our process changes the apps have now been updated and released as Generally Available, Okta Verified.
- 8x8 Inc: For configuration information, see 8x8 SCIM Configuration Guide.
- AFAS by FuseLogic: For configuration information, see Configuring Provisioning from Afas.
- AlertMedia: For configuration information, see AlertMedia SCIM Configuration Guide. Note you will need an AlertMedia account to access this guide.
- Appenate: For configuration information, see Appenate SCIM Configuration Guide. Note you will need an Appenate account to access this guide.
- Atipica: For configuration information, see Okta user provisioning integration.
- Bitly Enterprise: For configuration information, see OKTA Single Sign-On Provisioning Configuration for Bitly.
- Brivo Onair: For configuration information, see Identity Connector Integration Guide - Okta Provisioning.
- Cerner: For configuration information, see Cerner SCIM Configuration Guide. Note you will need an Cerner account to access this guide.
- Civis Platform: For configuration information, see Civis Platform SCIM Provisioning configuration guide -- Okta.
- ClearStory Data: For configuration information, see Okta User Provisioning.
- CyberArk SCIM Server: For configuration information, see Configuring Provisioning for CyberArk SCIM.
- Cybsafe: For configuration information, see CYBSAFE-Okta SCIM App Configuration.
- Databricks: For configuration information, see Configuring SCIM Provisioning for Okta.
- Druva 2.0: For configuration information, see Manage Users from Okta using SCIM.
- Egnyte SCIM 2.0: For configuration information, see Okta SSO Configuration Guide (SCIM 2.0).
- Emburse: For configuration information, see Emburse - Okta SCIM Configuration.
- Fin Analytics: For configuration information, see Using Okta for Fin SSO.
- Forecast: For configuration information, see Single Sign-On and user provisioning with Okta.
- Global Relay Identity Sync: For configuration information, see Configuring Global Relay Identity Sync for Okta (SCIM Provisioning).
- Guru: For configuration information, see SCIM Configuration Guide.
- H5mag: For configuration information, see Okta Single-Sign-On Integration Guide.
- Heureka Platform Connector: For configuration information, see Configuring Okta Connector for Heureka Intelligence Platform.
- Honey: For configuration information, see Setting up single sign-on and user provisioning through Okta.
- Infor CloudSuite: For configuration information, see Infor CloudSuite Provisioning for Okta Online Help.
- Kudos: For configuration information, see Provisioning Configuration for Kudos.
- LaunchDarkly: For configuration information, see Configuring Okta to Manage LaunchDarkly Users via SCIM.
- Leapsome: For configuration information, see User provisioning via Okta.
- Lessonly: For configuration information, see Configuring Provisioning for Lessonly.
- LogMeIn: For configuration information, see Configuring Provisioning for LogMeInProducts.
- Mavenlink: For configuration information, see Mavenlink OKTA Application Configuration Guide.
- monday.com: For configuration information, see Provisioning Configuration - Okta.
- Netskope: For configuration information, see Netskope SCIM Configuration Guide. Note you will need to request access to this guide.
- Northpass: For configuration information, contact Northpass Support.
- OpenEye Web Services: For configuration information, see Configure Okta Provisioning.
- Oracle Cloud Infrastructure: For configuration information, see Oracle Cloud Infrastructure Okta Configuration for Federation and Provisioning.
- OrgWiki (SCIM): For configuration information, see OrgWiki Okta SCIM Configuration Guide.
- PlanMyLeave: For configuration information, see Planmyleave User Provisioning using SCIM v2.
- PlusPlus: For configuration information, see Provisioning users with OKTA and SCIM.
- ProLease: For configuration information, see ProLease SCIM Setup Guide.
- Quick Base: For configuration information, see Provision Users with Okta.
- RFPIO: For configuration information, see User Provisioning OKTA Version 1.1.
- Rhombus Systems: For configuration information, see How to configure SCIM 2.0 with Okta.
- Rollbar: For configuration information, see SAML auth and SCIM provisioning with Okta.
- SalesLoft: For configuration information, see Auto-User Provisioning Integration with Okta.
- SendSafely: For configuration information, see Okta SAML SSO SCIM Provisioning.
- Sharesecret: For configuration information, see Okta SAML SSO Configuration.
- Sharpr: For configuration information, see How to Configure Provisioning for Sharpr.
- Siftrock: For configuration information, see Okta SCIM Configuration Guide.
- Sonar: For configuration information, see Configuring Provisioning for Sonar.
- SpringCM: For configuration information, see Okta SCIM and SAML Integration.
- Status Hero: For configuration information, see Configuring Okta SCIM Provisioning for Status Hero.
- Symantec Web Security Service: For configuration information, see Integrate Okta as the SAML IdP.
- Tableau Online: For configuration information, see Automate User Management through an External Identity Provider.
- TeamViewer: For configuration information, see Configure Provisioning for TeamViewer.
- Tehama: For configuration information, see SSO Okta Setup.
- Telmediq: For configuration information, see Telmediq Provisioning Guide.
- TextExpander: For configuration information, see TextExpander Okta SCIM Configuration.
- Twebcast: For configuration information, see Setup user provisioning for Twebcast with Okta.
- VidCruiter: For configuration information, see Configuring SCIM with Okta.
- Visitly: For configuration information, see Integrate with Okta provisioning.
- Workpath: For configuration information, see Okta Configuration Guide.
- Workteam: For configuration information, see Configuring User Provisioning.
- Zapier SAML: For configuration information, see Provision user accounts with SCIM.
- Zerotek: For configuration information, see SCIM Configuration Guide - v1.0.pdf.
- Zscaler 2.0: For configuration information, see SAML & SCIM Configuration Guide for Okta.
SAML for the following Okta Verified applications
-
activpayroll - activ8 (OKTA-271002)
-
Nethris (OKTA-266636)
-
Octarine (OKTA-272822)
-
Openpath Security (OKTA-272571)
-
Reachdesk (OKTA-272823)
-
Rescana (OKTA-270985)
SWA for the following Okta Verified application
-
Aquera (OKTA-272801)
Weekly Updates
Fixes
General Fixes
OKTA-275403
The System Log Advanced Search feature incorrectly listed the least common fields, rather than the most common fields, in the results.
OKTA-243812
The link text for the SolarWinds Service Desk app configuration documentation was wrong.
OKTA-250348
The .self scopes were displayed for Service clients on the Okta API Scopes page, despite the clients not having a user context.
OKTA-255236
MFA Enroll and MFA Reset emails in foreign languages contained an untranslated word.
OKTA-255878
The German translation on the Email Preview page contained incorrect capitalization.
OKTA-258904
The Dutch translation for the Phone Call factor contained a typo.
OKTA-260542
When deleting the SSPR factor on the Okta End-User Dashboard, Internet Explorer and Edge displayed a transparent window.
OKTA-266380
Import inline hooks was incorrectly triggered multiple times for the same user.
OKTA-267851
The WebAuthn(FIDO2) MFA enrollment prompt page did not support translation.
OKTA-268306
Expired AD users received different authentication errors depending on whether the Passwordless Policy was enabled or disabled.
OKTA-272891
Office 365 metadata in the /mex endpoint contained an unsupported URL that caused Single Sign-On to occassionally fail on Microsoft Dynamics CRM.
OKTA-273352
Authentication API returned a 500 error message instead of a 400 error message when the request was submitted in a SUCCESS state.
OKTA-274852
The name Import inline hook was not updated to reflect the current UI. It is now renamed as User import inline hook.
OKTA-275331
In certain SP-intiated flows, users were repeatedly prompted for credentials when ForceAuthN was requested.
OKTA-276093
When an admin's last role was revoked using the Roles API, it sometimes did not trigger a System Log event.
OKTA-276168
The autocomplete results for the field debugContext.debugData.url in the System Log Advanced Search feature affected performance and were removed. This field is still usable for queries in the System Log UI and in the Logs API.
OKTA-277609
Chromium-Edge new users who had not installed the Okta Browser plugin were displayed a banner stating that the plugin was required but the browser was unsupported.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
RightScale (OKTA-274507)
The following SWA apps were not working correctly and are now fixed
-
Apple Search Ads (OKTA-276421)
-
Brex (OKTA-276715)
-
Brex (OKTA-274478)
-
Cisco WebEx Meeting Center (OKTA-270559)
-
Director's Desk (OKTA-275986)
-
Discovery Benefits (OKTA-274220)
-
Innovative (OKTA-274248)
-
RIMS (OKTA-275987)
-
Rubicon Project (OKTA-275990)
-
Safeco (OKTA-275248)
-
Spotlight Reporting (OKTA-275991)
-
Squarespace V5 (OKTA-277555)
-
The Economist (OKTA-274254)
-
Twitter Developer (OKTA-277553)
-
Webtrends Analytics (OKTA-275988)
-
Zions Bank (OKTA-277344)
-
Zoho CRM (OKTA-274715)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps is now Generally Available in the OIN as partner-built:
- Percy: For configuration information see the Percy Okta Configuration Guide.
SAML for the following Okta Verified applications
-
Folloze (OKTA-272837)
-
Orca Security (OKTA-273918)
-
Ovio Explore (OKTA-274954)
-
Percy (OKTA-275268)
-
Topbox.io (OKTA-274250)
-
Zoho Directory (OKTA-272820)
SWA for the following Okta Verified applications
-
AccessVA ID.me (OKTA-276941)
-
AssetWorks FleetFocus (OKTA-277749)
-
Brainerd Dispatch (OKTA-274549)
-
Colorado Springs Employee Self Service (OKTA-269168)
-
Elimity (OKTA-276935)
-
IBM Sterling File Gateway (OKTA-275226)
-
PSI True Talent (OKTA-277332)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Kisi Physical Security (OKTA-276272)
OIDC for the following Okta Verified application
-
Aporeto Console: For configuration information, see Aporeto Cloud PAM and Okta OIDC Integration.
Fixes
General Fixes
OKTA-255792
Email notifications for MFA factor resets displayed no location if there was no geo-location information available for the event.
OKTA-258881
When the Factor Sequencing EA feature was enabled, some users were incorrectly switched to a new factor chain after verifying the first factor of the default factor chain.
OKTA-264155
Event Hook verification failed in some cases when using certain HTTPS certificate authorities.
OKTA-274239
Certificates that contained wildcards in CN or SAN were wrongfully considered valid for subdomain.domain.com when they were issued for *.subdomain.domain.com.
OKTA-275890
When a customer configured a dynamic attribute for an OIN SAML 2.0 app, and then Okta added an attribute with the same name to that app, both attributes were sent in the SAML assertion. The assertion should have contained the customer's dynamic attribute only.
OKTA-275981
The Russian translation for set up was incorrect in the Extra Verification settings section of the end-user dashboard.
OKTA-277702
In some cases, the IP Address field for security events was not properly populated in the System Log.
OKTA-278773
If a sign-in did not have a device fingerprint it was not treated as a new device sign-in by the behavior policy rule for new device.
OKTA-280084
Users of free and developer editions of Okta could create and send customized email templates as an Automation action.
OKTA-280571
Testing API Credentials failed when adding additional child accounts to Connected Accounts IDs (optional) in AWS -Multiple instances.
OKTA-281195H
The Max Import Unassignment setting for some integrations could not be edited.
OKTA-281501H
The Import Safeguard Percentage setting from the AD integrations UI could not be edited.
App Integration Fixes
The following SAML apps were not working correctly and are now fixed
-
G Suite (OKTA-277619)
-
Mimeo (OKTA-268673)
The following SWA apps were not working correctly and are now fixed
-
Abstract (OKTA-278327)
-
Adobe Sign Provisioning (OKTA-275000)
-
Dell Boomi (OKTA-278299)
-
GatherContent (OKTA-278914)
-
Instacart (OKTA-277552)
-
Kenshoo (OKTA-277701)
-
MURAL (OKTA-278294)
-
ReverseRisk (OKTA-277977)
-
Roadmunk (OKTA-278298)
-
SharpSprings (OKTA-277613)
-
Society of Actuaries (OKTA-278302)
-
Woobox (OKTA-278292)
-
Wrike (OKTA-278293)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Logikcull (OKTA-276909)
-
Odo (OKTA-277131)
-
Terranova Security Awareness Platform (OKTA-277333)
-
Zoomifier (OKTA-274951)
SWA for the following Okta Verified applications
-
AIB (OKTA-277420)
-
Nave Jira (OKTA-276706)
-
Titlesdesk (OKTA-277420)
January 2020
2020.01.0: Monthly Production release began deployment on January 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta Browser Plugin version 5.36.1 for Chromium-based Microsoft Edge and Mozilla Firefox
This version includes the following:
- Mozilla Firefox
- The plugin is now offered from the Mozilla Add-ons store as opposed to from Okta servers.
- Miscellaneous UI fixes.
-
Chromium-based Microsoft Edge
Okta Plugin for Chromium-based Microsoft Edge is available for download from the Microsoft Edge Store: https://microsoftedge.microsoft.com/addons/detail/ncoafaeidnkeafiehpkfoeklhajkpgij
For version history, see Okta Browser Plugin version history
New System Log event for Grant User Privilege
The Grant User Privilege System Log event now logs activity for each user in a group when an Admin role is assigned to the group.
New System Log events for OIDC scope grants
System Log events are now triggered when an administrator grants consent for OpenID Connect scopes.
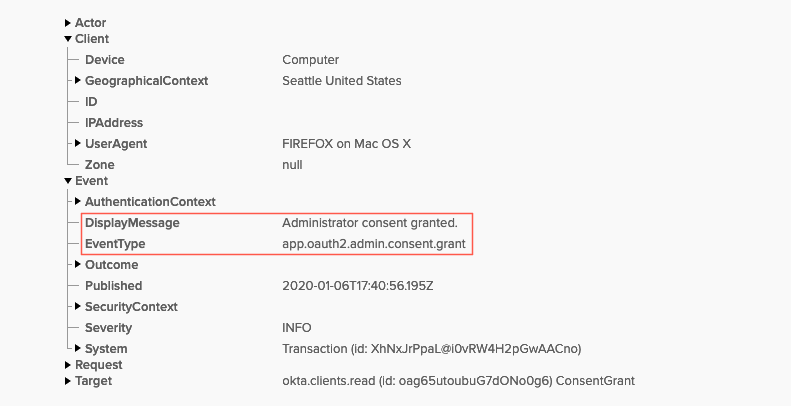
Rogue Accounts Report End of Life (EOL)
The Rogue Accounts Report feature has been removed due to low usage, high cost of maintenance, and the availability of custom solutions. For example, admins can retrieve similar data by using the List Users Assigned to Application API to see users who were assigned to an app in Okta, and then using custom code to generate a list of users assigned in the app itself. For more information, see this Support Article.
Federate multiple Office 365 domains in a single app instance
You can automatically federate multiple Microsoft Office 365 domains within a single Office 365 app instance in Okta. This eliminates the need to configure a separate Office 365 app instance for each Office 365 domain. This feature will be slowly made available to all orgs. For more information, see Federate multiple Office 365 domains in a single app instance.
Support for Salesforce Government Cloud
You can create instances of the Salesforce app that can integrate with Salesforce Government Cloud. For more details, see the Salesforce Provisioning Guide.
Box integration enhancement
The Box integration is enabled for Universal Directory and is enhanced by the following additional properties in the User Profile:
- firstName
- lastName
- timezone
- language
- space_amount (RO)
- max_upload_size (RO)
- job_title
- phone
- address
- avatar_url (RO)
- groups
- space_used (RO)
See the Box Provisioning Guide for more information.
Resumable Import
Resumable Import is a performance enhancement that prevents imports from starting over in the event of a deployment or infrastructure issue. Instead, the import automatically pauses and continues from the most recently completed step. For information on importing users, see Import users.
HealthInsight
HealthInsight audits an organization’s security settings and suggests recommended tasks to improve an org's security posture. Security tasks and recommendations are intended for admins who manage employee security within their organization.
HealthInsight may now be accessed directly from the Admin Console dashboard.
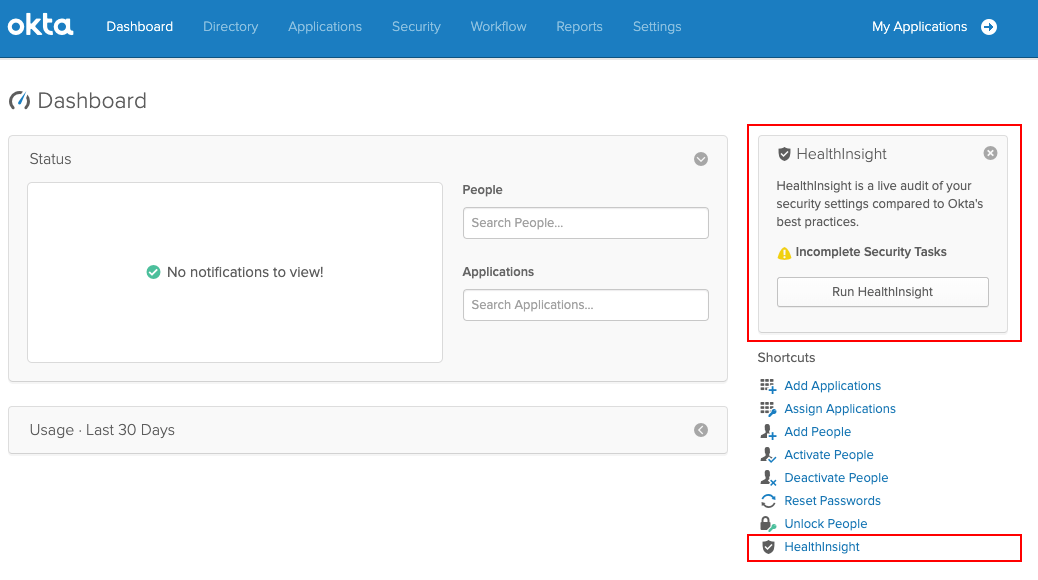
Fore more information, see HealthInsight.
App Catalog Search Improvements
The enhanced Okta Integration Network (OIN) App Catalog now features:
- A new incremental search and an improved search results preview
- Expanded search capabilities to check app integration names, descriptions, or categories
- Fuzzy search logic to match partial hits and name variations
- Tiles highlight the protocols supported by the app integration
This feature will be gradually made available to all orgs.
Generally Available Enhancements
UI Enhancements for HealthInsight
The HealthInsight card on the Admin Console dashboard and HealthInsight actions have been updated for improved usability. For more information about HealthInsight, see HealthInsight.
Additional context in MFA authentication in some apps
We have added an additional target element containing application information to MFA events triggered by authentication to Epic Hyperspace EPCS (MFA) and Microsoft RDP (MFA) apps.
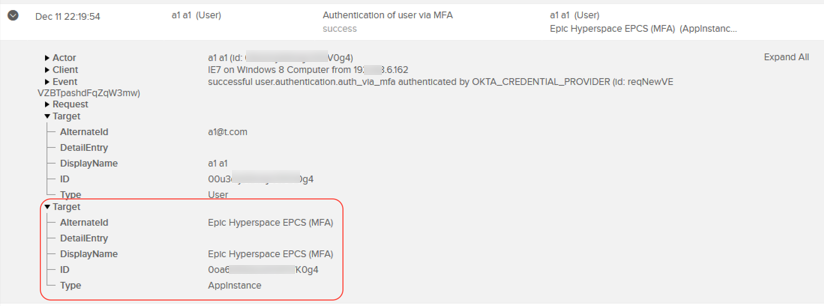
Improved text in single line challenge for RADIUS MFA
The text displayed during the a single line MFA challenge via RADIUS authentication has been improved to fixed grammatical errors.
Notification when adding a user to an Admin group
Admins now see a notification that admin privileges will be granted when adding a user to a group with Admin privileges.
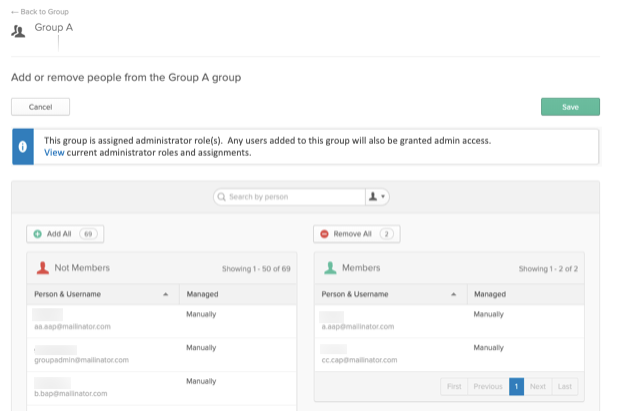
Updated Privacy Policy
Okta has updated its Privacy Policy. See https://okta.com/privacy-policy/ to review the latest version.
Condition update for MFA Enrollment policy rules
The name of the setting for the Any Application condition has been updated to specify app support for MFA Enrollment. For more information, see App condition for MFA enrollment policies.
UI enhancements for profile and attribute selection
The appearance of profile and attribute selection elements is updated to be more consistent with other Okta select elements.
Toggle on/off the end user onboarding screen
In the Settings > Appearance settings in the Admin Console, admins can control whether or not new end users see the onboarding screen upon their first sign in to the Okta End User dashboard.
This release doesn't have any Early Access features.
Fixes
General Fixes
OKTA-243820
The word Password was incorrectly translated in Dutch.
OKTA-246764
French translation for the Self-Service Unlock when Account is not Locked email template was not intuitive.
OKTA-253397
Microsoft RDP (MFA) prompts did not display the official Okta logo.
OKTA-257479
After an application was selected from the Okta Safari plugin toolbar menu, the selection window did not close as expected.
OKTA-259962
Searching for an app in App Administration Assignment did not display exact matches.
OKTA-262560
Fido 2.0 (Webauth) set as a secondary factor on Factor Sequencing failed on the user sign-in with the error We found some errors. Please review the form and make corrections.
OKTA-262649
In Okta Device Trust with VMware Workspace ONE implementations, app sign-on policy denied access on Android 10 even if the device was trusted.
OKTA-266237
App Admins who were configured to only see a subset of apps in the catalog were able to see all apps.
OKTA-267712
When creating a SAML integration using the AIW, the instructions contained the outdated acronym OAN instead of the current OIN (Okta Integration Network) acronym.
OKTA-268637
For orgs that had opted into the New Import and Provisioning Settings Experience for Active Directory EA feature, placeholder text was displayed instead of the correct text in the warning dialogue when the Profile and Lifecycle Mastering checkbox under Active Directory provisioning settings was checked and the Update Users checkbox was previously enabled.
OKTA-268720
The Settings tab for app provisioning failed to render in Internet Explorer 11.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Aha (OKTA-266200)
-
American Express Work Reconciliation (OKTA-266198)
-
Apple ID (OKTA-264195)
-
Aveda (OKTA-266196)
-
Blackbaudhost Citrix (OKTA-266199)
-
Bloomfire (OKTA-266193)
-
Brex (OKTA-266241)
-
Cisco WebEx Meeting Center (OKTA-262750)
-
Citrix RightSignature (OKTA-268537)
-
DoorDash (OKTA-268780)
-
Firefox (OKTA-266201)
-
FullContact Developer Portal (OKTA-268538)
-
Google Analytics (OKTA-266914)
-
Impraise (OKTA-268534)
-
MKB Brandstof (OKTA-267534)
-
Nest (OKTA-267942)
-
NewEgg Business (OKTA-268840)
-
OnePath Advisor (OKTA-266925)
-
Principal Financial Personal (OKTA-268782)
-
RescueTime (OKTA-266197)
-
Rhino3d (OKTA-268531)
-
Seek (AU) - Employer (OKTA-266703)
-
Shipwire (OKTA-266919)
-
Site24x7 (OKTA-268622)
-
Vindicia (OKTA-266192)
-
Wombat Security Awareness (OKTA-268532)
The following SAML app was not working correctly and is now fixed
-
Datadog (OKTA-267430)
Applications
Application Updates
- Zoom provisioning application now supports updating user email addresses.
- Citrix NetScaler Gateway has changed its name to Citrix Gateway.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Matki: For configuration information, see Provisioning with Okta.
- Clinical Maestro: For configuration information, see Clinical Maestro Okta Integration Configuration Guide.
- Cmd: For configuration information, see Okta/Cmd Configuration Guide.
SAML for the following Okta Verified applications
-
AppOmni (OKTA-266642)
-
Appsian Security Platform for PeopleSoft (Encrypted) (OKTA-265400)
-
Clinical Maestro (OKTA-264130)
-
Cmd (OKTA-266400)
-
Freshworks (OKTA-262038)
-
Grammarly (OKTA-266950)
-
Kisi Physical Security (OKTA-265701)
-
LoanBuddy (OKTA-266952)
-
Mode Analytics (OKTA-260404)
-
Reducer (OKTA-265134)
-
TeamzSkill (OKTA-265665)
SWA for the following Okta Verified application
-
Miniter (OKTA-262048)
Weekly Updates
Fixes
General Fixes
OKTA-172858
Help Desk and User admins could see the System Log page although it did not contain any events.
OKTA-239389
The Radius agent rpm uninstall command did not remove the .pid file.
OKTA-260178
Group rules that included a custom attribute based on a class name resulted in an Error in evaluating expression error.
OKTA-262628
A non-descriptive validation error was displayed when providing a non-unique value for a unique attribute during self-service registration. The error message now shows an appropriate message.
OKTA-265119
Profile Updates and User Deprovisioning did not run sequentially, which sometimes resulted in errors.
OKTA-265977
New users who tried to create an account received a 400 error when federating into applications such as Office 365.
OKTA-266061
The warning for Custom SMS stated that custom messages were limited to 160 characters instead of 159 characters.
OKTA-267419
For orgs with the latest App Catalog Search enabled, admins using Internet Explorer 11 who searched for an app to add were not redirected correctly to add applications.
OKTA-269174
The Chromium Edge Plugin store link was missing from the Downloads page in the Admin Console.
OKTA-270440H
Signing in from status.okta.com hung on the interstitial page.
OKTA-270581H
Attempts to access the HealthInsight section returned a 500 error.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Salesforce Marketing Cloud (OKTA-231271)
The following SWA apps were not working correctly and are now fixed
-
Guardian Insurance (OKTA-256039)
-
ARIN (OKTA-267889)
-
WealthEngine (OKTA-269191)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- SugarCRM (SugarIdentity): For configuration information, see Configuring SCIM for SugarIdentity With Okta.
Fixes
General Fixes
OKTA-252831
During PIV sign on, the error message for missing and invalid certificates did not instruct the user to close their browser before continuing, resulting in an error.
OKTA-253461
Attempts to use On-Prem MFA as an Authentication Method failed with a NullPointerException error.
OKTA-256707
When G-Suite is configured as Profile Master, custom attributes were not updated or imported from G-Suite apps to Okta.
OKTA-258610
Routing rules were incorrectly implemented for Chrome OS devices.
OKTA-259379
A non-existent Devices attribute for the Okta profile was displayed in the profile for Okta-mastered users.
OKTA-259826
Some users who had two sessions for the same authentication factor could become stuck in an infinite loop when they clicked the Edit Profile button on the end user dashboard.
OKTA-261365
When using Okta Verify and the LDAP Interface for authentication, rate limits sometimes caused OpenVPN account lockouts.
OKTA-261852
In specific use-cases, application-level MFA was not enforced for OIDC applications.
OKTA-262294
App assignment tasks for missing app username with AD SAM account name as the app username format were not updated after the AD SAM account name was defined for the user.
OKTA-262345
In the passwordless flow, AD users whose passwords were about to expire were not prompted to change or skip their passwords.
OKTA-262942
Okta Mobile on iOS devices that had never enrolled in the secure device mode received a session expired error after entering MFA.
OKTA-264570
A grant group privilege event was not logged when an admin role was assigned to a group of users.
OKTA-266432
The Okta Widget on the ADFS page generated a double scrolling bar when there were multiple factors available to enroll.
OKTA-267282
The browser name Chrome was logged in the System Log for newer versions of Edge.
OKTA-267492
In some cases, OAuth Clients erroneously displayed User Consent settings.
OKTA-268277
System Log events were logged for revoking user roles even when the deleted user was not assigned those roles.
OKTA-269153
SolarWinds Service Desk app API attribute mapping was sending incorrect values to Okta.
OKTA-269885
Sometimes the Self Service Registration form did not correctly display required custom properties.
OKTA-270752
When a user signs on using a PIV/CAC card, the IdP-based session timeout criteria were not applied.
OKTA-270835
Office 365 Admin Consent Flow did not respond after an admin clicked Accept.
OKTA-272110
A role to group assignment event was not logged.
OKTA-77623
The bar chart for Count of events per target displayed bars for null/unknown targets.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
OpenAir (OKTA-267934)
The following SWA apps were not working correctly and are now fixed
-
Atlassian Jira Service Desk (OKTA-271831)
-
BPF Schilders Dolphijn (OKTA-253876)
-
Concur (OKTA-266431)
-
Hilti (OKTA-251935)
-
MongoDB Cloud Manager (OKTA-272327)
-
ReadyRefresh (OKTA-270892)
-
Vonage Business (OKTA-271832)
-
Wrike (OKTA-259989)
Applications
New Integrations
New SCIM integration applications
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Threads: For configuration information see Threads SCIM Configuration Guide (Okta).
- Modes Analytics: For configuration information see How to Configure SCIM 2.
- ConveyIQ by Entelo: For configuration information see OKTA Configuration for ConveyIQ by Entelo.
- HackerRank For Work: For configuration information see Setting up SCIM Provisioning with Okta.
SAML for the following Okta Verified applications
-
BoardBookit (OKTA-270961)
-
BoardBookit Admin (OKTA-270960)
-
LogSnitch (OKTA-268634)
-
Pipedrive (OKTA-268053)
-
WEDO (OKTA-270937)
SWA for the following Okta Verified applications
-
Adesa CA (OKTA-265308)
-
Adobe (OKTA-272918)
-
Anyone Home CRM Outlook Login (OKTA-265223)
-
Bonusly (OKTA-269382)
-
CloudManager (OKTA-264840)
-
Collaboration Center (OKTA-261989)
-
ETQ Reliance (OKTA-263913)
-
Financial Accounting Support Tool (OKTA-249634)
-
Google Domains (OKTA-265048)
-
Google My Maps (OKTA-262690)
-
i-Ready (OKTA-265367)
-
New Hampshire MMIS Health Enterprise Portal (OKTA-270196)
-
NordVPN Teams (OKTA-267518)
-
USAC Applicant Login (OKTA-267402)
Mobile applications for use with Okta Mobility Management (OMM) (Android and iOS)
-
Envi MMIS (OKTA-264922)
-
Envoy (OKTA-264995
Mobile application for use with Okta Mobility Management (OMM) (iOS)
-
LiquidText (OKTA-267860)
December 2019
2019.12.0: Monthly Production release began deployment on December 16
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Okta Browser Plugin version 5.35.0 for Safari and Internet Explorer
This version includes the following:
- Bug fixes for custom URL domain support for the plugin
- Okta privacy link
- Back-end enhancements
For version history, see Okta Browser Plugin version history.
Okta Confluence Authenticator, version 3.1.2
This release contains a fix for OpenSaml initialization in OSGi environment and an update to OpenSaml library version 3.2.0. For version history, see Okta Confluence Authenticator version history
Okta SAML Toolkit for Java, version 3.1.2
This release contains a fix for OpenSaml initialization in OSGi environment and an update to OpenSaml library version 3.2.0. For version history, see Okta SAML Toolkit for Java Version History
SAML or SCIM applications created in certain developer cells can now submit to ISV portal
Developers in the OK7 developer cell who create and test SAML or SCIM applications using the App Wizard can now submit directly to the ISV portal at oinmanager.okta.com.
Increased timeout for Okta Sign In page
The initial timeout duration has been extended on the Okta Sign-In page.
ACS Limit Increased
The maximum number of Assertion Consumer Service (ACS) URLs for a SAML app is increased to 100.
LDAP Password Push
Okta now supports Password Push for LDAP. This allows each user's LDAP password to be synced to their Okta password. Any subsequent password changes users make are pushed to their user profile in LDAP. In addition to simplifying password management for orgs using LDAP, organizations using both Active Directory (AD) and LDAP can now synchronize their user passwords from AD through Okta to LDAP. For details, see the Provisioning section in Install and Configure the Okta Java LDAP Agent.
Suspicious Activity Reporting
End users can now report unrecognized activity to their org admins when they receive an account activity email notification. This feature is now available through the EA feature manager. See Suspicious Activity Reporting.
Group rules triggered by user reactivations
Group rules are now triggered when a user is reactivated. See About group rules for more information.
Multifactor Authentication for admins
MFA for Admins allows Super admins to enable mandatory multifactor authentication for all administrators accessing admin functionality. For details see Authentication.
Beta features available in Feature Manager
You can now enroll your Preview org in Open Betas in the Feature Manager. When you enroll in a Beta feature, you receive an email with further details. For details, see Manage Early Access and Beta features.
SAML Inline Hook
The SAML Inline Hook enables you to customize the authentication flow by allowing you to add attributes or modify existing attributes in outbound SAML assertions. For details, see our SAML Inline Hook page.
Admin Getting Started tasks
The new Admin Getting Started page helps super admins begin configuring their new Okta org.
For more information, see Get started with Okta.
Token Inline Hook
The Token Inline Hook enables you to integrate your own custom functionality into the process of minting OAuth 2.0 and OpenID Connect tokens. For details, see our Token Inline Hook page.
System Log events for successful Office 365 logins
A new System Log event is added when an end user successfully signs in to Office 365 using any of the Office 365 app chiclets on the dashboard.
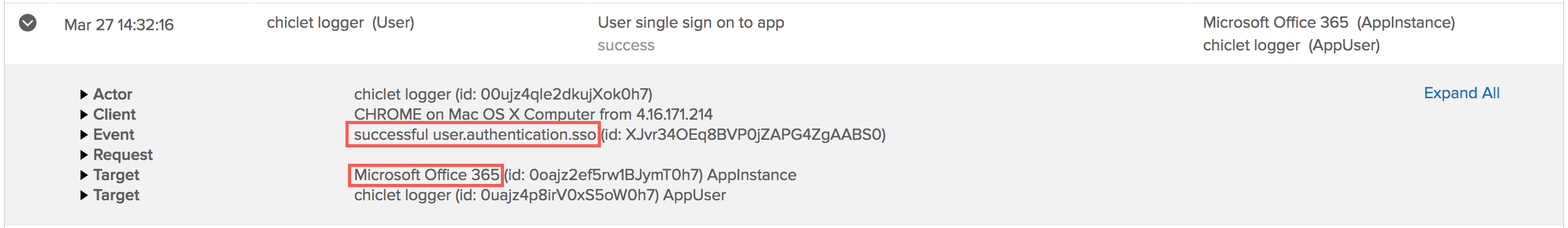
SCIM Template Apps include ISV portal link
Any apps created from the SCIM app templates display a banner that directs developers to use the ISV portal at oinmanager.okta.com to submit their SCIM app to the OIN.
SAML App Wizard change for software developers
During the creation of a SAML app with the App Wizard, software vendors receive a link to the ISV portal at oinmanager.okta.com to submit their app to the OIN. If the software vendors elect not to submit through the App Wizard, a banner appears on their app configuration page with the link to the ISV portal.
Custom URL domain support for the Okta Browser Plugin
This support enables the Okta Browser Plugin to work on the configured custom URL domain. See Configure custom URL domain.
Improved People page filter and Profile page details
We’ve added more detail to the user state labels on the People page.
And now provide the action required for users in a pending state on the User Profile page.
Generally Available Enhancements
OAuth Consent UX Enhancements
- The OAuth Consent end-user dialog has been modified to improve the user experience.
- For OAuth Scopes created for a new Authorization Server, the default values for Display Name and Description are updated to be more informative.
Select group UI enhancement
The appearance of Select Group elements are enhanced throughout the UI to be more visually intuitive and consistent with other Okta select elements:
Application Settings enhancements
- When you create a new application in the dashboard, it will be created with a default Post Logout Redirect URI (previously this field existed but defaulted to blank).
- When you create a new application of type Single Page Application (SPA), it will default to using Authorization Code with PKCE instead of defaulting to Implicit Flow.
- The Post Logout Redirect URI only impacts users using our /logout API call (not using any of our SDKs), and it is a list of possible values just like the (Login) Redirect URI.
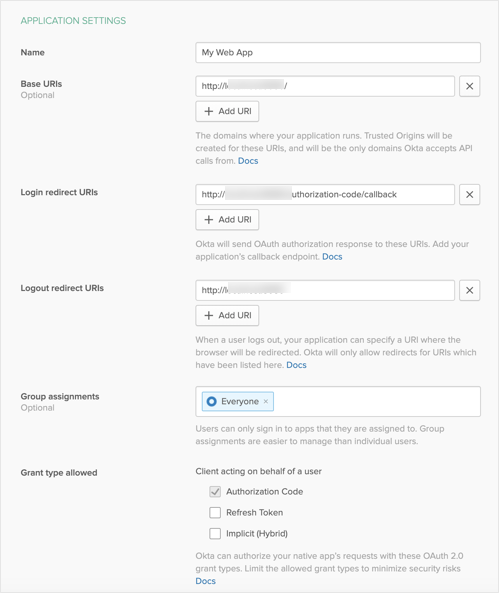
Event hooks support for MFA factor events
Event hooks are now enabled for MFA factor life-cycle events such as activating or resetting a factor.
Windows Mobile and Blackberry options removed
The option in the Okta Sign In Widget and in the End User Settings to enroll in Okta Verify or Google Authenticator using Windows Mobile or Blackberry devices is now removed.
Sorting functionality added for inline hooks and event hooks
Admins can now sort inline hooks by Status, Type, or Name, and event hooks by Verification, Status, or Name. For more information, see Inline hooks and Event hooks.
Authentication Server display name enhancement
The Authorization Server scope display name for new entries is now limited to 40 characters.
Use of admin information
Additional legal text regarding use of admin information is added to Settings > Account >Admin email notifications.
Email notification when org licensing changes
Super admins will now receive an email when their org is converted from a free trial and licensed based on a new active contract.
Addition of status text to status icons
The On-Prem MFA and RSA SecureID Agents status icons relied on color to provide status. Status is now also represented by text for improved accessibility.
Workplace by Facebook domain update
When setting up a Workplace by Facebook app, you now have the option to switch from the default org.facebook.com domain to the org.workplace.com domain.
Device fingerprinting for custom org URLs
Custom org URLs now support device fingerprinting for improved accuracy of new sign-in notifications and new device detection.
New device behavior detection
New device behavior detection is improved to provide better accuracy with new devices.
New warning modal for provisioning to apps
Admins who enable Profile Master and Push for the same app are now warned of the potential for overwritten attributes and the risk of lost data. For more information, see About profile sourcing.
This release doesn't have any Early Access features.
Fixes
General Fixes
OKTA-250443
When using Factor Sequencing, the Custom Password label did not appear in the Password field on the Sign-In page.
OKTA-251904
Okta did not update null/blank profile attributes into RingCentral.
OKTA-253324
In some cases, an incorrect System Log event of INVALID_OKTA_MOBILE_ID was logged even when OMM Device Trust was not enabled.
OKTA-256102
Country Code prefix for Kosovo was set to +undefined when enrolling SMS as a factor.
OKTA-259414
In some cases, Reapply mapping was displayed incorrectly when editing app users with an app user property that was sourced from two different groups.
OKTA-260360H
Social Login created a race condition with Self Service Registration.
OKTA-261676
LDAPi searches using a filter containing entryDN=* failed with result code 80.
OKTA-263016
For customers who opted into the New Import and Provisioning Settings Experience for Active Directory Early Access feature, if an admin entered an invalid custom expression into the AD username format field on the AD Settings page, clicking Save caused infinite loading of the page without saving the settings.
OKTA-263017
Customers who opted into the New Import and Provisioning Settings Experience for Active Directory Early Access feature could not see the UI control for previewing the result of the custom expression underneath the AD username format field when custom was chosen in the drop down.
OKTA-263915
Additional customizations applied to the ADFS site were not displayed when users accessed the ADFS second factor challenge page.
OKTA-264334
In some cases, customers importing users from Workday (as a Master) got an undefined error when executing profile matching.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Ingram Micro (OKTA-260621)
Applications
Application Updates
Provisioning support has been removed from the following apps due to low customer usage, lack of standards based integration, and high supportability cost:
- Veeva
- Replicon
- Roambi Business
- Gooddata
- Rightscale
New Integrations
New SCIM integration applications
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Getabstract: For configuration information, see the Getabstract SCIM Configuration Guide Instructions.
SAML for the following Okta Verified applications
-
Appsian Security Platform for PeopleSoft (OKTA-258107)
-
Cincopa (OKTA-260900)
-
Cisco Webex (OKTA-263286)
-
Firmex VDR (OKTA-262869)
-
Juro (OKTA-258096)
-
TripActions (OKTA-263057)
-
Wochit Studio (OKTA-263299)
Weekly Updates
Fixes
General Fixes
OKTA-252780
When a super admin canceled edits made to the email settings for an admin type, the edits were not actually canceled.
OKTA-260752
Dynamic SAML attributes appeared in read-only mode with the name, type, and value. Attributes now show only the name and value.
OKTA-261688
When adding Dynamic Attributes to a new SAML 2.0 app instance with long names or values, the text did not wrap correctly on the screen.
OKTA-261738
When creating a new SAML 2.0 app instance, the Attribute fields were auto-expanded, however the Expand button indicated that they were collapsed.
OKTA-262950
Okta Verify Push could be enabled even when Okta Verify was an inactive factor.
OKTA-264060
UNIQUE_PROPERTIES_UI caused delays and 500 errors for Postman DELETE USER API.
OKTA-264158
When OU_PICKER_V2_IN_AD_SETTINGS and AD_GROUP_PUSH were enabled, the organizational unit tree in the Push Groups tab on the AD Settings page rendered without formatting and check boxes.
OKTA-267811H
When AAD Graph API was enabled, role assignment and imports from Office365 sometimes failed.
App Integration Fixes
The following SAML apps were not working correctly and are now fixed
-
GaggleAMP (OKTA-265520)
-
NetFortris HUD Web (OKTA-264119)
-
Open Air (OKTA-252147)
The following SWA apps were not working correctly and are now fixed
-
AmericanFunds Retirement Solutions (OKTA-264261)
-
BioWorld (OKTA-265878)
-
BridgeBank Business eBanking (OKTA-263159)
-
eBay (OKTA-265287)
-
Kamer van Koophandel (OKTA-265639)
-
Mimecast (OKTA-263189)
-
Netskope (OKTA-265465)
-
Principal Advisor (OKTA-263869)
-
The Daily Beast (OKTA-266188)
-
WebRoot Anywhere (OKTA-264805)
The following Mobile apps were not working correctly and are now fixed
-
NetSuite (OKTA-263316)
-
SAP Cloud for Customer (OKTA-263312)
Applications
New Integrations
The following partner-built provisioning integration apps are now Generally Available in the OIN as Okta Verified:
- Articulate 360: For configuration information, see Configuring Provisioning for Articulate 360.
- SLIDO: For configuration information, see Configuring Provisioning for slido.
- Wellness360: For configuration information, see Configuring Provisioning for Wellness360.
- NanoLearning: For configuration information, see the Junglemap Okta user provisioning.
SAML for the following Okta Verified application
-
Blocks Edit (OKTA-264267)
SWA for the following Okta Verified applications
-
AuctionAccess (OKTA-263763)
-
Hunter Communications (OKTA-264917)
-
HYPR (OKTA-264057)
-
MKB Brandstof (OKTA-262883)
-
Savannah Morning News (OKTA-265411)
-
The Daily Beast (OKTA-264753)
Mobile applications for use with Okta Mobility Management (OMM) (Android and iOS)
-
Adobe Experience Manager (OKTA-263294)
-
FieldGlass SAML (OKTA-263295)
November 2019
2019.11.0: Monthly Production release began deployment on November 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Agentless Desktop SSO migration
Customers who enabled Agentless Desktop SSO using the registry key configuration method must migrate to the Kerberos alias supported configuration. Contact Support to enable ENG_ADSSO_MIGRATION_READINESS_CHECK which allows you to check your readiness prior to migrating.
For a list of complete migration steps refer to Migrate your agentless Desktop Single Sign-on configuration.
New System Log events for Okta user groups
System Log events have been added to indicate when Okta user groups are successfully created or deleted.
Sign-in widget for end-user factor enrollment
The sign-in widget is now displayed if an end user enrolls in a factor manually or resets a factor from the End User Dashboard settings. This feature is being released to Production orgs gradually over the month of November.
Minor visual changes to the Feature Manager
The Feature Manager user interface has been updated with minor changes including:
- The Early Access auto-enroll option is now at the bottom of the Early Access section.
- When a feature is auto-enabled in EA, the date of enrollment is listed beside the toggle switch.
Agentless Desktop SSO
Agentless desktop SSO and Silent Activation now support Kerberos alias authentication for customers implementing these features for the first time. See Configure agentless Desktop Single Sign-on and Office 365 Silent Activation: New Implementations. This feature is Generally Available in Production for new orgs only.
Web Authentication for MFA
Admins can enable Web Authentication as a factor as defined by WebAuthn standards. Web Authentication supports both security key authentication such as YubiKey devices and platform authenticators. For more information, see Multifactor Authentication.
Automations
Automations enable you to quickly prepare and respond to situations that occur during the lifecycle of end users who are assigned to an Okta group. You can set up two types of Automations and perform actions such as changing user lifecycle states and notifying users:
- Recurring Automations to check for conditions such as user inactivity and password expiration
- One-time Automations to bulk suspend and notify users belonging to a particular group irrespective of their activity
For more information, see Automations.
Required update for Microsoft Dynamics CRM, admin consent needed
We have updated the landing URL for the Microsoft Dynamics 365 app to use OAuth and to be accessible globally. The updated app resolves the issue where end-users outside the USA could not access Dynamics 365 and were redirected to an error page.
You need to provide or renew Admin consent within the Okta Office 365 app instance to continue using Dynamics 365 app in your Okta org.
Security Behavior Detection
To provide additional security without overburdening your end users, you can configure a Sign On policy for your organization to require additional authentication for behaviors defined as higher risk based on variance from individual users' prior sign ins. Admins can configure the system so that individual end users are only prompted for an additional MFA factor when there is a change in behavior that the admin defines. For more information, see Security Behavior Detection.
Generally Available Enhancements
Admin roles for groups
Admin roles can now only be granted to groups with less than 5000 members.
Admin settings for end-user suspicious activity reporting
In account settings, admins now have the option to exclude themselves or other admins from receiving user-reported notifications about suspicious account activity.
For more information, see Suspicious Activity Reporting.
WebAuthn UI enhancement
The description and icon for the WebAuthn factor have been updated both in the Admin Console and Sign-in Widget.
For more information, see Multifactor Authentication.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-212852
Group rules were not applied to reactivated users.
OKTA-221328
With Routing Rules enabled, users saw the message This is the first time you are connecting to [an application] from this browser even though they had logged in before.
OKTA-240039
With Routing Rules enabled, users saw the message This is the first time you are connecting to [an application] from this browser even though they had logged in before.
OKTA-241929
Custom TOTP factors were not supported as part of the authentication flow in Factor Sequencing.
OKTA-249465
On some web browsers, switching between Okta Verify and WebAuthn caused an error.
OKTA-254641
Changes to Max Import Unassignment settings were not logged in the System Log.
OKTA-254723
WebAuthn factor types were incorrectly named as Windows Hello in the MFA Usage Report.
OKTA-255688
The Reset via Email button on a custom sign-in page was visible and active even when that option was disabled for custom URL domains.
OKTA-257032
The Agentless Desktop SSO flow failed to authenticate users accessing custom-domain URLs.
OKTA-257269
In some cases, end users registering for Okta Verify were enrolled in One-Time Password but not in Push.
OKTA-257277
Some admins with MFA for Admin configured entered an infinite page-loading loop when signing into the Admin Console.
OKTA-257315
The HealthInsight page did not load properly for certain Okta orgs.
OKTA-56159
Re-authentication defined in sign-on policies only supported SAML-based apps and did not support SWA.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe Stock (OKTA-257769)
-
GoToWebinar (OKTA-255869)
-
Grammarly (OKTA-258776)
-
Instacart (OKTA-258045)
-
Sainsburys Groceries (OKTA-258041)
-
Twenty20 Stock (OKTA-257496)
-
Twilio (OKTA-258047)
Applications
Application Updates
Provisioning support has been removed from the following apps due to low customer usage, lack of standards based integration, and high supportability cost:
- OutSystems
- ExactTarget
- RightnowCX
- SugarCRM
New Integrations
SAML for the following Okta Verified application
-
GainsightPX (OKTA-253926)
SWA for the following Okta Verified applications
-
Ontario MC EDT (OKTA-244471)
-
ParcelQuest (OKTA-249541)
-
WatchGuard Evidence Library (OKTA-244478)
Weekly Updates
Fixes
General Fixes
OKTA-162537
The Testing IWA Web App help link on the Delegated Authentication page was broken.
OKTA-218841
End users did not receive proper credential update exceptions when there was an issue with their change password flow.
OKTA-235243
Group Push stopped on the first failure received by O365 and did not display any warnings in the System Log to indicate the issue.
OKTA-236583H
The error message for when a user was locked out did not respect the Group Password Policy settings.
OKTA-244438
In some cases a user could not be unassigned from a SCIM app if the SCIM Server had a slow response time.
OKTA-250498
Super admins were able to select the Rate limit warning and violation email notification when the feature was not enabled for their org.
OKTA-251844
Users were unable to sign in due to a 400 error that was caused by the following conditions: using Internet Explorer, using an SP-initiation SAML sign on, IDP Discovery was enabled, IWA and an MFA prompt were configured.
OKTA-257469
Due to hard validation, attempts to use group functions between profile-mastered appuser to Okta user mapping resulted in validation errors.
OKTA-260343
The Firefox plugin could not be downloaded from the Mozilla Add-ons store. The Firefox plugin version 5.34.0 is now available from the Admin Console, Settings > Downloads menu.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
BombBomb (OKTA-258406)
-
Mimecast Personal Portal v2 (OKTA-258584)
-
MyGeotab (OKTA-258044)
-
Veeva Vault (OKTA-258852)
-
WebEx Premium (OKTA-258040)
-
WP Engine (OKTA-259045)
Applications
New Integrations
The following partner-built provisioning integration apps are now Generally Available in the OIN as Okta Verified:
- Zestful: For configuration information, see Configuring Provisioning for Zestful.
- Mixpanel Provisioning: For configuration information, see Configuring SCIM Provisioning for Mixpanel with Okta.
- Web Manuals: For configuration information, see Web Manuals' Okta provisioning instructions.
- Workgrid: For configuration information, see Okta SCIM API Configuration.
- Chorus.ai: For configuration information, see Configuring Provisioning for Chorus.ai.
- Drafted: For configuration information, see Okta Provisioning (SCIM).
- ClickUp: For configuration information, see Okta SCIM Configuration Guide for ClickUp.
SAML for the following Okta Verified applications
-
Concur Travel and Expense (OKTA-254835)
-
JazzHR (OKTA-246402)
-
NetFortris HUB Web (OKTA-250307)
-
Netskope User Enrollment (OKTA-253910)
-
Portnox CLEAR (OKTA-253896)
-
Portnox CLEAR Self-onboarding (OKTA-253895)
-
Udemy for Business (OKTA-258121)
-
Vant SSO Proxy (OKTA-257483)
-
YouAttest (OKTA-259546)
SWA for the following Okta Verified applications
-
Dealerpull (OKTA-248564)
-
Encompass TPO Connect (OKTA-241362)
-
Global Database InvestmentMetrics (OKTA-245640)
-
Global Database InvestmentMetrics (OKTA-245640)
-
Informa (OKTA-245651)
-
Instacart Canada (OKTA-248835)
-
k-eCommerce (OKTA-256824)
-
Safeco Agent (OKTA-247347)
-
Southwest Traveler (OKTA-244178)
-
Stetson Insurance Funding Agent Login (OKTA-247772)
-
Street Smart by CycloMedia (OKTA-247460)
-
Transus (OKTA-247849)
Mobile applications for use with Okta Mobility Management (OMM) (Android and iOS)
-
Jive (OKTA-245483)
-
ShareFile (OKTA-260468)
Mobile application for use with Okta Mobility Management (OMM) (Android iOS)
-
Jive Communications (OKTA-245485)
Fixes
General Fixes
OKTA-247115
Some links in Suspicious Activity Reporting events did not work as expected.
OKTA-260013
The MFA Usage Report did not display some MFA factors when it was generated for all users.
OKTA-262346H
Some provisioning operations for some orgs failed with 409 errors.
OKTA-262644H
For some orgs, the Upload Logo button (Settings > Appearance) did not work.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Acronis Cloud (OKTA-261592)
-
Dell Boomi (OKTA-260860)
-
eOriginal (OKTA-260858)
-
HotSchedules (OKTA-259809)
-
Lola (OKTA-259813)
-
Nationwide Eviction (OKTA-261405)
-
Percolate (OKTA-259811)
-
U.Chicago Dist. Ctr. (OKTA-259812)
Applications
New Integrations
The following partner-built provisioning integration app is now Generally Available in the OIN as Okta Verified:
- Ooma Enterprise: For configuration information, see Configuring Provisioning for Ooma.
SAML for the following Okta Verified applications
-
PrinterLogic SaaS (OKTA-257046)
-
PTO Exchange (OKTA-259997)
SWA for the following Okta Verified applications
-
Bannockburn Global Forex (OKTA-252379)
-
Booking Admin (OKTA-257151)
-
Brex (OKTA-254738)
-
Crown Mark (OKTA-255472)
-
Dealer Daily Toyota (OKTA-253563)
-
Empower (OKTA-248283)
-
Firemax - G5 (OKTA-249415)
-
Health Assured UK (OKTA-258033)
-
Rileys eStore (OKTA-248900)
-
RUN Powered by ADP (OKTA-251863)
-
SafetySync (OKTA-248899)
-
State of California Department of Motor Vehicles (OKTA-256771)
-
Untangle (OKTA-250112)
-
Wipster (OKTA-248068)
-
WordFly (OKTA-251885)
Fixes
General Fixes
OKTA-244018
Signing out from Okta from within the password re-authentication screen caused a new Okta Sign In page to appear within the existing Okta UI.
OKTA-246083
When configured to add apps on the fly, the Okta Browser Plugin did not always offer to save credentials for some apps.
OKTA-249009
Attempts to Push Groups from Okta to ShareFile failed and produced an error.
OKTA-252921
The wrong attribute values were mapped from Okta to PagerDuty if the values limited_user or team_responder were selected in the app assignment for a user.
OKTA-253183
When an admin attempted to modify an existing admin’s role by unchecking all roles, then clicked Update Administrator, a non-user-friendly error message was returned instead of the message At least one role must be selected.
OKTA-256370
CSV imports failed when there were unique custom properties in the user profile and imported users had non-empty values set for the unique properties.
OKTA-257508
A 500 error rather than a user-friendly error was returned when an invalid factor was used during the credential authentication flow.
OKTA-257703
An application.provision.user.sync event was generated with a successful outcome before provisioning was attempted.
OKTA-258832
Imports from Confluence 7.0 failed with the error No such operation getUser.
OKTA-259741
Additional MFA factors were not enforced for Okta Mobile if an org created a sign-on policy using Okta as IDP as the priority one rule that defined additional MFA factors.
OKTA-261115
In some cases, the My Applications button was not visible on the admin console.
OKTA-262419
Not all Yubikey device names were displayed after they were enrolled for WebAuthn.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Cisco Webex Teams (OKTA-259313)
The following SWA apps were not working correctly and are now fixed
-
Adobe Reseller Console (OKTA-263079)
-
AlertLogic (OKTA-261300)
-
Apple Store (OKTA-262873)
-
Avalara CertCapture (OKTA-262331)
-
BioWorld (OKTA-262957)
-
CallTower (OKTA-262327)
-
Experian (OKTA-262329)
-
General Motors GlobalConnect (OKTA-262328)
-
Inspired eLearning (OKTA-262335)
-
Kamer van Koophandel (OKTA-262334)
-
Percipio (OKTA-262330)
-
Southwest Traveler (OKTA-262925)
-
WeWork (OKTA-261968)
-
Work Number Commercial Verifier (OKTA-261507)
Applications
New Integrations
The following partner-built provisioning integration apps are now Generally Available in the OIN as Okta Verified:
- Clearwage: For configuration information, see the Clearwage Provisioning and SSO Configuration guide.
- Vant SSO Proxy: Note: The configuration guide for this app is not public. The ISV will provide the internal link to this documentation to the engineers who will be using this integration directly.
- Book4time: For configuration information, see Book4time SCIM Setup Guide.
SAML for the following Okta Verified applications
-
KindLink (OKTA-259556)
-
Mitel Connect (OKTA-262010)
-
NetFortris HUD (OKTA-261151)
-
Netskope User Enrollment (OKTA-261565)
-
TeamzSkill (OKTA-262037)
-
Visit.org (OKTA-261400)
SWA for the following Okta Verified applications
-
Amazon ES (OKTA-259282)
-
Applied Epic Assuredpartners (OKTA-256238)
-
ASIC - Registered Agents (OKTA-260407)
-
Averon (OKTA-260126)
-
ConnectWise Automate (OKTA-252945)
-
Double Dutch Event (OKTA-256694)
-
Nx2me Clinician Portal (OKTA-259247)
-
OneNote (OKTA-259831)
-
RFPIO (OKTA-259502)
-
SALTO KEYS (OKTA-260440)
-
The Hartford Customer Service Center (OKTA-257302)
-
USA Today (OKTA-261633)
-
Welltower Portal (OKTA-254521)
-
WestJet Biz (OKTA-261389)
October 2019
2019.10.0: Monthly Production release began deployment on October 14
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Reports calendar selections limited to past 3 months
The calendar date range for a report displays the past three months only. This matches the maximum date range for report data.
Tokens transform events no longer available
Token transform System Log [events]() will no longer fire for SAML and Token inline hooks. They are retained in Inline Hook events.
See API event types.
Device Trust applies to apps in Okta Mobile for iOS
Any Device Trust policies configured in your environment are now also enforced when iOS device users access resources through Okta Mobile. This functionality is enabled by default. To change it, go to Security > General > Okta Mobile.
See Okta Mobile Settings.
Okta Browser Plugin version 5.33.0 for all browsers
This version includes the following:
- Security warning and anti-phishing whitelist
- Reflection of real-time app and profile changes in the end user dashboard
- Custom URL domain support for the plugin (available in Preview orgs)
- New look (available in beta)
- Back-end enhancements
OPP agent, version 1.3.4
This version of the OPP agent:
- Improves networking utilities and recovery speed after a DR event
- Improves log correlation between the agent and Okta
- Fixes a bug that read special characters from a CSV incorrectly
Active Directory agent, version 3.5.9
This release of the AD agent fixes an issue where meta data about Active Directory domains was not updated in Okta during imports from AD. In some cases this prevented features which rely on this meta data, for example Agentless Desktop SSO, from working correctly or being configured for the first time.
JIRA Authenticator Toolkit, version 3.1.2
This release includes the following bug fix: JIRA service failed to start after upgrading the JIRA Authenticator from 3.0.7 to 3.1.1.
Okta Browser Plugin reflects real-time app and profile changes in the end user dashboard
The Okta Browser Plugin now reflects the real-time state of the end user dashboard, eliminating the need to refresh the dashboard for the plugin to reflect the latest app and profile changes. This feature is available on Okta Browser Plugin version 5.29.0 or higher. For more information, see About the Okta Browser Plugin.
App condition for MFA enrollment policy
Admins can now use a new condition when setting a rule for an MFA enrollment policy. When this condition is configured, end users are prompted for factor enrollment when accessing all of their applications or only for those selected by their org admin. For more information, see App condition for MFA enrollment policies.
Add event hooks from the Admin Console
Admins can now add event hooks from the Admin Console. Event hooks send outbound calls from Okta that trigger asynchronous process flows in admins' own software. For more details, see Event hooks.
Generally Available Enhancements
Adobe CQ Enhancement
You can specify whether to ignore inactive users or not during imports to/from Adobe CQ.
Group Admin behavior change
When a group admin with permissions to manage a single group adds a new user to the org, the group name is automatically populated.
New System Log event for email challenge
The new event now includes more debugData information to indicate whether an email challenge was answered (redeemed) using the same browser from which it was initiated.
Scope Naming Restriction
OAuth Scopes may not start with the okta. prefix. See Create scopes.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-220377
When assigning users to Microsoft Office 365, a Profile push error message was displayed. Users could still sign in and their profiles were updated correctly.
OKTA-221078, OKTA-231642
When Okta MFA for Azure AD Conditional Access was enabled, admins were unable to configure Microsoft Office 365 using the I want to configure WS-Federation myself using PowerShell option.
OKTA-233578
Deactivated users were imported from Adobe CQ.
OKTA-235187
In OAuth 2.0/OIDC /authorize request, the Okta Sign-In Widget incorrectly rendered the login_hint parameter, substituting + with a space.
OKTA-236849
Users were unable to sign in to the GoAnywhere SWA app automatically and had to enter their credentials manually.
OKTA-237085
Admins could not add an IP to a Network Zone in the System Log if there were more than 20 Network Zones. Only the first 15 zones were displayed.
OKTA-240197
The group icon for the Namely app was incorrectly displayed on the Directory > Groups page.
OKTA-240375
MFA factor enrollment policies were not enforced when Factor Sequencing was enabled.
OKTA-243056
When admins removed a user from a group with more than one # character in the group name, the confirmation message ignored all text preceding the last #. This resulted in an incorrect confirmation message.
OKTA-244957
Users were able to sign in to the NorthWest Evaluation Association MAP app only when using Sign in with 1 click.
OKTA-245114
Imports failed in Preview instances of the WebEx (Cisco) app.
OKTA-246107
In SP-initiated flows for the AnyBill app, the Okta plugin did not route the user to the correct URL.
OKTA-247915
Admins were allowed to subscribe to email notifications for which they did not have permission.
OKTA-248760
When admins entered a username to test if a new LDAP configuration was valid, the Next button did not work.
OKTA-250256
In some cases, the group attribute for Template WS-Fed apps was evaluated incorrectly.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Chicago Tribune (OKTA-248424)
-
CrowdStrike Support Portal (OKTA-250779)
-
Cube19 (OKTA-253339)
-
MailGun (OKTA-250727)
-
Nice inContact Workforce Management (OKTA-250421)
-
Template 2 Page Plugin (OKTA-249755)
Applications
Application Updates
- Provisioning support removed for Huddle and Connected Data apps - Provisioning support has been removed from the Huddle and Connected Data apps due to its low customer usage, lack of standards based integration, and high supportability cost.
- The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Elevio: For configuration information, see Provisioning Users with Okta.
- Dynamic Signal: For configuration information, see Setup for Okta SCIM User Provisioning.
New Integrations
SAML for the following Okta Verified applications
-
Compusense (OKTA-252571)
-
Moesif API Analytics (OKTA-251060)
Weekly Updates
Fixes
General Fixes
OKTA-235246
Org2Org setup created a new appUser instead of restoring the original user after encountering an Error while Reactivating user message.
OKTA-247437
Report admins did not have access to the Proxy IP Usage Report.
OKTA-249412
403 return status in API caused spinning icon in UI when Mobile admins tried to view the Security Health Check page.
OKTA-249465
Users encountered an error if they switched between WebAuthn and other factors when signing in to Okta in a web browser.
OKTA-250499
Telangana was missing as a region for India in Network Zones.
OKTA-252845
Immediately after enabling WebAuthn, users saw Windows Hello in a stale window when resetting an enrollment factor.
OKTA-253687
Back to Settings link incorrectly appeared in the OIDC sign-in flow.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
2145 Parkplace (OKTA-250451)
-
Adobe Creative (OKTA-254693)
-
Adobe Enterprise (OKTA-254514)
-
Cisco Webex Meetings (OKTA-253433)
-
Dealer Daily Lexus (OKTA-253658)
-
Google Analytics (OKTA-253582)
-
My T-Mobile (OKTA-251610)
-
Paycor (OKTA-253575)
-
SSQ Financial Group (OKTA-253421)
Applications
New Integrations
SAML for the following Okta Verified applications
-
CyberArk Password Vault Web Access (OKTA-251875)
-
DataRails (OKTA-251850)
-
Elevio (OKTA-253738)
-
SimpliGov (OKTA-249789)
-
Visibly (OKTA-253409)
-
VMWare Workspace ONE (OKTA-252568)
SWA for the following Okta Verified application
-
Adobe Admin Console (OKTA-254510)
Fixes
General Fixes
OKTA-208239
Duplicate notifications were displayed in the Profile Editor after a new attribute was added.
OKTA-218100
Security email notifications sometimes displayed extra commas.
OKTA-231286
Editing AD instances sometimes resulted in a provisioning error in Office 365 instances.
OKTA-237415
Activation emails were sent to end users despite being configured otherwise.
OKTA-237944
When saving a user's updated profile details from the Profile page, a manual refresh was required.
OKTA-244162
The MFA Factor Reset email displayed the TOTP factor with an error.
OKTA-244298
The Import from Active Directory tab did not describe what type of import will remove AD groups in Okta if the groups have been deleted in the AD.
OKTA-244986
Behavior Detection logs showed UNKNOWN for user's first sign-in, but showed POSITIVE for sign-in after resetting the behavior profile.
OKTA-247912
If the IdP routing rule contained a user identifier condition and an application condition, some users were routed incorrectly.
OKTA-249204
For orgs that allow non-email usernames, users with an ID me were not able to sign in due to an API conflict. This ID is no longer allowed, but existing users with that ID are unaffected.
OKTA-250170
Attempts to add users to the approval process of the Access Request Workflow failed.
OKTA-254883
Duo factor activation events were not generated.
OKTA-255088
The Early Access Self-Service link for User Types incorrectly pointed to the Beta doc rather than the EA release topic in online help.
OKTA-255517
In the Security > General page, the Learn More link next to the Report Suspicious Activity selection pointed to the wrong page in the online help.
OKTA-255582
In Preview orgs, users who removed Okta Verify through their Settings page remained enrolled in the factor.
OKTA-255940
After access to Okta Support was enabled, impersonation could be disabled or enabled in the impersonated session.
OKTA-256720
Import settings for Salesforce were unintentionally reset and lost.
OKTA-256724
Users who signed in via IWA after their password was reset with the Temporary Password option were prompted to change their password twice.
OKTA-257203
Resetting all factors for a user resulted in an error.
OKTA-257353
Auth schema inline hooks could not be renamed.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe Fonts (OKTA-254976)
-
Adobe Licensing Website (OKTA-254315)
-
Amazon UK (OKTA-255211)
-
Eden (OKTA-221449)
-
Entelo (OKTA-253476)
-
GoToMeeting (OKTA-255995)
-
iTunes Connect (OKTA-257282)
-
Jive (OKTA-256518)
-
JumpCloud (OKTA-254291)
-
Knoll (OKTA-257055)
-
Kyriba (OKTA-255894)
-
MIBOR (OKTA-257057)
-
My Jive (OKTA-256680)
-
Nexus System Connect (OKTA-254290)
-
The Wall Street Journal (OKTA-255220)
-
Threads Culture (OKTA-256355)
-
U.S. Bank (OKTA-254309)
-
WP Engine (OKTA-257193)
-
YouCanBook.me (OKTA-257284)
-
Zoominfo (OKTA-243203)
Applications
Application Updates
-
Netskope now supports the following Provisioning features (this is in addition to the other provisioning features it already supports):
- Group Push
Users who have previously set up the Netskope integration and enabled Provisioning need to follow the migration steps detailed in the Netskope Configuration Guide if they want to use the new feature.
- OfficeSpace Software now supports the following Provisioning features (this is in addition to the other provisioning features it already supports):
- Importing users
- Profile/Attribute Level Mastering
- Schema updates
Users who have previously set-up the OfficeSpace Software integration and enabled Provisioning need to follow the migration steps detailed in the OfficeSpace Software Configuration Guide if they want to use the new features
New Integrations
The following partner-built provisioning integration apps are now Generally Available in the OIN as Okta Verified:
- AMGtime: For configuration information, see Configuring User Provisioning for AMGtime/Okta.
- DatoCMS: For configuration information, see Configuring Provisioning with Okta.
- Miro (formerly RealtimeBoard): For configuration information, see Setting up automated provisioning with OKTA.
- Signagelive: For configuration information, see Okta Single Sign On and Automated Provisioning Configuration.
SAML for the following Okta Verified applications
-
Accrualify (OKTA-256378)
-
Ambient.ai (OKTA-254752)
SWA for the following Okta Verified applications
-
E-Link (OKTA-249632)
-
EagleBank (OKTA-242296)
-
TECtok (OKTA-245077)
-
Time Clock Plus Manager (OKTA-244676)
September 2019
2019.09.0: Monthly Production release began deployment on September 9
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Customizable email template for LDAP users
The LDAP Forgot Password Denied email template can now be customized for LDAP users who have requested a password reset but must have their password reset by an admin. See Customize an email template.
New System Log event for event hooks
Event hook eligible System Log events now display the event hook ID in the Debug Context object under the TargetEventHookId field.
For a list of event hook eligible System Log events, filter our Event Types Catalog by the event-hook tag.
Okta Browser Plugin, version 5.32.0 for all browsers
This version includes the following:
- Custom URL domain support for the plugin (available through the EA Feature Manager)
- Back-end enhancements
End of support for Okta Mobile Connect on iOS 13 and iPad OS 13
Okta Mobile Connect will not function on iPhones and iPads that upgrade to iOS 13 and iPad OS 13, respectively, because version 13 introduces changes that affect the way an Apple API handles external requests to open Okta Mobile. See Okta Mobile Connect.
User enrollment of multiple Web Authentication factors
End users now have the option to enroll in more than one instance of a WebAuthn-based factor, which can be set up either from the sign-in widget or from the end user dashboard settings. See Multifactor Authentication.
Active Directory, honor AD password policy
If an AD-mastered user has forgotten their password the AD password policy is honored when the user resets their password.
Support for LDAP provisioning
With the addition of the following Provisioning Features, Okta's LDAP integrations now closely match the functionality already available to Okta Active Directory (AD) integrations.
-
Create Users
-
Update and deactivate LDAP accounts
-
DN customization
-
Profile Masters
For more information, see LDAP integration.
Admin report CSV changes
The Administrator report containing information about all admins, their roles, and permissions will now be generated asynchronously. Super admins can generate the report by clicking Request Report and they will receive an email with a download link when the report is ready.
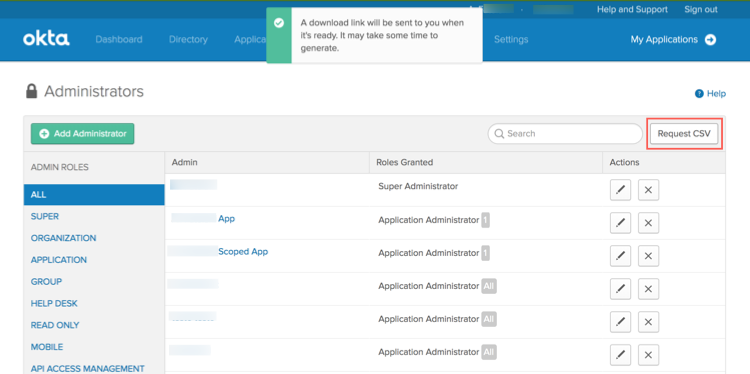
Inline Hooks
Admins can now add Inline Hooks from the admin console. Inline Hooks enable admins to integrate custom functionality into Okta process flows. For more information, see Inline hooks.
Configure Okta Device Trust for Native Apps and Safari on MDM managed iOS devices
Okta Device Trust for MDM managed iOS devices allows you to prevent unmanaged iOS devices from accessing enterprise services through browsers and native applications:
Note: This feature requires Okta Mobile 5.12 for iOS (or later), available in the App Store beginning February 1st.
For details, see Configure Okta Device Trust for Native Apps and Safari on MDM managed devices.
ThreatInsight Threat Detection
Admins can now configure ThreatInsight — a new feature that detects credential-based attacks from malicious IP addresses. ThreatInsight events can be displayed in the admin system log and also be blocked once this feature is configured. For more information, see Okta ThreatInsight.
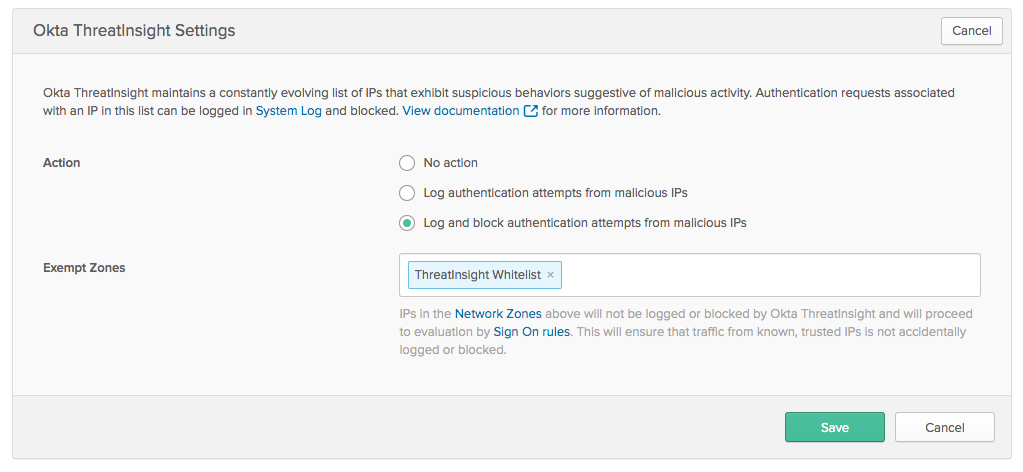
Apps supporting incremental imports
Workday joins Active Directory and LDAP in the ability to run immediate, incremental imports. Okta strives to add this functionality to more and more provisioning-enabled apps. This feature is currently only available for Preview orgs.
Note: To use this functionality, your org must also have the Workday Incremental Imports (ENG_PROV_WORKDAY_INCREMENTAL_IMPORTS) Early Access feature enabled.
Early Access Features
New Features
Quick Access tab on the Okta Browser Plugin available through EA feature manager
Quick Access tab on the Okta Browser Plugin is now available through the EA feature manager. See Allow end-users to quickly access apps.
MFA for Oracle Access Manager
With Okta MFA for Oracle Access Manager (OAM), customers can use OAM as their Identity Provider (IdP) to applications and also use Okta for MFA to provide a strong method of authentication for applications. For more information, see MFA for Oracle Access Manager.
Factor Sequencing
Admins can now provide end users with the option to sign in to their org using various MFA factors as the primary method of authentication in place of using a standard password. See MFA Factor Sequencing.
Fixes
General Fixes
OKTA-192270
The translations were missing for the API AM User Consent buttons.
OKTA-230781
On the Push Groups to Active Directory > Push Groups by Name page, clicking Show more incorrectly redirected the admin to the People page.
OKTA-232406
The Self-Service Create Account Registration form did not clear a failed password validation status even after the password was updated to meet complexity requirements.
OKTA-237684
The last MFA factor used was not remembered for some orgs that use app-level MFA rules and a custom URL domain for sign-in attempts initiated by a Service Provider.
OKTA-237864
The Active Directory Settings page was slow or unresponsive for directories with more than 10,000 Organizational Units (OUs). To obtain the fix for this bug, contact Support.
OKTA-238146
When Factor Sequencing was enabled and a user clicked Sign Out from the sign-in widget, the browser page had to be refreshed manually for the user to sign in again.
OKTA-240089
Some authentication error messages for the custom IdP factor were not displayed by the sign-in widget.
OKTA-242345
Some sign-on policies and rules for IWA were not applied when a user signed in.
OKTA-246020
An extra character > appeared in the Admin navigation header.
OKTA-246246H
The temporary password was not displayed in developer account activation emails.
OKTA-247093
Web Authentication factor names were not displayed correctly under Extra Verification in end user settings.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Active Campaign (OKTA-245468)
-
Aegify (OKTA-245093)
-
BSPlink (OKTA-239934)
-
Check Point (OKTA-244812)
-
CultureIQ (OKTA-245092)
-
DesignCrowd (OKTA-245635)
-
Google Play Developer Console (OKTA-241992)
-
Hippo CMMS (OKTA-246930)
-
Key Bank (OKTA-245091)
-
MyFax (OKTA-244628)
-
OnePath Advisor (OKTA-243552)
-
ProjectManager.com (OKTA-244279)
-
Shutterfly (OKTA-245801)
-
Wells Fargo Funding (OKTA-244825)
Applications
Application Updates
To reflect Webex name changes we have updated our documentation as follows:
- Webex (Cisco) is renamed to Cisco Webex Meetings
New Integrations
SAML for the following Okta Verified applications
-
15five (OKTA-245730)
-
Centrify Privilege Access Service (OKTA-244805)
-
COMPASS by Bespoke Metrics (OKTA-246403)
-
Gateway Software Solutions (OKTA-231714)
-
Good2Give (OKTA-244842)
-
Legal Diary (OKTA-231714)
-
Wellness360 (OKTA-242402)
SWA for the following Okta Verified application
-
United Capital (OKTA-240147)
Weekly Updates
Fixes
General Fixes
OKTA-239075
After having their passwords reset by an admin, AD-mastered users who changed their AD password and then used Delegated Authentication to sign in to Okta encountered an unnecessary password reset page during the IWA Desktop SSO sign-in flow.
OKTA-239805
It was possible to remove the last individually assigned super admin from an org.
OKTA-243796
The Import Now button did not appear for newly created OPP app instances.
OKTA-244073
Jira service failed to start after upgrading the Jira Authenticator from 3.0.7 to 3.1.1.
Note: To receive this bug fix, download the latest Jira Authenticator 3.1.2.
OKTA-248184
Suspicious Activity emails sent to admins erroneously included information about actions taken as a result of the suspicious activity.
OKTA-248458
When an org admin toggled the WebAuthn factor feature, non-Windows users with their browsers open to the sign-in page erroneously saw the Windows Hello factor.
OKTA-249451H
Sending an Okta Verify push, then while waiting for the end user's response, switching to WebAuthn as a factor resulted in an error.
Applications
New Integrations
SAML for the following Okta Verified applications
-
Airbrake (OKTA-247505)
-
Parley Pro (OKTA-239461)
Fixes
General Fixes
OKTA-221735
The Docusign app did not display the Permission profile values correctly.
OKTA-230033
Admins were allowed to attempt to assign a U2F factor to a user even when it was disallowed by policy.
OKTA-238336
Provisioning more than 3600 requests from Okta to Salesforce caused both user creation and user updates to fail.
OKTA-240371
During an SP-initiated app sign in to a custom domain, the behavior of the Remember Device check box was inconsistent for App-level and Org-level MFA.
OKTA-240769
WebEx was not provisioning the correct email attribute value.
OKTA-241439
User profile mappings did not generate errors when Expression Language group functions were used inside an App to Okta mapping.
OKTA-241761
A new NetSuite domain name was missing from the list of NetSuite options.
OKTA-241916
There was a typo in one of the Feature Manager Early Access features.
OKTA-244297
After having their passwords reset by an admin, AD-mastered users who changed their AD password and then signed in to Okta encountered an unnecessary password reset page during the IWA Desktop SSO sign-in flow.
To obtain the fix for this bug, contact Support.
OKTA-244537
Users were able to re-enroll in a previously enrolled WebAuthn authenticator.
OKTA-245768
While it was still pending verification, WebAuthn appeared on the end user's Settings page as an enrolled factor.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Workday (OKTA-245265)
The following SWA apps were not working correctly and are now fixed
-
Air Canada Travel Agency (OKTA-246673)
-
Alerus Retirement (OKTA-248084)
-
Alerus: Account Access (OKTA-246929)
-
BigBlueOnline (OKTA-248218)
-
Duo Security (OKTA-247829)
-
HackerRank For Work (OKTA-247487)
-
Mimecast (OKTA-246444)
-
OneSignal (OKTA-247482)
-
ProofHub (OKTA-247818)
-
Sun Life Financial (OKTA-246462)
-
SyncHR (OKTA-247514)
-
The Hartford At Work (OKTA-247955)
-
Wistia (OKTA-246913)
-
Zuman (OKTA-247537)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Arxspan (OKTA-248526)
-
EdCast (OKTA-246404)
-
FaxLogic Advanced Web Client (OKTA-247506)
-
Heureka Platform Connector (OKTA-239141)
-
Mapbox (OKTA-247507)
-
Notion (OKTA-246110)
SWA for the following Okta Verified applications
-
ContentSquare (OKTA-244251)
-
Wells Fargo - Personal (OKTA-244153)
-
WhiteHat Customer Portal (OKTA-243554)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Clarizen (OKTA-248809)
-
Doxis4 (OKTA-244112)
-
MobileIron Cloud (OKTA-248803)
-
xMatters (OKTA-248805)
-
Zscaler Private Access (OKTA-248807)
Mobile application for use with Okta Mobility Management (OMM) (Android)
-
Igloo (OKTA-248490)
-
Syncplicity (OKTA-248487)
Fixes
General Fixes
OKTA-230273
Clicking the name of an Organizational Unit rather than selecting its check box in Group OUs connected to Okta caused the corresponding Organizational Unit in User OUs connected to Okta to be selected.
OKTA-235285
When signing in to an app, users were prompted to enroll in email authentication instead of specific apps that were included as part of the App Condition for Enrollment policy.
OKTA-239833
Clarizen provisioning configured for a sandbox environment failed.
OKTA-245037
The Custom Email Templates preview CSS appeared to be different from the actual email.
OKTA-246931
Okta groups of type APP_GROUP failed to be marked as deleted using Group API when the original App Group was already marked as DELETED.
OKTA-247199
WebAuthn did not work with custom domains.
OKTA-248625
After upgrading from U2F to WebAuthn and then disabling WebAuthn, U2F users did not see a U2F option on the enrollment page.
OKTA-249385
Admins could add the same property name with different cases into the appUser profile for Generic OIDC IdP.
OKTA-250615
Users for orgs without a group-based Okta MFA enrollment policy could not enroll WebAuthn factors from the end user Settings page.
OKTA-250722
The custom sign-in page call-out displayed the wrong version number as the latest version of the Okta Sign-in Widget.
OKTA-251211H
Metadata about Active Directory domains was not updated in Okta during imports from AD. In some cases this prevented features which rely on this metadata, for example Agentless Desktop SSO, from working correctly or being configured for the first time.
To obtain this fix, download the Okta Active Directory agent, version 3.5.9.
OKTA-251828H
App icons on the Okta End-User Dashboard took longer to load in Chrome 77 when hardware acceleration was on.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Employee Self Service Portal (OKTA-247820)
-
Evernote (OKTA-247819)
-
Microsoft Office 365 (OKTA-239332)
-
Milestone XProtect Smart Client (OKTA-248227)
-
MobileIron Cloud (OKTA-247821)
-
MyFax (OKTA-244628)
-
OnceHub (OKTA-249321)
-
Universal Production Music (OKTA-249121)
-
Wells Fargo (Commercial Electronic Office) (OKTA-249085)
-
Work Number Commercial Verifier (OKTA-248228)
Applications
New Integrations
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Vable: For configuration information, see Okta users provisioning for Vable platform.
SAML for the following Okta Verified applications
-
OpsRamp (OKTA-247509)
-
RSA SAML Test Service Provider (OKTA-246422)
-
SevenRooms (OKTA-248528)
-
SpotMe (OKTA-248481)
-
ValenceDocs (OKTA-244909)
Mobile applications for use with Okta Mobility Management (OMM) (Android and iOS)
-
ADP (OKTA-248495)
-
Cvent (OKTA-248498)
-
SolarWinds Service Desk (OKTA-249028)
-
Wordpress by MiniOrange (OKTA-249020)
Mobile applications for use with Okta Mobility Management (OMM) (Android)
-
Atlassian Confluence Server (OKTA-248497)
-
Benevity (OKTA-248496)
Fixes
General Fixes
OKTA-219847
Provisioning tasks for G Suite failed to complete when the daily limit for API calls was reached.
OKTA-221627
The honorificSuffix and honorificPrefix were mapped incorrectly between Okta and AD.
OKTA-241281
Samanage import failed with an Error while download schema enum values: null error.
OKTA-245525
Okta to App profile mappings could not be saved after provisioning settings were enabled for an application.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Apptio (OKTA-249495)
-
BAML Works (OKTA-250531)
-
ESRI Customer Care Portal (OKTA-249497)
-
Lucidchart (OKTA-239922)
-
LucidChart (OKTA-239922)
-
Mailchimp (OKTA-250518)
-
Nice inContact (OKTA-245717)
-
Trustwave (OKTA-249499)
Applications
New Integrations
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Udemy for Business: For configuration information, see Configuring Single Sign-On and Provisioning in Okta for Udemy for Business.
SAML for the following Okta Verified applications
-
Clutch (OKTA-247508)
-
Cyberator (OKTA-250305)
-
PurelyHR (OKTA-250517)
-
Scout CMS (OKTA-251113)
-
Smart360 (OKTA-248575)
August 2019
2019.08.0: Monthly Production release began deployment on August 12
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
System Log event for Agentless Desktop SSO authentication error
A new System Log event (User not found during agentless DSSO Auth) appears when there is an Agentless DSSO authentication error due to one of the following reasons:
- The UPN is not in a valid format multiple users match
- The search criteria no users match the search criteria
Okta Active Directory agent, version 3.5.8
This release of the Okta AD agent implements a check on the AD agent service startup. The check overrides the value of the connectionLimit parameter if it is misconfigured. If the value is acceptable but not optimal, a warning message that describes the recommended value is logged. For details about the recommended values, see Okta Active Directory agent variable definitions. For agent version history, see Okta Active Directory agent version history.
Install Plugin button on the end-user dashboard on Firefox goes to Firefox Add-ons
In the Firefox browser, the Install Plugin button on the end-user dashboard now redirects to Firefox Add-ons, where users can download the latest version of Okta Browser Plugin.
Remove Duo from end user settings
Duo may now be removed from end user settings so that end user enrollment takes place only at sign-in, based on the configured MFA enrollment policy. For more information, see Duo Security (MFA).
Admin console search
Admins can now use a quick search for the names of end users or apps. However you only see search results based on what you have admin permission to view. When the search results are presented, if the name or app you are seeking is listed, you can click on the item and be taken to the corresponding user page or application page. For details, see Admin Console search.
Scoping admin privileges, AD and LDAP-mastered groups now supported
Super admins can now scope Group and Help Desk admin privileges to AD and LDAP-mastered groups in addition to Okta-mastered groups. This EA Feature can be enabled in the Feature Manager. For details, see Assign Help Desk admin privileges.
LinkedIn IdP Creation Re-Enabled
Creation of LinkedIn Identity Providers has been re-enabled in all Preview Orgs. For more information, see Set up a LinkedIn app.
Incremental import support for LDAP users
LDAP users can now take advantage of incremental imports, eliminating the need for full imports every time. Incremental imports improve performance by only importing users that were created, updated, or deleted since your last import. For details, see LDAP integration.
Reauthentication prompts
All prompts for reauthentication now use the Sign In widget rather than the Classic UI.
IWA Desktop SSO, behavior change
If you turn off IWA DSSO, the IWA Routing Rule will be switched to Inactive. The next Routing Rule will be used to direct your users to the appropriate sign in. When you turn IWA DSSO on again, you must also switch the IWA Routing Rule to Active again. For details, see Install and configure the Okta IWA Web agent for Desktop Single Sign-on in Install and configure the Okta IWA Web agent for Desktop SSO.
Generally Available Enhancements
Devices menu is changing to the OMM menu
The Devices menu and other OMM-specific areas of Admin Console have been renamed to OMM or Okta Mobility Management. This was done to:
- Clarify that items in the menu and associated product areas are relevant only for orgs that have configured Okta Mobility Management.
- Free-up the label Devices for future use.
Active Directory, first and last name optional
You can now mark the first and last name attributes as optional for AD-mastered users. This allows you to import users with one or both of these blank fields. For details, see Make first and last name optional in Active Directory.
New prompt during WebAuthn enrollment
A new prompt during WebAuthn enrollment that asks the user if they want to Allow Okta to see authenticator data. Fore details, see Multifactor Authentication.
Early Access Features
New Features
Custom Factor Authentication
Custom Factor Authentication allows admins to enable an Identity Provider factor using SAML authentication. For more information, see Custom IdP factor .
Integrate Okta Device Trust with VMware Workspace ONE for iOS and Android devices
The Okta + VMware integration is a SAML-based solution that combines the power of Okta Contextual Access Management with device signals from VMware Workspace ONE to deliver a secure and seamless end-user experience. For details, see Integrate Okta Device Trust with VMware Workspace ONE for iOS and Android devices.
Fixes
General Fixes
OKTA-194153
SCIM App template URI requests were using + instead of %20 (space), making them RFC non-compliant.
OKTA-207634
In some cases, there were redirect issues after upgrading to JIRA On-Prem version 3.0.7.
OKTA-228380
MFA-required users with , in their passwords did not automatically go through the proper PUSH flow.
OKTA-229541
To preserve cross-site functionality in light of upcoming updates to Chrome (https://www.chromestatus.com/feature/5088147346030592), Okta has added the SameSite=None attribute to all relevant cookies.
OKTA-239067
The Get Okta Mobile on the App Store page was corrupted when attempting to add a new account to native Outlook app.
OKTA-239419
Agentless DSSO failed when the Routing Rules feature was enabled because no IdP rule was created.
OKTA-240083
When Agentless DSSO failed and there was no OnPrem IWA agent, users were redirected to a default login page (an example default login page URL custom.com/login/default) instead of the customer’s login page (an example URL custom.com) configured by the customer under Identify Provider Settings.
OKTA-240115
Attempts to change Group Roles through the public API failed and incorrect events were logged in the System Log.
OKTA-240523
If Prompt for factor was cleared for an existing rule, Factor mode and Factor Lifetime were erroneously displayed when the rule was expanded.
OKTA-240669
No customer-facing error messages were displayed when admins tried to save a customized email template with a subject that exceeded the 128-character limit.
OKTA-71860
An incorrect error message was shown when the body of a customized email template exceeded the maximum number of characters.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
AnyBill (OKTA-240273)
-
FCO (OKTA-241250)
-
Indianapolis Business Journal (OKTA-241433)
-
Knoll (OKTA-240954)
-
Nextiva VOIP (OKTA-240856)
-
Sfax (OKTA-241251)
-
Twilio (OKTA-241252)
-
Webex Premium (OKTA-241571)
-
WORK NUMBER Social Service Verifier (OKTA-241573)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Arxspan (OKTA-240204)
-
DataGrail (OKTA-239290)
-
Getabstract (OKTA-239289)
-
HackEDU (OKTA-237775)
-
ITProTV (OKTA-238934)
-
RStudio Connect (OKTA-241802)
-
Zoom (OKTA-143049)
SWA for the following Okta Verified applications
-
One Net Receptionist (OKTA-234416)
-
Thrift Savings Plan (OKTA-233571)
-
Vendor Invoicing Portal (OKTA-233570)
Mobile applications for use with Okta Mobility Management (iOS)
-
Adobe Fill & Sign - Doc Filler (OKTA-235517)
-
Adobe Scan (OKTA-235515)
-
Adobe Scan: Mobile PDF Scanner (OKTA-235514)
Weekly Updates
Fixes
General Fixes
OKTA-229898
If the Service account username field was left blank on the Desktop SSO settings page when configuring Agentless Desktop SSO settings for Active Directory, the error message incorrectly used the term SPN instead of Service account username.
OKTA-237827
In Feature Manager, when an Open Beta had a dependency on a Closed Beta, the Contact Support link was missing from the Open Beta description.
OKTA-237924
Some LDAPi search requests using group membership filters timed out.
OKTA-241759
When an end user canceled their enrollment in an Identity Provider factor, they were not returned to the Okta enrollment screen automatically.
OKTA-242944
When admins enabled a Beta feature, the confirmation email they received contained incorrect Beta feature names.
OKTA-244013H
The attribute for userId in the SAML assertion was interpreted as Okta userid instead of the value sent.
OKTA-244527H
Some users could not login to their Okta org using samAccountname.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
IBM MaaS360 (OKTA-232700)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Lab Horizon (OKTA-240597)
-
Motus (OKTA-240602)
-
Purchasing Platform (OKTA-231720)
-
Target Solutions (OKTA-241682)
SAML for the following Community Created application
-
Area 1 Horizon (OKTA-241845)
Fixes
General Fixes
OKTA-240654
When admins customized the sign-in page, tool tip fields appeared when there should be none.
OKTA-241861
When editing the On-Prem Desktop SSO form on the Security > Delegated Authentication page, the Cancel button at the top of the form was not displayed.
OKTA-179828
Admins could deactivate a SAML Identity Provider when it was still active as an Idp Factor.
OKTA-223737
For some users, the ACTIVATE MY ACCOUNT button did not render correctly in the Activate your developer account email.
OKTA-226475
In the BambooHR app, users were imported one day before their actual start dates.
OKTA-236983
When factor sequencing feature was enabled, the Add button was displayed even when all authentication options had been added.
OKTA-239014
AD-mastered users were not able to update their primary phone number on the Settings page when the attribute was Okta-mastered and with READ-WRITE permissions.
OKTA-242976
When factor sequencing feature was enabled, for orgs that require Okta Verify with push notifications, users that were enrolled for Okta Verify TOTP and not push notifications could not sign in.
OKTA-243197
When factor sequencing feature was enabled and an Idp factor was configured, the default factor strength of the IdP factor was missing.
OKTA-243624
No results were displayed when filtering application group's membership by application name.
OKTA-243665
Users could not sign in if they were enrolled in Custom TOTP by an admin but the factor enrollment policy included both Custom TOTP as a required factor and any other factor as an optional/required factor.
OKTA-244032
A change was made to prevent conflicts with the Universal Directory expression language. It now correctly fetches the configured userId.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
First Advantage Enterprise Advantage (OKTA-239473)
-
Microsoft Office 365 (OKTA-239316)
-
Mitel Sky Portal (OKTA-241260)
-
Nice inContact Workforce Management (OKTA-242929)
-
QANTAS (OKTA-241871)
Applications
New Integrations
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Heureka Platform Connector: For Configuration information, see Configuring Okta Connector for Heureka Intelligence Platform
- Invisionv7: For Configuration information, see the InVision for Okta SCIM Configuration Guide.
SAML for the following Okta Verified applications
-
Arbitrip (OKTA-242956)
-
Assetnote (OKTA-243043)
-
CaseFleet (OKTA-242714)
-
Contentful (OKTA-242957)
-
Conversocial Bots Platform (OKTA-243282)
-
Good2Give (OKTA-242715)
-
Nutanix Frame (OKTA-239515)
-
Zestful (OKTA-242404)
SWA for the following Okta Verified applications
-
GetYourGuide for Suppliers (OKTA-236209)
-
Inman (OKTA-236695)
-
Oracle Textura Payment Management (OKTA-236554)
-
Simmons Insights (OKTA-236319)
-
Sprout Mortgage (OKTA-233945)
-
Telesystem CommPortal (OKTA-237396)
-
Telesystem Hosted VoIP Admin CommPortal (OKTA-237395)
-
The Trade Desk API (OKTA-241847)
Mobile application for use with Okta Mobility Management (iOS/Android)
-
OrgWiki (SCIM) (OKTA-242734)
Fixes
General Fixes
OKTA-221428
Group push failed if the group name shared a prefix with an already pushed group.
OKTA-222859
The Token Inline Hook service did not trigger Inline Hook System Log events.
OKTA-226939
The SAML Inline Hook service did not trigger Inline Hook System Log events.
OKTA-231689
The Resend Activation Email prompt showed the incorrect expiration time-frame.
OKTA-243785
The MFA Factor Reset email displayed an error for a custom TOTP factor.
OKTA-243953
Calls and SMS from some US regions were considered international instead of domestic for billing purposes.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Cisco Webex Teams (OKTA-243546)
-
ClearCompany (OKTA-243545)
-
General Motors GlobalConnect (OKTA-243537)
-
Instacart (OKTA-243551)
-
Nice inContact (OKTA-243548)
-
Stampli (OKTA-243543)
Applications
Application Updates
To reflect GitHub name changes we have updated our documentation as follows:
- GitHub is renamed to GitHub Team
- GitHub Enterprise Cloud is renamed GitHub Enterprise Cloud – Organization
New Integrations
SAML for the following Okta Verified applications
-
Concur Travel and Expense (Early Access) (OKTA-239059)
-
Conversocial Bots Platform (OKTA-243282)
-
FaxLogic Administrator Dashboard (OKTA-244803)
-
IntSights (OKTA-243531)
-
KCM GRC Platform (OKTA-244907)
-
Trestle (OKTA-244439)
SWA for the following Okta Verified applications
-
Armstrong e-Service (OKTA-245629)
-
Armstrong Online Order Tracker (OKTA-237974)
-
Australian Injectable Drugs Handbook (AIDH) (OKTA-242364)
-
Foxpass (OKTA-239867)
-
GlobeTax ESP (OKTA-236982)
-
Honey (OKTA-238638)
-
IBM Micromedex (OKTA-239816)
-
NYC Procurement and Sourcing Solutions Portal (PASSPort) (OKTA-242930)
-
Quest (OKTA-241899)
-
Slido (OKTA-239865)
-
TRAXPayroll (OKTA-239158)
-
Zuman (OKTA-239495)
July 2019
2019.07.0: Monthly Production release began deployment on July 15
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Timeout warning added to the Sign-In Widget
A timeout warning has been added to the Sign-In Widget for SMS and Voice Factor enrollment and challenge flows. For more information, see Customize the Okta-hosted sign-in page.
Token expiration window increased to five years
The expiration window of Refresh Tokens can be configured up to five years in custom authorization servers. The minimum expiration is unchanged. For more information, see API Access Management.
AD Desktop Single-Sign On, interface changes
The user interface for the Security > Delegated Authentication page used to configure Desktop Single-Sign On has been streamlined. There are no functional changes. For details, see Install and configure the Okta IWA Web agent for Desktop Single Sign-on.
Okta Verify factor available for all orgs
All orgs now have the option to configure and enable Okta Verify as a factor. For more information, see Multifactor Authentication or Okta Verify.
ADFS app support for OIDC authentication
The ADFS app now provides support for OIDC authentication. For more information, see MFA for Active Directory Federation Services (ADFS).
Custom Email Template enhancement
To curtail phishing, free editions of Okta are no longer able to create and send customized email templates. For feature information, see Customize an email template.
Okta Browser Plugin for Firefox available from Firefox Add-ons
Okta Browser Plugin version 5.31.0 for Firefox is now available from the Firefox Add-ons. For version history, see Okta Browser Plugin version history.
OPP agent, version 1.3.2
On Premises Provisioning Agent version 1.3.2 supports CSV Directory Integration. For version history, see Okta Provisioning agent and SDK version history.
Prevent end users from choosing commonly used passwords
Admins can restrict the use of commonly used passwords through the group password policy. For more information, see Configuring an Organization-wide Password Policy.
Multifactor Authentication for admins
MFA for Admins allows Super admins to enable mandatory multifactor authentication for all administrators accessing admin functionality. For details see Authentication. This feature is currently available for new orgs only.
New admin role, Report admin
The Report admin role grants a user read-only access to all reports and the System Log. Report admins do not have edit access to any data.
Dynamic network zones
You can define dynamic network zones that match IP type and geolocation specifications. For more information, see Network Zones.
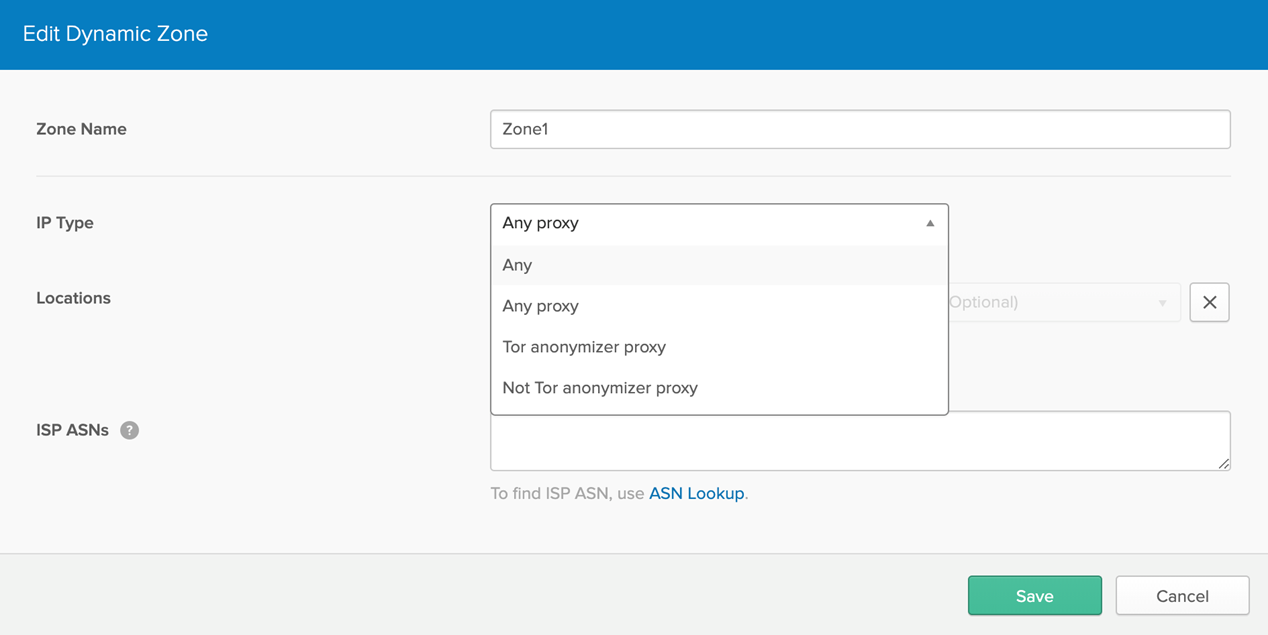
LDAP support for Auxiliary Object classes
You can now input a comma-separated list of auxiliary object classes when importing users from LDAP. For more information, see Configuring Your LDAP Settings.
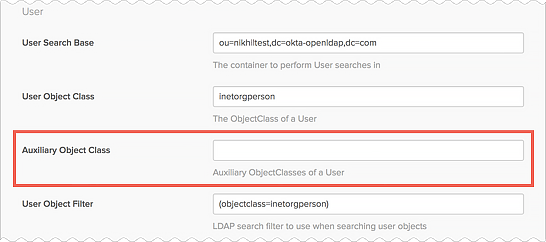
Current Assignments and Recent Unassignments reports added to the Reports page
Current Assignments and Recent Unassignments reports are now linked from the Application Access Audit section of the Reports page. These match the reports available from the Applications tab. For information, see Reports.
Generally Available Enhancements
New System Log event for sent emails
A new System Log event has been added to notify admins when an email is sent to a user for verification. When fired, this event contains information about the token lifetime in the debugData.
New System Log event for redeemed credentials in an email
A new System Log event has been added to identify when a credential sent in an email to a user has been redeemed, meaning the link was clicked or the code was entered.
When fired, this event contains information about the result and debugData with the action.
Validate service account credentials for Kerberos realm
When configuring the service account credentials for the Kerberos realm, you can now optionally choose to validate these credentials. For more information on Agentless DSSO, see Configure agentless Desktop Single Sign-on.
UI enhancements for Sign-On Policies and Password Policies
When creating a new MFA sign-on policy, the Prompt for Factor option is now selected by default. When creating a new password policy, the option to enforce a password history is now set to the last four passwords by default. For more information about sign-on policies and password policies, see to Sign-on policies.
System Log events for Behavior Settings
New System Log events now appear when creating, deleting, or updating behavior settings.
Early Access Features
New Features
Enforce Okta Device Trust for Native Apps and Browsers on MDM-managed Android devices
Okta Device Trust for Native Apps and Browsers on MDM-managed Android devices allows you to prevent unmanaged Android devices from accessing enterprise services through browsers and native applications.
Note: This feature requires Okta Mobile 3.14.1 for Android (or later). For details, see Enforce Okta Device Trust for Native Apps and Browsers on MDM-managed Android devices.
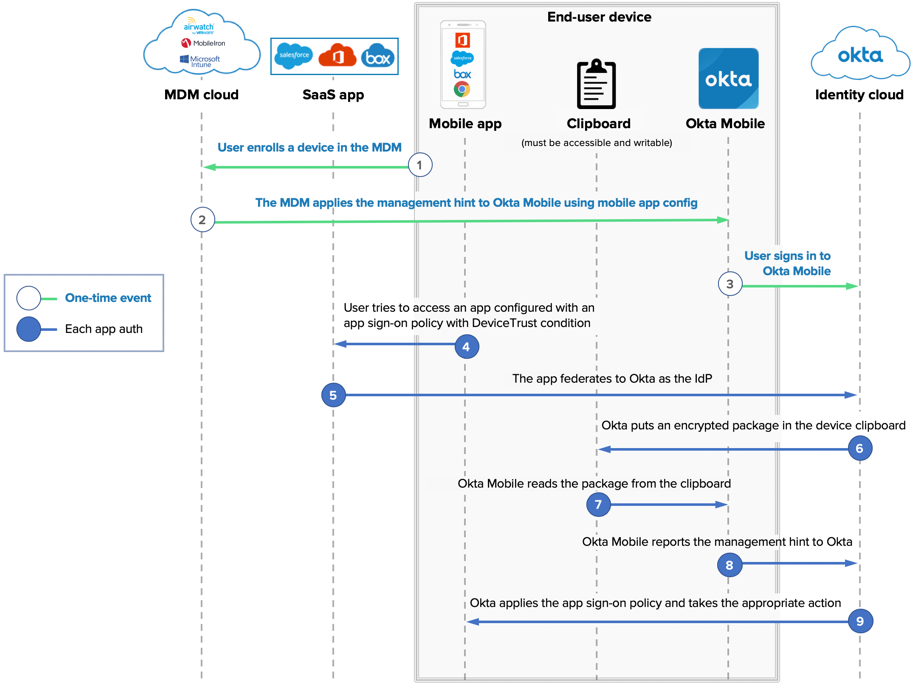
Fixes
OKTA-215899
The Downloads page incorrectly reported that some agents needed to be upgraded.
OKTA-221328
Group rules were not applied to reactivated users.
OKTA-235794
When MULTIPLE_FACTOR_ENROLLMENTS was enabled and MULTIPLE_OKTA_VERIFY_ENROLLMENTS disabled, changing the Okta Verify factor to REQUIRED returned a 400 error.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Amgen FIRST STEP (OKTA-234000)
-
Bank of America CashPro (OKTA-234532)
-
Bullhorn Jobscience (OKTA-233305)
-
Credible Behavioral Health (OKTA-236584)
-
eFax Corporate Admin (OKTA-232145)
-
HRConnection by Zywave (OKTA-234054)
-
Mimecast Personal Portal v3 (OKTA-235247)
-
Percolate (OKTA-235361)
-
Thomson Reuters Legal Tracker (OKTA-228672)
-
Xfinity (OKTA-234737)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Twic: For configuration information, see the Twic SCIM Integration Guide.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Zapier: For Configuration information, see the Zapier User Provisioning with SCIM guide.
SAML for the following Okta Verified applications
-
Panorays (OKTA-233837)
-
Teamie (OKTA-233564)
SWA for the following Okta Verified applications
-
A.I.D.A. Virtual Cards (OKTA-229475)
-
Aquera apps (OKTA-232806):
- AD LDS by Aquera
- Adobe Cloud by Aquera
- ADP Workforce Now by Aquera
- Atlassian by Aquera
- Box by Aquera
- Ceridian Dayforce by Aquera
- Documentum by Aquera
- Fastly by Aquera
- InvisionApp by Aquera
- Jama Software by Aquera
- LaunchDarkly by Aquera
- MongoDB by Aquera
- Runscope by Aquera
- Smartsheet by Aquera
- VividCortex by Aquera
-
Avery (OKTA-228198)
-
Cision Communications Cloud (OKTA-231151)
-
Coalfire (OKTA-228801)
-
Correspondent Hub (OKTA-229741)
-
Grip On It (OKTA-224027)
-
Jackson (OKTA-231411)
-
Moneris Gateway (OKTA-228650)
-
Music Vine (OKTA-229245)
-
National Life Group Agents Login (OKTA-231088)
-
Nationwide Financial (OKTA-231408)
-
OneMobile Oath (OKTA-224130)
-
PerfectServe (OKTA-230812)
-
Structural (OKTA-229603)
-
TIAA (OKTA-231409)
-
VPAS Life (OKTA-231407)
-
Zix Customer Support (OKTA-229476)
Weekly Updates
Fixes
General Fixes
OKTA-212923
A deleted LDAP instance was still visible on the Profile Editor page.
OKTA-220203
A SCIM Patch request did not handle a 204 No content response as expected.
OKTA-229606
In some cases, email notification settings for Helpdesk admins were not honored.
OKTA-237862
Instructions in Okta Verify to upgrade to Push Notifications mistakenly instructed end users to click Edit instead of + (plus) on Android devices.
OKTA-237865
Using the System Log Advanced Filter feature generated errant rate limit events.
App Integration Fixes
The following SWA app was not working correctly and is now fixed
-
Carta (OKTA-234742)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Spoke (www.askspoke.com) : For configuration information, see Configuring Provisioning for Spoke.
New Integrations
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- FuseLogic: For Configuration information, see Configuring Provisioning for FuseLogic.
- AFAS by FuseLogic: For Configuration information, see Configuring Provisioning from Afas.
- Leapsome: For Configuration information, see User provisioning via Okta from Leapsome.
- HackerRank For Work: For Configuration information, see Setting up SCIM Provisioning with Okta from HackerRank.
- iObeya: For Configuration information, see Configuring user provisioning with Okta from iObeya.
- New Relic (Limited Release): For Configuration information, see Configure SCIM provisioning from New Relic.
- PlusPlus: For Configuration information, see Configuring User Provisioning with OKTA and SCIM from PlusPlus.
SAML for the following Okta Verified applications
-
Good2Give (OKTA-233039)
-
InVision V7 (OKTA-227283)
-
PandaDoc (OKTA-236095)
-
Pathmatics Explorer (OKTA-236215)
-
QuestionPro (OKTA-236060)
-
Small Batch Learning (OKTA-237044)
-
Springer Link (OKTA-235129)
-
Viima (OKTA-235095)
-
VirtualPeople.ai (OKTA-236075)
SWA for the following Okta Verified applications
-
Angus (OKTA-233616)
-
Typography Hoefler and Co (OKTA-233903)
Mobile application for use with Okta Mobility Management (OMM) (iOS)
-
Citrix Netscaler Gateway (OKTA-227497)
Fixes
General Fixes
OKTA-182061
The system.agent.ad.read_topology System Log event contained a misspelling and also saved with no display message.
OKTA-222840
The 404 error page in French contained a spelling error on the Go to home page button.
OKTA-226817
Read Only admins had access to Add Origin and Edit buttons on the Trusted Origins page, but they received a You do not have permission to perform the requested action error message when trying to add or edit an origin.
OKTA-227476
For the Netsuite app, non-mandatory object attributes were treated as mandatory for group app assignments.
OKTA-228324
When signing in to an app with a factor originally registered as U2F then subsequently used as WebAuthn, users received a success message but the sign-on process looped, prompting continuously for MFA.
OKTA-228418
For the Workday app, username mappings were deleted when Provisioning settings were saved for the application.
OKTA-228446
The Japanese translation on the Password Reset screen had unnecessary punctuation.
OKTA-228963, OKTA-229818
The Japanese translation on the Okta-generated Activation page was incorrect.
OKTA-231247
For the Samanage app, user deactivation failed.
OKTA-232686
Active Directory scheduled imports ran as full imports instead of incremental.
OKTA-233323
When saving the Profile and Lifecycle Mastering settings for an LDAP directory, an error message was displayed if the Allow LDAP to master Okta users option was selected along with any Okta to LDAP provisioning features were also enable.
OKTA-233327
Changes made to the Allow <App name> to master Okta users option in an app's Provisioning settings were lost if the admin subsequently clicked the Save button in the To App section, without reloading the page.
OKTA-234463
The getManagerUser("active_directory").$attribute expression used the appuser schema to look up the property definition instead of the Okta user.
OKTA-235669
The Get Okta Mobile on the app store screen did not display correctly on the iPhone SE.
OKTA-236083
When deleting a YubiKey seed, the confirmation messages were misleading.
OKTA-236260
The Hyperspace Agent checked for SSL pinning against all requests instead of only Okta requests.
OKTA-236860
Admins were able to remove all groups and individually assigned Super Admins for an org. We now check to ensure there is always at least one Super Admin in the org.
OKTA-238999
The Okta Verify icon displayed on the User Factor Reset page of the Admin Console was outdated.
OKTA-239323
In existing free trial editions of Okta, the pencil icon that allows admins to edit customized email templates was grayed out instead of active, as expected. Note that in new free trial editions, the pencil icon is grayed out as a security precaution.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Zapier SAML (OKTA-239414)
The following SWA apps were not working correctly and are now fixed
-
AvePoint Online Services (OKTA-236799)
-
Constellation Energy Manager (OKTA-239151)
-
Dynatrace (OKTA-236800)
-
Equinix Customer Portal (OKTA-237306)
-
FastMail (OKTA-236798)
-
Flickr (OKTA-237551)
-
Forrester Research (OKTA-233568)
-
GS1 US (OKTA-237509)
-
Gusto (OKTA-239476)
-
Inbox by Gmail (OKTA-237790)
-
Informatica Cloud (OKTA-239291)
-
Liquid Web (OKTA-237452)
-
LiveChat (OKTA-239926)
-
MassMutual RetireSmart (OKTA-239477)
-
Microsoft Embedded Communication Extranet (OKTA-237786)
-
My NS Business (OKTA-236797)
-
Notion (OKTA-236796)
-
Parse.ly (OKTA-239314)
-
Peapod (OKTA-236795)
-
PremiumBeat (OKTA-236801)
-
Royal Caribbean Cruise Lines (OKTA-239334)
-
Sainsburys Groceries (OKTA-238858)
-
Skrill (OKTA-236794)
-
Societe Generale: Markets (OKTA-237787)
-
The Wall Street Journal (OKTA-237636)
-
Thomson Reuters Legal Tracker (OKTA-237785)
-
VSP (OKTA-238098)
-
Wells Fargo Funding (OKTA-236805)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- HackerRank for Work: For configuration information, see Setting up SCIM Provisioning with Okta.
New Integrations
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- RFPIO: For Configuration information, see the RFPIO User Provisioning Okta guide.
- Siftrock: For Configuration information, see the Siftrock Okta SCIM Configuration Guide.
SAML for the following Okta Verified applications
-
Amazon Business (OKTA-236081)
-
Circula (OKTA-233040)
-
Forcepoint Web Security (OKTA-209495)
-
Wealth Access (OKTA-238247)
SWA for the following Okta Verified applications
-
8x8 PartnerXchange (OKTA-226146)
-
Agilent (OKTA-232699)
-
Aimsio (OKTA-232267)
-
Behance (OKTA-234044)
-
Bpost (OKTA-231079)
-
citibank (OKTA-239471)
-
CodySoft Health Plan Management System (OKTA-231679)
-
Evan Evans Tours (OKTA-232322)
-
HERE Developer (OKTA-233014)
-
M Financial Group (OKTA-231423)
-
MenaITech (OKTA-233606)
-
MillerSearles (OKTA-231421)
-
Pacific Life Annuities (OKTA-231420)
-
Schwab Institutional (OKTA-230675)
-
SmartFile (OKTA-237953)
-
Trustwave Portal (OKTA-231868)
June 2019
2019.06.0: Monthly Production release began deployment on June 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Matching imported users
When you import users, you now can set up Okta rules to match any attribute that is currently mapped from an AppUser profile to an OktaUser profile. This helps you sync identities across systems and determine whether an imported user is new or if the user profile already exists in Okta. For more information, see Match imported user attributes.
Enhanced Okta LDAP integrations with Universal Directory
Okta LDAP integrations now feature custom mapping, schema discovery, and a fully extensible attribute schema that allows you to import or update any attribute stored in LDAP. With these enhancements, Okta LDAP matches the schema functionality already available to Okta's Active Directory integrations. Note: This feature is in Production for new orgs only.For more information, see Profile Editor.
Last factor remembered for authentication
End users who attempt to sign in to their org are prompted to authenticate with the last factor they used based on the device or client. For more information about authentication factors, see Multifactor Authentication.
Enhanced Group Push for Samanage
Group Push now supports the ability to link to existing groups in Samanage. For details about this feature, see About Group Push
Location zones support blacklisting
You can blacklist an entire location zone to prevent clients in the zone from accessing any URL for your org. For more information on zones, see Networks.
LDAP support for Auxiliary Object classes
You can now input a comma-separated list of auxiliary object classes when importing users from LDAP. For more information, see LDAP integration.

New macOS Device Trust Registration Task, version 1.2.1
This release provides the following:
- The enrollment process is halted if the default keychain is unavailable for some reason (for example, is corrupted or missing). This ensures that end users are not prompted to reset the keychain.
- An improved Registration Task update process ensures that enrolled devices are not inadvertently unenrolled in the event the update itself fails.
- Provides support for a query allowing admins to determine which version of the Registration Task is installed on the device.
For details, see Okta Device Trust for macOS Registration Task Version History.
New Windows Device Trust Registration Task, version 1.3.1
This release includes the following:
- Improved handling of private keys to ensure successful certificate renewal.
- To fix an issue in earlier versions where a failed certificate renewal could leave computers in a bad state, this version allows admins to trigger certificate renewal on a per-computer basis. For details, see Force certificate renewal in some circumstances.
For version history, see Okta Device Trust for Windows Desktop Registration Task Version History.
Okta Windows Credential Provider, version 1.1.4
This version contains bug fixes and general improvements
For more details, see MFA for Windows Credential Provider.
Okta Browser Plugin version 5.29.0 for all browsers
This version includes the following:
- Quick Access apps tab (currently available as Early Access)
- Real time reflection of apps and profile changes in the end-user dashboard (currently Generally Available for Preview orgs)
- Back-end enhancements
For more information, see Allow end-users to quickly access apps.
Generally Available Enhancements
Password policy default for new orgs
The default password policy for new orgs is updated to enforce that a password may not be reused if it matches one of four previously used passwords. For more information, see Sign-on policies.
Early Access Feature Manager enhancement
The EA Feature Manager now displays a dialog box detailing any known limitations for that Early Access feature. Admins will be prompted to acknowledge they have read and accept these limitations. For more information, see Manage Early Access features.
Aquera apps timeout increased
We have increased the SCIM API timeout value for Aquera and Aquera (Basic Auth) apps to 5 minutes.
Okta Sign-on widget improvements
The look and feel of the Okta Sign-on Widget has been improved for accessibility and readability.
Early Access Features
New Features
System Log event for Agentless Desktop SSO configuration updates
When changes are made to the Agentless DSSO configuration, the System Log tracks the action as shown below. For more information on Agentless Desktop SSO, see Configure Agentless Desktop SSO.

System Log event for Kerberos realm settings
When changes are made to the Kerberos realm settings, the System Log tracks the action as shown below. This event also indicates the initiator of the event and the current setting for Kerberos Realm. For more information on Agentless Desktop SSO, see Configure agentless Desktop Single Sign-on.
System Log event for Agentless Desktop SSO redirects
When Agentless Desktop SSO redirects to the IWA SSO agent or the default Sign In page, the System Log tracks the action as shown below. For more information on Agentless Desktop SSO, see Configure agentless Desktop Single Sign-on.

Fixes
General Fixes
OKTA-145726
Admins were able to enter more than one name into the Add Administrator dialog box.
OKTA-198019
Okta didn't push the user reactivation to Salesforce when a user was reassigned to the application in Okta.
OKTA-214457
Report admins were able to view the Directory > People tab.
OKTA-218387
Super admins were able to assign Org admin notifications to include Rate limit warning and violation emails.
OKTA-222666
When a user was mastered by both LDAP and AD, group rules that are dependent on the second master's group membership weren't triggered.
OKTA-225931
Inline hooks weren't called when importing data using a CSV Directory integration.
OKTA-227137
In the Device Trust set up for iOS and Android, the Reset Secret Key dialog box was too wide.
OKTA-227449
When using Internet Explorer to view Step 2 of the Device Trust Setup wizard in the Admin Console, the Previous button was missing.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Airbnb (OKTA-223490)
-
Atlassian Jira Service Desk (OKTA-225796)
-
Butler University (OKTA-225109)
-
Comerica Business Connect (OKTA-228368)
-
Corporate Traveler (OKTA-228370)
-
Curalate (OKTA-228373)
-
Go365 (OKTA-229492)
-
HighBond (OKTA-228038)
-
HM Revenue and Customs (HMRC) (OKTA-229496)
-
Hyatt Legal Plans (OKTA-229498)
-
InVision (OKTA-227444)
-
Lifeworks (OKTA-225685)
-
Lucky Orange (OKTA-228407)
-
Okta Help Center (OKTA-229494)
-
PowerDMS (OKTA-228367)
-
Safari Online Learning (OKTA-228404)
-
Schwab StockPlanManager (OKTA-226694)
-
Sonic Boom (OKTA-229495)
-
Squarespace V5 (OKTA-228400)
-
The Trade Desk (OKTA-219683)
-
TigerText (OKTA-229690)
The following SAML apps were not working correctly and are now fixed
-
HighBond (OKTA-228037)
-
Service-Now UD (OKTA-210568)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- TOPdesk Person by FuseLogic: For configuration information, see The TOPdesk Person Configuration Guide.
- TOPdesk Operator by FuseLogic: For configuration information, see The TOPdesk Operator Configuration Guide.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- SalesLoft: For Configuration information, see the SCIM Guide for SalesLoft - Okta.
SAML for the following Okta Verified applications
-
Bamboo by miniOrange (OKTA-225331)
-
Chargebee (OKTA-228025)
-
COR (OKTA-223779)
-
Fisheye/Crucible by miniOrange (OKTA-225341)
-
MindTouch (OKTA-222766)
-
QuestionPro (OKTA-229101)
-
StatusHub Admin (OKTA-228032)
-
Synerion Enterprise (OKTA-229100)
SWA for the following Okta Verified applications
-
Barracuda Email Security Service (OKTA-223499)
-
Constellation Energy Manager (OKTA-217426)
-
Greenbyte Breeze (OKTA-226657)
-
ISACA (OKTA-220349)
-
NetFortris HUD Web (OKTA-221616)
-
Techsmith (OKTA-221549)
-
UHOne Broker Portal (OKTA-224243)
Weekly Updates
Fixes
General Fixes
OKTA-207466
When locked-out user emails were sent to all admins, not just those able to unlock the users, the emails did not include user information.
OKTA-218823
When editing an existing Device Trust configuration using the new mobile Device Trust wizard, the Mobile device management provider field was blank instead of containing the vendor name.
OKTA-219430
When using the Radius app for authentication, after the initial push notification, subsequent notifications from Okta Verify listed the incorrect location.
OKTA-220139
The Send test email feature attempted to send emails to admin’s username instead of their email address.
OKTA-221079
Not all zones were displayed in the Exempt Zones search filter when there were more than 10 search results.
OKTA-224052
When users tried to sign in but chose the incorrect PIV card, clicking Retry displayed the Okta 404 error page instead of the custom error page.
OKTA-224158
Trying to access custom apps on Okta Mobile Android browser failed.
OKTA-225869
Group admins were able to add a user to an administrator group upon user creation.
OKTA-226049
If no Device Trust platform was configured in Security > Device Trust, an incorrect message was displayed in the Device Trust section of the Add Rule dialog box when creating a Sign On policy.
OKTA-226145
LDAP provisioning failed when trying to deactivate users in the AD Lightweight Directory Services (LDS) server.
OKTA-226369
The documentation icon and link on the FIDO2 (WebAuthn) factor type page was formatted incorrectly.
OKTA-229440
When a user attempted to reset the Webauthn factor and the reset failed, the wrong error message was shown.
OKTA-229725
Two System Log events were generated instead of one when the name of an Inline Hook was changed.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
HighBond (OKTA-230762)
The following SWA apps were not working correctly and are now fixed
-
American Express - Work (OKTA-230058)
-
Appsee (OKTA-230282)
-
GitHub (OKTA-229516)
-
PowerDMS (OKTA-230286)
-
Spiceworks (OKTA-230304)
Applications
New Integrations
SAML for the following Okta Verified application
-
Way We Do (OKTA-229995)
SWA for the following Okta Verified applications
-
Amgen FIRST STEP (OKTA-217876)
-
Apptio (OKTA-223714)
-
BSPlink (OKTA-224041)
-
Flightradar24 (OKTA-71196)
-
GitHub.com (OKTA-229516)
-
Notion (OKTA-220840)
-
Snowflake (OKTA-227090)
-
Synopsys eLearning (OKTA-226662)
Fixes
General Fixes
OKTA-218818
Identity Provider Routing Rules produced unnecessary System Log events.
OKTA-227097
The SMS Usage Report categorized messages to Canada as international instead of domestic.
OKTA-230756
Navigating the System Log and maps generated rate limit warnings and violations.
OKTA-231842
The Windows Hello factor was listed as enabled when only the U2F factor was enrolled.
OKTA-232420
On the Okta Privacy page, information in the Introduction and Contact Us sections was out of date.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
RedLock (OKTA-228626)
The following SWA apps were not working correctly and are now fixed
-
AT&T Business Direct (OKTA-225556)
-
Bing Ads (OKTA-230606)
-
Carta (OKTA-231435)
-
Commuter Check Direct (OKTA-230032)
-
Flexential Portal (OKTA-231722)
-
Intel - Supplier (OKTA-229135)
-
MyRackspace Portal (OKTA-231264)
Applications
Application Updates
-
We are updating the names of some app integrations as follows:
-
Jira On-premise > Atlassian Jira Server
-
Confluence On-premise SAML > Atlassian Confluence Server
-
Atlassian Confluence Server > Atlassian Confluence Cloud
-
Jira Cloud (Atlassian) > Atlassian Jira Cloud
-
- Tableau Online now supports the following Provisioning features (this is in addition to the other provisioning features that it already supports):
- Update user attributes
- New attribute: Site Role
Users that set up the Tableau Online integration and enabled Provisioning before June 12, 2019 need to follow the steps detailed in the Tableau Online Configuration Guide in order to use this new feature and/or attribute.
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- OrgWiki (SCIM): For Configuration information, see the OrgWiki Okta SCIM Configuration Guide.
SAML for the following Okta Verified applications
-
Avochato (OKTA-228020)
-
Stack Overflow for Teams (OKTA-229999)
-
Whimsical (OKTA-232056)
SWA for the following Okta Verified applications
-
American Banker (OKTA-227046)
-
Ivanti Partners (OKTA-228205)
Fixes
General Fixes
OKTA-145001
When a user entered an invalid country code in a user profile, the error message was not specific enough.
OKTA-221804
Reports listing App admin application assignments incorrectly displayed All <appname> Apps instead of only the scoped applications that the admin had access to.
OKTA-222453
Org admins were able to access the Getting Started page.
OKTA-224240
End users authenticating with Inbound SAML into Okta could not edit their profiles from the end-user dashboard.
OKTA-225137
The IWA web app redirected user sessions to the incorrect user when the web app was located behind AWS Network Load Balancer.
OKTA-228723
Updating more than one inline hook field created a System Log entry for each changed field.
OKTA-229765
Sign-in attempts that were prevented by the Pre Authentication Sign-On Policy Evaluation were not identified correctly in the System Log.
OKTA-231465
Searching for groups using the LDAP Interface worked only when the Paged Search option was enabled in the LDAP settings.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Comcast Business (OKTA-229067)
-
Toggl (OKTA-230708)
-
CloudAlly (OKTA-232109)
-
Synopsys eLearning (OKTA-232254)
Applications
Application Updates
-
We have made the following changes to our OrgWiki SCIM OAuth integration:
-
Changed the assignedID attribute to assignedId
-
Changed attribute mapping for assignedId attribute from user.employeeNumber to user.email
-
-
We have added the following SAML attribute to our Zapier integration:
-
Name: internalId, value: user.id
-
- We have added the following SAML endpoints to our Sumologic integration:
- https://service.ca.sumologic.com
- https://service.de.sumologic.com
- https://service.jp.sumologic.com
New Integrations
SAML for the following Okta Verified applications
-
Jumpstart (OKTA-225579)
-
ClickUp (OKTA-231641)
-
Atatus (OKTA-231643)
-
Auryc (OKTA-231655)
-
Postman (OKTA-233559)
-
Cloud Management Suite (OKTA-204349)
-
ChurnZero (OKTA-207112)
-
Sigma (OKTA-231716)
-
BigID (OKTA-231654)
Fixes
General Fixes
OKTA-155522
The Get access with Okta mobile link was underlined inconsistently in webview.
OKTA-205368
When an app sign-on policy rule was set to deny not-in-zone authentications, users who were denied the access were not redirected to the contact admin page as expected.
OKTA-221617
When using the group search API to search based on group names, if the group name contained a %(percentage) symbol the API call failed and returned no value.
OKTA-227706
api/v1/groups endpoint did not return the next page header unless limit was specified and defaulted to 10,000, even when more than 10,000 groups existed.
OKTA-227747
Downloading the list of admins in CSV format from the Devices > Devices tab failed with a 500 error.
OKTA-228245
The default new user activation emails were not formatted correctly when viewed inside Outlook 2016 client on Windows 10.
OKTA-229130
If an app name was bigger than 50 characters, a POST call to /api/v1/meta/schemas/apps/$instanceId/default failed with the error name: The field is too long.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Betterment (OKTA-232680)
-
GoAnywhere Login (OKTA-233563)
-
Iheart Radio (OKTA-233013)
-
Microsoft Office 365 (OKTA-232668)
-
PlanGuru (OKTA-233010)
-
ServiceM8 (OKTA-233011)
-
Shopify (OKTA-231343)
-
Solarwinds (OKTA-233164)
-
Udacity (OKTA-233012)
Applications
New Integrations
SAML for the following Okta Verified applications
-
BigID (OKTA-231654)
-
New Relic (Limited Release) (OKTA-233359)
-
SWBC - AutoPilot Portal (OKTA-226704)
-
Wandera (OKTA-233317)
-
Zscaler Private Access 2.0 (OKTA-193443)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Aquera (OKTA-230755)
SWA for the following Okta Verified application
-
Aquera (OKTA-230755)
May 2019
2019.05.0: Monthly Production release began deployment on May 13
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Password Expiry settings for Active Directory
You can specify the password expiry policies for Active Directory for all preview organizations to set the number of days before password expiry when the user receives a warning.
Improved mobile Device Trust enablement flow for admins
The new mobile Device Trust enablement flow uses a 2-step wizard for a clearer, more consistent admin experience. Existing enablement settings are migrated automatically to the new flow, so there's no need for customers with existing Device Trust deployments to change their configuration. For details, see .
Assign admin privileges to an Okta group
Super admins can now assign Okta admin privileges to Okta groups, making it easier to onboard large numbers of admins quickly. Everyone in the group receives the admin privileges assigned to the group.
IdP Extensible Matching Rules
IdP extensible matching rules allow you to define a regular expression pattern to filter untrusted IdP usernames. For details, see our IdPs page.
Configure a custom URL domain
You can customize your Okta org by replacing the Okta domain name with a custom URL domain name that you specify. For example, if the URL of your Okta org is https://example.okta.com, you can configure a custom URL for the org such as https://id.example.com. For details, see Configure a custom URL domain.
CSV Directory Integration
The CSV directory integration is a lightweight out-of-the-box option that enables you to build custom integrations for on-premises systems using the Okta On-Premises Provisioning agent. See CSV directory integration.
Active Directory agent, version 3.5.7
This version of the AD agent includes fixes to close and recreate connection groups and add a retry in response to 502 errors during import.
For agent version history, see Okta Active Directory agent version history.
System Log events for blacklisted countries
When a country is added or deleted from a blacklist, the System Log tracks the action, as shown below. For more information on blacklisting, see Network Zones.
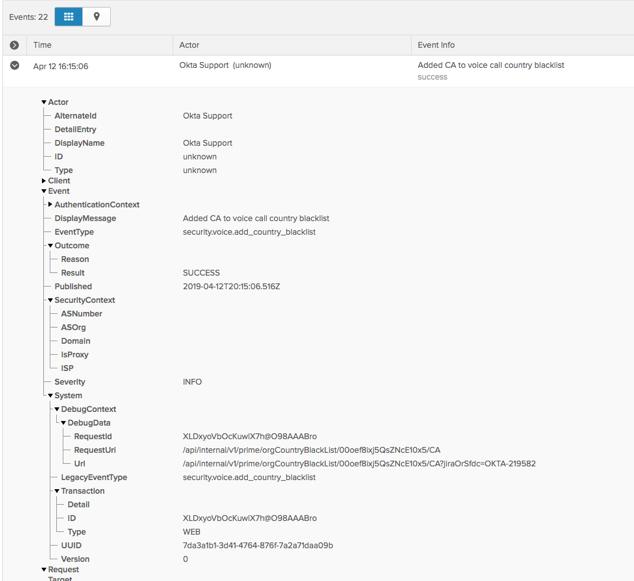

Generally Available Enhancements
Accounts locked after ten successive lockouts without a successful sign-in attempt
If an account has ten successive account lockouts followed by auto-unlocks with no successful sign-in attempts, Okta ceases auto-unlocks for the account and logs an event. For more information on account locking, see Sign-on policies.
Okta SSO IWA Web agent, new version 1.12.3
This version of the Okta SSO IWA Web agent contains internal fixes. For version history, see Okta SSO IWA Web App version history.
UI Improvements for Security Email Notifications
Settings for end user email notifications have been moved to their own section: Security Notification Emails. For more information, see General Security.
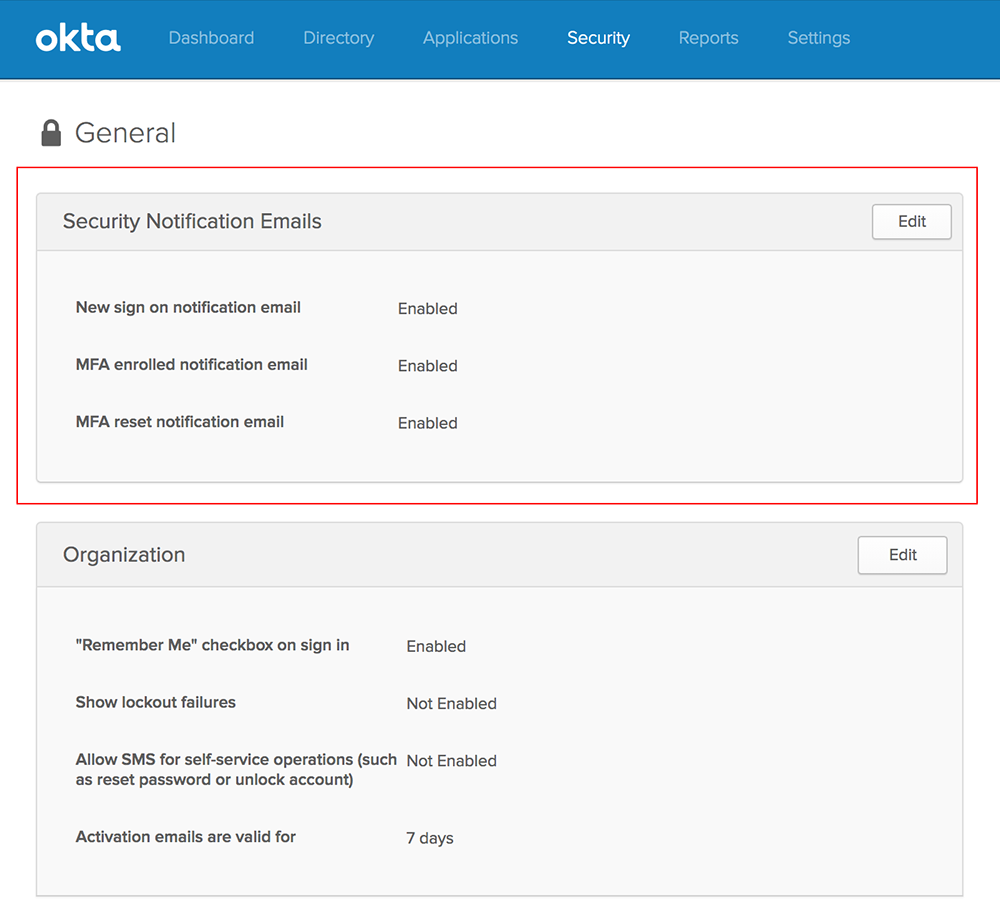
WebEx additional attributes
We have added more extensible attributes to the WebEx application. For details, see the WebEx Provisioning Guide.
DocuSign authentication mode change
We are switching the authentication mode of our DocuSign provisioning integration to OAuth. For more information, see the DocuSign Provisioning Guide.
Okta Browser Plug-in version 5.28.0 for all browsers except Internet Explorer
This version includes the following enhancements:
- Accessibility improvements
- ARIA attributes for UI elements
- Alt text for logos and images
- Access to controls and tooltips through keyboard
- Real-time reflection of the end user dashboard (currently an Early Access feature). For more information, see Okta Browser Plugin version history.
Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-215983
Email templates translations for MFA Factor Enrolled and MFA Factor Reset did not work when the Thai language was selected.
OKTA-217878
For Self Service app registration for apps with provisioning enabled, when admins changed the Approval setting from Required to Not Required the resulting error message was misleading.
OKTA-218001
System Log entries for Device Trust displayed incorrect spacing for some entries.
OKTA-220849
The SuccessFactors app import API did not work.
OKTA-221717
Routing rules for Identity Provider discovery were ignored when both IWA Desktop SSO and Agentless SSO were enabled.
OKTA-221914
Identity Provider routing rules that set User Matches to User Attribute matches Regex were not evaluated correctly.
OKTA-222256
CSV Directory scheduled incremental imports failed.
OKTA-222632
Admins who manage two groups, one granted via individual assignment, and the other via group assignment, could not assign users from one group into the other.
OKTA-222660
When using the LDAP interface, pagination on groups containing more than 1000 users failed.
OKTA-224104
Users assigned admin roles by group did not get assigned the correct default admin email settings.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Adobe Fonts (OKTA-222877)
-
Air France (OKTA-223010)
-
The Australian (OKTA-221618)
-
FINRA IARD (OKTA-223775)
-
Keap (OKTA-222416)
-
LastPass (OKTA-206231)
-
Metropolitan Bank US (OKTA-222451)
-
Mimecast Personal Portal v2 (OKTA-221490)
-
Nationale Nederlanden: Pensioen Service Online for Business (OKTA-222412)
-
Nextdoor (OKTA-223774)
-
Nmbrs (OKTA-223801)
-
Oakland Public Library Catalog (OKTA-222415)
-
Onfido (OKTA-223804)
-
Optimal Blue (OKTA-223500)
-
Plooto (OKTA-223747)
-
Poll Everywhere (OKTA-223776)
-
The San Diego Union-Tribune (OKTA-223015)
-
WhiteHat Sentinel (OKTA-222784)
-
Wrike (OKTA-223803)
Applications
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- TeamViewer: For configuration information, see Configure Provisioning for TeamViewer
- Zerotek: For configuration information, see the Zerotek SCIM Configuration Guide Instructions.
- Drafted: For configuration information, see the Drafted Okta Provisioning (SCIM) Step-by-Step Guide.
-
Spoke (www.askspoke.com): For configuration information, see Configuring Provisioning for Spoke.
SAML for the following Okta Verified applications
-
Buildkite (OKTA-215231)
-
ExpenseIn (OKTA-223019)
-
FireHydrant (OKTA-221216)
-
StoriesOnBoard (OKTA-223754)
-
Syndio (OKTA-221802)
-
Zoom SAML (OKTA-223027)
SWA for the following Okta Verified applications
-
Dynatrace (OKTA-221851)
-
Legislative Tracking System (OKTA-219355)
-
Park-line (OKTA-222807)
-
Tax Workflow (OKTA-222999)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
RescueAssist (OKTA-220114)
Weekly Updates
Fixes
General Fixes
OKTA-211631
Active Directory imports failed when federation broker mode was disabled for the app.
OKTA-212278
The Japanese translation of the end-user activation page needed improvement.
OKTA-213647
The System Log advanced search returned a 500 error when processing search terms containing the percent character (%).
OKTA-221535
Admins saw a loop when they enabled Multifactor Authentication for admins with no MFA factor set as Optional or Required in the corresponding MFA policy.
OKTA-221914
In cases where IdP Discovery was enabled, when a routing rule was configured to use User Attribute matches Regex for User Matches, the regular expression would be evaluated improperly.
OKTA-222183
If an Event Hook name was changed after it had been verified, users were asked to verify the Event Hook again.
OKTA-224205
Local users not assigned the RDP app were able to sign in to the app without being prompted for MFA if their user account on the server had rights to connect to RDP sessions and InternetFailOpenOption was set to True. Okta Windows Credential Provider version 1.1.4.0 needs to be downloaded for this fix.
OKTA-225805
The Security > General > Security Email Notifications page briefly displayed incorrect values after the email fields were set to Enabled and then the page was refreshed.
OKTA-225584H
When using the LDAP interface if a soft token was specified as a part of a bind request’s credentials, a push notification may have been erroneously sent to the user’s phone while normal authentication using the soft token was taking place.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
RedLock (OKTA-213155)
The following SWA apps were not working correctly and are now fixed
-
Cisco (OKTA-218994)
-
Visual Website Optimizer (OKTA-224230)
Applications
New Integrations
SAML for the following Okta Verified applications
-
CloudAcademy (OKTA-220845)
-
Druva 2.0 (OKTA-224318)
-
PitchBook (OKTA-222083)
-
Squadcast (OKTA-223018)
SWA for the following Okta Verified applications
-
CodySoft (OKTA-223598)
-
iAuditor (OKTA-225943)
-
Medi-Cal (OKTA-225406)
-
Saia (OKTA-223491)
Fixes
General Fixes
OKTA-220205
Failed authentication using FIDO factors were counted towards account lockout limit.
OKTA-222410
Mobile admins could not edit native apps despite having necessary permissions.
OKTA-223821
An IWA Auth event was incorrectly triggered in the System Log when a user logged in via Agentless Desktop SSO. The Authenticate User via IWA event has been removed from this flow. No other events in the flow are impacted.
OKTA-224002
Changing the LDAP configuration did not convert the next LDAP incremental import to a full import as expected.
OKTA-226976H
Setting up JAMF failed when testing the API credentials for On-Premises JAMF server that uses SSL certificate signed by by USERTrust RSA Certification Authority.
OKTA-227307
A user identifier condition evaluation for IdP Discovery sometimes returned an HTTP 400 bad request error when either the user or the attribute being evaluated was not found.
OKTA-228350H
When the EA feature, OFFICE365_USE_GRAPH_API_FOR_PROVISIONING was enabled, in certain cases Office 365 groups were deleted during an import.
OKTA-2285347H
Imports from Office 365 failed if the EA feature, OFFICE365_USE_GRAPH_API_FOR_PROVISIONING was enabled.
OKTA-230034H
Agentless Desktop SSO failed to authenticate on misconfigured Chrome browsers, resulting in a 400 Bad Request error.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Boxed (OKTA-226698)
-
CBT Nuggets (OKTA-226697)
-
Contract Express (OKTA-225826)
-
Copper (OKTA-223771)
-
Customer Service Portal (OKTA-225821)
-
Mimecast Personal Portal v2 (OKTA-226257)
-
Nextiva NextOS 3.0 (OKTA-225822)
-
Prosperworks (OKTA-225823)
-
Rackspace Admin Control Panel (OKTA-225820)
-
WP Engine (OKTA-225575)
Applications
Application Updates
The MaestroQA application integration now supports Just In Time (JIT) provisioning.
New Integrations
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Syndio: For configuration information, see Syndio SSO Configuration.
- Status Hero: For configuration information, see Configuring Okta SCIM Provisioning for Status Hero.
SAML for the following Okta Verified applications
-
Activaire Curator (OKTA-226658)
-
Aqua Cloud Security Platform (OKTA-220542)
-
CallPlease (OKTA-225465)
SWA for the following Okta Verified applications
-
Cisco Webex Teams (OKTA-221715)
-
Healthx (OKTA-226236)
-
Key Travel (OKTA-223497)
-
Technology Review (OKTA-225508)
Fixes
General Fixes
OKTA-193320
When Agentless Desktop SSO was denied due to Network Zone settings, the default Okta Sign In page was presented instead of defaulting to agent-based Desktop SSO.
OKTA-218719
No more than five applications could be created through the Admin Console for developer production orgs.
OKTA-219246
Users were unable to sign in to Okta when using Chrome browsers on Chromebooks.
OKTA-220360
The Identity Provider (IdP) admin page encountered a rate limit error when there were a large number of IdPs configured and an admin clicked through the list quickly.
OKTA-220640
Deactivated admins were not listed on the Administrators page.
OKTA-222413
Clicking the Resend Activation Email button sent the Password Reset email instead of the User Activation email.
OKTA-225581
The System Log did not log the User account unlock by admin event when a bulk account unlock action was performed by an admin.
OKTA-226272
After an OAuth2 authorize flow, ID Tokens were missing the nonce claim if a routing rule was configured to default to a social IdP.
OKTA-229525H
When a user tried to sign in to an IdP that was set up as a profile master, it sometimes resulted in incorrectly creating a new user instead of linking to the existing user.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Amazon UK (OKTA-226343)
-
Bing Ads (OKTA-226105)
-
IBM Cloud (OKTA-226062)
-
Northern Trust (OKTA-225827)
-
Sterling HSA (OKTA-223769)
-
UBS One Source (OKTA-226305)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Syndio: For configuration information, see Syndio SSO Configuration Guide.
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Cybsafe: For configuration information, see CYBSAFE-Okta SCIM App Configuration.
- Druva 2.0: For configuration information, see Manage Users from Okta using SCIM.
- Snowflake: For configuration information, see Configuring Provisioning for Snowflake.
SAML for the following Okta Verified applications
-
Aspen Mesh (OKTA-223014)
-
BitBucket by miniOrange (OKTA-225246)
-
Confluence by miniOrange (OKTA-225240)
-
Jira by miniOrange (OKTA-225231)
-
Juno (OKTA-227096)
-
productboard (OKTA-225440)
SWA for the following Okta Verified application
-
GoToMeeting (OKTA-226649)
April 2019
2019.04.0: Monthly Production release began deployment on April 15
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Enhanced Group Push for Litmos
Group Push now supports the ability to link to existing groups in Litmos. While this option is currently only available for some apps, we’ll periodically add this functionality to more provisioning-enabled apps. For details about this feature, see About Group Push.
Schema Discovery for Litmos
The Litmos provisioning app now supports UD and Schema Discovery. For more information, see the Litmos Provisioning Guide.
Enhanced Okta Mobile Security Settings for Android and iOS
Applies to:
- Okta Mobile 3.8.1+ for Android
- Okta Mobile 5.22.0+ for iOS
From the admin console, you can configure the following security settings for devices running specific versions of Okta Mobile:
- Specify the PIN length.
- Allow/disallow use of a simple PIN (repeating/ascending/descending numeric sequences).
- (Android only) Allow/disallow users taking screenshots, recording videos, or sharing their screen.
For details, see Okta Mobile Settings.
Enhanced search for Group membership rules
You can now search for group rules by name, target groups, and expression conditions. For more information about Group membership rules, see About group rules.
Change to Reset Password page
When Administrators navigate to Directory > People > Reset Password, the default view is now Locked Out users instead of All. This has been changed for performance reasons. See Reset an individual user password or Reset multiple user passwords.
LDAP Agent, version 5.5.7
This release includes the following:
- Bug fixes for incremental import.
-
A new System Log event fires when the
modifyTimestampattribute in LDAP is null for users or groups, which causes incremental import to be converted to a full import. One event per import session is logged: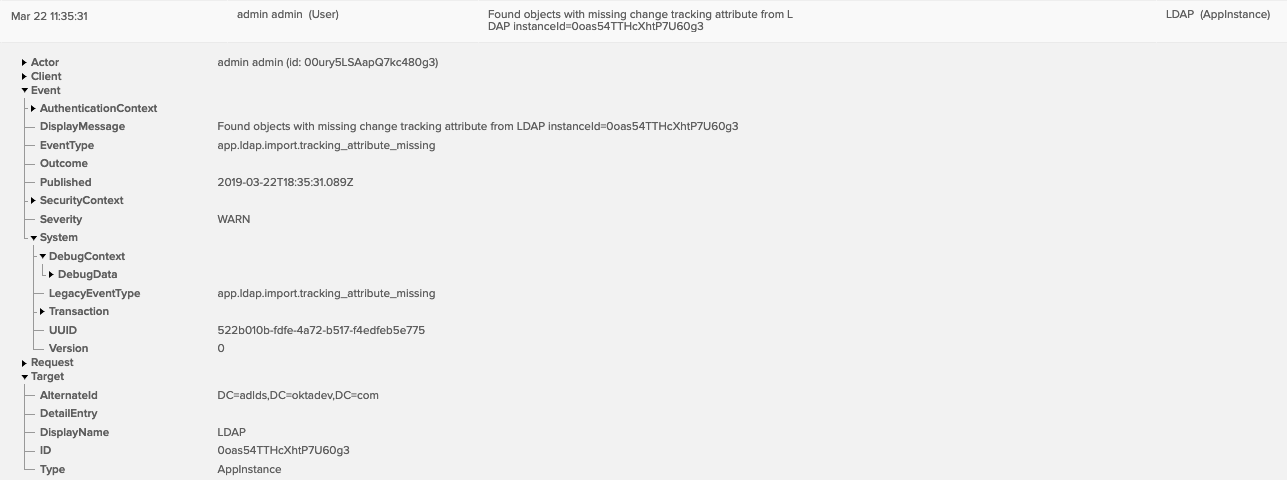
For agent version history, see Okta LDAP Agent version history.
Admin change to org settings requires additional reauthentication
To increase security on admin accounts, additional authentication is required when an admin makes changes to the org's User Account settings (Settings > Customization > User Account). If it has been more than 15 minutes since they last entered their pass- word, the admin is asked to enter their password again to reauthenticate. If multifactor authentication is configured, the admin will be prompted for MFA verification as well. For details, see Customize your Okta org.
New Template App
The Template Two Page Plug-in App has been added to the OIN. This plugin template app enables org admins to create private SWA apps for the two-page sign in flow, where the username field is on the first page, and the password field is on the second page. It works much like the Template Plug-in App and Template Plug-in App 3 Fields. For more information about Template apps, see Configure the Okta Template App and Okta Plugin Template App.
Okta Browser Plug-in version 5.27.0 for Chrome and Internet Explorer
This version includes the following enhancements:
-
For Chrome and Internet Explorer, a keyboard shortcut to open the Okta Browser Plug-in. Users will see a recommendation to use the shortcut when they click on the plugin popover window. This recommendation is only shown once.
- For Internet Explorer, you can disable the shortcut in the Registry Editor.
-
Users can also close Okta Browser Plug-in popups using keyboard shortcuts.
- For Chrome, the Okta Secure Web Authentication Plug-in is renamed to the Okta Browser Plug-in.
For more information about these shortcuts, see Keyboard shortcuts for the Okta Browser Plugin.
Okta Browser Plug-in version 5.26.2 for Safari
This version includes backend enhancements. For version history, see Okta Browser Plugin version history
Generally Available Enhancements
EA Feature Manager enhancement
The EA Feature Manager now allows you to more easily discover and enable functional dependencies for EA product features. Any EA product feature with dependencies highlights its dependencies and provides a link to that dependency so that you can enable the dependencies before enabling the EA product feature. For details, see Manage Early Access features.
Trust site links renamed to Status
The Trust site links in the Admin footer and error pages have been renamed to Status.
Sensitive values masked
For values of attributes marked as sensitive, the values are masked with asterisks in OpenID Connect and Access Token Preview. For more information on these types of tokens, see Test your Authorization Server configuration.
Custom Sign-in Pages can use Sign-in Widget version 2.18
Custom Sign-in Pages can now use Sign-in Widget version 2.18. Selecting the latest option automatically uses 2.18. For more information on the Sign-In Widget, see Okta Sign-in Widget.
Self-service OIDC Apps
OIDC apps are eligible for self-service registration. For more information about self-service registration, see About self-service registration.
Amazon AWS app updates
The Amazon AWS app integration has been updated as follows:
- Dynamic mapping of multiple accounts/roles within AWS: This feature allows dynamic mapping of multiple accounts/roles within AWS by using group assignments from Okta. For more information, see Connect Okta to Multiple AWS Instances via User Groups. Note that previously this was available as an Early Access feature. This functionality is now available as a option on the Sign On tab.
- Join all roles: A new Join all roles option is available on the Amazon AWS app Sign On page that allows admins to specify that AWS SAML uses all roles (users and groups).
- Improved security: The Amazon AWS app integration's App Filter application property on the Sign On tab is updated to provide better security and maintainability.
Rate Limits Updated
Okta's API rate limits have been updated: OAuth 2 rate limits were updated and clarified for all orgs. The limit for the api/v1/apps endpoint was updated for Enterprise orgs. For more information, see Rate Limits at Okta.
Enhanced user experience on end user dashboard
This includes the following enhancements:
- End-user dashboard UI elements respond better to mobile screen sizes.
- Launch App box is available on mobile screens. The dashboard chiclets have a new appearance.
For more information about the dashboard, see Manage dashboard tabs for end users

Early Access features from this release are now Generally Available.
Fixes
General Fixes
OKTA-191963
Some G Suite license options were missing from the Okta Integration Network.
OKTA-198767
Loading a Custom Sign On Page with a configured Custom Domain returned a 404 error if the web browser was configured with a primary language other than English.
OKTA-207897
When importing user profiles from WebEx, the country code did not convert to the country name.
OKTA-208292
While creating a new contact in the SFDC Customer Portal, Okta provisioning did not search for matching existing Contact objects in Salesforce.
OKTA-208907
When a new LDAP instance was configured, settings related to Delegated Authentication were overwritten.
OKTA-209762
End users could not upgrade from Okta Verify with a One Time Passcode (OTP) to Okta Verify with Push if their org Sign On policy did not prompt for an MFA, but their app Sign On policy did.
OKTA-210250
The lastDownloadToken field in agent logs did not update after incremental imports.
OKTA-210873
When BambooHR was Profile Master, expression mappings were not updated for Office 365.
OKTA-211709
Litmos did not automatically reschedule and import a job once a rate limit was reached.
OKTA-213074
The App Admin role could not be assigned when an org had a significantly large number of deleted apps.
OKTA-213122
Pushing groups from Okta to G Suite failed when group member was already in a group, or had been already removed.
OKTA-213291
When importing users via a CSV file, the Do not create a password and only allow login via Identity Provider option could not be selected.
OKTA-213293
When conducting an import from Workday to Okta, boolean properties were not handled properly and did not map to the actual values.
OKTA-214020
In Agentless Desktop SSO settings, only the first 20 instances were editable.
OKTA-216082
When pushing users from Okta to Salesforce Federated ID, the profile attribute could not be set to not required.
OKTA-218007
Identity Providers did not support matching the user with an Okta username or email when the IdP Extensible Matching Rules feature was enabled.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Amadeus Selling Platform Connect (OKTA-217081)
-
Amplitude (OKTA-215291)
-
Answer 1 Zapier (OKTA-215720)
-
AT&T Cybersecurity (formerly AlienVault) (OKTA-217657)
-
Atlassian (OKTA-215304)
-
Basecamp (OKTA-215286)
-
BB&T (OKTA-217648)
-
Buffer (OKTA-217890)
-
CareFirst (OKTA-215296)
-
CyberSource (OKTA-217636)
-
FINRA Web CRD (OKTA-215277)
-
HipChat (OKTA-215244)
-
IBM Partner World (OKTA-215287)
-
Loggly (OKTA-215999)
-
Pacer (OKTA-216799)
-
RingCentral (OKTA-215283)
-
Smallpdf (OKTA-217685)
-
SmartyStreets (OKTA-217661)
-
T. Rowe Price (OKTA-214661)
-
TruQu (OKTA-216808)
-
Vungle (OKTA-215348)
-
WePay (OKTA-215245)
-
WP Engine (OKTA-217760)
-
Yelp Biz (OKTA-215074)
-
YouCanBook.me (OKTA-215253)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Idiomatic: For configuration information, see Configuring Provisioning for Idiomatic.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Infor CloudSuite: For configuration information, see Infor CloudSuite Provisioning for Okta Online Help.
- Egnyte: For configuration information, see Configuring Okta SCIM Provisioning for Egnyte.
- Fin Analytics: : For configuration information, see Using Okta for Fin SSO.
SAML for the following Okta Verified applications
-
Area 1 Security (OKTA-216838)
-
BuiltWith (OKTA-216847)
-
Kiva (OKTA-215932)
-
Palo Alto Networks - Aperture (Reverse Proxy) (OKTA-214670)
-
Workable (OKTA-212879)
SWA for the following Okta Verified applications
-
American Express vPayment (OKTA-212465)
-
B of A Automative Dealer Services (OKTA-214379)
-
BigBlueOnline (OKTA-214709)
-
BrickFTP for Las Vegas Nevada (OKTA-214142)
-
Cal Bank Trust (OKTA-213107)
-
Comcast Payment Center (OKTA-217425)
-
Connect CDK Global (OKTA-216063)
-
DigiDip (OKTA-217112)
-
European Union (OKTA-209889)
-
FIS E-Banking Services: Generic Login Flow (OKTA-209723)
-
Frontier Communications (OKTA-214708)
-
Frontier Communications (OKTA-217302)
-
FSRS gov Awardees (OKTA-217427)
-
Greenwaste (OKTA-217198)
-
IOI Payroll V2 (OKTA-214471)
-
Leumi Bank UK (OKTA-215922)
-
Metropolitan Bank US (OKTA-215923)
-
MyMerrill (OKTA-213642)
-
Nationale Nederlanden: Pensioen Service Online for Business (OKTA-214224)
-
Obeo (OKTA-210256)
-
PNC Foreign Currency (OKTA-215697)
-
Premium Haystack (OKTA-215438)
-
Rookout (OKTA-213093)
-
Schoox (OKTA-215053)
-
Signature Bank (OKTA-201621)
-
Silvergate Bank (OKTA-201618)
-
Ski Data for 2145 Parkplace (OKTA-214361)
-
Van Lanschot (OKTA-214922)
Weekly Updates
Fixes
General Fixes
OKTA-213061
Group admins scoped to manage a group that was assigned an admin role did not display user or group pages properly.
OKTA-214827
After a SPA OIDC client was created, the Client Authentication method was not displayed in the UI as expected.
OKTA-215691
Adding an IP address to an IP Blacklist Zone from the System Log resulted in a 400 error.
OKTA-215977
When an AD agent connected via proxy, a TLS alert to the proxy caused AD imports to intermittently fail.
OKTA-218083
Search functionality for IDP routing rules failed to get results for apps that contained the "|" pipe character.
OKTA-219226
The enrollment window for MFA U2F used an incorrect CSS that caused the display to be slightly incorrect.
OKTA-221403
There was no space between the app name icon in the app search results on the end user dashboard.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Miro (OKTA-219464)
The following SWA apps were not working correctly and are now fixed
-
Expensify (SWA Only) (OKTA-218710)
-
HM Revenue and Customs (HMRC) (OKTA-218854)
-
Rabobank Internetbankieren (OKTA-218881)
-
Sprout Social (OKTA-218711)
-
The Information (OKTA-218929)
-
UserVoice (OKTA-218709)
-
WFX (OKTA-218240)
Applications
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- TOPdesk Operator by FuseLogic: For configuration information, see the TOPdesk operator provisioning integration guide.
SAML for the following Okta Verified applications
-
Broker Buddha (OKTA-219121)
-
Celonis (OKTA-217901)
-
Drafted (OKTA-219407)
-
Enzyme QMS (OKTA-213382)
-
Matik (OKTA-218397)
-
PressPage (OKTA-218318)
-
RStudio Connect (OKTA-219846)
-
Trend Micro Apex One as a Service (OKTA-218066)
-
Zerotek (OKTA-218354)
SWA for the following Okta Verified applications
-
California Water (OKTA-217189)
-
Compass PHS (OKTA-207732)
-
Harland Clarke Checks Center (OKTA-216860)
-
Lola (OKTA-211494)
-
New York Magazine (OKTA-215724)
-
Nexus System Connect (OKTA-215329)
-
United TranzActions (OKTA-216858)
-
Westchester Fast Track (OKTA-218185)
Fixes
General Fixes
OKTA-201787
The Okta browser plugin did not work in Chrome for the ALMobile private app.
OKTA-205783
Private apps that were incorrectly categorized as User Directory appeared on the Directory Integrations page.
OKTA-206470
User credentials were not passed to the LastPass app when using Chrome.
OKTA-206749
Super admins could subscribe to org-wide email notifications for admin roles, to which they did not have permission.
OKTA-207909
When setting up a new password, the Change Password button did not become inactive after the first click.
OKTA-210587
The Dashboard displayed links that the following admin roles cannot access: App, Group, Help Desk and API access management admins.
OKTA-210776
The security image on the sign-in page did not load when the username contained a plus (+) character.
OKTA-210869
An App admin assigned permissions through a group role was not able to edit the SAML settings of an app for which they had permission.
OKTA-210961
The Need help signing in link did not have ARIA attributes to indicate its expand or collapse state.
OKTA-211541
When an admin created a user with a password that did not meet the password requirements, the System Log showed a successful Create Okta User event even though the user creation failed.
OKTA-213686
Authorization for an app failed when using a routing rule configured to default to a social identity provider.
OKTA-214203
In some cases, reactivating a user created a duplicate entry in the System Log.
OKTA-214365
Some /authn APIs were missing the Cancel link in their response.
OKTA-215638
The Japanese translation of the password reset restrictions needed improvement.
OKTA-215983
Email templates for MFA Factor Enrolled and MFA Factor Reset did not translate into the Thai language correctly.
OKTA-221657
When IdP Discovery was enabled for some customers, IWA sign-in flows stopped working due to browsers truncating requests in the URL.
OKTA-221667
An App Admin assigned permissions through a group role could only view OpenID Connect apps when creating a new app.
OKTA-221708
Some icons were missing when signing in to the Gmail app using Okta Mobile for Device trust.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
2020 Spaces (OKTA-220169)
-
ADP Workforce Now (OKTA-221296)
-
Alabama Power (OKTA-220005)
-
Avalara (OKTA-218996)
-
Benefit Resource Inc (OKTA-218390)
-
Breeze (OKTA-221637)
-
CAPPS Enterprise Portal (OKTA-219133)
-
CRG emPerform (OKTA-219139)
-
Express Xactlycorp (OKTA-220904)
-
EZPassNY (OKTA-218426)
-
Harland Clarke Checks Center (OKTA-221646)
-
Lifeworks (OKTA-219537)
-
New York Times (OKTA-221218)
-
Redis Labs (OKTA-221219)
-
Shopify (OKTA-221653)
-
SpringCM (OKTA-217660)
-
T. Rowe Price (OKTA-220319)
Applications
Application Updates
We are switching the authentication mode of our DocuSign provisioning integration to OAuth. For more information see the DocuSign Provisioning Guide.
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Chorus.ai: For configuration information, see Configuring Provisioning for Chorus.ai.
SAML for the following Okta Verified applications
-
Braze (OKTA-218398)
-
Chorus.ai (OKTA-217886)
-
Fulcrum (OKTA-220635)
-
Harness (OKTA-219122)
-
IT-Conductor (OKTA-220627)
-
MaestroQA (OKTA-220841)
-
PhraseApp (OKTA-220846)
-
Zapier SAML (OKTA-219123)
-
ZenQMS (OKTA-220313)
SWA for the following Okta Verified applications
-
Adobe Admin Console (OKTA-214878)
-
Adobe Fonts (OKTA-217129)
-
BigBlueOnline (OKTA-214709)
-
Catsy (OKTA-221527)
-
CFA Institute (OKTA-218957)
-
Cloud Ranger (OKTA-220214)
-
Condeco Connect (OKTA-220492)
-
E-Boekhouden (OKTA-217430)
-
First Republic Securities (OKTA-217204)
-
Jaggaer Supplier Support (OKTA-221245)
-
MD-Staff (OKTA-211897)
-
my529 Financial Advisor (OKTA-219991)
-
Outgrow (OKTA-217883)
-
PG&E (OKTA-217203)
-
SecureDock (OKTA-220676)
-
Stratechery (OKTA-217201)
-
The Trade Desk for Goodway Group (OKTA-218990)
-
US Plastic (OKTA-220482)
March 2019
2019.03.0: Monthly Production release began deployment on March 11
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Security Tips on admin console
Security Tips now appear on the admin console. These tips suggest a list of security features that can be enabled to improve the security posture of an org. For more information, see HealthInsight.
Skip importing groups during Office 365 user provisioning
While provisioning Office 365 in Okta, you can choose to skip importing Office 365 user groups and group memberships into Okta. This allows you to focus initially on user provisioning and take care of group assignments later in the deployment process. For more information, see Skip importing groups during Office 365 user provisioning.
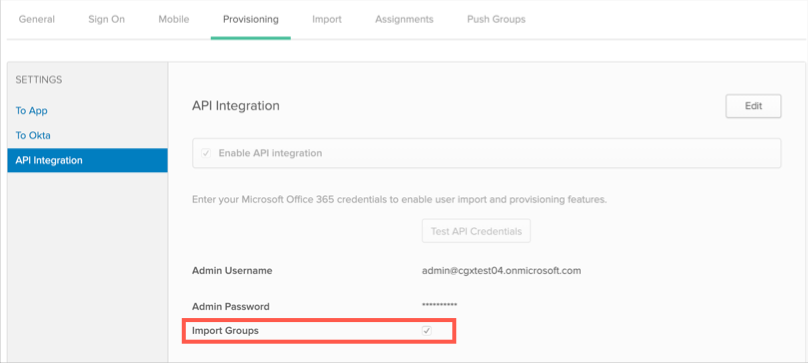
Additional Custom Attributes for Webex integration
Our Webex integration is enhanced by adding support several new custom attributes. Okta imports these attributes that you can then map as additional custom properties. For more information see the Webex Provisioning Guide.
System Log enhancement
We’ve enhanced our System Log to take advantage of our new Network Zones feature. Admins can now hover over an IP address that's part of an event and navigate through the series of menus to add that IP address to either the gateway or proxy list of IP addresses.
SCIM App Wizard
Okta supports SCIM (System for Cross-domain Identity Management specification) provisioning for apps created with the Okta App Integration Wizard (AIW).
For more information about SCIM, see SCIM-Based Provisioning Integration. For instructions to enable SCIM for app-wizard apps, see The SCIM App Wizard.
View admin list by role
Super admins can now filter the list of admins by role and type for easier searching.
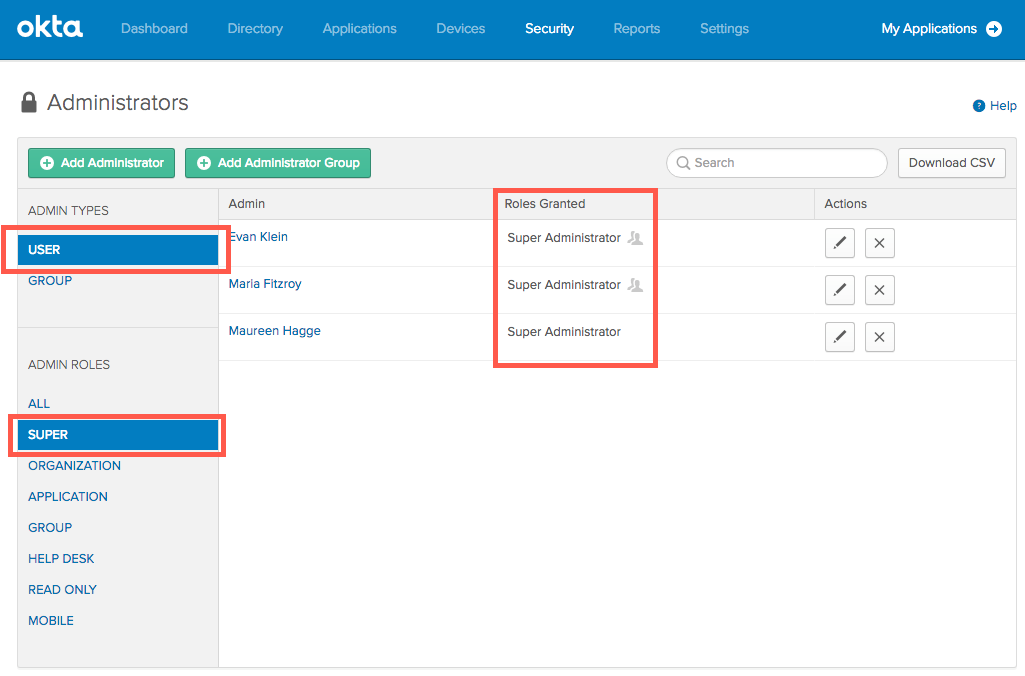
Social Identity Providers
This feature allows your end users to self-register with your custom applications by first authenticating through their existing social identity accounts, such as Facebook, Google, Yahoo, or LinkedIn. For new users of your custom application, Okta creates a Just In Time (JIT) Okta user profile based on attributes stored in their social profiles.
For more information see Identity Providers.
System Log events for YubiKey Seed
New System Log events have been added when a user uploads or revokes a YubiKey Seed successfully.
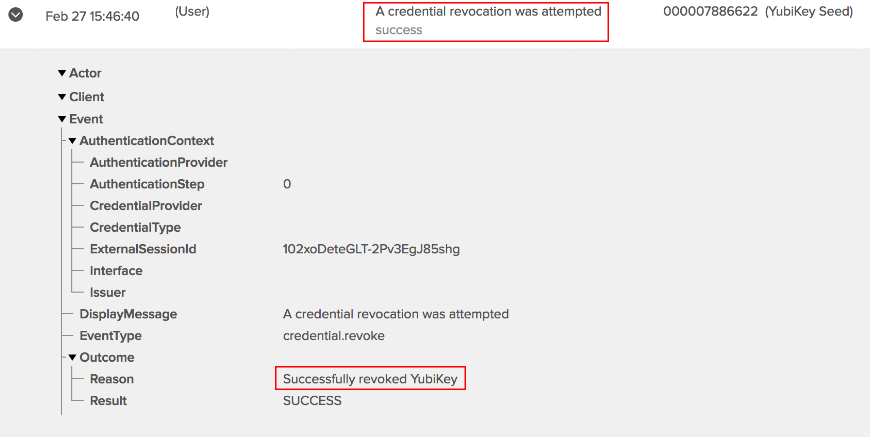
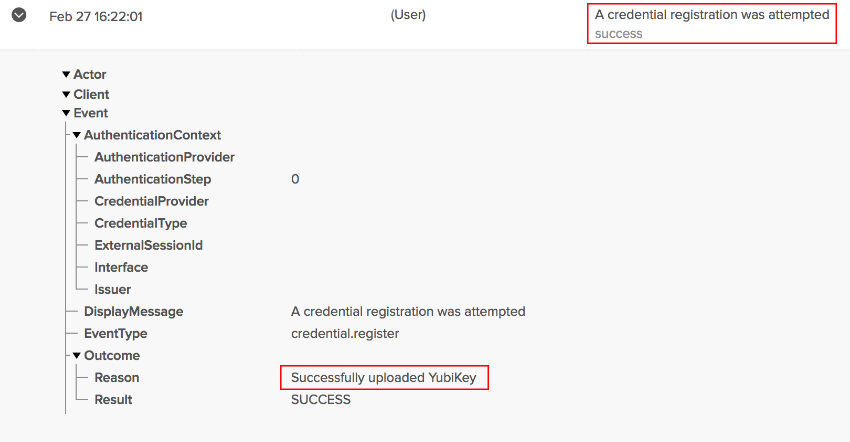
System Log events for Active Directory imports
A new System Log event appears when an Active Directory import is converted from an incremental to a full import.
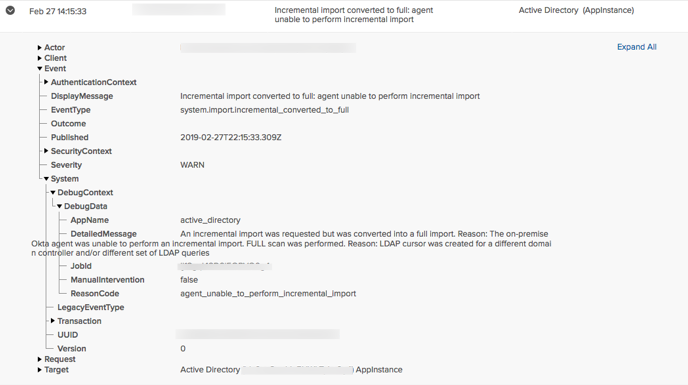
A new System Log event appears when a full Active Directory import is required.
Admin role behavior changes
Admin roles assigned by adding a user to an Admin group can no longer be edited or customized for individual users. To edit or remove admin privileges from a user that were assigned by adding the user to an admin group, you must remove the user from the group. Additionally, if a user has individual admin privileges assigned to them as well as admin privileges they received due to being in an admin group, each admin privilege will be listed separately. The icons indicate whether the privilege was assigned individually or as a result of group membership.
Use Expression Language (EL) to map AD attribute to Workplace by Facebook
Okta now uses EL to map manager from AD to the Workplace by Facebook app for all new apps. For more information about Workplace by Facebook provisioning, see the Workplace by Facebook Provisioning Guide.
CPC app operations throttling
To ensure execution of all customers’ provisioning operations in a timely manner, operations for CPC apps are now throttled on a per org basis.
Generally Available Enhancements
Documentation links for Security Checklist
The Security Checklist on the admin console is updated to include documentation links for each setting. For more information about this feature, see .
Region codes updated for network zones
Network zones region codes are updated to adhere to the specifications of the ISO-3166 standard. This update includes changes to region names within Mexico, the Democratic Republic of the Congo, and Czech Republic. For more information about using country and region codes, see Network Zones.
Early Access Features
New Features
Review prompt on Okta Mobile for iOS
End-users using Okta Mobile on iOS are prompted to provide an App Store rating for the app. When they provide a rating in the app and click Submit, they are taken to the App Store page for the Okta Mobile app to provide more optional feedback about the app. They can click Not now to dismiss the option. For more information, see About Okta Mobile.
OIN Manager supports multiple application submissions
When submitting a new application integration for review by Okta, the OIN Manager now supports multiple concurrent application submissions (for new orgs only).
Fixes
General Fixes
OKTA-135037
Disabled users in the Roambi app were incorrectly imported into Okta.
OKTA-205616
The tooltip for username was missing on the Identifier-first login page when using IdP Discovery.
OKTA-205713
The Okta Interstitial page used an incorrect font on Windows OS.
OKTA-205734
The authentication process took more time than expected when the "Permit Automatic Push for Okta Verify Enrolled Users option for the RADIUS application was activated.
OKTA-207282
End-users could not see the Zip Code on the Personal Information page on the end user dashboard despite having read-write permissions.
OKTA-207634
Customers were not properly redirected to the correct JIRA On-Prem instance after updating to JIRA On-Prem version 3.0.7.
OKTA-208446
Updates to the Okta Reporting Path were not saved on the first attempt and failed with errors when configuring API integration for the UltiPro app.
OKTA-209118
When configuring an OPP app with a SCIM connector, authentication headers were sometimes misconfigured.
OKTA-210624
For Desktop Device Trust flows, authentication failures reported in the System Log lacked sufficient detail.
OKTA-211769
When Single Line Prompt was enabled in the Radius app, login using a soft token generated duplicate events in the System Log.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Allegra False Creek (OKTA-211577)
-
Amazon Web Services (OKTA-200754)
-
Basecamp (OKTA-210785)
-
Bitbucket (OKTA-209277)
-
Citi Velocity (OKTA-211570)
-
CrazyEgg (OKTA-208795)
-
Expensify (SWA Only) (OKTA-209343)
-
Glance (OKTA-211569)
-
Google AdSense (OKTA-208416)
-
Meetup (OKTA-208796)
-
MSCI ESG Manager (OKTA-210231)
-
SecureMail Cloud (OKTA-210230)
-
Stamps.com (OKTA-211576)
-
T. Rowe Price (OKTA-208929)
Applications
Application Updates
-
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
WorkRamp: For configuration information, see Configuring SCIM Provisioning for WorkRamp.
-
Expensify: For configuration information, see Expensify's Deactivating User's with Okta.
-
-
Namely now supports the following Provisioning features (in addition to the Profile Master feature that it already supports):
-
Create users
- Update user attributes
For users that have set-up the Namely integration and enabled Provisioning before July 23, 2018, they have to follow the migration steps detailed in the Namely Configuration Guide if they want to use the new feature.
-
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- LogMeIn: For configuration Information, see Configuring Provisioning for LogMeIn Products.
-
SendSafely: For configuration Information, see Configuring SCIM Provisioning for SendSafely.
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Zscaler 2.0 (OKTA-210280)
SAML for the following Okta Verified applications
-
Idiomatic (OKTA-210213)
-
Stack Overflow Enterprise (OKTA-211271)
SWA for the following Okta Verified applications
-
1st Global: Identity Server (OKTA-203266)
-
Amazon Incentives (OKTA-205373)
-
ClickToTweet (OKTA-206100)
-
Cumberland (OKTA-202677)
-
ForeScout (OKTA-203181)
-
Fremont Bank (OKTA-205715)
-
GoodHabitz (OKTA-206150)
-
HR Certification Institute (OKTA-204048)
-
Johnson & Johnson (OKTA-207334)
-
LinkedIn Sales Navigator (OKTA-202984)
-
LivePerson LiveEngage (OKTA-206681)
-
Lutron (OKTA-206149)
-
PNC Retirement Directions Participant Login (OKTA-206676)
-
SagicoreLife: Agent Login (OKTA-202262)
-
SecurePay (OKTA-210232)
-
Supermetrics (OKTA-205909)
-
Template Two Page Plugin App (OKTA-207162)
-
Texas Mutual (OKTA-207028)
-
Zscaler 2.0 (OKTA-210280)
Weekly Updates
Fixes
General Fixes
OKTA-184126
Custom domains were incorrectly reserved before being verified.
OKTA-194918H
Password credentials for the Paychex Online app were not inserted into the Password field in Edge browsers.
OKTA-204814
Certain group membership rules to assign AD-mastered users to an Okta group did not remove the users from the group when they were deactivated in AD.
OKTA-207871
Editing certain existing custom SAML app configurations resulted in errors.
OKTA-209615
In some cases, the EA Feature Manager page on the Admin Console had mismatched or empty feature descriptions.
OKTA-211237H
The complex password generator was able to generate passwords in the format of an <html> tag.
OKTA-212828
Resetting Web Authentication from the end user Settings page displayed errors even when the action was successful.
OKTA-212890
The Getting Started page on the Admin Console displayed errors for Internet Explorer 10 users.
OKTA-213551H
Push Group failed for the Zscaler 2.0 app and no Retry task was available in the admin console.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
NetSuite (OKTA-209499)
The following SWA apps were not working correctly and are now fixed
-
MileIq (OKTA-212466)
-
Ncontracts (OKTA-209463)
-
Ray Wenderlich (OKTA-212010)
-
Sequr (OKTA-212548)
-
Skillshare (OKTA-211690)
-
WorkFlowy (OKTA-212464)
-
WP Engine (OKTA-210832)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Casetabs (OKTA-212169)
-
Projector PSA (OKTA-212170)
-
Sqreen (OKTA-211580)
-
UWV Employer Portal (OKTA-209228)
SWA for the following Okta Verified applications
-
Arrowhead Auto: Producer Login (OKTA-203718)
-
Citi Investor Reporting For Structured Finance (OKTA-194263)
-
ClinPhone (OKTA-211579)
-
IDShield Plus (OKTA-207842)
-
Salt Lake Tribune (OKTA-203950)
-
Taleo Enterprise User Login (OKTA-211578)
-
Wright National Flood Insurance Company (OKTA-207916)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Microsoft Office 365 (OKTA-199395)
Fixes
General Fixes
OKTA-130296
When configuring JIT settings for a social identity provider, the Everyone group could erroneously be selected as one of the Group Assignments.
OKTA-139818
Attempting to set user credentials for an AppUser to a string longer than the permitted maximum length displayed an Internal Server Error instead of a Forbidden message.
OKTA-204598
Some successful MFA events did not appear in the System Log for some Orgs.
OKTA-205976
In some cases, Web Authentication FIDO2 appeared as Windows Hello (Web Authentication) while resetting factors on the Admin Console.
OKTA-209194
First time import of Namely-mastered users into Active Directory failed.
OKTA-209332
An app's Current Assignments report did not autopopulate the app's name even when the report was accessed through the app page.
OKTA-213567
Sometimes Okta Verify took too long to respond back to the browser, resulting in time-outs.
OKTA-214003
Certain invalid state token values caused the AuthN API to return an internal server error.
OKTA-214175
Okta Verify push did not work when authenticating via the LDAP Interface.
OKTA-217033H
The Group Attribute Statements filter could not be saved in a custom SAML App.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Dell Premier (OKTA-213974)
-
Drift (OKTA-213975)
-
Fidelity & Guarantee Life (OKTA-213252)
-
Fitbit (OKTA-213976)
-
Flurry (OKTA-213977)
-
IBM Cloud (OKTA-214031)
-
NoMachine: Workbench (OKTA-210779)
-
Poll Everywhere (OKTA-213315)
-
RingCentral (OKTA-213133)
-
Safari Online Learning (OKTA-213099)
-
T. Rowe Price (OKTA-212189)
Applications
New Integrations
SAML for the following Okta Verified applications
-
Automox (OKTA-212528)
-
HealthKick (OKTA-212505)
-
Hive (OKTA-213326)
-
Sapling HR (OKTA-212512)
-
Workpath Platform (OKTA-213337)
SWA for the following Okta Verified applications
-
2020 Spaces (OKTA-210855)
-
Alabama Power (OKTA-211825)
-
Atlassian Service Desk (OKTA-206555)
-
BuildingConnected (OKTA-210302)
-
Cat SIS (OKTA-210839)
-
CoSchedule (OKTA-210164)
-
Fidelity Funds Network (OKTA-209733)
-
Interxion (OKTA-211723)
-
IOI Payroll V2 (OKTA-210854)
-
John Deere Service Advisor (OKTA-210838)
-
LexisNexis Bridger Insight XG (OKTA-195697)
-
LexisNexis Member Login (OKTA-209424)
-
Rabobank Internetbankieren (OKTA-209208)
-
Regus (OKTA-209724)
-
Rhino3d (OKTA-209991)
-
Salesforce (force.com) (OKTA-209752)
-
Steelcase Americas Village (OKTA-207490)
-
Steelcase Product Reference (OKTA-213961)
-
Thomson Reuters Practical Law (OKTA-209079)
-
Traackr (OKTA-210193)
Fixes
General Fixes
OKTA-193430
The German translations for password requirements on the Welcome page and in the Password Reset flow were incorrect.
OKTA-203455
HTML in the Activation Email template did not render properly.
OKTA-204472
The Status box on the Admin Console erroneously displayed non-existent tasks for Group Push mappings.
OKTA-205284
When users tried to access some SAML apps that they were not assigned, they got an incorrect response code.
OKTA-208042
Certificate renewal failures sometimes rendered the existing certificate unusable and Device Trust validation failed until renewal was attempted again and succeeded. Note: This fix requires the New Windows Device Trust Registration Task, version 1.3.1.
OKTA-209139
Features in the Early Access Feature Manager could be disabled even if they had dependent features that were enabled and not in Early Access Feature Manager.
OKTA-210984
The alt text for the logo on the Sign In page was not clear.
OKTA-214498
In some cases the activation token in the Activation Email was valid beyond the set time limit.
OKTA-218084H
GSuite group memberships could not be imported from nested groups. Note that the following feature flags must be enabled: PROV_GOOGLE_USE_ACTUAL_ID_AS_EXTERNAL_ID_FOR_GROUP, PROV_GOOGLE_FIX_GROUP_ID_NESTED. Contact Okta Support for assistance.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Cisco (OKTA-213384)
-
CCH Intelliconnect (OKTA-214497)
-
Frontier (OKTA-214713)
-
myKASTLE (OKTA-214293)
-
Workable (OKTA-214303)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN:
- Abstract: For configuration information, see Configuring SCIM Provisioning for Abstract.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps are now available in the OIN as Early Access:
-
Infor CloudSuite: For configuration information, see Infor CloudSuite Provisioning for Okta Online Help.
SAML for the following Okta Verified applications
-
CallCabinet Atmos (OKTA-211053)
-
CareerVillage (OKTA-214516)
-
Cisco ASA VPN (SAML) (OKTA-196744)
-
FactSet (OKTA-214985)
-
Leapsome (OKTA-214515)
-
Status Hero (OKTA-215230)
-
Valimail Defend (OKTA-209773)
-
Zapier SAML (OKTA-214934)
SWA for the following Okta Verified applications
-
AJ Bell (OKTA-212543)
-
BSA-E-Filing (OKTA-213447)
-
Clear Company Krostcpas (OKTA-213476)
-
Hitachi Visualization Suite (OKTA-212856)
-
Las Vegas Open Data (OKTA-212857)
-
Lumity (OKTA-212197)
-
PricingDirect (OKTA-212352)
-
Tech Data NL (OKTA-212439)
-
Tracxn (OKTA-209902)
-
Valet Living (OKTA-214387)
February 2019
2019.02.0: Monthly Production release began deployment on February 19
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
PIV Support for MTLS
Authentication for PIV (Personal Identification Verification) now supports the MTLS protocol and may be used once you have whitelisted the following domain: *.mtls.okta.com. For more information about IP whitelisting and Okta domains, refer to Allow access to Okta IP addresses.
Location-based network zones
Zones can now be defined based on geo-location. For more information on location zones, see Networks.
Remember Device setting enabled by default
As part of sign-on policy rules, admins can now enable by default the setting for end users to not be challenged on the same device again upon sign in. For more information on this feature, see Security Policies.
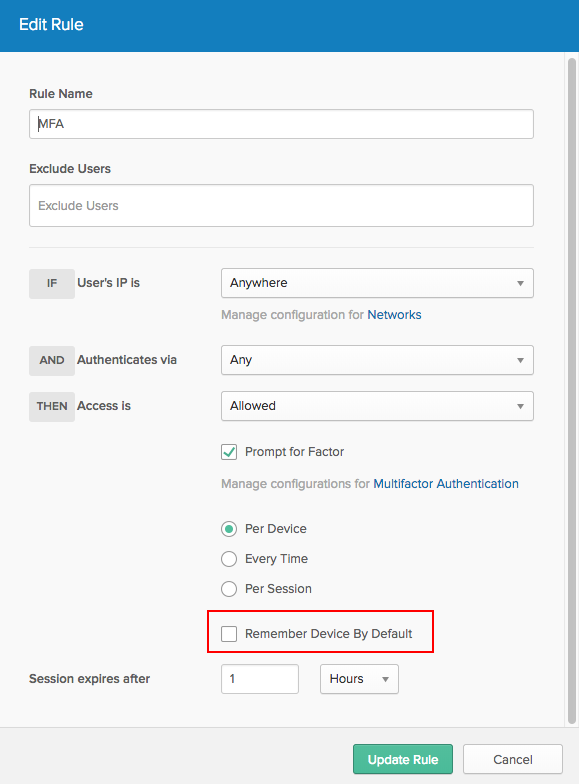
Support for converting contractors to full time employees in Workday
Added support for converting contractors to full time employees within Workday. For more information see Workday Provisioning Guide.
End-user plugin settings
End users can now configure Okta Plug-in settings directly from the Your Apps menu  in their browser. This feature lets end users customize the local behavior of the plugin, and helps end users and admins troubleshoot problems that may occur with the plugin. For details, see Configure the Okta browser plugin (end user settings). This feature is GA for Preview orgs only.
in their browser. This feature lets end users customize the local behavior of the plugin, and helps end users and admins troubleshoot problems that may occur with the plugin. For details, see Configure the Okta browser plugin (end user settings). This feature is GA for Preview orgs only.
Copy temporary password to clipboard
When resetting a password, admins can copy the temporary password directly to the clipboard by clicking the copy to clipboard icon.
Google Integration updated
Okta's Google social login integration has been updated to account for the deprecation of the Google+ API. More information can be found in our Knowledge Base.
Signature and Digest Algorithms for Template WS-Fed Applications
Template WS-Fed applications can now choose between SHA1 vs SHA256 options for their Signature and Digest Algorithms. In addition, all Template WS-Fed applications will have X.509 certificates signed with SHA256. For more information, see Configure the Okta Template WS Federation Application.
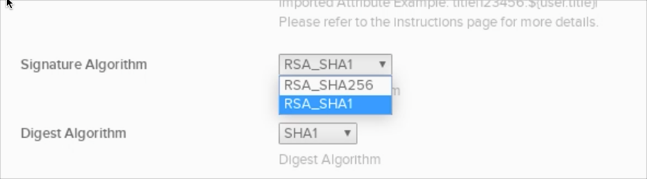
Okta Plug-in for Safari updated to 5.26.1
The Okta plugin for Safari browsers is updated to version 5.26.1. To meet Apple requirements, Okta built this version of the plugin as an App Extension to replace the legacy .safariextz architecture. This and future versions of the Okta Safari plugin will be available from the Mac App Store. For history, see Okta Browser Plugin version history
Generally Available Enhancements
Email notifications enabled by default
The setting for sending an email notification to end users who enroll in a new factor or request a factor reset is now enabled by default. For more information, see General Security.
EA Feature Manager feature list expanded
You can now enable Early Access features in the EA Feature Manager that may have other feature dependencies. If you select an EA feature that has a dependency on another feature, you must enable the required feature dependency before enabling your initial selection. For details, see Manage Early Access Features.
G Suite Provisioning Guide
Provisioning for G Suite now includes a link to the G Suite Provisioning Guide.
Early Access Features
New Features
MFA for ePCS
Okta provides multifactor authentication for the Electronic Prescribing for Controlled Substances (ePCS) system with its integration to Epic Hyperspace, which is the front-end software that launches ePCS. For more information, see MFA for Electronic Prescribing for Controlled Substances - Hyperspace
Early Access Enhancements
Inline MFA Enrollment for RADIUS Apps
Admins can now either allow or prohibit end users to access resources protected by RADIUS to enroll in MFA while authenticating. For more information, see RADIUS applications in Okta.
Fixes
General Fixes
OKTA-145565
The response error message included a typo when an invalid 4-byte UTF-8 character (such as an emoji) was input into a text field
OKTA-201017
Sometimes when a Microsoft proxy was used, the proxy IP was displayed as the client IP in the System Log although the policies were enforced on the client IP.
OKTA-201572
End users had difficulty entering an SMS MFA code on the Okta sign-in page because a large portion of the Enter Code field was not clickable.
OKTA-201733
The Early Access feature that allows Okta-mastered users to move across OUs sometimes failed to update the organizational unit for Active Directory users whose account was pushed to Active Directory from Okta and whose AD username (CN) contained one of the following characters: ,\#+<>;"=
OKTA-203163
User profile updates for the Cornerstone app failed if the user already existed in Cornerstone.
OKTA-206191
In some cases group rules dependent on other group rules were not processed properly during user updates.
OKTA-206270
The Identity Provider list did not properly display the Authorize URI and Redirect URI fields.
OKTA-207402
Attempts to apply an app Sign On Policy Rule to users returned a spinning icon. This issue only occurred on Preview orgs.
OKTA-207554
The app Sign On Policy Rule that denied user access was not logged in the System Log’s application.policy.sign_on.deny_access event.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
CyberArk Password Vault Web Access (OKTA-206890)
The following SWA apps were not working correctly and are now fixed
-
BullsEye Telecom (OKTA-207387)
-
Easy Projects (OKTA-207086)
-
Google Data Studio (OKTA-207296)
-
Infor EAM (OKTA-206680)
-
Looker (OKTA-206856)
-
ThinkHR (OKTA-207312)
-
Visible Equity (OKTA-206845)
Applications
Application Updates
-
Quick Base now supports the following Provisioning feature:
-
Group Push.
For configuration information, see Configuring Okta Provisioning for Quick Base.
-
- The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Atlassian Cloud: For configuration information, see Atlassian's Configure User Provisioning with Okta.
- Zoom: For configuration information, see Configuring Zoom with Okta.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Oracle Cloud Infrastructure: For configuration information, see Oracle Cloud Infrastructure Okta Configuration for Federation and Provisioning.
- PlanMyLeave: For configuration information, see PlanmyLeave User Provisioning using SCIM v2.
SAML for the following Okta Verified applications
-
Boostr (OKTA-203119)
-
Pavaso (OKTA-207100)
-
PitchBook (OKTA-206101)
-
Revivn (OKTA-206671)
-
Rockset (OKTA-207102)
SWA for the following Okta Verified application
- Zywave Home (OKTA-193830)
Weekly Updates
Fixes
General Fixes
OKTA-197013
MFA Factor Reset email template failed to save with a validation error.
OKTA-199716
If the Self Service Registration form included Preferred Language and Country Code attributes, the Registration page did not load.
OKTA-200815
The Report Client IP setting of the RADIUS app did not affect the IP displayed in the Okta Verify Push notification received by the end user.
OKTA-202390
The setting for Dropbox user deactivation type in the application's Provisioning tab was not saved.
OKTA-202836
The number of Adobe Experience Manager groups and roles displayed in Okta was limited to 2000.
OKTA-203199
CSV reports downloaded from the System Log were missing IPChain data.
OKTA-203815
Some Okta accounts were not reactivated properly after related Active Directory accounts were re-enabled.
OKTA-204327
Assigning more than 10 network zones to Agentless Desktop SSO failed with an internal server error.
OKTA-204577
Some admins without appropriate permissions were able to see the Import tab for Directory Integrations.
OKTA-204887
Downloading CSV reports for Current Assignments failed.
OKTA-205714
When a Routing Rule was used with Agentless Desktop SSO or on-premise IWA, and user match criterion was specified, the rule resulted in a failed login flow.
OKTA-208669
Litmos app provisioning failed for some clients using the Australian tenant of the app.
OKTA-209258
Evaluation of some EL expressions resulted in unintended errors.
OKTA-209844
If routing rules and IWA were both enabled, the User matches section for Routing Rules was erroneously visible.
App Integration Fixes
The following SAML apps were not working correctly and are now fixed
-
NetSuite (OKTA-208950)
-
SightPlan (OKTA-208109)
-
SightPlan (OKTA-208109)
-
Torii (OKTA-208155)
The following SWA apps were not working correctly and are now fixed
-
AccessNS (OKTA-207099)
-
Amazon JP (OKTA-206135)
-
Apple Developer (OKTA-208815)
-
BVS Performance Solutions (OKTA-201303)
-
EZ Texting (OKTA-207091)
-
IATA (OKTA-205105)
-
NCCI Field Call (OKTA-207098)
-
Shopify (OKTA-209070)
-
Site5 (OKTA-207092)
-
Tegile (OKTA-208801)
-
Virgin Pulse (OKTA-207089)
-
yodeck (OKTA-208800)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Effy Freshservice: For configuration information, see Effy's Configuring SCIM with Okta.
New Integrations
New SCIM integrations
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Abstract: For configuration information, see Configuring SCIM Provisioning for Abstract.
- Symantec Web Security Service: For configuration information, see Symantec's Integrate Okta at the SAML IdP.
- Flock: For configuration information, see the Flock Okta Connector Configuration Guide.
SAML for the following Okta Verified applications
-
AMGtime (OKTA-208211)
-
Doppler (OKTA-208076)
-
EpicCareLink (OKTA-209500)
-
Flock (OKTA-208088)
-
Ontrack Workflow (OKTA-205379)
-
Qualified.io (OKTA-204346)
-
Squadcast (OKTA-208072)
-
Stormboard SAML (OKTA-208075)
-
Web Manuals (OKTA-206111)
Mobile applications for use with Okta Mobility Management (OMM) (Android and iOS)
-
Jobvite (OKTA-205265)
-
Lattice (OKTA-203396)
-
Lattice (OKTA-203396)
SWA for the following Okta Verified applications
-
Access FileCloud (OKTA-202796)
-
Aquera (OKTA-207382)
-
AutoEntry (OKTA-201237)
-
BungalowNet (OKTA-201604)
-
Centralized Showing Service (OKTA-202381)
-
Qumulo Partner Portal (OKTA-202644)
-
Rocket Lawyer (OKTA-202052)
-
Sweetgreen (OKTA-201715)
-
SwipedOn (OKTA-203574)
-
Tempo (OKTA-200175)
-
Travelport: Rooms and More (OKTA-201895)
-
Uxpressia (OKTA-199602)
Fixes
General Fixes
OKTA-175415
Some users who enabled Yubikey as an MFA factor could not use it for sign in.
OKTA-186607
In some cases, AD-mastered users reactivated in Okta remained in the Password Reset status on the Okta Admin Console.
OKTA-196329
The toggle button for switching between the Okta Developer Console and the Classic UI was mispositioned.
OKTA-205724
Adding a SAML identity provider with the Assertion Consumer Service URL set to Organization (shared) resulted in a 400 bad request error during SP-initiated flows.
OKTA-205914
Profile changes were not synced to Active Directory or LDAP directories when they occurred at the same time that an app-mastered user was reactivated in the app.
OKTA-206305
Deleted users were sometimes incorrectly shown as Active instead of Inactive in the Okta Usage Report.
OKTA-206513
In some cases, the Okta Admin Console took a long time to load.
OKTA-206559
Sometimes IdP routing rules did not direct to the correct identity provider when the request contained an empty username query parameter.
OKTA-210021
For app sign on policies configured to gate app access when client IPs match specified network zones, the matched network zone did not appear in the Zone field of the System Log events.
App Integration Fixes
The following SAML apps were not working correctly and are now fixed
-
HostAnalytics (OKTA-208766)
-
IBM MaaS360 (OKTA-195086)
The following SWA apps were not working correctly and are now fixed
-
Appbot (OKTA-209897)
-
DHL Express (OKTA-209932)
-
IDrive (OKTA-209898)
-
Smallpdf (OKTA-209784)
-
WP Engine (OKTA-209535)
Applications
Application Updates
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Flock: For configuration information, see the Flock Okta Connector Configuration Guide.
- Expensify: For configuration information, see Expensify's Deactivating User's with Okta.
- 4me: For configuration information, see 4me's Okta configuration documentation.
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Lessonly: For configuration information, see Configuring Provisioning for Lessonly.
SAML for the following Okta Verified applications
-
Fulcrum (OKTA-210208)
-
HostAnalytics (OKTA-210227)
-
IDrive (OKTA-204347)
-
Modern Health (OKTA-210046)
-
PlainID (OKTA-210274)
SWA for the following Okta Verified applications
-
Adobe Experience Cloud (OKTA-204957)
-
Benson (OKTA-204945)
-
Bloomberg BNA (OKTA-205736)
-
Boston Properties (OKTA-204477)
-
Catalist (OKTA-204927)
-
Comerica Business Connect (OKTA-204380)
-
Florida Peninsula (OKTA-204778)
-
Genworth Mortgage Insurance (OKTA-202860)
-
Legrand Service Center (OKTA-204458)
-
NCR (OKTA-205586)
-
SoftMouse (OKTA-205528)
-
Title365 (OKTA-202822)
-
Wish (OKTA-205049)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
Figma (OKTA-203395)
January 2019
2019.01.0: Monthly Production release began deployment on January 14
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Email notifications for Factor Enrollment and Factor Reset
Admins can enable two new settings for email notifications that are sent to end users. When enabled, end users will receive an email confirmation if the end user or an admin enrolls in a new factor or resets an existing factor for their account. For more information on end user email notifications, see General Security.
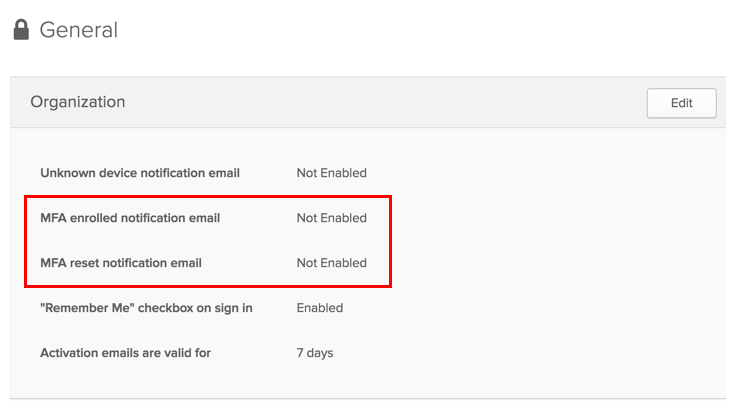
Automatically send an email to locked-out end users
You can automatically send your users an email if their account becomes locked due to too many failed sign-in attempts. You can insert a link in the email to let users unlock their account. For details, see Configure lockout settings.
Group Push enhancements
Group Push now supports the ability to link to existing groups in the following application integrations:
- Slack
- Dropbox for Business
- ServiceNow UD
You can centrally manage these apps in Okta. For details, see About Group Push.
Extended Client Access policy capability for apps
When you create App Sign on Policy rules, you can now specify platform types with greater granularity. For details, see Add Sign On policies for applications.
Additional Custom Attributes for DocuSign integration
Our DocuSign integration is enhanced by adding support several new custom attributes. Okta imports these attributes that you can then map as additional custom properties. For details, see the DocuSign Provisioning Guide.
System Log save and reuse searches
After performing a System Log search, a Save button now appears next to the query. Click Save and you are prompted to name your search. Once saved, your named search appears on the main Reports page. You can reuse your saved search, modify it, or delete it. Note that saved searches can only be seen by the user who created them. A maximum of 20 searches can be saved at any time.
LDAP Interface, query performance improvement
LDAP Interface queries will no longer return the memberOf attribute unless requested specifically, or when all operational attributes are queried using “+”. This change brings performance improvement to searches that did not require this attribute. Improvements were also made to return additional operational attributes that were part of LDAP core schema. This list includes hasSubordinates, structuralObjectClass, entryDN, subschemaSubentry, and numSubordinates. Note that numSubordinates is not calculated for users and groups containers. For details, see Set up and manage the LDAP Interface.
XFF Evaluation for Dynamic Zones and Behavior Detection
As part of Dynamic Zone and Behavior Detection evaluation, the client IP is now validated using the trusted proxies that have been configured for that org. In the admin System Log, this IP appears as the Client IP. For more information, see Dynamic Zone Evaluation.
New Windows Device Trust Registration Task, version 1.3.0
This release includes the following:
- Improved support for organizations that route internet traffic through a proxy server.
- Fixes an issue in which some Device Trust System Log events reported the Windows operating system version inaccurately on Windows desktops running Windows 8.1 or higher.
For version history, see Device Trust for Windows Desktop Registration Task Version History.
Support for Vietnamese language
Support for the Vietnamese language for the end user experience is now available to all customers. You can select the default language preference for your entire org, and your end users can select a different language preference for their own experience. For more information, see Configure the Display Language.
JIRA On-Prem Authenticator, version 3.0.7
This release includes enhanced SP-initiated SAML flow and support for spUsers and spGroups to handle JIRA only users. For version history, see JIRA Authenticator Version History.
Okta Browser Plug-in, version 5.25.0
Okta Browser Plug-in has been updated to version 5.25.0 for Chrome, Edge, Firefox, and Internet Explorer. This version contains security enhancements in addition to enhanced end user settings. For version history, see Okta Plug-in Version History. (Version history/browser ver history).
Enforce Device Trust for managed Windows computers
Okta Device Trust for Windows allows you to prevent unmanaged Windows computers from accessing enterprise services through browsers and native applications. For details, see Enforce Device Trust for managed Windows computers.
Generally Available Enhancements
EA Feature Manager
To provide more information about self-serviceable EA Features, links to help or developer documentation are now available for select features in the EA Feature Manager. For details, see Manage Early Access features.
New device notification enhancement
The setting for end users to receive a new device notification email when signing in to Okta from a new or unrecognized device is now enabled by default for all orgs. For more information about email notification settings, refer to New or Unknown Device Notification Emails.
Username passes to IdP when using identity-first IdP Discovery flow
When using an identifier-first IdP discovery flow and the user is redirected to the Identity Provider, such as SAML, Google, Microsoft, or Generic OIDC, the username value is passed on to the Identity Provider so the user does not have to type it in again.
API Token size increased for OAuth
We have increased the API token size when configuring OAuth 2.0 based authentication from 2 kB to 64 kB. For more information about OAuth, see OpenID Connect & OAuth 2.0 API.
Logos available for all Social Identity Providers
All social identity providers have the default logos shown below:

LDAP Interface, increased page size
The LDAP page size is increased from 200 to 1001, allowing LDAP clients to use a multiple page size of 1000. See Set up and manage the LDAP Interface.
Search range for group membership
The Okta LDAP Interface previously limited membership searches to the first 200 users for a group. This restriction has been removed and the LDAP Interface will iterate through all pages before returning membership response back to the client. This applies to LDAP searches that query uniquemember and ismemberOf attributes. See Set up and manage the LDAP Interface.
Temporary Passwords for Pending Users
Temporary passwords can now be created for users who are in the Pending user action state and cannot access their activation email. Creating a temporary password for a user in this way will activate the user and require them to change the password during their next successful sign-in attempt. For more information see Manage users.
IP Blacklist zone, increased Gateway IP limit
We have increased the number of Gateway IP addresses that can be used in an IP Blacklist zone from 150 to 1000. For details, see Networks.
IP Blacklist zones enhancement
Blacklist zones are no longer configurable in policies as they are evaluated before policy rules are evaluated. For more information about Network Zones, see Networks.
Early Access Features
New Features
Multi-forest support for Windows Device Trust enrollment
IWA web app version 1.12.2 supports cross-forest/cross-domain Windows device trust enrollment. Now an IWA web app running in one forest can detect and assess the trust posture of Windows desktop devices located in another trusted forest and then allow these devices to enroll in Windows Device Trust. For more about Windows Device Trust, see Enforce Okta Device Trust for managed Windows computers.
Okta collecting product feedback from end users
Admins can allow Okta to collect feedback from end users. If this feature is turned on, end users will see a prompt on their Okta dashboard requesting feedback about our products and services. You can opt out of Okta User Communication in Settings > Customization > General. For more information, see End User Communication.
Web Authentication for U2F as a Factor
Admins can enable the factor Web Authentication for U2F, where U2F keys are authenticated using the WebAuthn standard. For more information, see Web Authentication for U2F.
Fixes
General Fixes
OKTA-193300
In the admin System Log, the zone field was populated for all events that matched a sign-on policy even when the IP of the client request did not match any zones configured in the policy.
OKTA-193330
When the same user was API and App Admin, only OIDC apps were visible in the Universal Directory profile editor.
OKTA-194244
A misleading error message was displayed when the rate limit was exceeded while using the LDAP Interface to query LDAP.
OKTA-197762
Fixed inconsistent behavior with the Reset Password Link for LDAP users.
OKTA-199498
In some cases, Okta-mastered users were deactivated when their linked accounts in Active Directory were deactivated.
OKTA-200928
Logging on through Jira on-prem chiclet didn't error out properly if the end user didn't exist in the target app.
OKTA-203819H
Some orgs were unable to create the number of users that they were entitled to.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Portal (Admin) (OKTA-198299)
-
Bloomberg BNA (OKTA-202952)
-
Blue Cross Blue Shield North Carolina (OKTA-191585)
-
Coolblue (OKTA-203010)
-
Copper (OKTA-202311)
-
Dell EMC (OKTA-197625)
-
Egencia France (OKTA-202309)
-
Garveys (OKTA-202308)
-
Google AdWords (OKTA-200072)
-
Google Play Developer Console (OKTA-201061)
-
GT Nexus (OKTA-203008)
-
Monster Hiring (OKTA-202848)
-
Newton Software (OKTA-202111)
-
ONE by AOL Mobile (OKTA-201772)
-
SAP NetWeaver Application Server (OKTA-202310)
-
Tenable Support Portal (OKTA-201111)
-
The San Diego Union-Tribune (OKTA-202856)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Meta Networks Connector: For configuration information, see How to Configure SCIM 2.0 For Meta Networks.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Effy: Freshservice Provisioning: For configuration information, see Effy: Freshservice Provisioning's Configuring SCIM with Okta.
SAML for the following Okta Verified applications
-
Oracle Cloud Infrastructure (OKTA-203179)
-
PerimeterX (OKTA-202317)
-
Visitly (OKTA-202988)
-
Workpath (OKTA-202894)
SWA for the following Okta Verified applications
-
AIMA (OKTA-197142)
-
BioDigital (OKTA-197194)
-
Cisco Registered Envelope Service (OKTA-197090)
-
DeKalb Physician Portal (OKTA-197193)
-
Financial News (OKTA-198739)
-
Fresh Direct (OKTA-197128)
-
My Eaton (OKTA-200770)
-
Ocado (OKTA-197129)
-
Private Advisors (OKTA-198720)
Weekly Updates
Fixes
General Fixes
OKTA-192916
Okta Expression Language for defining a custom UserName mapping was not supported when creating a new app.
OKTA-194089
Read-only admins and Application admins saw incorrect values for Max Unassignments for applications with provisioning enabled.
OKTA-197629
In SAML App Wizard apps, the error returned when the Relay State was too long, was unclear.
OKTA-200927
Some DelAuth users who had an incomplete profile setup were not able to complete the SAML forceAuthn flow.
OKTA-201827
Group Rules did not trigger for SecondEmail if the attribute was updated via self-service.
OKTA-203326
System Log processing experienced a lag when clearing large import queues because of firing a syslog event for each user in the import flow. Now a single syslog event is fired indicating the number of users cleared from the import queue.
OKTA-205267H
For some SP-initiated SAML Requests, it incorrectly included the <Subject> element in the AuthN request.
OKTA-205324H
Okta did not allow admins to delete a group push mapping if the mapping was in error status.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
ADP Portal (Admin) (OKTA-203745)
-
Avalara Partner Portal (OKTA-204049)
-
Barrons Online (OKTA-203796)
-
LA Times (OKTA-203390)
-
Netflix (OKTA-204051)
-
Shopify (OKTA-203516)
-
TigerText (OKTA-203393)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Peakon: For configuration information, see Peakon's Set up user provisioning with Okta.
New Integrations
SAML for the following Okta Verified applications
-
Cobalt (OKTA-204332)
-
Imagineer Clienteer (OKTA-203743)
SWA for the following Okta Verified applications
-
AnyImage (OKTA-200388)
-
Crowdstrike Falcon (OKTA-199903)
-
FIS Client Portal (OKTA-193928)
Fixes
General Fixes
OKTA-152340
Pushing after removing group memberships failed for CPC apps (For example, ServiceNow, Dropbox, Slack).
OKTA-167393
In Okta Verify, Push challenges that were approved by users from the notification center had to be approved again in the Okta Verify iOS app.
OKTA-184036
Re-creating a user via JIT did not assign AD group memberships if the User Must Change Password At Next Logon option was enabled on the AD user profile after the user was deleted from Okta.
OKTA-189547
Translation to Japanese for the MFA prompt Do not challenge me on this device for the next 30 minutes was incorrect.
OKTA-192100
Multiple run-time exception errors caused the LDAP agent to fail.
OKTA-195065
Pushing groups for GSuite app failed with the error Unexpected character ( '<' (code 60)): expected a valid value.
OKTA-196483
When the default backoff setting for the AD and LDAP agents was 1 hour, it caused the agents to remain unavailable for the entire hour regardless of when the underlying issue was fixed.
OKTA-197083
Admin roles that were granted, scoped, or revoked through the Roles API did not appear in the System Log.
OKTA-197934
Provisioning for the Adobe Experience Manager SAML app failed when users had an underscore "_" in their login attribute.
OKTA-198025
The following role attributes can now be added in PagerDuty: admin, limited_user, observer, read_only_user, restricted_access, team_responder, user.
OKTA-198932
Template SAML 1.1 apps did not honor the configuration for response/assertion signing in IdP-initiated flows.
OKTA-199767
The Help link for Verifying IE Plug-in Enablement led to an invalid page.
OKTA-201029
The MFA Factor Enrolled email was sent before enrollment was completed.
OKTA-201591
The application condition for an IdP Discovery rule only allowed for 20 applications.
OKTA-201763
The Update Now button on the Sign On tab was always present even when not needed.
OKTA-201789
When searching for users by string match, if the string contained a space (for example, users with multiple last names such as "Van Horne") Okta only tried matching against the full name.
OKTA-202346
Changing profile mappings between applying only at user creation and applying at both creation and update would sometimes fail to apply the change.
OKTA-202684
For custom SAML applications, if the admin changed the Name Id format to persistent, the metadata was not updated.
OKTA-203596
An Application Sign-On policy created to allow or deny access to rich clients using modern auth and running on iPad didn't work as expected.
OKTA-204275
Domain matching in IdP Discovery rules were incorrectly case-sensitive.
OKTA-204738
An Invalid Factor error was encountered when end users used a permitted U2F factor, but also had one or more disallowed devices registered.
OKTA-205371
The Language drop-down list box on the Settings page incorrectly contained the label Beta for some languages.
OKTA-205410
Customers with Network Zone locations with China region codes CN-11, or CN-(some number) could not see the name of the region correctly, nor could they edit the Network Zone.
OKTA-205446H
For new enrollments, Voice Call MFA failed with Each code can only be used once. Please wait for a new code and try again.
OKTA-205703
The Current Assignments report was not filtering correctly when USER_LISTS_FOR_AUDITING was enabled.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
-
Bomgar (OKTA-196914)
The following SWA apps were not working correctly and are now fixed
-
ADP Screening and Selection Services (OKTA-202613)
-
Air Canada (OKTA-204326)
-
AnswerForce (OKTA-204331)
-
Backblaze (OKTA-205585)
-
BlackBerry Developers (OKTA-204370)
-
BlueJeans (OKTA-204960)
-
Booking (OKTA-204584)
-
Capital One (OKTA-204050)
-
Copper (OKTA-204325)
-
Crowdstrike Falcon (OKTA-205584)
-
CSCglobal (OKTA-204849)
-
Curalate (OKTA-206158)
-
Dell Boomi (OKTA-204328)
-
Eventbrite (OKTA-206655)
-
Evernote (OKTA-206169)
-
FACTs (OKTA-204599)
-
GatherContent (OKTA-205587)
-
Google AdWords (OKTA-206109)
-
Google Analytics (OKTA-205638)
-
GuideStar (OKTA-206168)
-
Hippo CMMS (OKTA-205390)
-
Infor EAM (OKTA-204329)
-
JobAdder (OKTA-202705)
-
LoopUp (OKTA-205012)
-
Maxemail (OKTA-206469)
-
My ADT (OKTA-206221)
-
MyCitrix (OKTA-205472)
-
NodePing (OKTA-205274)
-
Quantum Workplace (OKTA-204596)
-
Reputation.com Personal (OKTA-204737)
-
Shopify (OKTA-205380)
-
SimplyWell Member (OKTA-206545)
-
Trip Advisor (OKTA-205588)
-
USPS (OKTA-206184)
-
Virgin Mobile OneView (OKTA-206157)
-
WorkflowMAX (OKTA-206136)
-
WorkTerra (OKTA-206161)
Applications
New Integrations
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Zscaler 2.0: For configuration information, see Zscaler's SAML & SCIM Configuration Guide for Okta.
- Twic: For configuration information, see the Twic Scim Integration Guide.
- Visitly: For configuration information, see Visitly's Integrate with Okta Provisioning.
- Workteam: For configuration information, see Workteam's Configuring User Provisioning.
SAML for the following Okta Verified applications
-
CodeSignal (OKTA-204339)
-
Signagelive (OKTA-202831)
-
Simian (OKTA-204348)
-
Stampli (OKTA-203206)
-
Workspace (OKTA-205099)
SWA for the following Okta Verified applications
-
Ask the Fed (OKTA-197941)
-
Data Navigator (OKTA-197939)
-
Doctena (OKTA-198514)
-
Jack Henry & Associates Client Portal (OKTA-194264)
-
LexisNexis Bridger Insight XG (OKTA-196365)
-
Tech Data France (OKTA-192411)
2018 Production Releases
December 2018
2018.12.0: Monthly Production release began deployment on December 10
* Features may not be available in all Okta Product SKUs.
Generally Available Features
New Features
Push Notifications for the Okta RADIUS Agent
The Okta Radius Agent now includes functionality for end users to opt in to receive push notifications for MFA when enrolled with Okta Verify. For information on how to enable this setting, see Autopush for RADIUS.
Okta Windows Credential Provider agent, version 1.1.3
This release contains general bug fixes. For version history, see Okta MFA Credential Provider for Windows Version History.
Profile Editor supports linked objects
You can now add a custom attribute with a linked object data type to the Okta user profile. For details, see Add a linked object to an Okta user profile.
Add Notes to Okta-managed apps
You can now add App Notes to communicate with end users and other admins about apps. In addition to enhancing app deployment and usage, App Notes can also reduce help desk calls, provide troubleshooting assistance, and increase end user self service.
App Notes facilitate the following types of communications:
- Application notes to end users – Allows admins to present helpful information to end users, such as why they've been assigned the app, whom to contact for help, and links to additional information.
- Application notes to admins – Allows admins to share administrative details about apps with other Super, App, Read-only, and Mobile admins.
For more information, see Add notes to an app.
Super admins can choose default email notifications for admins
Super admins have the ability to select which email notifications a specific type of admin receives by default. This allows you to manage the amount of email traffic the different admin roles receive. The new defaults will override existing admin email notifications default settings (see Email Notifications for default settings). This will exclude most admins from receiving most email notifications.
Generally Available Enhancements
Admin Console update
We have updated the release number displayed in the Admin Console to the YYYY.MM.U format that we are officially adopting with the December Monthly Release. For more information, see Release notes.
Okta User Communication improvement
We have improved the Okta User Communication message in Settings > Customization to clarify the scope of end user communication.
Group Push enhancements
Group Push now supports the ability to link to existing groups in the following application integrations:
- Smartsheet
- Facebook at Work
- Org2Org
- Adobe CQ
- JIRA, JIRA On-Prem
- DocuSign
You can centrally manage these apps in Okta. For details, see Enhanced Group Push.
People page performance improvements
The A-to-Z links on the People page have been deprecated as part of efforts to improve the performance and responsiveness of the page in the Admin UI for large orgs. Screenshots:
Before:
After:
Reports enhancement
When generating reports, the earliest start date you can select is now 13 months prior to the current date. For more information about Reports, see Reports.
Early Access Features
Early Access Enhancements
FIPS-mode encryption enhancement
We have updated the Okta Verify configuration UI label for the FIPS-Mode encryption setting. For more information, see Enabling FIPS-mode encryption.
Fixes
General Fixes
OKTA-185031
Recreating group push mappings for previously existing groups would cause group memberships to not be mastered by Okta.
OKTA-187881
An LDAP directory could not be assigned to an Okta group when Sync password was enabled and Create users was disabled.
OKTA-193192
Some end users were still prompted to authenticate with MFA despite successful enrollment with Okta Verify or Duo within the same session.
OKTA-194472
The API Access Management Admin role was not returned for the user when performing a GET on api/v1/users/${userId}/roles endpoint.
OKTA-195092
When using browsers other than Internet Explorer, Agentless Desktop SSO was performing two authentication requests for each user, increasing the authentication time.
OKTA-196220
Push Groups functionality only worked for admins with Super Admin rights.
OKTA-197099
Provisioning operations for the Coupa app failed.
OKTA-197991
The MFA Usage Report listed Okta Verify with Push as an enrolled factor even if the factor was reset by an end user from their dashboard making it no longer enrolled.
OKTA-198258
There was a minor grammatical error in the app approval admin notification message.
OKTA-198556
IdP Discovery rule with a Sharepoint On-Premise specific app instance condition was not routing properly on SP-initiated login flows.
OKTA-198797
After creating an ASN dynamic zone via the API, then viewing via the UI, the default proxy type was Unchecked instead of Any proxy.
OKTA-201054H
SAML IdP flow broke down with a 404 error if the ACS URL was in {{org}}/auth/saml20/{{IdP name}} format.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
- Alibaba Cloud (Aliyun) (OKTA-198076)
- Anaplan (OKTA-198239)
- Apple Business Manager (OKTA-198241)
- Dell Boomi (OKTA-198237)
- Egencia UK (OKTA-198487)
- Linux Academy (OKTA-198691)
- PacificSource InTouch (OKTA-197597)
- Perfode (OKTA-198238)
- Rival IQ (OKTA-190557)
- Salesforce: Marketing Cloud (OKTA-197948)
- Web Manuals (OKTA-199509)
Applications
Application Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- LearnCore: For configuration information, see LearnCore's Using Okta for provisioning and SSO in LearnCore.
New Integrations
New SCIM Integration Application
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Web Manuals: For configuration information, see Web Manuals' Okta Provisioning Instructions.
SAML for the following Okta Verified applications
- Abstract (OKTA-192587)
- BambooHR (OKTA-199943)
- CloudBees (OKTA-191171)
- SAP Concur Solutions (OKTA-198484)
- Workable (OKTA-198491)
SWA for the following Okta Verified applications
- Acronis Cloud (OKTA-189384)
- Ameriflex Wealth Care Portal (OKTA-197201)
- Autodesk BIM 360 (OKTA-194354)
- buildpulse (OKTA-196661)
- Business Insider PRIME (OKTA-196625)
- Drift (OKTA-192116)
- Forum: Business Online Banking (OKTA-195330)
- HigherGear - (OKTA-196158)
- HomeDepot Vendor Portal (OKTA-190428)
- HP DaaS (OKTA-196207)
- Insperity Premier (OKTA-191066)
- Kayak (OKTA-74699)
- TrendKite (OKTA-197199)
- WealthEngine (OKTA-198240)
- Zywave Home (OKTA-193830)
Weekly Updates
Fixes
General Fixes
OKTA-155477
AD-mastered users logging into Okta with a temporary password were not asked to create a new password.
OKTA-177142
Inbound delegated authentication failed in application when the application username and Okta username were different.
OKTA-182115
As a result of multiple redirects, URLs became too long when a SAML app was used in conjunction with IWA and multifactor authentication.
OKTA-188067
When adding a user to the source user group, if the target user group did not exist, group push mappings did not display an error.
OKTA-189754
The Sign On policy did not show a warning after reaching the limit of 20 rules per policy in the UI. The limit has now been increased to 50 before showing the warning.
OKTA-190684
The OpenID Connect Client ID Token settings form was missing a link to the reference documentation about the groups claim, also the the Sign On mode tab was missing a link to the profile mappings.
OKTA-191321
In some cases, the LDAP search filter did not allow using "<" and ">" simultaneously.
OKTA-191398
The System Log did not include hostname in the Debug Context for Windows events.
OKTA-195890
IdP Discovery routing rules with an application condition and without a user identifier condition were not routing to social IdPs.
OKTA-195916
Resetting the password for one account while a different user was signed into another account in the same browser generated a successful System Log event for the wrong account, and the UI showed a failure message although password reset was successful.
OKTA-196579
The WebEx app did not update sessionType attributes for users.
OKTA-199133
The System Log did not report enrollment failures that occurred when the relevant Device Trust setting was not enabled in the Okta Admin Console.
OKTA-200176
The Application Usage report returned a server error instead of a bad request message when an invalid date was entered to generate the report.
App Integration Fixes
The following SAML app was not working correctly and is now fixed
- IntraLinks (OKTA-198125)
The following SWA apps were not working correctly and are now fixed
- Crunchbase (OKTA-198994)
- Dashlane Business (OKTA-199046)
- Shopify (OKTA-200163)
- Thycotic Force (OKTA-198995)
Applications
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- OfficeSpace Software: For configuration information, see the OfficeSpace Software Okta - SCIM configuration guide.
SAML for the following Okta Verified applications
- Expiration Reminder (OKTA-200470)
- RecruitBot (OKTA-196618)
SWA for the following Okta Verified applications
- Haivision Support (OKTA-191530)
- ONE by AOL: Video (OKTA-196063)
Fixes
General Fixes
OKTA-71278
The Identity Providers list was missing the Action column header and had alignment issues.
OKTA-154988
Missing fields were not highlighted in the error message displayed when adding a new SAML identity provider.
OKTA-189636
Username changes in Okta for AD-Mastered users were not correctly pushed to the JIRA On-Prem app.
OKTA-190763
Users who had been locked out and then deactivated were still listed as locked out on the Reset Password and Unlock People pages, as well as on dashboard notifications.
OKTA-191917
When the Agentless Desktop SSO flow failed, the FromURI parameter was missing, causing a launched app not to load.
OKTA-193120
Incremental imports did not properly terminate users due to time zone differences.
OKTA-194696
Group membership updates that failed due to the Org2Org rate limit were not retried.
OKTA-197806
For orgs with the EA feature, Advanced Schema for Box enabled, assigning a group to Box sometimes failed.
OKTA-201633
The users/${userId}/factors/catalog endpoint returned email as a supported factor type although Email Authentication had not been enabled for the org in their MFA setting.
OKTA-201799
When searching for a group containing a space character, the text box selection to continue typing was lost and required users to click on the text box again to type next character.
App Integration Fixes
The following SWA apps were not working correctly and are now fixed
-
Aha (OKTA-200921)
-
Amazon DE (OKTA-200178)
-
CarGurus (OKTA-201462)
-
Cintellate by SAI Global (OKTA-201461)
-
GFI Mail Essential Online (OKTA-199274)
-
GTA Travel (OKTA-200126)
-
Gusto (OKTA-199737)
-
Handshake (OKTA-201464)
-
HP Connected (OKTA-200425)
-
MyViverae by Viverae (OKTA-200739)
-
Papertrail (OKTA-199505)
-
Sauce Labs (OKTA-199066)
-
SeamlessWeb (OKTA-201041)
-
The San Diego Union-Tribune (OKTA-201415)
Applications
Application Updates
The following partner-built provisioning integration apps are now Generally Available in the OIN as partner-built:
- Retool: For configuration information, see Retool's Okta Specific Guide.
- Wrike: For configuration information, see Wrike & Okta, User Provisioning.
- Drift: For configuration information, see Drift's Okta SCIM Configuration Guide.
- OfficeSpace Software: For configuration information, see the OfficeSpace SoftwareOkta - SCIM configuration guide.
New Integrations
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- 4me: For configuration information, see 4me's OKTA configuration instructions.
- Tableau Online: For configuration information, see Tableau Online's Automate User Management through an External Identity Provider.
- CyberArk SCIM Server: For configuration information, see Configuring Provisioning for CyberArk SCIM.
- Workpath: For configuration information, see Workpath's Okta Configuration Guide.
SAML for the following Okta Verified applications
-
Abacus (OKTA-201459)
-
Envoy Global (OKTA-201924)
-
Firstbird (OKTA-202087)
-
Five9 Plus Adapter for Salesforce (OKTA-198492)
-
Imagineer WebVision (OKTA-202327)
-
International Relocation Center (OKTA-200829)
-
iObeya (OKTA-198510)
-
SevenRooms (OKTA-199302)
-
Splash (OKTA-201453)
-
Wootric (OKTA-198958)
-
Zoom SAML (OKTA-200668)
SWA for the following Okta Verified applications
-
Anexia Engine (OKTA-197187)
-
Bloomberg (OKTA-198566)
-
CAPPS Enterprise Portal (OKTA-190371)
-
FHLBank of Dallas (OKTA-189796)
-
Information Management Network (OKTA-199265)
-
Morningstar UK (OKTA-199264)
-
NET-ENTERPRISES.FR (OKTA-190878)
-
PostNL Digital Postage Stamp (OKTA-198257)
-
Quip (OKTA-191534)
-
SonicWall Capture Security Center (OKTA-198693)
-
TxDMV webDEALER (OKTA-192030)
-
Vantiv IQ (OKTA-193087)
Mobile application for use with Okta Mobility Management (OMM) (Android and iOS)
-
LogicMonitor (OKTA-193723)
When you delete a group, the Group Push mappings associated with the group are disabled and the mapping status will show as an error. You can then either deactivate or delete the mappings. For information about Group Push, see Using Group Push.
When you create a rule for an active Identity Provider, you can choose whether to activate the rule and apply it immediately, or else create it in an inactive state. Conversely, when you create a rule for an inactive Identity Provider, the rule cannot be activated and is automatically created in an inactive state. ![]() Screenshot:
Screenshot:
When you deactivate an Identity Provider with active routing rules, Okta displays a warning that the rules will be deactivated. ![]() Screenshot:
Screenshot:
For more information about Identity Providers, see Identity Providers.
When configuring network zones, admins can now set Kosovo as a country using country code XK in order to ensure that IP addresses from Kosovo are more accurately defined. For more information about network zones, see Networks.
If an app-to-app mapping includes an invalid expression, profile sync job creates a new System Log event to capture the failure, skips evaluating the expression, and processes the rest of the mapping. ![]() Screenshot:
Screenshot:
The BambooHR integration now supports OpenID Connect (OIDC). For configuration information, see the BambooHR Provisioning Guide.
The Okta browser plugin for Chrome is updated to version 5.24.1. This version includes the following bug fix:
- App icons did not load in Okta plugin for Google Chrome when the CDN was disabled.
For version history, see Okta Browser Plugin Version History.
The Okta browser plugin for Chrome and Firefox browsers is updated to version 5.24.0. This version includes an update to the end user plugin settings (available in Early Access) and back-end product enhancements. For version history, see Okta Browser Plugin Version History.
Job Title has been added to the list of RingCentral custom attributes that can be added via Schema Discovery. For more information about RingCentral provisioning, see the following provisioning guides:
For SharePoint (On-Premises) app, Expression Language evaluation for Application Attributes now supports sending any OKTA user attributes, including custom OKTA user attributes. For more information, see Adding the SharePoint (On-Premises) App in Okta.
During standard imports, users are sometimes mistakenly imported from 3rd-party apps. The Clear Unconfirmed Users button allows admins to clear all unconfirmed users within an import queue. See Import users.
When generating reports, the earliest start date you can select is now 13 months prior to the current date. For details about Okta reports, see Reports.
Okta has made a new chiclet, Microsoft Power BI, available for the Microsoft Office 365 app. You can enable it on the General tab of your org's Microsoft Office 365 app instance. For details, see Enable a Microsoft Office 365 Chiclet.
Region codes for China have been updated due to a recent change in the universal ISO standard. To prevent region codes from displaying incorrectly, update your network zone region codes accordingly. For more information, see Network Zones.
Unlinking between an Okta group and the pushed group in downstream application cannot be reversed. A notification has been added to warn the admins that unlinking a group in this way cannot be undone. ![]() Screenshot
Screenshot
User Locked Out emails are sent to admins in batches and contain a list of all users who are locked out. The email shows users locked out since the previous email was sent. Previously each admin received one email for each locked out user in real time.
Administration for multifactor authentication is streamlined with a new single page design that improves navigation and usability for enabling and configuring authentication factors. For more information, see Multifactor Authentication.
We’ve added more detail to the user state labels on the People page. ![]() Screenshot:
Screenshot:
And now provide the action required for users in a pending state on the User Profile page. ![]() Screenshot:
Screenshot:
This feature enables an administrator to configure a workflow for a self-service app that requires approval. It enables an end user to request access to an app and an approver to approve or deny the request. For more information, see Access Request Workflow > Configure the App Approval Workflow.
The policy for randomly generated passwords for Password Sync can now be defined by Okta, on a per-app basis.
If Okta’s randomly generated password for Password Sync does not meet the password requirements of a specific app, Okta can, upon request, change that app’s password policy. This functionality is now available for all orgs.
Okta now deletes all users' sessions after a successful password reset as part of the forgot password flow.
Admins can configure activation emails with lifetimes of 1, 2, or 4 hours. For more information on the General security options, see General Security. ![]() Screenshot
Screenshot
There were no new features in this release. For new apps and bug fixes delivered in this release, select the appropriate tab.
There were no new features in this release. For new apps and bug fixes delivered in this release, select the appropriate tab.
Only a Super Admin can view the self-service menu (Applications > Self Service) for an organization. In the past, both org admins and super admins could access this menu. There is no change to the options on the menu. For more information on roles and permissions, see Administrators.
In an Identity Provider Discovery flow, the username entered as the identifier in the first screen is passed to other Okta orgs. End users do not need to re-enter a username when signing in to any other Okta org to which they are redirected. For more information, see Identity Provider Discovery.
Support for the Norwegian (Bokmål) language for the end user experience is now available to all customers in Beta format. You can select the default language preference for your entire org, and your end users can select a different language preference for their own experience. For more information, see Configure the Display Language.
Super org admins can now download a CSV file containing a list of all admins and their permissions, using the Download CSV button on the Administrator page. For details, see Administrators. ![]() Screenshot
Screenshot
Requests to the /token and /authorize endpoints will now accept JWTs signed with a private key. For more information, see the OIDC documentation for the token endpoint and the authorize endpoint.
These email notification types are off by default for admins in new orgs:
- User Deprovision
- App user import status
- User lockouts
Each admin can individually opt in at Administrator > Settings > Account. Admins in existing orgs will be unaffected. For details, see Account Settings. This feature is available for new orgs only.
When enabled, end users will receive a new device notification email when signing in to Okta from a new or unrecognized device. This feature is now generally available to all orgs. For more information about email notifications, refer to the New or Unknown Device Notification Emails section in General Security.
Okta is consolidating where app usernames are configured. Instead of being able to change the app username in the Profile Editor and the app’s Sign On tab, you will be able to edit the Okta to App username mappings only on the app’s Sign On tab.
Note: The following apps will not be changing their behavior: Active Directory, LDAP and SAML Identify Provider.
For the Okta to App flow, you can no longer override username mappings in the Profile Editor.
Username mappings on the Sign On tab
The userName mapping in the app's Sign On tab will be the source of truth for the Okta to App flow. Updating the userName mapping on Create only or Create and Update will also be controlled from the app's Sign On tab. ![]() Screenshot:
Screenshot:
Super Admins and Org Admins can send all admin emails as BCC so that recipients' email addresses are hidden. For more information, see Global notifications options.![]() Screenshot
Screenshot
You can now disable the default Okta loading animation (interstitial page) that appears when users are redirected to custom applications. End users are shown a blank interstitial page, instead. This allows you to present a more branded end user experience. For more information, see Customizing the Interstitial page>. ![]() Screenshot:
Screenshot:
This feature streamlines the App Self-Service UI with the Access Request Workflow UI and allows admins to write a note to the end user about the app instance. See Access Request Workflow and Self Service Registration for more details. ![]() Screenshot
Screenshot
You can now assign Apps to App Admins at the instance level. This allows for more granular access control. For details, see Administrators.
We have added a new, customizable email template that alerts your end users when someone connects to their Okta account from a new device. This feature protects against silent access to an end user's account. For more about Okta email templates, see Email and SMS Options. This feature is Generally Available for new orgs only.
The Multifactor Factor Types UI has been updated to include U2F activation and enrollment for end users. For more information about U2F enrollment, refer to the Factor Types Configuration section in Multifactor Authentication.
You can integrate Adaptive MFA with your VMware Horizon View , Pulse Connect Secure, BeyondTrust PowerBroker Password Safe, and Check Point clients. Follow these links for more information and complete setup instructions.
The Self Service Registration (SSR) form now supports enum data types of string, numbers, and integers. For more information, see Okta Self-Service Registration.
Admins now receive an email listing all users deactivated during 30 minute periods instead of individual emails for each deactivation.
Okta has made a new chiclet, Microsoft Forms, available for the Microsoft Office 365 app. You can enable it on the General tab of your org's Microsoft Office 365 app instance. For details, see Enable a Microsoft Office 365 Chiclet. ![]() Screenshot
Screenshot
This version contains security enhancements. For version history information, see Okta RADIUS Server Agent Version History.
This version contains security enhancements. For version history information, see Okta On-Prem MFA Agent Version History.
The System Log now reports when requests are denied due to a blacklisted network zone. ![]() Screenshot:
Screenshot:
For more details about the System Log, see Reports.
The Factor Type for MFA events is moved from the Actor's details to the Event's details in the System Log. ![]() Screenshot:
Screenshot:
For more details about the System Log, see Reports.
Okta has added the following nine supported languages for Email and SMS Customization: Czech, Greek, Hungarian, Indonesian, Malaysian, Polish, Romanian, Turkish, and Ukrainian. See Supported display languages.
BambooHR now retrieves additional attributes such as department and division for pre-start users.
For more information about BambooHR provisioning, see the BambooHR Provisioning Guide.
An enhancement to the device fingerprint feature has been made so that end users may receive a new device notification email when signing in via an embedded browser. Sign in via embedded browsers can take place in applications such as Microsoft Outlook on Mac OS or Windows and mobile apps. For more information about email notifications see New or Unknown Device Notification Emails.
Admins can now recover the default values of mappings that had been overridden during individual app assignments. This feature also clearly displays default EL expressions, and simplifies overrides with Override and Reset buttons. For more information, see Attribute Mapping Overrides.
When enabled, Okta imports Google custom schemas which you can then map as additional custom properties. Note: In order to have permission to pull custom schema information from Google, Okta requires an additional OAuth scope. This requires you to reauthenticate your app instance in order use this functionality.
For more information about Google schema discovery, see the G Suite Provisioning Guide.
When you create a custom attribute, you can enter a list of enum values. For example, you can create a Shirt size attribute with a list of values including: small, medium, large. For details, see Create Custom Attributes.
This feature allows you to create instances of the Salesforce.com app that can integrate with either a Salesforce Customer Portal or a Salesforce Customer Community. For more details, see the Salesforce Provisioning Guide.
You can configure a custom domain so that email Okta sends to your end users appears to come from an address that you specify instead of the default Okta sender noreply@okta.com. This allows you to present a more branded experience to your end users. For details, see Configure a Custom Email Domain. ![]() Screenshot
Screenshot
Okta Mobile supports fingerprint authentication on Android devices and Touch ID/Face ID authentication on iOS devices. For details, see Lock/Unlock the Okta Mobile App. ![]() Example Screenshot:
Example Screenshot:
Voice Call Factor authentication is now available as an MFA factor. With this feature enabled, end users will receive a phone call that audibly provides a 5 digit verification code to be entered upon login. This factor can be enabled either on its own or with other factors enabled. For more information about voice call as a factor, see Multifactor Authentication. ![]() Screenshot:
Screenshot:
The Group member page (Directory > Groups) has the following enhancements:
- The Manage People button is now the Add Members button.
- The Search bar is relocated to the right side of the screen.
- The managed column is now the Added By column to indicate who added the new group member.
Additionally, when searching for a user name, if the number of search results exceeds the page limit, you are prompted to refine your search.
Super Admins have the ability to enable select Early Access (EA) features to which their organization is entitled. There is no need to contact Support to request access to these new features. EA features that require additional configuration will still require assistance from Support to be enabled. For details, see Manage Early Access features.
You can also track availability of EA features on the Product Roadmap available in the Okta Help Center.
In addition to filtering by application, Okta's Application Usage report has an option to include report data from All applications. If you select this option, the data is only available to download as a CSV file (in unaggregated format).
For more details, see Reports. ![]() Screenshot
Screenshot
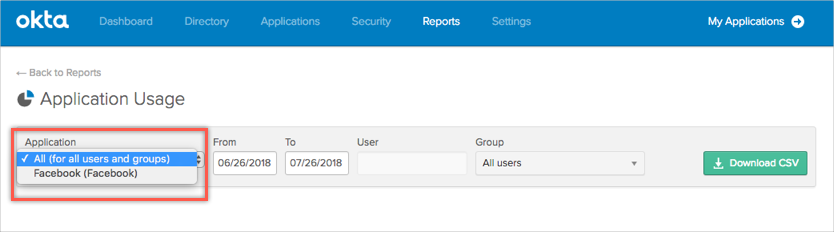
Group Push now supports the ability to link to existing groups in Zendesk. You can centrally manage these apps in Okta. While this option is currently only available for certain apps, Okta will periodically add this functionality to more and more provisioning-enabled apps. This feature is now GA. For details, see Using Group Push.
The System Log now reports when a user has been imported, updated, and deleted through real time sync. ![]() Screenshot
Screenshot
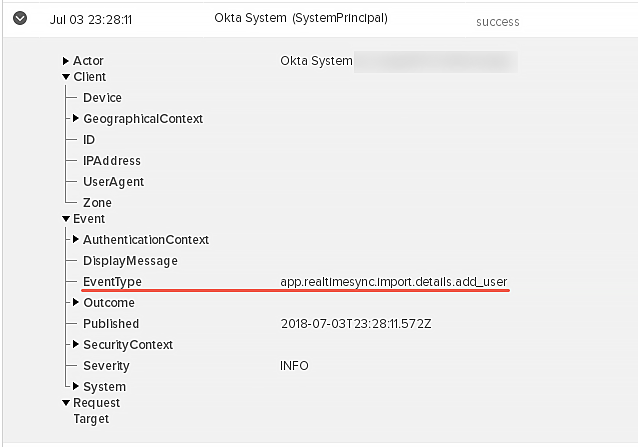
The OIN Manager is an Okta portal through which independent software vendor (ISV) partners can submit SSO and provisioning apps to Okta. Once approved, these integrations are included into the Okta Integration Network (OIN).
You can integrate Adaptive MFA with your Sophos VPN clients. For more information, see Configure Sophos UTM to Interoperate with Okta via RADIUS.
We have increased the default number of group membership rules allowed per org from 100 to 2000. For details about Group rules, see About Groups.
If your server policy is set up to deny access to external IP addresses and websites, you must configure a whitelist to enable access as required. The IP whitelist information can be obtained programmatically and can be downloaded in JSON format here: IP whitelist file. To view the current IP ranges, download the .json file. To maintain a history, save successive versions of the file. For more information about Okta IP whitelisting, see Configuring Firewall Whitelisting.
Okta continues to optimize performance in generating reports with a focus on data reliability, quality and self service of report data delivery. To achieve this, certain reports are now delivered asynchronously as a CSV download. For more information about reports, see Reports. ![]() Screenshot:
Screenshot:
This release includes the following changes:
- The installer will not continue if it cannot use a TLS 1.2 connection to connect to the Okta service. For Windows 2008 R2 TLS 1.2 is disabled by default and needs to be enabled through the registry. For details, see TLS 1.2 registry edits.
- Increased the minimum .NET version supported to 4.5.2. If the installer does not detect .NET 4.5.2 or higher, it will be installed.
For version history, see Active Directory Agent Version History.
U2F is available as an MFA factor. See Factor Types for more information about different MFA types, including U2F. ![]() Screenshot:
Screenshot:
The Okta browser plugin for the Chrome, Firefox, Internet Explorer, and Safari browsers was updated to version 5.19.0 in release 2018.24. This version provides support for the Okta Account Chooser. For version history, see Browser Plugin Version History.
The Okta System Log and Events APIs filter out any password information that customers might have included in query parameters. This filter is part of our on-going optimizations to scrub sensitive data from logs. Okta always recommends that customers use POST requests, and never use sensitive data in HTTP GET parameters. ![]() Screenshot:
Screenshot:
Setting multiple enum value attributes on the end user Profile Settings page is now supported. ![]() Screenshot:
Screenshot:
New Salesforce app instances now come with a reduced set of base attributes:
- username
- firstName
- lastName
- profile
Attributes that used to be in the base schema are moved to custom:
- title
- communityNickname
- mobilePhone
- phone
- street
- city
- state
- postalCode
- employeeNumber
- companyName
- division
- department
- managerId
- role
- salesforceGroups
- featureLicenses
- publicGroups
This change allows admins more fine-grained control over which attributes Okta will sync in the downstream SFDC instance.
For information about Salesforce provisioning, see Okta's Salesforce Provisioning Guide.
Okta supports custom expressions when mapping attributes from Okta to Confluence. For more information about Confluence provisioning, see the Confluence Provisioning Guide.
- Support for custom properties to push and import to/from Google.
- Support for multi-value fields (arrays) for Google Schema Discovery.
For more information about Google schema discovery, see the G Suite Provisioning Guide.
Note: Boolean properties for multi-value fields are not supported by Okta Universal Directory. They are ignored during schema import and are not visible in the Profile Editor.
A confirmation notification is now displayed after resetting or enrolling in a factor. ![]() Screenshot:
Screenshot:
You can integrate Adaptive MFA with your F5 BigIP APM Edge clients. For complete installation and usage information, see Configure the F5 BigIP APM to Interoperate with Okta via RADIUS.
New message notifications appear when an Authorization Server is activated, deactivated, or deleted. ![]() Screenshot:
Screenshot:
To address a security vulnerability, end users' primary email address is now populated automatically in the Request Access to Apps dialog box and the Your email field is no longer editable. The dialog box displays when end users click Request an app in the footer of their Okta org. ![]() Screenshot:
Screenshot:
All admins are being unsubscribed from receiving email notifications for Known Issues and System Outages which is now renamed to Trust incidents and updates. To receive these notifications, go to Settings > Account > Email Notifications. For details, see Email Notifications.
In Settings > Account, under Email Notifications, the Known Issues and System Outages option is renamed to Trust incidents and updates. All new Super admins will be subscribed by default. For details, see Email Notifications.
Some admins can select whether they want to receive emails when a user is deactivated. The admin roles that have this option are: Super Admin, Org Admin, App Admin and Mobile Admin. For details, see Email Notifications.
The following events are added to System Log:
- The feature for supporting multiple network zones is disabled for an org (IWA SSO only).
 Screenshot:
Screenshot:
- When synchronizing users with a directory, users will be skipped if they match default filter rules.
 Screenshot:
Screenshot:
The Okta Downloads page contains a new section, MFA Plugins and Agents that replaces the Okta On-Prem MFA Agents section. ![]() Screenshot
Screenshot
By default, Okta requires user names to be formatted as email addresses in Okta Universal Directory. Using the Format Restriction control in the Profile Editor, Administrators can remove the email format constraint from the Username attribute in Okta UD or replace it with a specific set of characters that are allowed. This provides additional control over the format for Okta usernames for all users in an Okta org. For more information see Manage profiles.
End users can now switch between multiple Okta accounts easily through the Okta browser plugin. This feature prompts signed-in end users to trust or reject subsequent Okta accounts the first time they access those accounts allowing them full control to choose seamlessly between accounts. For details, see Switch between multiple Okta accounts using the plugin. ![]() Screenshot
Screenshot
If there's a problem with the Okta browser plugin, an error message with a Refresh Plugin button now displays allowing end users to refresh the plugin cache. For more, see About the Okta Browser Plugin. ![]() Screenshot
Screenshot
The list of Okta-provided email templates is reorganized by template type. This makes it easier for admins to find and evaluate Okta-provided email templates in Settings > Email & SMS. For more information about Okta email templates, see Email and SMS. ![]() Screenshot:
Screenshot:
Error message text has been modified when assigning non-email formatted values for username attribute.
The System Log contains an entry when a user cannot be unlocked automatically by the nightly batch job due to a read-only event. ![]() Screenshot:
Screenshot:
Authentication whitelisting and blacklisting (explicitly permitting or denying access) based on network zones is now Generally Available (GA). Network zones are sets of IP address ranges. You can use this feature in policies, application sign on rules, and VPN notifications. This expands the use of Gateway IP Addresses. This feature is now GA for all orgs. For more information, see Network. ![]() Screenshot
Screenshot
Custom email templates allow you to send custom Okta-generated email messages to end users in multiple languages. See Customize an email template.
![]() Screenshot
Screenshot
This version disables CDN during install and contains bug fixes. For history, see Okta RADIUS Server Agent Version History.
This version disables CDN during install. For history, see On-Prem MFA Agent Version History.
Okta Verify Auto-Push makes Multifactor Authentication (MFA) even easier. Now, when end users land on the MFA challenge page (with Okta Verify with Push enabled), the challenge is sent automatically with no need to click Send Push. To set up this feature, end users select Send Push Automatically on the authentication screen. For more information, see Okta Verify with Push Authentication. ![]() Screenshot:
Screenshot:
Support for a cloud access security broker (CASB) is available for all SAML apps. For more information, see the CASB Configuration Guide.
When you customize an Okta-generated email template through the Add Translation dialog box, the text in the body of the template updates automatically into the language you select in the Language list. The Generally Available version of this feature includes updated labels and other minor UI improvements. See Supported display languages. ![]() Screenshot
Screenshot
The Litmos integration is updated to support SHA2 cryptographic hash algorithm which utilizes the new Litmos SAML endpoint splogin.
If you are currently using the Litmos SAML integration, Okta highly recommends that you review the steps outlined in the migration section of the Litmos Configuration Guide and switch to SHA2 at your earliest convenience. ![]() Screenshot:
Screenshot:
You can extend Adaptive MFA to your Fortinet appliance. For complete installation and usage information, see Configure the Fortinet Appliance to Interoperate with Okta via RADIUS.
New device notification email events now appear in the System Log. ![]() Screenshot:
Screenshot:
We've improved the user experience for U2F-compliant factor enrollment by making the following changes:
- U2F instructions are updated to remove references to specific browsers such as Chrome and Firefox
- Error messages now include more descriptive text
For more information, see MFA Factor Types. ![]() Screenshot:
Screenshot:
There were no new Production features in this release.
Added the following enhancements to support Rate Limit notifications:
-
Notification banners within Okta for Super administrators when the Rate Limit warning and violation thresholds have been reached within the last 24 hours.
 Screenshot
Screenshot -
Automatic email notifications to Super administrators when the Rate Limit warning and violation thresholds have been reached within the last 24 hours.
 Screenshot
Screenshot -
An Email Notifications setting available in Settings > Account for the Super administrator to turn the email notification on or off. This setting is turned on by default.
 Screenshot
Screenshot -
Syslog entries that track discrete rate limit events for warnings and violations, and that can be queried independently or jointly. This provides you with a full picture of organizational as well as individual client trends.
For example, the following query shows both warnings and violations:
eventType eq "system.org.rate_limit.warning" OR eventType eq "system.org.rate_limit.violation"Both the notification banner and the email notification contain a link to the query above.
 Screenshot
Screenshot
For more information, refer to Rate Limiting at Okta.
The Convert Assignments screen is populated only when there are assignments to convert. When there are no assignments to convert it presents a message. ![]() Screenshot.
Screenshot.
The Downloads page includes the following changes:
- The agent status is highlighted at the top of the page, indicating whether or not agents are up-to-date.
 Screenshot
Screenshot - Agent status information appears after the first agent of that type is configured.
- For the AD, SSO IWA, On-Prem MFA, Provisioning, and LDAP agents, there is now a status message indicating whether the agent is up-to-date or a new version is available.
- The Connected Agents table displays the host name, the version of the agent that is currently running, whether the agent is TLS 1.2 compliant.
 Screenshots
Screenshots - The AD Password Sync and RADIUS agents information includes a link to the System Log to view the agent version, if applicable.
- The Admin Downloads section moved to the top of the page and similar agents are grouped (for example, all AD agents are together).
- A link to a CSV file containing this information is added to the right-hand sidebar.
 Screenshot
Screenshot
ID tokens can now be retrieved using a Refresh Token.
If Okta fails to process an IWA token, you can now redirect end users to a custom error page. This option is useful if you embed Okta into your solution and want to control end-to-end branding to enhance end user experience. For more information, see Login Error Page.
Note: This feature is now Generally Available for all orgs.
You can deactivate Workday mastered users on their last day worked, even if the period of time between that day and the termination exceeds a specified Pre-Start interval. See the Workday Provisioning Guide for more information.
The Workday integration now connects to the latest Human Resources API (v29) and uses the Maintain Contact Information Workday API for email and telephone write back, a more secure web service that some customers prefer. Additionally Okta has improved the pre-start interval functionality by only processing new users being created and ignoring updates within the pre-start interval. There are also some performance enhancements when performing an import from Workday. See the Workday Configuration Guide for details.
This feature is Generally Available for new orgs only.
You can configure Advanced API Access for Office 365 instances by using the admin consent option on the Sign On tab.
Admins needs to leave this checked to complete OAuth authentication flow with O365, which is required for signing into chiclets such as Yammer, Teams, and CRM. For more information, see Admin Consent for Advanced API Access. ![]() Screenshot:
Screenshot:
Okta has updated its Workday integration: Workday Real Time Sync (RTS) can now run concurrently with regular imports. Refer to Workday Provisioning Guide to learn more about Workday RTS.
If the org admin revokes the Device Trust certificate through the admin console, the Sys Log for Device Trust Certificate Revocation now identifies the admin. As before, if the certificate is implicitly revoked due to user deactivation, the Actor continues to be shown as Okta System. For details, see Revoke and remove Device Trust certificates.
![]() Screenshot:
Screenshot:
The Citrix NetScaler Gateway now integrates with Okta via RADIUS, in addition to SAML and OAuth. For detailed information, see the Citrix Netscaler Gateway Radius Configuration Guide.
Password Reset is available for users who are not yet active. This is to enable users who may have lost their original activation email to request a password reset.
Email addresses enclosed in double quotation marks are supported for Okta logins.
The Account tab on the Customization page is renamed General. For details about options on this tab, see Customization. ![]() Screenshot:
Screenshot:
Direct links to the documentation for the Okta Windows Credential Provider and the Active Directory Federation Services (ADFS) Plugin are available in the sidebar. ![]() Screenshots:
Screenshots:
This Generally Available agent update contains the following fixes:
- Locate the correct user when searching for a SamAccountName that is duplicated in a forest
- Include the User-Agent in the header of the request
For history, see AD Password Sync Agent Version History.
This release fixes an issue where the screen appeared blank. For version history see Browser Plugin Version History.
The Forgotten Password Text Message screen offers an option to resend the code to enter for SMS or call again for Voice call. For more information about password reset functionality, see End User Password Reset.
![]() Screenshot:
Screenshot:
The PagerDuty app now implements v2 of the PagerDuty API. PagerDuty API v1 is going to be deprecated on April 24, 2018. The change of API should be transparent to customers. For more information, see https://v2.developer.pagerduty.com/. For more information about PagerDuty provisioning, see the PagerDuty Provisioning Guide.
This version provides internal fixes to the installer, including a fix which allows the installer to work behind a firewall.
For history, see On Premises Provisioning Agent and SDK Version History.
You can configure the Okta browser plugin to behave on your custom end user portal exactly as it behaves in the Okta end user dashboard. For details, see Configure your custom end user portals to leverage the Okta browser plugin.
If Okta fails to process an IWA token, you can now redirect end users to a custom error page. This option is useful if you embed Okta into your solution and want to control end-to-end branding to enhance end user experience. For more information, see Login Error Page.
Note: This feature is Generally Available for new orgs.
You can now set the SkipUrls registry key to prevent the Okta Internet Explorer browser plugin from inspecting the pages of specified URLs for the presence of login and change password forms. This allows pages to load faster. For details, see Exempt specified URLs from login form inspection.
When both first and last name attributes are empty, the login name is displayed in the following UI pages:
- User Picker in App Approver picker
- New Group
- Convert individual user back to group in app
- Exclusive user list in group rule
- App User assignment
- API token review
- Yubikey UI
- Spotlight search
First and last names can be null if they are removed in the Profile Editor or changed with the Users API.
This Generally Available release provides the following:
- To improve the security of IWA integrations, we now default to the TLS 1.2 security protocol in orgs running .NET Framework 4.5 or later. Orgs running earlier versions of the .NET Framework continue to use TLS 1.0.
- Fixed an issue that caused an error when accessing the Box desktop app with SSO.
- Internal fixes to the installer.
For history, see IWA Agent Version History.
This Generally Available release provides internal fixes to the installer. For history, see LDAP Agent Version History.
This release provides performance and security enhancements. For version history, see Browser Plugin Version History.
Email notifications sent to users after the detection of a new device or browser at login have improved messaging and now specify Unknown browser and Unknown OS instead of just Unknown.
Okta and Palo Alto Networks interoperate through either RADIUS or SAML 2.0. For each Palo Alto gateway, you can assign one or more authentication providers. Each authentication profile maps to an authentication server, which can be RADIUS, TACAS+, LDAP, etc. Using RADIUS, Okta’s agent translates RADIUS authentication requests from the VPN into Okta API calls. For more information, see Configure the Palo Alto Networks VPN to Interoperate with Okta via RADIUS.
The Client ID field is now populated in the Client Section of the System Log. ![]() Screenshot:
Screenshot:
System Log entries are now added for the Hipchat and Confluence apps. For details, see the Hipchat and Confluence sections in Provisioning Integration Error Events.
When setting up an Microsoft Office 365 app, the checkbox for Admin Consent on SSO tab is now unchecked by default. For more information on Admin Consent, see Admin Consent for Advanced API Access.
Updated app icons for Okta Verify are available for iPad users. ![]() Screenshot:
Screenshot:
The Okta ADFS (Active Directory Federaton Services) Plugin version 1.4.0 is available. This version supports load balanced ADFS servers.
The Learn More link in the Attributes Statements (optional) section of the SAML Settings page points to improved information. ![]() Screenshot:
Screenshot:
In environments where internet traffic is required to go through a proxy, the sign-in flow for the AD agent installer uses the proxy settings specified within the installer. If no proxy settings are specified, the machine defaults are used. Previously,admins had to open up a hole in their data center firewall during installation.
For more information about the AD agent see Okta Active Directory Agent.
An in-product link to the Provisioning Guide for Cornerstone app is added, replacing in-product help text.
This release provides the following:
To improve the security of IWA integrations, we now default to the TLS1.2 security protocol in orgs running .NET Framework 4.5 or later. Orgs running earlier versions of the .NET Framework continue to use TLS1.
For history, see SSO IWA Web App version history.
This new version supports TLS 1.2.
For history, see On-Prem MFA Agent Version History.
Labels and messages in the Customize an email template feature are updated to improve usability.
The Microsoft Office 365 (O365) admin consent flow is now optional and is selected by default on the Sign On tab for the O365 app. Admins needs to leave this checked to complete OAuth authentication flow with O365, which is required for signing into chiclets such as Yammer, Teams, and CRM. For more information, see Admin Consent for Advanced API Access. ![]() Screenshot:
Screenshot:
The default scopes included with OAuth Custom Authorization Servers have improved display names and descriptions.
This new version supports TLS 1.2. For history, see Okta RADIUS Server Agent Version History.
When configuring scopes for Identity Providers, whenever a comma, tab, or return is typed, scopes are tokenized. For example, typing "Profile, Email" in the Scopes field in the screenshot below, will result in two scopes, Profile and Email.
For more information, see User Consent for OAuth 2.0 and OpenID Connect Flows.
Okta has defined 31 default base attributes for all users in an org. These base attributes are generally fixed and cannot be modified or removed. There are now two exceptions: First Name and Last Name. These two attributes can now be marked as required or optional for Okta-mastered users only. For details, see Profile Editor.
An enhancement was made for our platform customers using the auto-push feature for Okta Verify. As a result, all product users will need to re-affirm their Okta Verify Auto-Push preference (check the Send Push Automatically checkbox) if it was checked previously. Following this, Okta Verify with Auto-Push will behave as it did originally. For more information about this new parameter, see https://developer.okta.com/docs/api/resources/authn.html#request-parameters-for-verify-push-factor.
This release provides the following:
- Improved IE performance when Browser Help Object (BHO) logging is enabled
- An option to opt out of cert pinning through the registry
- Iimprovements and bug fixes
For version history, see Browser Plugin Version History.
- System Log events are added for the ExactTarget, GitHub, Google, Gotomeeting, Rightscale, Roambi, Samanage, SendWordNow, ServiceNow2, ServiceNow, Smartsheet, SugarCRM, VeevaVault, WebEx, Yammer, and Zendesk provisioning integrations. Previously, the log events were only available using the Okta API. For details, see Provisioning Integration Error Events.
- System Log events are added for the Huddle, Jive45, Litmos, Lotus Domino, MoveIt DMZ, Msbpos, NetSuite, Org2Org, PagerDuty, Postini provisioning integrations. For details, see Provisioning Integration Error Events.
We have added new external Id attribute to the Zendesk provisioning app. ![]() Screenshot:
Screenshot:
You can now customize the email SAML attribute for the Netsuite app to map to an email or username attribute.
The Enable on-premises provisioning configuration option is removed from RADIUS apps, as it is not supported.
Okta and Cisco ASA interoperate through either RADIUS or SAML 2.0. For each Cisco ASA appliance, you can configure AAA Server groups which can be RADIUS, TACAS+, LDAP, etc. Using RADIUS, Okta’s agent translates RADIUS authentication requests from the VPN into Okta API calls. For more information, see Configure the Cisco ASA VPN to Interoperate with Okta via RADIUS.
Version 2.7.0 of the Okta Sign-In Widget is available. New features include :
- Voice call as an option for Unlock Account
- Display of multiple MFA responses
- Display a warning for beta registrations
For more information, see Okta Sign-In Widget.
The Okta Application Network (OAN) includes more than 5,000 pre-integrated business and consumer apps. As Okta expands beyond SSO and Provisioning, we are extending the network to include new integration types, and updating the catalog name to the Okta Integration Network (OIN). As part of this rebranding, we have changed the UI and documentation to reflect this change—managing and adding your apps and integrations remain the same.
The OIN now includes the following new integrations in addition to previous SSO and Provisioning options:
- F5 BIG-IP APM
- Sumo Logic Okta Activity Log Integration
- ServiceNow - Okta Orchestration Activity Pack
- Splunk Add-on for Okta
- QRadar Device Support Module (DSM)
For details about these new integrations, search and click the Learn More button. ![]() Screenshot:
Screenshot:
Note: This feature is now Generally Available for all orgs.
The flow of an end user's identity throughout the different stages of access is known as a user’s lifecycle. This release contains several enhancements to define the options that manage this cycle clearly.
- Simplified Import settings: Using a profile master necessitates a clear distinction between new and imported end users to prevent conflicts. Feedback from our users prompted improvements with matching rules, auto-confirmation and auto-activation settings.
- New lifecycle settings: When an end user is deactivated in a profile mastered app, admins can now set whether they are deactivated, suspended, or remain an active user in Okta.
See Profile Mastering and Life Cycle for more details.
Note: This feature is now Generally Available for all orgs.
Secure your APIs with API Access Management, Okta’s implementation of the OAuth 2.0 authorization framework. API Access Management uses the Okta Identity platform to enable powerful control over access to your APIs. API Access Management can be controlled by Okta admins as well as by a rich set of APIs for client, user, and policy management. For details on features available from the Admin console, see API Access Management.
We've improved the text and flow of the Add Rules dialog that is part of the Early Access API Management functionality. For details see, Create Rules for Each Access Policy.
The API Access Management Admin role has the following permissions:
- Create and edit Authorization Servers, Scopes, Claim, and access policies
- Create and edit OAuth/OIDC Client apps
- Assign users and groups to OAuth/OIDC client apps
- View user profiles when assigning users/clients for token preview
For more information, see API Access Management.
An animated transition page now appears when users click chiclets to log into apps:

Integrating Social Login with Okta is improved with redesigned screens, prepopulated IdP username value, and expanded entry options for scopes. ![]() Screenshot:
Screenshot:
The following message changes apply to either the Okta Org Authorization Server or a Custom Authorization Server including default (which requires API Access Management), or both, as indicated in each section.
The existing messages app.oauth2.authorize_failure, app.oauth2.as.authorize_failure and app.oauth2.as.authorize.scope_denied_failure replace these messages:
- app.oauth2.authorize.access_denied
- app.oauth2.authorize.invalid_client_id
- app.oauth2.authorize.invalid_cache_key
- app.oauth2.authorize.no_existing_session
- app.oauth2.authorize.login_failed
- app.oauth2.authorize.mismatched_user_in_cache_and_session
- app.oauth2.authorize.user_not_assigned
- app.oauth2.authorize.scope_denied
- app.oauth2.as.authorize.warn_failure
- app.oauth2.as.authorize.scope_denied
Details about the nature of the failure are included, so no information has been lost with this simplification.
These System Log changes affect responses from requests that involve either the Okta Org Authorization Server or a Custom Authorization Server including default.
Instead of supplying two different messages for token grant failures on /token, the existing message app.oauth2.as.authorize.token.grant_failure replaces these messages:
- app.oauth2.as.token.grant.warn_failure
- app.oauth2.as.token.grant.scope_denied_failure
This System Log change affects responses from requests that involve a Custom Authorization Server including default.
Instead of supplying a different message for ID token and access token generation, there's just one message for each. The ID token or access token minted is included in the message as it was previously.
- The existing message app.oauth2.authorize.implicit_success replaces:
- app.oauth2.authorize.implicit.id_token_success
- app.oauth2.authorize.implicit.access_token_success
- The existing message app.oauth2.as.authorize.implicit_success replaces:
- app.oauth2.as.authorize.implicit.id_token_success
- app.oauth2.as.authorize.implicit.access_token_success
The _success messages weren’t being written to the System Log previously, but are now.
These System Log changes affect responses from requests that involve either the Okta Org Authorization Server or a Custom Authorization Server including default.
Instead of supplying a different message for ID token and access token generation, there's just one message for each. The ID token or access token minted is included in the message as it was previously.
- The existing message app.oauth2.authorize.implicit replaces:
- app.oauth2.authorize.implicit.id_token
- app.oauth2.authorize.implicit.access_token
- The existing message app.oauth2.as.authorize.implicit
replaces:
- app.oauth2.as.authorize.implicit.id_token
- app.oauth2.as.authorize.implicit.access_token
These System Log changes affect responses from requests that involve either the Okta Org Authorization Server or a Custom Authorization Server, including default.
System Log entries are now added for the GoodData app. For details, see the GoodData section in Provisioning Integration Error Events
Admins can update the second email address on a master user profile when Attribute Mapping is enabled.
The Okta Sign On screen display is improved to display all factors when multiple Multifactor Authentication factors are required.
The header size limit for CSV imports is increased from 1000 to 50,000 characters.
The System Log tracks the following items:
- User authentication via IDP.
 Screenshot:
Screenshot: - Country code for SMS and voices.
 Screenshot:
Screenshot: - System Log events are added for the Clarizen, CrashPlanPro, Docusign, and Egnyte provisioning integrations. For details, see Provisioning Integration Error Events.
Added validation to API token creation when the maximum character length is exceeded
When creating or updating a rule in the Custom Authorization Server's policy, there is a button to add all default OpenID Connect scopes to the rule condition quickly. ![]() Screenshot:
Screenshot:
For more information, see Create Rules for Each Access Policy.
Grant types for OAuth 2.0 clients are reorganized for convenience on the General Settings page for an app and in the app creation screen in the developer console. For information on grant types, see App Wizard - Procedures. ![]() Screenshot:
Screenshot:
The Okta Sign In page supports unlocking an account with a Voice Call. ![]() Screenshot:
Screenshot:
-
The System Log tracks mass password expiry events.
 Screenshot:
Screenshot: -
The System Log tracks events when a user account is unlocked by an Admin, when the primary email for an account is updated, and when behaviors are detected.
When defining custom scopes for an Authorization Server, you can choose whether the metadata for these scopes is included in the public metadata. For more information, see Create Scopes.
Information and error messages are improved for the Access Token Lifetime and Refresh Token Lifetime setting in a policy rule. ![]() Screenshot:
Screenshot:
Okta’s Privacy Policy, available at https://okta.okta.com/privacy/, was updated on January 18, 2018 in order to comply with new, forthcoming requirements promulgated by Google, and to disclose more precisely the manner in which Okta interoperates with Google's G Suite after the OAuth authentication flow is successfully completed by the admin.
The password policy soft lock feature provides the option to lock Active Directory (AD) mastered users in Okta with password policies. To ensure that users are locked in Okta before they are locked out of their windows accounts, Admins must set a lockout count in Okta that is lower than the lockout count specified in the AD policy.
This feature does not change the current behavior for any organizations. Consequently, when this feature is enabled, the default invalid password lockout count for Active Directory password policies is reset to zero (0). Admins must specify a new lockout count to use this feature which s tracked in the System Log as a policy update event.
Some legacy customers might have non-zero values set in the invalid password lockout count in Okta. When these values are reset to zero with this feature, a System Log event is created to show the old and new values and inform Admins that the lockout is disabled.
For more information, see Group Password Policies.
Import Lockout Status from AD
Lockout status from AD is not imported automatically. To receive these imports, contact Okta Support. Any legacy users who already receive these imports will continue to receive them.
Rollout
This feature is becoming Generally Available and will be enabled in a phased manner across all cells. The feature will be enabled for the majority of customers in Preview and US Cell 1 by January 19th and for the remainder of customers in all other cells by February 2nd.
The button for creating OAuth 2.0 Services (Client Credentials apps) is moved from the applications list into the Add Application Wizard. For more information, see Add OAuth 2.0 Client Application. ![]() Screenshot:
Screenshot:
During OAuth Token Preview, selections for response type are not visible when the grant type is not IMPLICIT. For more information on token preview, see Test Your Authorization Server Configuration.
The General tab on the app instance screen for OAuth 2.0 clients now displays the Login initiated by dropdown for all grant types with App Only as the default. ![]() Screenshot:
Screenshot:
System Log entries were enhanced to include events when users were unassigned from group membership. ![]() Screenshot:
Screenshot:
Admin Managed tabs are not created if there are no apps to display in the tab. For more information, see Manage dashboard tabs for end users.
When admins create a new user they can choose whether to have that user create a password on first sign in or create a password for the user which must be changed on their next sign in. For details, see Add People.
Added support to allow updates to User and AppUser profile schemas. See App User Schema API documentation for more information.
The following User Profile properties have been added to our Netsuite integration:
location, class, notes, salutation, homePhone, officePhone, fax
To use these properties, you can either create a new app instance, or contact Okta Support to manually migrate the User Profile template. For more information about our Netsuite integration, see the Netsuite Provisioning Guide.
In Settings > Customization, fields in the Sign In page section now contain default placeholder text instead of default editable text. This enhancement makes it easier to distinguish fields that contain Okta's default text from fields that contain custom, admin-provided text. Placeholder text disappears when you enter custom text in the field. For more information, see Customize Sign In Page headings, links, labels, and placeholders.
Explanatory text on the Authorization Server are expanded, and also include a direct link to the Authentication Guide topic on the Developer site.
Error messages for permission errors for the password reset dialog are more descriptive and user-friendly.
All new SAML 2.0 apps are bootstrapped with SHA-256 signed public certificates. Existing SAML 2.0 apps are unchanged.
We have added email and phone writeback functionality for UltiPro international employees. For more information about UltiPro provisioning, see UltiPro User Import and Provisioning.
2018 Application Integrations and Updates
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Pivotal Tracker: For configuration information, see Tracker SCIM Documentation.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Retool: For configuration information, see Retool's SCIM User Provisioning - Okta Specific Guide.
- VidCruiter: For configuration information, see VidCruiter's Configuring SCIM with Okta.
-
Freshdesk (OKTA-191125)
-
Numeracy (OKTA-197992)
-
Retool (OKTA-197113)
-
Saba (OKTA-193973)
-
CALXA (OKTA-191701)
-
Dashlane Business (OKTA-188394)
-
FannieMae DUS Disclose (OKTA-193513)
-
Hillgate Travel (OKTA-191141)
-
Jack Henry and Associates (IPAY) (OKTA-194266)
-
Moody's (OKTA-193598)
-
MyToll (OKTA-190867)
-
Ncrunch (OKTA-190531)
-
Nmbrs (OKTA-188157)
-
PrintMail (OKTA-194265)
-
Retargeter (OKTA-191730)
We have updated our Zoom integration to support a new attribute, User Type. This allows customers to set the User Type per user being provisioned from Okta to Zoom to be either Basic, Pro, or Corp.
For users who have set up the Zoom integration and enabled Provisioning before November 8, 2018, follow the migration steps detailed in Zoom's Configuring Okta With Zoom if you want to use the new attribute.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Pivotal Tracker: For configuration information, see Pivotal Tracker''s Configuration Guide (note you will need to request access to this document.)
-
SpringCM: For configuration information, see SpringCM's Okta SCIM and SAML Integration.
-
Cerner (OKTA-194709)
-
Coralgix (OKTA-195349)
-
Digify (OKTA-193483)
-
eLeaP (OKTA-194168)
-
Mimecast - Admin (OKTA-193270)
-
Mobile Locker (OKTA-194895)
-
SaaSLicense (OKTA-195120)
-
Synthetix (OKTA-189127)
-
Star Station (OKTA-187650)
-
Aha! (OKTA-189385)
-
CorpTrav (OKTA-191634)
-
SAP Jam (SuccessFactors) (OKTA-189112)
-
Speco Technologies (OKTA-195019)
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Brivo Onair: For configuration information, see Brivo Onair's Identity Connector Integration Guide.
-
Rhombus Systems: For configuration information, see Rhombus Systems' How to Configure SCIM 2.0 with Okta.
-
Abstract (OKTA-192943)
-
Clubhouse (OKTA-194685)
-
ExpenseNet (OKTA-194122)
-
Lead Apparel (OKTA-187687)
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Cerner: For configuration information, see Cerner's Publishing Identity Data Using Okta (note that you need a Cerner account to access this documentation).
- Atlassian Cloud: For configuration information, see Atlassian Cloud's Configure User Provisioning with Okta.
- WorkRamp: For configuration information, see WorkRamp's SCIM Configuration Guide.
- AlertMedia: For configuration information, see AlertMedia's How to Configure User Provisioning with Okta (SCIM) (note that you need an AlertMedia account to access this documentation).
-
Aha! (OKTA-193716)
-
Drift (OKTA-193719)
-
Halo Communications (OKTA-192603)
-
Socialbakers (OKTA-193252)
-
UltiPro (OKTA-193804)
-
Abbvie (OKTA-189416)
-
Air Canada Travel Agency (OKTA-189703)
-
Asteron Life (OKTA-185986)
-
ChathamDirect (OKTA-189336)
-
Cloud Conformity (OKTA-189068)
-
Entoro Investor Login (OKTA-187239)
-
NoMachine: Workbench (OKTA-185837)
-
Plivo (OKTA-187847)
-
Sabre Vacations Travel Agency Login (OKTA-186555)
-
XactAnalysis (OKTA-188418)
- The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Figma: For configuration information, Figma's Configure Okta Provisioning.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Federated Directory: For configuration information, see Federated Directory's Integrate with Okta.
- Pigeonhole Live (OKTA-191208)
- Slab (OKTA-190334)
- Sunlight (OKTA-190547)
- Twic (OKTA-190548)
- Amazon IT (OKTA-186022)
- AudaExpress (OKTA-187178)
- Citizens Business Bank Online Banking (OKTA-187670)
- Federal Mogul ePresentment for Corporation Statements & Invoices (OKTA-186329)
- WooBoard (OKTA-187152)
- Corporate Travel Management (OKTA-190328)
The Solarwinds SWA integration application has been enhanced to support custom login URL’s.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access
- Tehama: For configuration information, see Tehama's instructions to Create a SCIM-based connected application.
- TextExpander: For configuration information, see the TextExpander Okta SCIM Configuration guide.
- Keeper Password Manager and Digital Vault: For configuration information, see Keeper Password Manager and Digital Vault's Configuring SCIM with Okta.
- Netskope: For configuration information, see Netskope's Provisioning Users and User Groups using OKTA.
-
HubSpot (OKTA-190126)
-
Tines (OKTA-190101)
-
Alamy (OKTA-189545)
-
Citrix Netscaler Gateway (OKTA-185234)
-
HiPay (OKTA-186563)
-
Invisalign (OKTA-186776)
-
LowesLink (OKTA-185180)
-
Meritain (OKTA-186927)
-
Mimecast - Admin (OKTA-185382)
-
Sabre Cruises (OKTA-186554)
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Zinc: For configuration information, see Zinc’s Setting up AD Sync with OKTA.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Forecast: For configuration information, see Forcecast’s Single Sign-On and user provisioning with Okta.
-
Emburse: For configuration information, see the Emburse-Okta SCIM Configuration guide.
- Carbon Black - PSC (OKTA-187929)
- MyWorkDrive (OKTA-189557)
- Seed (OKTA-188581)
-
Air Canada: Corporate Rewards Agent Login (OKTA-185502)
- CommInsure: Adviser (OKTA-185985)
- OnePath Advisor (OKTA-185989)
- Risk Control (OKTA-185533)
- Scribble Maps (OKTA-185677)
- HighGround (OKTA-184805)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Figma: For configuration information, see Figma's Configure Okta Provisioning.
-
Automox (OKTA-189108)
-
Instructure Bridge (OKTA-185486)
-
ABD Insurance and Financial Services (OKTA-183836)
-
Deluxe-Strategic Sourcing (OKTA-186091)
-
GoCompare (OKTA-185231)
-
Google Discover (OKTA-184419)
-
New Voice Media (OKTA-184604)
-
Nitro Cloud (OKTA-186292)
-
Salesforce (force.com) (OKTA-184354)
-
Zlife (OKTA-185988)
-
Figma (OKTA-186594)
-
Boardvantage Meetx/Director (OKTA-183845)
-
McMaster-Carr (OKTA-185177)
-
MyWave Connect (OKTA-183859)
-
Orgill (OKTA-185331)
-
RapidAPI (OKTA-185363)
-
Smallpdf (OKTA-184134)
- The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- 1Password Business: For configuration information, see Connect Okta to the 1Password SCIM bridge.
- Workplace by Facebook now supports Force Authentication. For more information see the Workplace by Facebook SAML setup instructions.
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Databricks: For configuration information, see the Okta Databricks Configuration Guide.
-
Avid Secure (OKTA-181718)
-
MyAcademy (OKTA-187155)
-
TopBox (OKTA-179620)
-
Workplace by Facebook (OKTA-185097)
-
Appsulate (OKTA-187156)
-
Brandify (OKTA-183379)
-
G Adventures Sherpa Agency (OKTA-183941)
-
GAMMIS (OKTA-182914)
-
IBM Partner World (OKTA-182930)
-
MIBOR (OKTA-187007)
-
TechPortal (OKTA-182900)
-
Zerto: DRaaS Service Portal (OKTA-180711)
- The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- ScreenSteps: For configuration information, see ScreenSteps' Configuring SCIM with Okta.
- 15Five now supports the following Provisioning feature (in addition to the other provisioning features that it already supports):
- Group Push
Users who have set-up the 15Five integration and enabled Provisioning before August 27, 2018, must follow the steps detailed in the 15Five Configuration Guide if they want to use the new features.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- OpenEye Web Services: For configuration information, see OpenEye Web Services' Configuring Okta Provisioning
- Sharpr: For configuration information, see How to Configure Provisioning for Sharpr.
-
Emburse (OKTA-185748)
-
TestingBot (OKTA-185998)
-
Akamai Enterprise Application Access (OKTA-180151)
-
Creditntell (OKTA-180856)
-
Essendant Solutions Central (OKTA-181089)
-
Exact Online (OKTA-167861)
-
Pure Storage Partners (OKTA-180445)
-
Wombat Security Awareness (OKTA-182578)
-
Zendesk (OKTA-181154)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Meta Networks: For configuration information, see Meta Networks' How to Configure SCIM 2.0 For Meta Networks.
-
DailyPay (OKTA-184138)
-
Fastly SAML (OKTA-184539)
-
Mimeo (OKTA-184146)
-
ProMaster (by Inlogik) (OKTA-184149)
-
Recruiterbox (OKTA-184536)
-
StatusHub Hub SAML (OKTA-180233)
-
TeamViewer (OKTA-183668)
-
EveryoneSocial (OKTA-181223)
-
Hermes Investment Management: EOS (OKTA-179402)
-
IRMLS Indiana Regional MLS - Safemls (OKTA-181470)
-
NatureBridge (OKTA-183752)
-
Polygon (OKTA-183237)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- H5mag: For configuration information, see H5mag's Okta Single-Sign-On Integration Guide.
-
Content Insights (OKTA-168880)
-
Adobe Enterprise (OKTA-178641)
-
Amazon Video Partner (OKTA-177266)
-
MassMutual Not-for-Profit Workplace Retirement (OKTA-178022)
-
Nuance (OKTA-180548)
-
Primeiro Pay (OKTA-181176)
- Dovetale (OKTA-183038)
- People.ai (OKTA-180849)
- Workteam (OKTA-182091)
- Imprima iRoom (OKTA-181903)
- Apple Business Manager (OKTA-179326)
- Centrelink (OKTA-180192)
- Decision Lender (OKTA-179129)
- Emburse (OKTA-183553)
- Mobile Health Consumer, Inc.(OKTA-180025)
- MY TELE2 FOR BUSINESS (OKTA-178240)
- United Intranet (OKTA-179628)
Fuze now supports the following Provisioning features (in addition to the other Provisioning features that it already supports):
- Importing Users
- Profile Mastering
Users who have set up the Fuze integration and enabled Provisioning before August 1, 2018, need to follow the migration steps detailed in the Fuze Configuration Guide if they want to use these new features.
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Amazon Chime: For configuration information, see Amazon Chime's Connect to Okta SSO instructions.
- 4me (OKTA-180242)
- SendSafely (OKTA-180234)
- AIA (OKTA-179070)
- AirVantage (OKTA-177125)
- Clearview (OKTA-179071)
- Fiscal Unattended Portal (OKTA-178318)
- Looker (OKTA-174927)
- LucidPress (OKTA-177037)
- Thycotic Force (OKTA-181148)
- Vyond: GoAnimate (OKTA-177036)
- LinkedIn Learning (OKTA-177771)
Namely now supports the following Provisioning features (this is in addition to the Profile Master feature that it already supports):
- Create users
- Update user attributes
For users that have set-up the Namely integration and enabled Provisioning before July 23, 2018, they have to follow the migration steps detailed in the Namely Configuration Guide if they want to use the new features.
-
Carbonite Endpoint Protection (OKTA-179619)
-
CipherCloud (OKTA-178258)
-
Omnilert (OKTA-178842)
-
Air Canada Travel Agency (OKTA-176497)
-
Deep Social (OKTA-175548)
-
FastMail (OKTA-173347)
-
FPI Portfolio (OKTA-177374)
-
GTA Travel (OKTA-175171)
-
Health Wise Global (OKTA-175660)
-
IBM Partner World (OKTA-178902)
-
iTunes Podcasts Connect (OKTA-177007)
-
JumpCloud (OKTA-176802)
-
Pinnacle Financial Partners (OKTA-174891)
-
Profitstars (OKTA-179309)
-
Quick Base (OKTA-179540)
-
Revenue NSW (OKTA-179226)
-
SkyKick (OKTA-177199)
-
StiPP (OKTA-177420)
-
Dialpad (OKTA-174331)
-
SwiftKey (OKTA-177039)
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- ScaleFT: For configuration information, see ScaleFT's Okta SCIM Configuration Guide.
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Quick Base. For configuration information, see Configure Okta Provisioning for Quick Base.
-
CloudSaver (OKTA-178376)
-
Fuel Cycle (OKTA-177763)
-
IMIchat (OKTA-172672)
-
Luminate Secure Access Cloud (OKTA-177980)
-
PitchBook (OKTA-178524)
-
Spoke (www.askspoke.com) (OKTA-176635)
-
Ultimo (OKTA-176636)
-
Symsys (OKTA-178538)
-
FrameIO (OKTA-175531)
-
Grove (OKTA-176622)
-
GTA Travel (OKTA-175171)
-
My NS Business (OKTA-176453)
-
Track My Backflow (OKTA-175785)
-
Wire (OKTA-173345)
-
Microsoft Dynamics CRM Online (OKTA-175795)
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- ProsperWorks: For configuration information, see the ProsperWorks SCIM Setup Guide.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Telmediq: For configuration information, see the Telmediq Provisioning Guide.
- CGR Foundation: For configuration information, see Configuring SCIM2 with Okta.
-
eFront (OKTA-176299)
-
Federated Directory (OKTA-177196)
-
Process Plan (OKTA-176823)
-
Torii (OKTA-176916)
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- ScaleFT: For configuration information, see ScaleFT's Okta SCIM Configuration Guide.
- ScreenSteps: For configuration information, see ScreenSteps' Configuring SCIM with Okta.
- ProsperWorks: For configuration information, see the ProsperWorks SCIM Setup Guide.
- Wrike: For configuration information, see Wrike & Okta: User Provisioning.
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
- Robin: For configuration information, see Robin's SCIM provisioning using Okta's connector app.
- CloudRepo: For configuration information, see the OKTA and CloudRepo Integration Guide.
- Elements.cloud: For configuration information, see Elements.cloud's Configuring User Provisioning with OKTA.
- Comeet: For configuration information, see Comeet's Okta SSO integration instructions.
-
Autotask Endpoint Backup (OKTA-175184)
-
Beneplace G3 (OKTA-173834)
-
Egress (OKTA-174618)
-
Forter (OKTA-174571)
-
getSayDo (OKTA-173822)
-
Mind Tools (OKTA-172557)
-
MockFlow (OKTA-170692)
-
ProsperWorks (OKTA-172832)
-
StatusHub (OKTA-174984)
-
Tiled (OKTA-173560)
-
BeValuedUk (OKTA-175212)
-
Cylance Partner (OKTA-173385)
-
Explorer for ArcGIS (OKTA-166173)
-
MRI Software (OKTA-177190)
-
Symsys Selmore (OKTA-174360)
-
Telmediq (OKTA-177265)
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
-
Mavenlink: For configuration information, see the Mavenlink OKTA SCIM Application Configuration Guide.
-
Guru: For configuration information, see Guru's SCIM Configuration Guide.
-
Zoom: For configuration information, see Zoom's Okta Configuration Guide.
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
LeanKit: For configuration information, see Configuring Provisioning for LeanKit.
We removed support for provisioning for the imeetcentral app.
-
Nvoicepay (OKTA-172287)
-
Sigma (OKTA-174900)
-
TrackVia (OKTA-171562)
-
Carrick Capital Partner (OKTA-173141)
-
Cisco (OKTA-173291)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
-
ScreenSteps. For configuration information, see Configuring SCIM with Okta.
We support SHA2 for the following integration:
-
Litmos (OKTA-169369)
-
AppDynamics v4.5+ (with SAML Encryption) (OKTA-172601)
-
Mambu (OKTA-171083)
-
Hippo CMMS (OKTA-173145)
-
TruQu (OKTA-172875)
The following partner-built provisioning integration app is now Generally Available in the OIN as partner-built:
-
Academy LMS by Praetorian Digital. For configuration information, see Configuring Provisioning for Academy LMS.
-
Paladin (OKTA-172501)
-
Talkdesk (OKTA-170361)
-
Cadence (OKTA-172519)
-
Guidewire Community (OKTA-171779)
-
Ipreo (OKTA-170892)
-
Mimecast Secure Messaging (OKTA-166261)
-
Portico Property Management (OKTA-171052)
-
Quadient Cloud (OKTA-166195)
-
SecureWorks (OKTA-172818)
-
WebAdvisor (OKTA-167409)
-
Wells Fargo (Commercial Electronic Office) (OKTA-172565)
-
Namely (OKTA-171365)
-
VMware Horizon View VDI (OKTA-171494)
-
Cadence (OKTA-171772)
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
-
1Password Business. For configuration information, see Automate provisioning with Okta in 1Password Business.
-
Comeet. For configuration information, see Comeet's Okta SSO integration instructions.
-
Built.io Flow (OKTA-170655)
-
Collective Health Employer Portal (OKTA-170658)
-
FOSSA (OKTA-170095)
-
Guru (OKTA-170656)
-
iDeals VDR (OKTA-166918)
-
Korbyt (OKTA-171463)
-
Marvelapp (OKTA-170657)
-
OpenEye Web Services (OKTA-167710)
-
1Password Business (OKTA-172516)
-
Amazon DE (OKTA-167431)
-
Benchmarking (OKTA-168838)
-
Dell Boomi (OKTA-171444)
-
DocsCorp Support (OKTA-168878)
-
Granite Group Advisors Education (OKTA-167734)
-
HP Channel Services Network (OKTA-170175)
-
HP Express Decision Portal (OKTA-166576)
-
IBM MaaS360 (OKTA-167146)
-
ITSupport247 (OKTA-167960)
-
Kronos: SaaShr Payroll (OKTA-169641)
-
LA Times (OKTA-166855)
-
Qlikid (OKTA-171593)
-
Rabobank Internetbankieren (OKTA-171384)
-
Rippe and Kingston LMS (OKTA-168601)
-
SAP Fiori Client (OKTA-170853)
-
ShowClix Organizer Login (OKTA-168649)
-
Spot.IM (OKTA-170306)
-
WebEx (Cisco) (OKTA-165568)
-
WorkFusion Forum (OKTA-168914)
-
xpenditure (OKTA-171605)
-
Yodeck (OKTA-170597)
-
G Suite (OKTA-170627)
-
Palo Alto Networks - GlobalProtect (OKTA-170860)
-
Zoho One (OKTA-171114)
-
Confluence On-Premise SAML (OKTA-168082)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Peakon. For configuration information, see Peakon's Set up user provisioning with Okta.
-
LaunchDarkly (OKTA-169378)
-
Saleshood (OKTA-169149)
-
EOLIS (OKTA-166337)
-
HP Partner First Portal (OKTA-166039)
-
HSB Connect (OKTA-167254)
-
Pandora (OKTA-162880)
-
Samsara (OKTA-166084)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Fuze. For configuration information, see the Fuze-Okta Provisioning Integration guide.
The following partner-built provisioning integration app is now available in the OIN as partner-built Okta Verified:
- Honey. For configuration information, see Honey's How To Configure SSO And User Provisioning Through Okta.
-
BeyondTrust (OKTA-166383)
-
Fivetran (OKTA-168577)
-
SmartDraw (OKTA-168214)
-
Collector (OKTA-168887)
-
Collector for ArcGIS (OKTA-166172)
-
ManageEngine ServiceDesk Plus (OKTA-164522)
-
Onfido (OKTA-168265)
-
Survey123 For ArcGIS (OKTA-166171)
-
G Suite (OKTA-165929)
-
SAP Fiori Client (OKTA-166524)
-
OrgWiki (OKTA-166365)
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
-
8x8. For configuration information see the 8x8 SCIM Configuration Guide.
-
Zinc. For configuration information see Zinc's Setting up AD Sync with OKTA documentation.
-
Amazon Web Services Redshift (OKTA-165274)
-
Duo Admin Panel (encrypted assertions) (OKTA-167692)
-
Enplug (OKTA-166192)
-
Everlaw (OKTA-167870)
-
SecurityCompass (OKTA-164352)
-
Verkada (OKTA-167421)
-
Xton Access Manager (OKTA-167253)
-
Yodeck (OKTA-166898)
-
Amadeus Selling Platform Connect (OKTA-164289)
-
Amazon JP (OKTA-165793)
-
Braze (OKTA-165681)
-
Cognito Forms (OKTA-165816)
-
Fiserv ServicePoint (OKTA-164827)
-
MasterControl (OKTA-164742)
-
Mercado Pago Chile (OKTA-164690)
-
MileIq (OKTA-166676)
-
Percipio (OKTA-164973)
-
Stampli (OKTA-166043)
-
StormWind Studios (OKTA-163355)
-
The Library (OKTA-165278)
-
Trafalgar (OKTA-164559)
-
Condeco Desk Booking v2 (OKTA-165976)
-
InFlight Mobile (OKTA-165974)
-
InVironMobile (OKTA-165975)
-
INX (OKTA-165973)
-
ProsperWorks (OKTA-165092)
The following partner-built provisioning integration apps are now available in the OIN as Okta Verified:
- Dialpad. For configuration details, see the Dialpad Okta SAML & SCIM Configuration Guide.
- Vivantio ITSM. For configuration details, see the Vivantio ITSM Okta Provisioning Guide.
-
Braze (OKTA-164730)
-
EZRentOut (OKTA-165985)
-
Peakon (OKTA-164574)
-
Podbean (OKTA-165001)
-
ReadCube (OKTA-165511)
-
ScreenSteps (OKTA-166666)
-
Shareworks (OKTA-166193)
-
Visual Paradigm Online (OKTA-164575)
-
Ziflow (OKTA-165510)
-
Columbia Bank: Columbia Connect Login (OKTA-164598)
-
DemandCaster (OKTA-162686)
-
eNett (OKTA-161969)
-
Helpshift (OKTA-164347)
-
Meditta Customer Portal (OKTA-164125)
-
Mood Mix (OKTA-163389)
-
MT Bank: Web InfoPLUS Login (OKTA-163923)
-
Registro.br (OKTA-163594)
-
The Alabama Department of Revenue Motor Vehicle Division (OKTA-164095)
-
Dialpad (OKTA-162928)
-
Sequr (OKTA-165140)
-
CGR Foundation (OKTA-163834)
-
SimpleLegal (OKTA-162488)
-
TradeShift (OKTA-163383)
-
ArcGIS Online (OKTA-163206)
-
Alacriti: OrbiPay Payments (OKTA-162622)
-
Ascensus (OKTA-158493)
-
Bendigo Bank (OKTA-162125)
-
Boxed (OKTA-161706)
-
Colorado CDOT Maps (OKTA-162497)
-
Join Handshake (OKTA-162160)
-
Okta Ice: Gourmet Ice Cream (OKTA-163277)
The following partner-built provisioning integration app is now available in the OIN as partner-built Early Access:
- Vivantio ITSM. For configuration details, see the Vivantio Okta Provisioning Configuration Guide.
-
Givitas (OKTA-163560)
-
SSOGEN (OKTA-163382)
-
Zoom (OKTA-161971)
-
Appsulate (OKTA-162836)
-
Aurilo (OKTA-160566)
-
CBS Helpdesk (OKTA-161425)
-
Creditsafe (OKTA-163255)
-
ESET: License Administrator (OKTA-157798)
-
FamilySearch (OKTA-160772)
-
MYOB Essentials (OKTA-160212)
-
Northpass (OKTA-161830)
-
StatusHub (OKTA-161879)
-
WEXOnline Client Login (OKTA-161332)
-
Impraise SAML (OKTA-163703)
-
Nexus Payables (OKTA-162012)
-
IrisPR (OKTA-161401)
-
LCVista (OKTA-161816)
-
LeanKit (OKTA-161594)
-
LeaseEagle (OKTA-161705)
-
AccessNS (OKTA-161378)
-
AirTriQ (OKTA-159849)
-
Circulation (OKTA-160516)
-
EduServices (OKTA-163277)
-
Fido SSP (OKTA-159156)
-
Go365 (OKTA-160329)
-
Kaseya Virtual System Administrator (OKTA-160565)
-
Kids A-Z Kids Login (OKTA-160556)
-
LumApps (OKTA-160612)
-
Veritas Support (OKTA-160843)
-
G Suite (OKTA-160751)
The following partner-built provisioning integration apps are now available in the OIN as Okta Verified:
- Hootsuite. For configuration details, see the Hootsuite Okta SCIM Configuration Guide.
- MyPolicies. For configuration details, see the MyPolicies + Okta SCIM Employee Provisioning guide.
- Lumpy. For configuration details, see the Okta + Lumity: SCIM Provisioning guide.
- Teamable: For configuration details, see the Configuring provisioning for Teamable guide.
The following partner-built provisioning integration apps are now available in the OIN as partner-built Early Access:
- Airtable. For configuration details, see Airtable's Okta provisioning configuration options guide.
- Appenate. For configuration details, see the Appenate Configuration Guide (note you will need to login to Appenate for access to this doc).
- Atipicia. For configuration details, see Atipicia's Okta user provisioning integration guide.
- Biztera. For configuration details, see Biztera's Configuring Okta Provisioning guide.
- Dialpad. For configuration details, see DIALPAD + OKTA | SAML & SCIM INSTRUCTIONS.
- ProLease. For configuration details, see the ProLease SCIM Setup Guide.
- StarLeaf. For configuration details, see the Starleaf Okta Integration.
- Twebcast. For configuration details, see Setup user provisioning for Twebcast with Okta.
- Vable. For configuration details, see OKTA users provisioning for Vable platform.
- DocSend. For configuration details, see DocSend's Okta SCIM Integration.
- Kudos. For configuration details, see the Kudos Okta SCIM 1.1 configuration guide.
- LearnCore. For configuration details, see LearnCore's SCIM Integration Documentation.
- SchoolKeep. For configuration details, see SchoolKeep's Configuring Okta Provisioning.
- Sequr. For configuration details, see the Sequr + Okta : Employee Provisioning Integration guide.
- Velpic. For configuration details, see Configuring the Velpic App from the OKTA Application Network for SCIM.
- Workboard. For configuration details, see Configuring Provisioning for Workboard.
- Zugata. For configuration details, see Zugata's Sync Users with Okta - SCIM.
- Expensify. For configuration details, see Expensify's Deactivating users with Okta guide.
- ClearStory. For configuration details, see ClearStory's Okta User Provisioning guide.Or Provision
- Cloud Repo. For configuration details, see the OKTA and CloudRepo Integration Guide
- Civis Platform. For configuration details, see Configuring Provisioning for Civis Platform
- Rollbar. For configuration details, see the Rollbar's Okta Configuration guide.
-
Duo Admin Panel (OKTA-157272)
-
Supermood (OKTA-161747)
-
T&E Express (OKTA-161402)
-
TalentWall (OKTA-161809)
-
Allinial Global (OKTA-159690)
-
AnswerForce (OKTA-159091)
-
InstaMed Online for Providers (OKTA-159927)
-
Jive (OKTA-158828)
-
Lucky Mobile OneView (OKTA-159151)
-
OpenX Community (OKTA-159626)
-
Rogers SSP (OKTA-159155)
-
Update OIN App (OKTA-162277)
-
Virgin Mobile OneView (OKTA-159150)
-
Impraise (OKTA-160452)
-
Microsoft Flow (OKTA-158687)
-
Microsoft Planner (OKTA-158691)
-
Microsoft Power BI (OKTA-158690)
-
Microsoft StaffHub (OKTA-158688)
-
Microsoft Sway (OKTA-158686)
-
Microsoft Visio Viewer (OKTA-158846)
-
Names & Faces (OKTA-160449)
-
Office 365 Message Encryption Viewer (OKTA-158847)
-
Office Delve (OKTA-158685)
-
iLobby (OKTA-160231)
-
PROLEAZ (OKTA-159605)
-
Samepage (OKTA-159604)
-
Sonar (OKTA-160236)
-
InstartLogic (OKTA-159557)
-
iNSYNQ (OKTA-156377)
-
San Diego Tribune (OKTA-158974)
-
Bersin (OKTA-158347)
-
CA Technologies Continuous Delivery Director (OKTA-159230)
-
TeamViewer (OKTA-158486)
-
Comcast Business (OKTA-158584)
-
First Republic Bank: Corporate Online Sign In (OKTA-158497)
-
First Tennessee Digital Banking (OKTA-157454)
-
Oakland Public Library Catalog (OKTA-158490)
-
Twenty20 Stock (OKTA-158185)
-
Nine (OKTA-158954)
-
Sonos (OKTA-158254)
- Provisioning is enabled for the Teamable Partner-Built application (OKTA-159394). For details, see the Teamable Provisioning Configuration Guide for details.
- Provisioning is enabled for the Lumity Partner-Built application (OKTA-159171). For details, see the Lumity Provisioning Configuration Guide for details
-
AlertOps (OKTA-158941)
-
Atiim (OKTA-156758)
-
Honey (OKTA-159100)
-
Oktopost (OKTA-158746)
-
PathSavvy (OKTA-159590)
-
Sapling (OKTA-157436)
-
Templafy (OKTA-158476)
-
TextExpander (OKTA-154028)
-
TraceGains (OKTA-157106)
-
AppNexus: Customer Support Portal (OKTA-158053)
-
Associated Bank (OKTA-157218)
-
Bizequity (OKTA-158244)
-
ECP (OKTA-155556)
-
Guidewire Live (OKTA-157445)
-
Humana Military (OKTA-158412)
-
ISOnet (OKTA-158232)
-
Jetstar AgentHub (OKTA-156973)
-
Parker: PHconnect Login (OKTA-158386)
-
Quay (OKTA-156972)
-
VocabularySpellingCity (OKTA-157236)
-
Microsoft Dynamics CRM Online (OKTA-157274)
-
OpenVPN Connect (OKTA-157442)
-
Pocket (OKTA-157815)
-
Virtru (Google Login) (OKTA-157353)
-
CultureHQ (OKTA-156714)
-
Databook (OKTA-157722)
-
InstaCheckin (OKTA-157452)
-
PlanGrid (OKTA-156180)
-
Burgiss: Cash Management (OKTA-154713)
-
DataServ (OKTA-157609)
-
R and D Manage (OKTA-156454)
-
Sharpr (OKTA-156588)
-
Stackla (OKTA-156474)
-
ABN AMRO (OKTA-156308)
-
Everest 7.0 (OKTA-155695)
-
Express VPN: Affiliates (OKTA-156499)
-
Instapage (OKTA-156197)
-
OUI.sncf (OKTA-156191)
-
Phone2Action (OKTA-156595)
-
Sling TV (OKTA-156708)
-
State of Wisconsin DWD: Insurer Reports (OKTA-152447)
-
WordPress.com (OKTA-156182)
-
Civis Platform (OKTA-155135)
-
ContractWorks (OKTA-153656)
-
Givitas (OKTA-155684)
-
Iggy (OKTA-155258)
-
ITProTV (OKTA-155248)
-
Pritunl (OKTA-154499)
-
PurchaseControl (OKTA-152586)
-
Supermood (OKTA-148675)
-
Wordpress by MiniOrange (OKTA-151125)
-
BootcampSpot v2 (OKTA-153220)
-
Crimson Hexagon (OKTA-155976)
-
Delivery Slip (OKTA-155537)
-
EverBank (OKTA-152736)
-
Franklin Synergy Bank (OKTA-152727)
-
Haaretz (OKTA-154551)
-
Leaseplan FleetReporting NL (OKTA-152941)
-
LinkPoint Connect Cloud Edition (OKTA-155230)
-
MassBio (OKTA-155241)
-
Milestone XProtect Smart Client (OKTA-153239)
-
Rapt Brand Fonts (OKTA-152869)
-
ReadyRefresh (OKTA-154418)
-
Salesgenie (OKTA-155096)
-
TPG (OKTA-154455)
-
Vertafore Agency Platform (OKTA-153643)
-
XpertHR (OKTA-155946)
-
Zoho Wiki (OKTA-154570)
-
Gboard (OKTA-154398)
-
NMBRS (OKTA-154804)
-
Arxspan (OKTA-154479)
-
Booking (OKTA-153126)
-
FHA Connection (OKTA-153897)
-
United Fire Group (OKTA-151261)
-
Wayfair (OKTA-152399)
-
Expensewatch (OKTA-154005)
-
Plex Apps (OKTA-153104)
-
Spoke (OKTA-153512)
-
Trustwave SWG Cloud (OKTA-153108)
-
Zoho One (OKTA-153517)
-
Addepar (OKTA-151872)
-
Adobe Stock (OKTA-152449)
-
ANZ Internet Banking Australia (OKTA-152515)
-
Ascensus (OKTA-151756)
-
CAI: Capital (OKTA-152732)
-
Carval: User Portal (OKTA-149880)
-
Health Plans (OKTA-153613)
-
Indiana Association of Realtors (OKTA-152450)
-
Instant Payroll (OKTA-152081)
-
Intuit Developer (OKTA-151109)
-
Kentik (OKTA-152102)
-
MIBOR (OKTA-143980)
-
MyShaw (OKTA-149352)
-
SAFE Credit Union (OKTA-152425)
-
UFG Agent (OKTA-151261)
-
VIA Rail (OKTA-152013)
-
Visionplanner (OKTA-152186)
-
Astea (OKTA-152017)
-
Moo.do (OKTA-152690)
-
Square (OKTA-152355)
-
UltiPro (OKTA-151970)
2018 Bug Fixes
- OKTA-168628 – Self assignment of a Federation Broker Mode app failed without any error message to the user.
- OKTA-187446 – The error message when adding an empty dynamic zone contained minor grammatical mistakes.
- OKTA-188556 – The Android for Work app appeared on Okta end user dashboard even though the app was configured in the Okta Admin console not to display.
- OKTA-189358 – Two Authentication of user via MFA and Evaluation of sign-on policy events were generated in the System Log for each user login.
- OKTA-189803 – When configuring policy assignment for Factor Enrollment, Sign-On, and Password policies, Group searches did not return more than 10 results.
- OKTA-191151 – Norwegian translations in Okta plugin had minor inconsistencies.
- OKTA-192504 – AD-mastered users were able to edit the Secondary Email attribute even when it was set to Read-Only.
- OKTA-193456 – Some Sign-On policies using a behavior rule did not display the correctly used rule in the System Log event.
- OKTA-193955 – User Profile labels were sometimes displayed in languages other than English when an admin tried to view the profile.
- OKTA-194153 – The UTF-8 encoding of the SCIM Server URL in the SCIM App Template was not RFC compliant.
- OKTA-194195 – When all MFA factors in an app Sign-On policy were set to optional, a new user after successfully enrolling in a factor was redirected to the app instead of the enrollment page to enroll in multiple MFA factors.
- OKTA-195093 –If an app had more than 20 instances that appeared above the option to select All <app name> Instances, it was not possible to select that option.
- OKTA-195582 – The interstitial page had an invalid HTML.
- OKTA-195906 – Saving custom email templates for MFA Factor Enrollment and MFA Factor Reset did not display an error when one or more required fields were missing.
- OKTA-197175 – Self service registration error messages displayed in the sign-in widget were not correctly localized.
- OKTA-197256 – The French translation of registration.error.minLength was incorrect.
-
Amplitude (OKTA-197221)
-
AvaTax Admin Console (OKTA-196830)
-
Benelogic (OKTA-197354)
-
ChannelAdvisor Forum (OKTA-196813)
-
Circulation (OKTA-196990)
-
DNSPod (OKTA-196832)
-
EVA Air (OKTA-197596)
-
Lynda.com (OKTA-196839)
-
National Car Rental (OKTA-73276)
-
Okta Org2Org (OKTA-197198)
-
Salesforce: Marketing Cloud (OKTA-196079)
-
SAM.gov (OKTA-197595)
-
Seek (AU) - Employer (OKTA-196831)
-
Swiftype (OKTA-197936)
-
viewfinity (OKTA-197594)
- OKTA-187113 – Emails sent to test a custom email template incorrectly used the default template instead.
- OKTA-188863 – After modifying metadata for a SAML app, URL metadata for the new Identity Provider Certificate in the SAML Setup instructions for the app was not updated.
- OKTA-190755 – On some Windows machines, attempts to open a document through Microsoft SharePoint failed with the error message: This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator.
- OKTA-191466 – For orgs that had configured and enabled iOS Device Trust, users on Okta Mobile on iOS accessing a SAML application (with ForceAuthn flag enabled ) were not able to complete the flow.
- OKTA-192955 – In some cases, when the Application Username Format was changed for an app on the Sign On tab, the username did not update accordingly in the app.
-
OKTA-197844H - In some cases, user imports failed with a Resource not found error.
- OKTA-197850H - App icons did not load in Okta Plugin for Google Chrome when the CDN was disabled.
-
Carta (OKTA-195136)
-
CBT Nuggets (OKTA-194884)
-
CH Robinson Navisphere 2.0 (OKTA-193943)
-
eDataSource (OKTA-192665)
-
General Motors GlobalConnect (OKTA-196112)
-
IBM Workspace (OKTA-194887)
-
Inspectlet (OKTA-196109)
-
MassMutual Retirement Access (OKTA-194881)
-
MidFirst Bank iManage Personal Banking (OKTA-194622)
-
Olapic (OKTA-196110)
-
PaloAlto Networks Support (OKTA-196076)
-
Rackspace Admin Control Panel (OKTA-194888)
-
Rubicon Project (OKTA-196217)
-
Safeware (OKTA-194880)
-
SonicWall (OKTA-195177)
-
UPS CampusShip (OKTA-194141)
-
Walmart (OKTA-196204)
- OKTA-150759 – System Log events for the iOS Device Trust did not display CredentialType value.
- OKTA-182989 – Admins could access the deprecated System Log V1 UI by directly pasting the URL in the browser.
- OKTA-191057 – Temporary passwords generated by an admin password reset included hard-to-distinguish characters that could be confusing to users.
- OKTA-189249 – IdP Discovery rule with a Sharepoint On-Premise app condition was not routing properly on SP-initiated login flows.
- OKTA-189512 – Mobile admins did not receive an email notification if a user was deprovisioned from Android For Work or Google apps.
- OKTA-192009 – Enrolling in Okta Verify using SMS on mobile devices resulted in a message Okta Verify Not Detected instead of a message to open the app or to download the app from the relevant app store.
- OKTA-194096 – The MFA Usage report incorrectly listed Okta Verify as an enrolled factor for a user even when the factor was reset and was no longer enrolled for the user.
- OKTA-194735 – The Device Trust message displayed while adding an app sign-on rule did not reflect correct platform names.
- OKTA-194899 – The set of roles allowed access to system log information by the [Events API](/docs/api/resources/events) did not match the set of roles allowed access by the [System Log API](/docs/api/resources/system_log).
-
CGarchitect (OKTA-194273)
-
Check Point (OKTA-194916)
-
Google AdWords (OKTA-195109)
-
IBM Partner World (OKTA-194275)
-
Intouch Tech Data (OKTA-194276)
-
Leaseplan FleetReporting NL (OKTA-194272)
-
Santander (OKTA-194277)
-
ShowingTime (OKTA-194896)
-
FCm Travel Solutions Client Portal (OKTA-195584)
- OKTA-141857 – Some SAML Capable Apps reports incorrectly prompted to convert the app to SAML, even when the app was already using SAML 1.1 or SAML 2.0.
- OKTA-151933 – A race condition caused Group Push Mappings to be re-associated with a deleted Group Push Mapping Rule. This caused the mappings to be hidden from the Group Push UI and prevented changes to Group Push Mappings in case modifications are needed to address failures.
- OKTA-165757 – Changed user attributes in Active Directory sometimes were not properly updated in Okta.
- OKTA-168628 – Self service was not disabled for an implicit app instance, resulting in an error in the logs.
- OKTA-179336 – App Embed Link in the General tab of the Application page was greyed out in Firefox browsers and could not be copied.
- OKTA-182143 – Save and Add Another group in the Group Push UI did not work the first time.
- OKTA-184312 – API integration for a SCIM app failed when the app had no users.
- OKTA-185043 – Custom Authorization Server dialog was too large and hid the Add button when more than 30 clients were added to access policies at a time.
- OKTA-186068 – When looking up System Log entries for a six-month period, an incorrect date error was displayed even when the selected From date was six months away from the To date.
- OKTA-188600 – In some cases, when app provisioning failed, retrying tasks either in bulk or individually on the Task page failed.
- OKTA-190204 – When the MFA for admins feature was enabled, upon signing into support.okta.com, admins were redirected to the Okta admin console instead of support.okta.com.
- OKTA-190313 – In some cases, end users signing into Okta using Integrated Windows Authentication were displayed an incomplete technical contact email address.
- OKTA-190610 – When the MFA for admins feature was enabled and a sign-on policy prevented admins from signing in to Okta, admins configured to be allowed temporary access were still locked out.
- OKTA-191811, OKTA-194143 – When specifying a regex for user matches in an IdP discovery routing rule, the following error was returned: We found some errors. Please review the form and make corrections.
- OKTA-193127 – Running Application Usage reports sometimes failed with a timeout error.
- OKTA-193871 – Pushing the Exchange ActiveSync mail profile to OMM-managed iOS devices failed for AD-mastered users in orgs with Delegated Authentication configured.
- OKTA-194116 – A PUT call did not remove the postalAddress value from the user profile as expected.
- OKTA-194502 – In the System Log, the client IP address displayed did not correctly match the client geo-location when the Dynamic Zones feature is enabled.
- OKTA-194909 – Provisioning a user to Office 365 through User Sync or Universal Sync failed with the error: Got exception Unable to create the DirSync response object ProvisionResponse.
- OKTA-196801H - Attempt to match an imported user to an existing Okta user using the option “Existing Okta user I specify” did not retrieve the desired account even when it existed in Okta.
- OKTA-196665H - Attempt to edit an inactive group rule returned an internal server error.
- OKTA-196612H - Some end users signing into Okta received password hints in another language even when the display language was English.
-
ADP Payline (AU) (OKTA-192607)
-
AliMed (OKTA-192595)
-
Amazon Marketing Services (AMS) (OKTA-194123)
-
Blue Sky Factory (OKTA-192127)
-
Cisco (OKTA-188488)
-
Google Analytics (OKTA-192899)
-
Google Data Studio (OKTA-192135)
-
IBM Cloud (OKTA-192612)
-
Jell (OKTA-192132)
-
LumApps (OKTA-187691)
-
MyCitrix (OKTA-193111)
-
Norex (OKTA-192594)
-
Ravti (OKTA-190349)
-
Salesforce - Marketing Cloud (OKTA-194482)
-
SignNow (OKTA-190434)
- OKTA-151397 – Group admins were erroneously able to view users who were outside the Active Directory groups being managed by them.
- OKTA-174550 – The incorrect password error message displayed for AD-mastered users and Okta-mastered users was inconsistent.
- OKTA-175568 – Messages that were sent to devices using the Factors API sometimes returned a 500 error if the message could not be sent.
- OKTA-176446 – Attempts to complete new user activation using JIT failed for users in a state of Pending Activation.
- OKTA-183303 – The Managed column on the Group Assignment page incorrectly appeared to be sortable/clickable.
- OKTA-184763 – Workday to Okta imports failed for users with Organizations that had a null Organization_Type_Reference.
- OKTA-187876 – Yubikey reports that included deleted users were not fully viewable, and displayed the following error message: Error, Service is in Read Only Mode.
- OKTA-189519 – In rare cases, a custom domain could not be removed using the Restore to Default link.
- OKTA-191750 – When setting up Admin Email Notifications, changing the Notification Preferences For dropdown option from Global Enablement to My Preference failed.
- A Cloud Guru (OKTA-187786)
- ADP Workforce Now (Employee) (OKTA-191089)
- Amazon Marketing Services (AMS) (OKTA-192124)
- Backblaze (OKTA-191414)
- Dun & Bradstreet (OKTA-189723)
- Fusebill (OKTA-189915)
- Instagram (OKTA-192593)
- MURAL (OKTA-192126)
- StatusCake (OKTA-192416)
- TravelCube Pacific (OKTA-190067)
- Zerto: DRaaS Service Portal (OKTA-189985)
- Atlassian Cloud (OKTA-188779)
- OKTA-183216 – When a device enrollment operation failed, the error message was incorrect.
- OKTA-186779 – For the AWS app, credentials verification failed when adding multiple accounts IDs belonging to China AWS region.
- OKTA-188601 – When a user account was deactivated in a provisioned app then imported to Okta and then to AD, the user account was not deprovisioned as expected.
- OKTA- 191753 – System Log query parameters prior to the allowed time range returned an unknown error (HTTP status code 500).
-
Akamai Enterprise Application Access (OKTA-187781)
-
Cisco (OKTA-188488)
-
Cisco Partner Login (OKTA-188281)
-
Integral Ad Science (OKTA-189258)
-
Juice (OKTA-187782)
-
Mapbox (OKTA-188752)
-
MURAL (OKTA-189084)
-
Pingdom (OKTA-190166)
-
PleaseReview (OKTA-187779)
-
Tumblr (OKTA-189894)
-
Verizon Wireless Business (OKTA-189357)
-
Saba (OKTA-164211)
- OKTA-178657 – When multiple attempts were simultaneously made to update a user's phone number for SMS or voice factors, the user was unable to enroll the phone number.
- OKTA-181134 – For Dropbox for Business app, group memberships were not imported while importing users and groups.
- OKTA-182512 – Okta was incorrectly pushing to the SCIM app memberships for users who were not previously provisioned to the app.
- OKTA-182770 – On updating Jira apps on Atlassian Cloud, the API rate limit of Atlassian often prevented pushing groups from Okta to Atlassian.
- OKTA-185451 – When an app admin with permission to administer a specific app attempted to save the app settings using the API Endpoint {{url}}/api/v1/apps/{{AppID}} failed with an insufficient permissions error message.
- OKTA-185620 – The Microsoft Forms chiclet on the enduser dashboard did not log in the user automatically when the sign on mode was SWA.
- OKTA-190057 – If Device Trust certificate issuance, enrollment, or renewal failed while the Okta service was in Read Only mode, the failure was not logged in the System Log.
-
Datadog (OKTA-185125)
-
Glassdoor (OKTA-189125)
-
Prezi (OKTA-188694)
-
Salesforce: Marketing Cloud (OKTA-189073)
-
Ascensus: Partner Login (OKTA-184944)
- OKTA-124052 – Profile sync from Okta to third-party apps failed instead of ignoring users not already provisioned to the third-party app.
- OKTA-180603 – The Variable Name for enumerated attributes was not displayed in the user profile.
- OKTA-182976 – Admins could not see all Microsoft Office 365 apps assigned to a user when previewing the end user Dashboard on the Customization page.
- OKTA-184730 – When setting up AWS GovCloud with multiple accounts, testing the API credentials or saving provisioning configuration failed with an invalid client token ID error.
- OKTA-188112 – When multiple attempts were simultaneously made to update a user’s phone number for SMS or voice, an HTTP 500 error occurred intermittently.
- OKTA-188212 – Links to Device Trust version history documents on the Settings > Downloads page were broken.
- OKTA-188697 – The Norwegian language was listed as Bokmål instead of Norsk Bokmål in the Display Language options.
- OKTA-188880 – Admins could not change the username format for OIDC apps in the Profile Mappings editor.
- OKTA-189139 – In some Preview orgs, Symantec VIP settings were not displayed in Internet Explorer 10 and 11 when configuring the factor for MFA.
-
ADP Portal (Admin) (OKTA-188716)
-
Comcast Business (OKTA-188339)
-
eWallet ADP (OKTA-188414)
-
OneSignal (OKTA-188704)
-
Visionplanner (OKTA-188355)
-
VMware Partner Network (OKTA-188299)
-
Wrike (OKTA-188554)
- OKTA-167649 – When configuring an LDAP instance, the text description of when to use the User Attribute field was not clear.
- OKTA-175504 – Kosovo was missing from the Country dropdown list when setting up a phone number for MFA.
- OKTA-179460 – In the Org2Org app, when a user was not activated in the target system, pushing user updates failed.
- OKTA-180472 – The System Log displayed duplicate entries to Org admins for enrolling and auto-activating MFA factors.
- OKTA-181897 – The error message on the Add Person pop-up was not descriptive enough.
- OKTA-184400 – The Activation email link failed for imported AD users, displaying an error message about a non-existent security question.
- OKTA-184613 – When the App admin was assigned an app that included the "|" character in its name, app search did not work.
- OKTA-184982 – The Multifactor page displayed UI elements such as the Edit button to Read Only admins.
- OKTA-185195 – SP-initiated logins for SAML 2.0 apps were not logged in the System Log when access was denied by an App Sign On policy.
- OKTA-185215 – For self service registration, password policy descriptions and error messages were not localized correctly, and defaulted to English.
- OKTA-186200 – Help Desk and Read Only admins received a blank pop-up screen when trying to activate or deactivate an MFA factor type on the Multifactor page.
- OKTA-186269 – The RSA SecurID username format dropdown did not display AD-related options.
- OKTA-186780 – The Reset Password page did not accept some usernames that were not in email format.
- OKTA-187597 – The Feedback button on the admin dashboard directed users to a wrong path.
- OKTA-187720 – If a company name contained the "&" character, the name was only displayed up to the "&" character on the New Account Registration page.
- OKTA-187875 – The download buttons on the Download page were inactive for some admins during maintenance.
-
Dealer Daily Lexus (OKTA-188063)
-
IRMLS Indiana Regional MLS - Safemls (OKTA-186105)
-
Procore (OKTA-187722)
- OKTA-172556 – Technical Contact on the Account Pending Activation page did not appear when staged users tried to log in to Okta.
-
OKTA-185863H – After CLOUD_DESKTOP_SSO was enabled, in certain situations the Allowed Network Zone list in the admin UI was duplicated multiple times. Once the list became too large, IWA began to fail and users were prompted to login.
- OKTA-185863 – Users could not enroll their phone number for Self Service as they were prompted with the error message "Password or factor verification has expired" even when the session was just created.
- OKTA-186848 – Okta Verify push notifications were not displayed immediately on Android devices when the device screen was turned off.
- OKTA-187067 – Subscribed admins did not receive the deactivation email when a user with assigned apps was deactivated through the Okta Admin UI.
-
OKTA-187726H – externalName and externalNamespace fields were missing from the Add Profile Attribute dialog for OIN SCIM apps.
-
Cisco WebEx Meeting Center (OKTA-185731)
-
D2L (OKTA-184842)
-
DeltaSkymiles (OKTA-185635)
-
Kamer van Koophandel (OKTA-187153)
-
Moodlerooms (OKTA-186579)
-
mySonitrol (OKTA-185824)
-
myATT (OKTA-185885)
- OKTA-83725 – The Zendesk app removed the admin role of an admin user required for Zendesk API access.
- OKTA-166236– The Sign In page did not render properly when the user agent was empty.
- OKTA-173065 – On the admin dashboard, the warning dialog displayed active buttons to Read-only admins.
- OKTA-175981 – API Token link reference for the On-Prem MFA Agent was linking to /admin/access/rsa-securid page instead of /admin/access/on-prem page.
- OKTA-181650 – Deprovisioning users from the Workplace by Facebook app failed due to an API rescheduling error if the user's manager could not be imported from AD.
- OKTA-184540 – Changing the list of Network Zones enabled for Desktop SSO did not generate a System Log event as expected.
- OKTA-184731 – In Chromebooks, when IdP Discovery was enabled, users were unable to login to certain IDPs.
- OKTA-185632 – Mapping from a user's primary email to their username was not enforced when the user's primary email was changed by an admin.
- OKTA-185819 – Bulk activate option for onboarding on the People page has been restored. This affects Preview orgs only.
-
Apple Store for Business (OKTA-185638)
-
Codility (OKTA-186038)
-
Factual (OKTA-185681)
-
ManageEngine ServiceDesk Plus (OKTA-185481)
-
MURAL (OKTA-185636)
-
Okta Help Center (OKTA-185639)
-
PR Newswire (OKTA-186572)
-
Siteimprove (OKTA-185464)
-
LogMeIn Central/Pro (OKTA-180957)
- OKTA-163542 – Newly imported Okta users were sometimes not added to an Okta push group in Slack.
- OKTA-169041 – In the Office 365 app, if a user had no licenses assigned, deleting that user during de-provisioning failed.
- OKTA-178599 – JIT Delegated Authentication failed in some cases when Okta was in safe mode.
- OKTA-180070 – In Browser Plugin settings, Enable Okta toolbar for group dropdown had no group selected by default on new orgs causing on-the-fly functionality to fail.
- OKTA-180348 – Linked Object property names were incorrectly allowed to begin with a digit or contain characters other than digits, ASCII letters, and underscores.
- OKTA-180375 – If an externally-mastered user was created by an API and an email factor was required, when the user's email address was updated in the externally-mastered source, the previous email address was still active and authentication codes could still be sent to it.
- OKTA-182523 – If a user had email and another factor enrolled for an app-level MFA policy, selecting email as a second factor in Okta Mobile on iOS 11.4.1 displayed 'L10N error' instead of a localized message.
- OKTA-182572 – Users were blocked when upgrading to Okta Verify Push if there was an app sign-on policy that prompted for MFA but no sign-on policy that prompted for MFA.
- OKTA-182744 – The device trust client could not be installed on domain-joined computers when IdP discovery was enabled and an IdP routing rule was configured.
- OKTA-183830 – When the Okta Sign-In Widget was set to use a language other than English, and configured with IdP Discovery, the Next button in the identity first login form was not translated.
- OKTA-186441H – Users and admins were prompted with an "500 Internal Server Error" whenever they tried to access ServiceNow UD.
- OKTA-186530H – For MS Office apps on iOS devices, the end user flow failed when an App Sign On rule to “Block EAS” was above a Device Trust rule.
- OKTA-187161H – SCIM connectors implemented with new created apps did not work on Preview.
-
Amazon UK (OKTA-183801)
-
Boxed (OKTA-183746)
-
Cisco Partner Login (OKTA-183727)
-
Insightly (OKTA-184701)
-
MIBOR (OKTA-183652)
-
My Jive (OKTA-184864)
-
QuickBooks (OKTA-184915)
-
SHI (OKTA-183447)
-
ThrivePass (OKTA-183453)
-
WorkFusion Forum (OKTA-184843)
-
Micro Focus Connected MX (OKTA-184531)
- OKTA-96203 – The Approvals inbox showed All tasks completed message instead of Nothing to show message when there were no completed tasks.
- OKTA-161648 – IWA authentication failed for users who had the same UPN across multiple AD domains.
- OKTA-177378 – For apps with Provisioning enabled, when the Update application username on field was set to Create Only, it reverted to Create and Update when the page was refreshed.
- OKTA-178803 – Clicking on the U2F factor Setup button for the first time on the end user Settings page displayed a message saying the factor was not supported by the browser but the flow worked normally upon second click.
- OKTA-179236 – If an API PUT request to update a user profile omitted a sensitive property, that sensitive property was not properly removed from the user profile.
- OKTA-179407 – Some error pages containing non-lower ASCII characters were not localized.
- OKTA-179766 – While setting up a phone number for Forgot Password Text Message, users with a Mauritian phone number received an invalid number message at the first attempt but were able to send code to verify the number on the second attempt.
- OKTA-181454 – When a user belonged to an MFA Enrollment policy where the Email factor was Required and the SMS factor was Optional, calling the /api/v1/authn/endpoint (Primary Authentication with Trusted Application) to authenticate the user for the first time resulted in the user being prompted to setup an Optional factor instead of receiving the Email OTP.
- OKTA-182947 – Enabling the Self-Service Registration feature with the Add to Sign-In widget checkbox selected displayed a horizontal scroll bar on the end user Sign In page.
- OKTA-183411 – Active app approval templates were not deactivated when Self Service for the app was disabled.
- OKTA-183667 – Attempts to delete a Group Rule resulted in a 500 error.
- OKTA-183882 – Deactivated admins received user locked out emails.
- OKTA-184762 – IdP Discovery stopped the processing of policy rules for a policy if a rule was being evaluated without a user and the rule contained a user attribute condition.
-
Air Canada Travel Agency (OKTA-182036)
-
AmeriHome Correspondent Connect (OKTA-182918)
-
BetterLesson (OKTA-182740)
-
CitiManager (OKTA-182916)
-
Citrix XenApp (OKTA-182034)
-
Cloudability (OKTA-182781)
-
Critical Mention (OKTA-183368)
-
FileWave (OKTA-183176)
-
Hulu (OKTA-183663)
-
MailGun (OKTA-183490)
-
MedBridge (OKTA-184387)
-
MyRackspace Portal (OKTA-183616)
-
New York Times (OKTA-183479)
-
ProfitStars (OKTA-182311)
-
Verizon Wireless Business (OKTA-182929)
-
Virgin Pulse (OKTA-182902)
-
Yardi (OKTA-182913)
-
ZeroFox (OKTA-182915)
-
NetDocuments (OKTA-181142)
- OKTA-165796 – When the user had both Okta Verify with Push enabled and Duo Security, ignoring auto Push from Okta Verify to switch to Duo Security displayed an error message.
- OKTA-174349 – Applications configured as Administrator sets username and password prevented users from enabling Auto-launch option for that app.
- OKTA-177385 – Okta Expession Language was incorrectly treating the character "_" as a single wildcard character.
- OKTA-177768 – IdP Discovery policy routing rule did not display disabled app instances.
- OKTA-178568 – If an SMS factor was used within 30 seconds of the factor being auto-activated, authentication would fail without displaying an error.
- OKTA-179126 – IdP Discovery policy inactive rules could be re-activated if pointed to an inactive IdP.
- OKTA-179325 – AD-mastered users, who were logging into Okta for the first time and had not used their enrolled MFA factors to log in, were unable to add their phone number for SMS and Voice Call self-service password recovery options on the Welcome page.
- OKTA-165507 – The System Log displayed an incorrect time calculation when the selection included a daylight savings time change.
- OKTA-184793H – With Device Trust enabled and only modern auth client application configured for the Office 365 app, some iOS users whose devices were managed by AirWatch were unable to access O365 from native apps.
- Pantheon (OKTA-181500)
- OKTA-159579 – The San Diego Union-Tribune app had a different login URL in Okta Plugin for Microsoft Edge.
- OKTA-172164 – Invalid EL expressions for attributes and claims in API AM, OIDC, and SAML displayed a 500 error, rather than causing an exception and returning an appropriate error.
- OKTA-173204 – AD-mastered users were unable to edit their Mobile Phone configured with ALM in Okta even when the User Permission for the attribute was set to Read-Write.
- OKTA-174211 – Custom domains and Okta-hosted custom sign-in pages rendered a blank page in Internet Explorer when the domain was added to Compatibility View.
- OKTA-176335 – When configuring a Custom Domain and a Custom Email Sender using the same custom subdomain, the admin was directed to place both CNAME and TXT records to be the same subdomain host, violating RFC 1034 Sec. 3.6.2.
- OKTA-178982 – When assigning apps to a group, next page returned a 500 error if an admin didn't have rights to view all apps.
- OKTA-180364 – Ambiguous dialog box was displayed after a successful MFA transaction.
- OKTA-180642 – Changing the Okta username format from the Active Directory > Settings page in Okta failed to also update existing users' usernames.
- OKTA-182574 – Applying admin-managed tabs to all users did not send emails upon success or failure due to NPEs.
- OKTA-180932 – In rare cases, a del-Auth user appeared to be active when locked out and vice versa.
- 451Research (OKTA-179132)
- BB&T (OKTA-180836)
- BioCentury (OKTA-181201)
- GoGoAir (OKTA-180854)
- Hosting (OKTA-180837)
- Kentik (OKTA-180843)
- MIBOR (OKTA-181155)
- Morgan Stanley ClientServ (OKTA-180844)
- My Atlassian (OKTA-179519)
- Sailthru (OKTA-180418)
- UMR (OKTA-177842)
- US Bank - Pivot (OKTA-181941)
- VerticalResponse (OKTA-180437)
- Wayfair (OKTA-180840)
- WebEx Premium (OKTA-180841)
- Zappos (OKTA-180842)
- Illumio ASP (OKTA-182517)
- OKTA-165762 – AD profile attributes did not write back to UltiPro-mastered user profiles.
- OKTA-166150 – End user names did not display correctly in Dashboard > Tasks if the user account did not include user first and last names.
- OKTA-167437 – Some profile attributes for User Sync provisioning type for Office 365 could only be mapped using group app assignment (scope: Group) as opposed to user app assignment (scope: Personal).
- OKTA-167701, OKTA-170446 – In some cases, the user's manager attribute did not provision to Office 365 when the user's manager DN changed in AD.
- OKTA-170588 – The Timeout for API Calls threshold for Okta On-Premise Provisioning timed out before the set threshold.
- OKTA-170844 – Users received a blank page when logging into the Jonas Premier app using the Okta dashboard.
- OKTA-173525 – SAML docs were sometimes populated with incorrect Signature Algorithm certificates.
- OKTA-175838 – Group admins were unable to create API tokens because the Security tab was missing from the Okta admin dashboard.
- OKTA-178335 – Removed System Logs for granting refresh tokens in token requests with the refresh token grant type. This applies to both API Access Management and OpenID Connect.
- OKTA-178359 – Some group rules did not trigger after users were imported into Okta.
- OKTA-178522 – IDP Discovery routing rules deemed domains containing the special character "-" as invalid.
- OKTA-178978 – Provisioning sometimes failed during Okta service maintenance.
- OKTA-181649H – New users that were mastered in Google Suite, Workday, or Salesforce and subsequently provisioned from Okta into Active Directory, were not enabled in AD when AD password policy required more than 16 characters long passwords.
-
Admin America Participant (OKTA-179417)
-
AI Insight (OKTA-179419)
-
Amadeus Selling Platform Connect (OKTA-177982)
-
Ambassador (OKTA-179233)
-
BNY Mellon - Connect Portal (OKTA-179106)
-
Pond5 (OKTA-180160)
-
PPM Roadmap (OKTA-179413)
-
S&P Capital IQ (OKTA-178570)
-
Spectrum Time Warner Cable (OKTA-179415)
-
Staples NetXpress New Zealand (OKTA-179414)
-
Sysomos (OKTA-179340)
-
The Courier Mail (OKTA-179225)
-
The Economist (OKTA-179108)
-
WebStudy (OKTA-179412)
-
Zeplin (OKTA-179714)
-
Fuel Cycle (OKTA-179998)
-
Illumio ASP (OKTA-179985)
-
Spoke (www.askspoke.com) (OKTA-179597)
- OKTA-90737 – The Permission set for user assignments was not showing up for the Replicon app. For existing Replicon app instances please contact Okta support to upgrade to latest schema.
- OKTA-119389H – Imported users for the Org2Org app had mismatched username and email values.
- OKTA-166720 – Allow administrators to consent for Advanced API Access setting was not saved for O365 app’s API credentials, in cases where WS-Fed was used and set to MANUAL on the Sign On tab.
- OKTA-173411 – Reveal Password did not show the password for SWA apps when the user is logged in by external social login providers.
- OKTA-173928 – When the Do not display application icon to users option was unchecked on the General tab of an On-Prem SAML app, the On-Prem settings on the Provisioning tab disappeared.
- OKTA-174179 – Not all SuccessFactors user attributes were imported into Okta.
- OKTA-176035 – Users that were deleted from a Group that was managed by a rule, still showed up in the Group.
- OKTA-177400 – The Zendesk provisioning API failed and returned a 403 Forbidden error for some customers.
- OKTA-178619 – The API Access Management authorization server token preview resulted in an error when previewing a token for client credentials grant type.
- OKTA-179489H – Admin password reset functionality was disabled for LDA- mastered users when the Group Password Policy feature was enabled.
- OKTA-180446H – Setting up provisioning or imports for a new G Suite app instance failed. Testing API credentials for any existing G Suite instances returned a 503 Service unavailable error.
-
FedEx Canada (OKTA-177987)
-
MIBOR (OKTA-178869)
-
NatureBox (OKTA-177974)
-
VoterVoice (OKTA-177979)
-
WebEx (Cisco) (OKTA-178499)
- OKTA-131104 – For customers with G Suite, duplicate email accounts were configured in Gmail after Android users enrolled their device in OMM (work profile).
- OKTA-159102 – When a user launched an iOS app that uses Okta to log in, the Okta widget displayed Please enter a password as soon as it was tapped.
- OKTA-163843 – Okta unnecessarily provided information about specific browsers on all browsers when end users set up a Security Key (U2F) making the instructions confusing on some browsers.
- OKTA-166582 – When multiple SMS requests for MFA were sent within a 30 second window, the error message returned was SMS recently sent instead of Too many requests.
- OKTA-168180 – The AD Domain or AD Agent fields were missing in AD agent connect and disconnect System Log events.
- OKTA-168338 – The okta-signin-widget did not include the accept-language header when making an API call.
- OKTA-175427H – The IDP Discovery page did not redirect the user to the IDP defined in the Routing Rule on an SP initiated flow.
- OKTA-176556 – During Self Service Registration some user accounts defaulted to Staged instead of Pending user action status as expected.
- OKTA-177435 – Category name in the app list showed L10N_ERROR as a category.
- OKTA-178668 – The Delegated Authentication page did not load properly.
-
Apple Store (OKTA-177813)
-
Atlassian Cloud (OKTA-175339)
-
EdgeCast (OKTA-175363)
-
Qualtrics (OKTA-178233)
-
SallieMae (OKTA-173895)
-
UMR (OKTA-177991)
-
Unicorn HRO Customer Center (OKTA-177995)
-
UsabilityHub (OKTA-177376)
-
WebEx Premium (OKTA-173896)
- OKTA-124352 – It was possible to select an inactive PIV IdP for certificate-based login.
- OKTA-146511 – Attempting to activate Okta Verify by an email link or code after having already attempted activation by SMS link resulted in a 500 error instead of a proper error message.
- OKTA-156179 – The Workplace by Facebook Manager field was only updated following reassignment changes in AD/Okta, not for other changes.
- OKTA-156459 – User reactivation failed for customers using the Graph API provisioning for the Microsoft Office 365 app.
- OKTA-160214 – Attempts to enable provisioning for the JIRA On-Prem app failed with a 500 error.
- OKTA-164208 – Network Zones were not displayed properly under Security -> Delegated Authentication -> Network Zones in IE.
- OKTA-165596 – The Send Push Automatically checkbox was deselected when reopening a new IE browser with Update KB4096040 in Windows 7Pro-32Bit.
- OKTA-165636 – The Help Desk Admin role could incorrectly click the Groups link without receiving an error. However, when clicking on any of the groups listed, the admin would receive a 403 error.
- OKTA-165849 – RSA SecurID MFA enrollment in Okta carried over the FOB token into the PIN field (at the Enter a new PIN having from 4 to 8 digits prompt).
- OKTA-166847 – The Okta plugin continued to fill out forms with stored values for User/Name and Password fields beyond the initial login.
- OKTA-167553 – The text on the interstitial page appeared jumbled when using Firefox browser version 59.0.2.
- OKTA-167623 – Upgrading the IWA agent caused the Network Zones under IWA Settings to be cleared.
- OKTA-168428 – Some users who were deactivated in Okta were not deactivated in Workplace by Facebook.
- OKTA-168629 – Calls to API AM /authorize with an invalid okta_key parameter resulted in a 500 error.
- OKTA-168648 – No error was shown when user activation failed due to a session timeout.
- OKTA-169454 – Desktop - Windows traffic from Microsoft BITS/7.5 (Microsoft Background Intelligent Transfer Service) was incorrectly filtered as non-Windows traffic by Office365 Client Access Policies.
- OKTA-171775 – Admins given the right to only administer one specific app (specific-app admin role) were unable to access the Provisioning tab for that app.
- OKTA-172284 – The SuccessFactors personal email attribute was removed by an Okta Push operation.
- OKTA-172556 – The IWA pending account activation page did not show the Technical Contact email address.
- OKTA-174625 – Users could not be assigned the Silver Partner role in Salesforce.
- OKTA-175748 – Clicking OIDC default scopes in an Authorization Server (AS) policy rule, incorrectly added all scopes for a custom AS.
- OKTA-175919 – For orgs with subdomain names containing mixed cases, the banner prompting users to grant access to apps continued to display even after the user trusts the domain.
- OKTA-175991 – A 500 error was returned when adding more than one hundred network zones.
- OKTA-176329 – The ContactDirSyncMapping event was not recorded in the System Log.
- OKTA-176736 – The enum attribute did not display a zero value correctly in edit mode (Admin > Directory > Profile Editor > Profile > Edit Custom Attribute).
- OKTA-177400H – Zendesk Provisioning threw a 403 error after performing a Cloudfare migration.
-
Amazon DE (OKTA-175408)
-
CareFirst (OKTA-174918)
-
CB Insights (OKTA-175570)
-
Comcast Business (OKTA-176072)
-
CrowdStrike Support Portal (OKTA-176089)
-
GoDaddy (OKTA-175683)
-
IBM Cloud (OKTA-175745)
-
Kaspersky CompanyAccount (OKTA-174914)
-
MB Program Info (OKTA-173889)
-
Nielsen Answers (OKTA-176091)
-
NOW - NetApp (OKTA-173891)
-
OneHealthPort (OKTA-175767)
-
OpenTable (OKTA-173892)
-
Operative.One (OKTA-174243)
-
Peapod (OKTA-173890)
-
Proposify (OKTA-175784)
-
PsPrint (OKTA-173894)
-
Qlik (OKTA-175675)
-
SAP Support Portal (OKTA-176093)
-
Seeking Alpha (OKTA-173893)
-
ST Math (OKTA-175125)
-
trafalgar (OKTA-174916)
-
Clarizen (OKTA-175553)
-
SkyHigh (OKTA-175513)
- OKTA-159705 – Okta did not accept Thawte issued certificates.
- OKTA-162707 – The RADIUS log sometimes showed a NoHttpResponseException entry that was not a real error.
- OKTA-167438 – When users changed their secondary email address, this event did not display in the System Log.
- OKTA-167602 – When a user was deprovisioned from Box, and the file volume was high, the user deactivation failed because the associated file transfer timed out.
- OKTA-171890 – In some cases, when using combined values across groups with the O365 app assigned, removing the last group from a user also removed the O365 license.
- OKTA-171950 – If the redirect_uri limit was exceeded, an HTTP 500 error was returned.
- OKTA-172843H – Custom reports for Workday incremental imports sometimes failed, resulting in null custom attribute values.
- OKTA-174277 – Self-service registration returned an Internal Server Error for users reseting a password using the API activation token.
- OKTA-174659 – Okta to AD Push Groups operations for groups starting with "#" failed to link to AD groups.
- OKTA-175160 – When activating or deactivating the email factor, an event was not generated consistently in the MFA usage report.
- OKTA-175583H – Assigning a new version of an app binary file (.ipa) for a native app failed.
-
Absolute Console (OKTA-173828)
-
Alaska Air Group Credit Union (OKTA-173897)
-
America First Credit Union (OKTA-173877)
-
Benefit Administrator - Ameritas (OKTA-173898)
-
Commission Junction (OKTA-173899)
-
DealerRater (OKTA-173885)
-
Eden (OKTA-174921)
-
Fedex United Kingdom (OKTA-172898)
-
HM Revenue and Customs (HMRC) (OKTA-174740)
-
Hype Machine (OKTA-173886)
-
Jungle Disk (OKTA-173887)
-
McAfee Consumer (OKTA-173888)
-
MetLife Business Insurance (OKTA-174318)
-
MURAL (OKTA-174638)
-
Quickbooks (OKTA-174037)
-
SnapLogic (OKTA-174915)
-
SonicWall (OKTA-173831)
-
UltiPro (OKTA-172729)
-
Netskope (OKTA-170729)
- OKTA-132768 – Pre-activated end users who requested a password reset were not automatically sent an email from Okta advising them to contact their administrator, as expected. (Note: This issue is fixed. It was documented as a feature enhancement in error in 2018.17 release notes.)
- OKTA-156213 – RDP failed to connect to Windows Server 2016.
- OKTA-168217 – When using a voice call factor twice within a 30-second time period, the error message incorrectly displayed a internal server error instead of a Too Many Requests error.
- OKTA-168223 – The System Log did not display OpenID Connect App assignment and un-assignment events.
- OKTA-171665 – When authenticating with U2F, the login screen did not have the option Do not challenge me on this device for the next ....
- OKTA-171675 – When a group associated with the self-service registration policy was deleted, any subsequent attempts to make changes to the registration policy received a This group does not exist error message.
- OKTA-171680, OKTA-171750 – It was possible to create access policy rules that set refresh token inactivity expiration times to Unlimited.
- OKTA-172619 – In some real time sync configurations, Okta was showing duplicate users from Workday in the import tab.
-
Activist Insight (OKTA-172889)
-
Bloomberg (OKTA-173419)
-
CloudHealth (OKTA-172894)
-
Crunchbase (OKTA-173424)
-
eBay (OKTA-172962)
-
Instagram (OKTA-173825)
-
Jitterbit (OKTA-172563)
-
MoneyGram U.S. (OKTA-172893)
-
The Alabama Department of Revenue Motor Vehicle Division (OKTA-168849)
-
Tracker.com (OKTA-172886)
-
WOW! (OKTA-172888)
- OKTA-162610 – Device notification emails defaulted to the Pacific Time Zone in the message regardless of the user profile time zone setting.
- OKTA-162740 – Notification emails triggered when changing an admin's email address were not sent from the configured custom domain.
- OKTA-168452 – When using the Apple Search Ads app on the MSEdge browser, the Okta Plugin did not match the URL correctly.
- OKTA-170357 – When signing keys could not be generated for a new Authorization Server, the error message was not clear.
- OKTA-171394 – When an AD user was deactivated then reactivated from Okta, the user was reactivated in Okta but not in AD as expected.
- OKTA-172487 – Mappings from user.getInternalProperty("id") to the app Username attribute did not save correctly.
- OKTA-173166 – The Reports page did not display the Account Unlock counts in the SMS Usage Report.
-
AirWatch Admin Portal (OKTA-169991)
-
Apple MyAccess (OKTA-168961)
-
Apple MyAccess (OKTA-168961)
-
Capriccio Fuzion (OKTA-168950)
-
Capriccio Fuzion (OKTA-168950)
-
CloudFlare (OKTA-172484)
-
InMobi (OKTA-171429)
-
NetXpress (OKTA-172464)
-
WeightWatchers (OKTA-172465)
- OKTA-93349 – Super Admins were able to change the role of other Super Admins without notifying the affected party.
- OKTA-127830 – Default password policy settings were sometimes incorrectly applied when creating a user with a password.
- OKTA-139641 – The MFA Usage report did not display the date/time in the Last Enrolled tab.
- OKTA-158993 – Some users were prompted for MFA on a device after already selecting Do not challenge me on this device again on that device.
- OKTA-159102 – The Okta login page on iOS displayed a Please enter a password error as soon as users clicked on the password field.
- OKTA-159505 – Some attributes were missing in the RADIUS end user Client IP attributes list.
- OKTA-159631 – The Slack desktop application request for MFA sometimes went into a loop when users configured it to prompt for MFA on every sign-on.
- OKTA-165633 – Password sync was available for Workplace by Facebook which does not support it.
- OKTA-167565 – The password fields were missing from the Okta Welcome page, causing users to be unable to register their accounts.
- OKTA-169341 – Existing users were not prompted to enroll a Security Question and Answer when enabling Self-Service Account Unlock with recovery Security Question enabled.
- OKTA-171056 – Some OAuth 2.0/OIDC refresh tokens would expire early.
- OKTA-171385 – Saving User profiles with App Mastered Numerical Attributes containing a value resulted in a 403 response.
- OKTA-171533 – When more than 20 OIDC apps were added to an org, no more than 20 appeared in the Clients dropdown of the Token Preview screen.
- OKTA-171670 – The Sharepoint on-premises application was not respecting custom interstitial URL settings for the org.
- OKTA-171896 – The JetBrains OIN app was not added to the Okta Dashboard when the account was created on the fly.
-
Akamai EdgeControl (OKTA-170641)
-
American Airlines (OKTA-170444)
-
AppLovin (OKTA-171070)
-
Confluence (Atlassian) (OKTA-171922)
-
CoStar (OKTA-170333)
-
DocSend (OKTA-171575)
-
Email On Acid (OKTA-172478)
-
Freshdesk (OKTA-170270)
-
Goldman Sachs Research (OKTA-169178)
-
Hightail (OKTA-171579)
-
NGP VAN (OKTA-171573)
-
SmartyStreets (OKTA-171843)
-
Stampli (OKTA-170087)
-
United Airlines (OKTA-170452)
-
YouCanBook.me (OKTA-171900)
-
Sisense (OKTA-170701)
- OKTA-159522 – The Application report for the Radius app did not display all users assigned to the app.
- OKTA-161741 – The Billing Contact information in Account Settings could not be edited. This occurred only for Developer Paid editions.
- OKTA-162503 – The Okta Chrome browser plugin caused a DOM exception to appear in the Dev Console when debugging applications on pages that contained sandboxed iFrames.
- OKTA-162664 – Simultaneous updates made by multiple admins to change user membership on Okta mastered groups were overwritten by the last update.
- OKTA-163173 – Group Push: Pushing app Groups to Jive that already exist or already existed in Jive displayed a L10N_ERROR[app.api.error.update.group] error message.
- OKTA-163381 – When imported groups had names or descriptions with 1023 characters or longer, running an import from ServiceNow into Okta failed with a data exception and did not complete the import.
- OKTA-164390 – Group Search queries with underscores returned incorrect results.
- OKTA-166755 – Importing users from Kaleo OIN app through a CSV file failed.
- OKTA-167278 – Events returned from the /logs endpoint when using the until parameter were previously delayed by up to 1 second. To improve the performance of our System Log, queries to the /logs endpoint that include an until parameter may now return results that are delayed up to 10 seconds. When making requests with an until value that is near real-time, ensure that you allow enough of a buffer as to not miss events (e.g. 20s).
- OKTA-169479 – Using the Okta Plugin negatively impacted browser performance in some cases when working with pages that contained many forms.
- OKTA-172049H – A deleted user account could not be recreated.
-
Authorize.Net Merchants (OKTA-169901)
-
Choice Strategies (OKTA-168607)
-
SAP BusinessObjects (OKTA-169481)
-
Windows Dev Center (OKTA-169230)
- OKTA-154726 – Email as an authentication factor produced an error at enrollment for international users.
- OKTA-157884 – Delays were experienced when deleting users. As a result of the fix, one will notice a period of time between when the deletion was initiated and when it completes. During the period, the user will still be visible, but the deletion cannot be reversed.
- OKTA-163626 – During an import into Okta, an event was fired stating that an Okta-mastered group was removed. This event is incorrect, Okta-mastered groups should not be removed during an import and no events should have been fired.
- OKTA-166669 – A secondary domain could not be registered on a fresh install of AD Agent 3.4.12. This issue is fixed by AD Agent release 3.5.0.
- OKTA-167483 – OAuth 2.0 and OIDC requests made with redirect URLs that contained underscores in the domain name would result in an error.
- OKTA-168285 – Group rules only worked when first activated, and subsequently only when they were deactivated and reactivated.
- OKTA-170869H – After an Okta user was deleted in a Preview org, attempts to create an account with same username failed with an 'already exists' error.
-
iCloud (OKTA-168778)
-
S&P Capital IQ (OKTA-169177)
-
The Hive Community (OKTA-166736)
- OKTA-137758 – If the configured default IdP was set to inactive, Okta still used the inactive IdP as the primary endpoint for user authentications.
- OKTA-159216 – When setting up a SAML 2.0 App using the App Integration Wizard, the username defined in the Sign-On tab was overwritten by the default username under the General tab.
- OKTA-162620 – The French translation had errors in the enrollment Password Recovery Security question.
- OKTA-162633 – The German translation had errors in the activation email template.
- OKTA-163276 – Roles were not populated while importing users in the Netsuite app if the user account does not have a location attribute present on it.
- OKTA-164970 – Manual imports from ServiceNow UD failed with following error: Error while downloading all users: could not deserialize the cpc user string. Errors found while setting values for the app user. appUserId=null, errors=com.saasure.framework.validation.util.SimpleErrors: 1 errors Error in object 'appUser': codes [invalidValueTypeForProperty.appUser,invalidValueTypeForProperty]; arguments [company]; default message [Unsupported data type value for given key]. This error means some user has an unknown (new or modified) value for a dropdown list property such as Department, Cost Center, etc. To resolve this issue, click Applications > More > Refresh Application Data, and run the import again.
- OKTA-165675 – The Greek translation had errors on the Okta login screen.
- OKTA-166113 – Users were prompted for MFA for clients in ADFS zones where MFA was not required.
- OKTA-166330 – Some ADFS logins failed and required the user to refresh the page to receive the MFA challenge.
- OKTA-169410H – After new mobile devices are enrolled into OMM, whenever a device reports back device info using update device status api or response to device info command, the update fails due to null pointer exception.
-
Apple Search Ads (OKTA-168085)
-
AppRiver (OKTA-166853)
-
BootcampSpot v2 (OKTA-168448)
-
Envoy (OKTA-168089)
-
Gaggle (OKTA-167422)
-
Oh My Green (OKTA-168122)
-
ServiceNow UD (OKTA-166665)
-
Achievers.com (OKTA-167722)
- OKTA-19371 – The SAML RelayState app path contained an extra forward slash.
- OKTA-134551 – The attribute msExchHideFromAddressLists was not synchronized correctly from Active Directory.
- OKTA-151741 – For customers using the EA feature Graph API provisioning for Microsoft Office 365, provisioning users to the Microsoft Office 365 app failed with the error Unrecognized field "odata.metadata" (Class com.saasure.application.office365.msgraphapi.objects.api.User), not marked as ignorable.
- OKTA-155207 – After an admin was unable to create a user profile in Microsoft Office 365 for a user, the user could not be assigned to the supporting group.
- OKTA-156396 – When uploading an unexpired IdP certificate in Microsoft Internet Explorer 11, the message this certificate is expired displayed. The certificate worked as expected.
- OKTA-156475 – The Okta Browser Plugin froze when authenticating without a session. This was fixed by removing an extra slash in the URL path.
- OKTA-158355 – There were minor grammatical errors in the sign in message.
- OKTA-159022 – After provisioning users to the AWS SAML app, users did not have the AWS chiclet on their Dashboards.
- OKTA-159631 – Multifactor Authentication challenges were incorrectly repeated after a successful completion for the Slack Desktop app.
- OKTA-159745 – Group Push to the ServiceNow app failed for large groups containing thousands of users.
- OKTA-161715/OKTA-162648 – Using the Okta Plugin negatively impacted browser performance when working with forms that contained many password fields.
- OKTA-162796 – Setting the Sign On method to Users share a single username and password set by administrator caused a 400 bad request error on user assignment.
- OKTA-162952 – The Adobe Experience Manager app prompted for a new password suggestion instead of sign in information during a SP-initiated flow.
- OKTA-163013 – Internet Explorer did not display Group and Network Zone information in App level Sign On Rules section when editing.
- OKTA-163122 – Duplicate events were fired from a single profile push update.
- OKTA-163152 – When a user was removed from an Okta group and deactivated, then assigned to a different Okta group and reactivated, the reactivated user would still be a member of the OU associated to the original group in spite of the prior deletion from the group.
- OKTA-163408 – The footer on the Activation Failure page incorrectly displayed on two lines.
- OKTA-163411 – The Activation page was not correctly translated for the Japanese language.
- OKTA-165493 – A scheduled Group Push to the Slack app using a rule failed for large groups.
- OKTA-165624 – The welcome email for the Okta Developer Platform contained a broken link for an image.
- OKTA-165637 – Importing users from the Box app with no group memberships failed intermittently with a NullPointerException error.
- OKTA-165749 – The Multifactor page was blank in some customers' preview orgs.
- OKTA-166721 – The Edit button was not visible when customizing a SMS multifactor authentication factor in preview organizations.
- OKTA-166777 – On the Tasks page, provisioning tasks did not display correctly until the Filter button was clicked.
-
Adobe Licensing Website (OKTA-167246)
-
Apple ID (OKTA-167247)
-
Associated Bank (OKTA-166530)
-
In Honda (OKTA-165909)
-
iTunes Connect (OKTA-166342)
-
National Life Group Customers Login (OKTA-166528)
-
Premium Beat (OKTA-166550)
-
Ramp (OKTA-166533)
-
SchoolDude (OKTA-166531)
-
Societe Francaise du Radiotelephone (OKTA-167244)
-
SproutSocial (OKTA-167248)
- OKTA-88738 – Read-only admins were able to access email template settings and admin notification functions.
- OKTA-146365 – The Duo multifactor authentication factor was enforced when the factor enrollment rule was set to first time user is challenged for MFA even though the sign-on policy was set to Do not prompt for MFA.
- OKTA-152483 – App admins assigned to the RADIUS app only could not edit Settings in the RADIUS app Sign On tab. Admins assigned to all apps were not affected.
- OKTA-160718 – Okta MFA did not work during sign on for the Airwatch Admin Portal SAML app on iOS Mobile only.
- OKTA-162352 – Users logging in through ADFS login received an error if the ADFS app was configured for MFA with the default policy and with all factors as optional.
- OKTA-163379 – Token Preview incorrectly showed Refresh Token as a grant type option, when it is not a valid grant type.
- OKTA-163525 – In the Advanced Sign-On Settings for the Dropbox app, the instructions for the Silent Provisioning option incorrectly stated that Dropbox support always needed to be contacted to verify your domain.
- OKTA-163584 – Repushing a group that contains a member that already exists in the Jira On-Prem or the Jira Cloud apps, resulted in an End of File exception.
- OKTA-163667 – When one deprovisioning task was manually cleared for a user, all tasks for that user were also cleared.
- OKTA-165355 – After customizing the end user dashboard, admins did not receive an email confirmation that changes were activated, as indicated in the screen text.
- OKTA-165473 – Reauthentication failed for the SAML apps if IWA was configured.
- OKTA-166715H – The URL to sign on to the Salesforce app with MFA exceeded the maximum character length.
-
Barracuda MSP Online Backup (OKTA-164607)
-
Commuter Check Direct (OKTA-164137)
-
Egencia DE (OKTA-165131)
-
Egencia Ireland (OKTA-164381)
-
Egencia UK (OKTA-165133)
-
FunctionFox (OKTA-164382)
-
HelpSpot Userscape (OKTA-164385)
-
Prey (OKTA-164614)
-
Spirit Airlines (OKTA-164383)
-
Robin (OKTA-163897)
- OKTA-116182 – Provisioning to Atlassian Jira failed if the Base URL on the General tab contained spaces in the Jira Cloud and Jira On-Prem apps in Okta.
- OKTA-156901 – Custom magnification levels were reset to the default 100% in Microsoft Internet Explorer 11 after clicking the Web Version link in the Okta toolbar.
- OKTA-159593 – Imports of over 6000 users from SuccessFactors to the SuccessFactors app in Okta failed.
- OKTA-159681 – The State (state), Supervisory Organization (supervisoryOrg) and Business Unit (businessUnit) attributes were not imported from Workday into Okta.
- OKTA-159692 – App sign on rules to deny access to modern auth clients were not enforced on Microsoft Windows 10 operating systems, build 16299.64 and above.
- OKTA-160653 – Unnecessary System Log events appeared with null worker references when processing group memberships during Workday import.
- OKTA-160881 – With Enhanced Group Push, existing group members from linked groups were not correctly mastered by Okta.
- OKTA-162107 – New Active Directory-mastered users were not prompted to enroll in voice call option for recovery during their first sign in.
- OKTA-162752 – Imports for the SuccessFactors app failed with a null pointer exception.
- OKTA-163222 – Enabling provisioning for the GoToMeeting app failed with an HTTP error 400.
The following SWA apps were not working correctly and are now fixed.
-
Amazon CA (OKTA-163946)
-
Creditsafe NL (OKTA-163690)
-
Creditsafe UK (OKTA-163692)
-
Financial Times (OKTA-163576)
-
FINRA IARD (OKTA-163579)
-
FullContact Developer Portal (OKTA-162151)
-
OPP (OKTA-163577)
-
SunTrust - Enterprise Spend Platform (OKTA-163940)
-
Travitor (OKTA-163968)
-
Unity Ads (OKTA-161838)
-
Wrike (OKTA-161802)
- OKTA-105508 – When setting up SAML 2.0 apps, the SHA1 signing algorithm was displayed in the setup instructions during the app set up, but the SHA2 signing algorithm was displayed after the setup was complete.
- OKTA-152571 – IWA agent installation failed in some circumstances.
- OKTA-156049 – After creating an OAuth 2.0 Client with the Okta API that specifies a Client ID (client_id), the correct Client ID appears in the application list but an incorrect Client ID appeared on the Client Credentials screen.
- OKTA-157893 – Browser plugin dialog box images were not displayed correctly in the Firefox and Safari browsers for certain apps.
- OKTA-158334 – End users activated with Just In Time (JIT) provisioning received an incorrect list of multifactor authentication options when the end user was part of a group managed by group rules.
- OKTA-158918 – When changing a password, using the < and > characters caused an error with the message, The field must not contain HTML tags.
- OKTA-159012 – The Okta Usage report did not include authentication events for users who signed in to Okta exclusively through Okta Mobile.
- OKTA-159677 – In the AD Sync Password section on the Security > Delegated Authentication page, the Learn More link pointed to an invalid URL.
- OKTA-160505 – The View Logs link on User Profile pages (Directory > People > User) could not be accessed with the Internet Explorer browser.
- OKTA-160746 – On the Downloads page, the Version History link for the OPP Windows Agent pointed to an invalid URL.
- OKTA-162471 – For users provisioned as non-Okta-Mastered users, secondary emails were not available in Okta, as they were not mapped correctly into Okta.
- OKTA-164762H – After the initial password reset for new Workday-mastered users, users had to click the Home button a second time to see their apps, after entering the new password.
-
Cisco Partner Login (OKTA-162618)
-
my.MYOB (OKTA-160213)
-
ProtonMail (OKTA-162274)
- OKTA-136701 – Error messages when setting the minimum password age and password expires after parameters did not clarify that password expiration must be at least 1 day (24 hours) greater than minimum password age.
- OKTA-142177 – SP-initiated logins caused an error when MFA enrollment was required.
- OKTA-154419 – Reports available to an admin were not shown on the Reports page, if any usage statistics were unavailable.
- OKTA-158073 – Reactivating Zendesk app users with Okta usernames that were different from their email addresses failed.
- OKTA-159659 – Assignments for the Help Desk Admin, Mobile Admin, and API Access Management Admin were not recorded in the System Log.
- OKTA-161024 – Provisioning to the Rally app failed sporadically due to rate limiting concurrent updates.
- OKTA-161143 – During a group push in Active Directory, clicking the Push Group button and then clicking Save & add another button caused the Show More button to display multiple times.
- OKTA-162075 –The generated display name on the People page and the user profile was not used when a user's first and last names were null.
- OKTA-162476 – Logins via the Sign-In Widget (2.6.0) where the redirectURL parameter is utilized returned an HTTP 403 error to the user.
- OKTA-162682 – The Send push automatically check box did not remain checked when authenticating after logging out, then logging back into Okta for app sign on MFA and on Okta mobile.
-
Aurea: Messaging Solutions (OKTA-161163)
-
BulkSMS.com (OKTA-161975)
-
Groupon Merchants (OKTA-161710)
-
JIRA Cloud (Atlassian) (OKTA-158210)
-
Netflix (OKTA-158630)
-
Thomson Reuters Westlaw (OKTA-161417)
-
Xactly (OKTA-159865)
-
Zoominfo (OKTA-161673)
- OKTA-144982 – An incorrect error message was returned when a blank password was specified in a password reset request.
- OKTA-152324 – If administrators in an org with the Developer Console enabled used the Classic user interface instead, and had no apps assigned, they couldn’t access their own user home page.
- OKTA-154829 – Apps with long embed links did not display the link properly.
- OKTA-156484 – The System Log Display Name for Target User was shown as unknown for the user.authentication.sso event.
- OKTA-157287 – Pushing an updated version of the iOS app in the Okta Private App store did not trigger an update on enrolled devices, and the app could not be updated manually.
- OKTA-157741 – Some Internet Explorer users intermittently received a 400 Bad Request error when accessing an app with Inbound SAML.
- OKTA-158406 – When performing a group push to a SCIM app, some removed users were still pushed as members.
- OKTA-159679 – After successfully pushing a group containing a user to the JIRAcloud app, updating the group membership second time removed the initial user from the group in JIRA and displayed an error java.io.EOFException in Okta.
- OKTA-159705 – Provisioning to third-party applications that use a SSL certificate issued by DigiCert Global Root G2 root certificate authority might fail.
- OKTA-160214 – Provisioning to third-party applications that use a SSL certificate issued by DigiCert Trusted Root G4 root certificate authority might fail.
- OKTA-161847 – Imports failed when some data (worker/employment/workerstatus) was missing when using Workday's Last Day Worked feature.
-
3Rivers (OKTA-161181)
-
Archer (OKTA-160611)
-
Bannersnack (OKTA-159732)
-
Basecamp (OKTA-161375)
-
Cisco Partner Login (OKTA-159507)
-
Nearmap.com (AU) (OKTA-160555)
-
Sage People (OKTA-160582)
-
Stamps.com (OKTA-159856)
-
WooBox (OKTA-160394)
-
Workday Support (OKTA-160809)
-
EmployeeReferrals.com (OKTA-159623)
- OKTA-146499 – In the Chrome and IE browser with a low resolution screen, results dropped off the page during group assignment.
- OKTA-152222 – The Active Directory Federation Services (ADFS) app was not created with a default rule to prompt for factor with every sign-on.
- OKTA-155181 – Multifactor authentication with the Okta Windows Credential Provider did not load on servers with private IP addresses.
- OKTA-155395 – Pressing the Android icon during Okta Verify MFA enrollment while configuring Okta Mobile causes the app to become unresponsive
- OKTA-158142 – When reactivating users from Active Directory, users who had been assigned apps that were subsequently deleted could not be reactivated.
- OKTA-158227 – When selecting a state or region to define a geolocation zone, the names for selections within Israel were mislabeled.
- OKTA-159727 – In the Edge browser, adding MFA to a App Sign On Rule for the RADIUS application failed.
- OKTA-160585 – Authentication failed when users attempted to sign in to Microsoft Office 365 accounts using rich clients and a proxy that require a `Reason Phrase` in the HTTP response , for example Netskope.
-
Amazon UK (OKTA-159968)
-
BNY Mellon - Connect Portal (OKTA-159857)
-
Citrix RightSignature (OKTA-158953)
-
Consumer Reports (OKTA-159858)
-
Gleam (OKTA-159853)
-
GoToAssist (RemoteSupport/Service Desk/Monitoring) (OKTA-159120)
-
HRConnection by Zywave (OKTA-159076)
-
MyRouteOnline (OKTA-160408)
-
nCrypted Cloud (OKTA-159868)
-
OneSCM (OKTA-159854)
- OKTA-142230 – Under certain circumstances users could not sign on using the RADIUS app when a concurrent sign-on policy was specified for all sign ons.
- OKTA-151824 – When the email address of an Okta admin was changed, the subject of the confirming email incorrectly had the subject Notice of Pending email address change.
- OKTA-153216 – Successful password resets completed during an Okta Safe Mode event are valid after the safe mode ends.
- OKTA-153630 – After making a change to a password in some SWA apps, end users were not prompted to update the password for that app in Okta.
- OKTA-154808 – Some users could not access the self service page for an app and received the error: HTTP 500 Internal Server Error "com.saasure.framework.exception.RequestTimeoutException".
- OKTA-157116 – Some users could not sign in to the Microsoft Office 365 app, because the time stamp for the last password change was set to a date in the future.
- OKTA-157912 – Some users could not be provisioned to the Box app consistently and received a null error.
- OKTA-158144 – Some sign-ins failed or required multiple MFA login attempts when MFA step-up for App sign-on is enabled.
- OKTA-158215 – Some users could not be provisioned or were inaccurately provisioned to the PagerDuty app when multiple users in the org had common strings in their email addresses.
- OKTA-158353 – Errors on user profile updates and/or provisioning API credential validation while provisioning to CASB enabled Jive app
- OKTA-158557 – The Add App screen showed that a number of apps and categories were available, but none of them were actually available.
-
Bank of American Fork (OKTA-158943)
-
Burgiss: Cash Management (OKTA-158715)
-
GE Customer Online Management System (OKTA-158047)
-
GoToTraining (OKTA-158246)
-
Helpscout (OKTA-158946)
-
Hertz Gold Plus Rewards (OKTA-158042)
-
KnowBe4 (OKTA-158554)
-
my529 (OKTA-158398)
-
Nomadesk (OKTA-158652)
-
One Nevada Credit Union (OKTA-158043)
-
RainKing (OKTA-138203)
-
Small Improvements (OKTA-158040)
-
Wizbii (OKTA-158041)
-
Zions Bank (OKTA-158211)
- OKTA-139510 – The error message displayed when deleting a schema property did not accurately reflect the error condition.
- OKTA-148398 – The System Log showed inconsistencies when changing the Active Directory import schedule from the Settings screen of the Active Directory Integration.
- OKTA-150609 – Imports were failing from Samanage when enum constraints were dropped in Samanage.
- OKTA-151824 – After changing the email address for an Okta Admin or end user, the notification email was titled Notice of Pending email address change insead of Notice of email address change.
- OKTA-154851 – When editing a group rule to filter users based on the user's email address, the screen showed the user's second email address in the attribute. When saved, the correct attribute was used.
- OKTA-155395 – When configuring Okta Mobile, pressing the Android icon during Okta Verify MFA enrollment caused Okta Mobile to become unresponsive.
- OKTA-155549 – On the enduser dashboard, some apps were erroneously identified as bookmark apps.
- OKTA-155620 – Custom interstitial pages were not displayed when accessing the Worday app.
- OKTA-156450 – Changes to the user principal name attribute in Active Directory were not reflected in Okta when used for sign in.
- OKTA-156505 – You can now push the Slack display name. This requires enabling display name push in both your Slack tenant and provisioning settings.
- OKTA-156543 – In the Add Origin screen (Security > API > Trusted Origin), the placeholder text was unclear and now reads, Organization origin name.
- OKTA-157200 – List of user entries in People page was sorted incorrectly.
- OKTA-157378 – When an application was assigned for approval by a group and the group was subsequently deleted, any approver who was part of the deleted group received an error when attempting to approve any request on the Task page.
- OKTA-157749 – Long running operations in Slack caused a timeout on Okta's side
- OKTA-158144 – Sign ons failed or required multiple MFA sign on attempts when when MFA step-up for App sign on is enabled.
- OKTA-158330 – Setting the the proxy status to Any proxy in a dynamic network zone matched any IP addresses where the proxy type was null.
-
AmeriHome (OKTA-152960)
-
ConceptShare (OKTA-157115)
-
Conservice (OKTA-156764)
-
HRConnection by Zywave (OKTA-156621)
-
Ramp (OKTA-156548)
- OKTA-144300 – Some users could not sign in to Okta with Yubikey as a second MFA factor.
- OKTA-151766 – Apps assigned to the G Suite group were not assigned to users who were subsequently added to the group.
- OKTA-151780 – When users were reactivated in Active Directory, Microsoft Office 365 group licenses were not present after reactivation.
- OKTA-153118 – Users with Emoji characters in any of their properties were not filtered during imports from Slack.
-
Criteo (OKTA-156911)
-
HRConnection by Zywave (OKTA-156621)
-
Lakeland Bank (OKTA-156309)
-
MyPayFlex (OKTA-155692)
-
Qualtrics (OKTA-156307)
-
Rise Vision (OKTA-155588)
-
Texas Capital Bank (OKTA-155686)
- OKTA-142217 – After an LDAP provisioning error, the agent required a reboot and the LDAP configuration could not be updated.
- OKTA-142973 – Just In Time (JIT) provisioning was automatically enabled after modifying LDAP integrations settings.
- OKTA-145619 – Updates to group membership in Okta were not transferred to the G Suite app
- OKTA-146142 – Terminology was inconsistent on the Okta Verify IOS lock screen.
- OKTA-147299 – Okta authentication with JIT failed when the user id contained some non-ASCII extended characters.
- OKTA-147446 – The Microsoft Office 365 app fails with the error *400 You must provide a required property: Parameter name: usageLocation" after assigning users to the app with the provisioning type "Licenses/Roles Management Only."
- OKTA-148246 – Active Directory attributes with a custom attribute name were not pushed from Okta to the Salesforce app.
- OKTA-150613 – Setting the OAuth 2.0 Client application label to the maximum length of 100 returned an error.
- OKTA-150817 – Some MFA prompts during sign in were incorrectly translated into Dutch.
- OKTA-151008 – The password requirements message was incorrectly translated into Portuguese.
- OKTA-151547 – Users were prompted for an additional multifactor authentication factor every time they clicked the *Admin* button if MFA for Admins was enabled.
- OKTA-154178 – When unlocking an account with email, the message was not fully localized for the Greek language.
- OKTA-155582 – Retrieving the list of searchable fields for the System Log caused an error.
-
Alibaba Cloud (Aliyun) (OKTA-155251)
-
BatchGeo (OKTA-155250)
-
Carlson Wagonlit (OKTA-153912)
-
FINRA Web CRD (OKTA-155257)
-
Flonomics (OKTA-156082)
-
Forrester Research (OKTA-154089)
-
HRConnection by Zywave (OKTA-154688)
-
ISO PAAS (OKTA-155021)
-
J.Crew (OKTA-154970)
-
Optum Health Financial (OKTA-154972)
-
Public Service Credit Union (OKTA-155260)
-
SkillSurvey (OKTA-155619)
-
The Wall Street Journal (OKTA-155570)
-
Trade Me (OKTA-154702)
-
UPS CampusShip (OKTA-155427)
-
Wall Street Journal (OKTA-155472)
-
WorkflowMAX (OKTA-156305)
-
Zenni Optical (OKTA-155256)
-
AWS Redshift (OKTA-155698)
- OKTA-141778 – Some Workday provisioning events were not recorded in the System Log or in the App Assignment report.
- OKTA-144546 – Provisioning operations for the Rally app sometimes failed with concurrency conflict errors.
- OKTA-146471 – LDAP users without email addresses on an LDAP server could not be imported into Okta.
- OKTA-146784 – Users received a cryptic Network Error message when they entered invalid text in the domain field on the login screen.
- OKTA-147256 – Okta Verify did not show the time of the event when prompting the user to approve or deny unless the app was already open.
- OKTA-147764 – The VPN Required notification was not displayed when launching from the Okta Dashboard Launch pad.
- OKTA-150040 – System Log entries were missing when a user presses deny in Okta Verify push.
- OKTA-150846 – Users could not create OpenID Connect app instances under certain circumstances.
- OKTA-151817 – When performing a password sync, modules in which the user was enrolled were removed in the Litmos app.
- OKTA-153201 – Some events were not logged when an app is configured to use a custom error page.
- OKTA-153615 – Users could not bypass the MFA requirement when using the Okta Windows Credential Provider in some cases.
- OKTA-154044 – When performing a SP-initiated SAML login to the Salesforce app, the user was redirected to the Okta Dashboard instead of the Salesforce page if they authenticated by a smartcard or certificate.
- OKTA-154176 – The ResponseType was not validated in token preview when the GrantType is IMPLICIT.
- OKTA-154178 – The unlock account email message is updated for the Greek language during sign in.
- OKTA-155004 – Some error messages shown to end users were not localized.
-
AFS Analytics (OKTA-154699)
-
Avis (OKTA-153523)
-
Awesome Screenshot (OKTA-154700)
-
CalPERS (OKTA-154520)
-
Descartes MK Denial.com (OKTA-154514)
-
Instacart (OKTA-154696)
-
Truckstop.com (OKTA-153520)
-
Virgin America (OKTA-154692)
- OKTA-100304 – The security image was not displayed in the Microsoft Outlook desktop app.
- OKTA-131155 – Custom email domain validation failed when the name contained uppercase characters.
- OKTA-136392 – Approval tasks for the Android for Work app were counted, but not displayed.
- OKTA-143996 – The App Integration Wizard failed to upload logos.
- OKTA-144230 – The password field was not filled in for the MIBOR SWA app.
- OKTA-145574 – Unprovisioned users were not listed in some group listings.
- OKTA-148543 – When disconnecting a user profile from the Workday app, the screen prompts were unclear.
- OKTA-150747 – Admins could not delete a Network Zone after deleting an application Sign On policy.
- OKTA-151539 – Adding apps "on the fly" failed for the isaca.org and pmi.org.
- OKTA-151556 – Custom mappings for the Alias attribute were not respected when creating a new user in Salesforce.
- OKTA-151574 – Users could not sign in to the Ceridian HR/Payroll app with SWA.
- OKTA-151734 – The Roambi Business app failed with a verification error while setting up provisioning.
- OKTA-151757 – Users not assigned to the Microsoft Office 365 app received an error when accessing the app with an SP-initiated flow.
- OKTA-152395 – Social Authentication Redirect Callout flow sometimes returned invalid authorization codes.
- OKTA-152451 – When attempting to edit SAML settings in the App Integration Wizard, users received a blank page if the app was previously deactivated.
- OKTA-153219 – When creating a test SCIM app and configuring it with SCIM API and auth keys, users received a 500 error message.
-
American Academy of Actuaries (OKTA-153597)
-
Boston Private Bank: Online Banking (OKTA-153117)
-
Bupa (OKTA-153521)
-
Ceridian eReports (OKTA-153211)
-
Disqus (OKTA-152553)
-
Fidelity 401k (OKTA-153072)
-
FINRA (OKTA-153210)
-
Forticloud (OKTA-153204)
-
LeadMailbox (OKTA-152191)
-
Microsoft Online Services Admin (OKTA-153207)
-
Orbitz (OKTA-153522)
-
Panopto (OKTA-153114)
-
RealSelf (OKTA-153115)
-
The Standard (StanCorp Financial Group) (OKTA-153480)
-
Ticketmaster (OKTA-153594)
-
Twilio (OKTA-153386)
-
Wells Fargo (OKTA-152639)
-
ZeroCater (OKTA-152950)
-
Zopim Dashboard (OKTA-152989)
-
Replicon (OKTA-151782)
-
SpringCM (OKTA-153352)
2017 Production Releases
Okta Verify for Android 3.6.0 is now available as an APK file on the Downloads page (Settings > Downloads). This release is also available in the Google Play Store. In addition to the availability as an APK file, it contains support for TLS 1.1 and bug fixes. For more information on APK files, see Distributing Okta Android Apps in China.
The size limit on the CSV download of the System Log is increased from 100K to 200K.
Configuring an application or integration to use OpenID Connect ID tokens or Oauth 2.0 access tokens with the Early Access API Management feature can take a lot of trial-and-error. Okta has made it easier to choose configuration settings and see the resulting tokens in the Token Preview tab of the Authorization Server page.
Add values on the left side to see how they would affect the token on the right. All the fields are selection boxes except User. For User, type in the first few letters to see a choice of user names.
You can try out different combinations of values, and see the resulting tokens (or error messages). Once you've got the right combination, it's easy to configure your authorization server and other components. For more information see Test Your Authorization Server Configuration. ![]() Screenshot
Screenshot
The following legacy events are now available in the System Log:
- app.auth.slo.with_reason
- app.auth.slo.saml.malformed_request.invalid_type
- app.keys.clone_legacy
- app.keys.generate_legacy
- app.keys.rotate_legacy
When creating or editing an OpenID Connect app, there is a now button to copy the client credentials to the clipboard. For more information, see The OpenID Connect Wizard. ![]() Screenshot
Screenshot
Profile Master and User Life Cycle Management enhancements are Generally Available for all EMEA Cell 1 and US Cell 5 organizations and all new production organizations. This feature is available as Early Access for all remaining organizations and will be Generally Available for all organizations in February 2018. For details see Profile Master and User Lifecycle Management.
The Okta Application Network (OAN) includes more than 5,000 pre-integrated business and consumer apps. As Okta expands our integrations beyond Single Sign-on and Provisioning we are adding new integration types to the catalog, now named the Okta Integration Network (OIN). While the new OIN still provides apps, it now includes advanced application integrations.
When adding or editing a claim to an authorization server, the Include in Token Type options are updated. The new values are Always and Userinfo / id_token request. The default is Always for id tokens. For more information on these options, see Create Claims. ![]() Screenshot
Screenshot
Version 5.16.2 is available from the Edge store. This version fixes the following issues:
- After navigating to the login page and entering a username, the security image was not displayed
- Per-app MFA did not work through the plugin. The system kept prompting for MFA.
For history, see Browser Plugin Version History.
This update supports TLS version 1.2 encryption protocol to align with industry best practices and standards for security and data integrity.
For more information about the SharePoint People Picker, including requirements, see the Microsoft SharePoint On-Premises Deployment Guide. For history, see Sharepoint People Picker Agent Version History.
This Generally Available version of the Password Sync agent includes the following:
- Updates the minimum supported TLS version to 1.2
- Updates the minimum Windows Server version to Window Server 2008
- Changes to the default settings
For history, see Password Sync Version History.
Attribute mapping enhances the existing profile editor, by allowing you to manage individual attributes. You can use the attribute mapping screens exclusively or combined with the existing profile, as desired. This feature is now GA.
Attribute mapping contains the following enhancements:
- Individual mapping
- Support for enumerations
- A sample value appears automatically
- Warnings
- The fields are sorted
- A link to profile editor
- A Force Sync button that applies the mappings
- Delete and edit buttons for each attribute mapping
For detailed information, see Attribute Mapping.
![]() Screenshot
Screenshot
You can automatically send your users an email if their account becomes locked due to too many failed sign-in attempts. You can insert a link in the email to let users unlock their account. This feature is now GA.
For details, see Configure lockout settings. ![]() Screenshot
Screenshot
We have switched the provisioning endpoints for GoToMeeting in anticipation of their API changes scheduled for December 5, 2017. For details see GoToMeeting's Important Updates to Your Account.
There are three new sub-menus on the Provisioning page for an application. After enabling provisioning, there are groupings for To App, To Okta, and API Integration, as shown below. Previously, these pages were combined on one page. For details, see Provisioning and Deprovisioning.
This version supports the following:
- Support for adding Remember me cookie during JIRA logins.
- Fix for new sessions not being created for Jira and Confluence apps when an already logged in user re-authenticates with a new SAML assertion.
- SP-initiated flows are disabled for Confluence users that are not present in Okta.
For version history, see Confluence Authenticator Toolkit Version History and JIRA Authenticator Toolkit Version History.
Instance Level Del Auth moves Del Auth enablement from the org level (Security > Delegated Authentication) to the instance level (Directory > Directory Integrations). While preserving current Del Auth functionality, instance-level Del Auth is optimized for use in environments with multiple AD instances. It allows admins to delegate authentication on a per AD-instance level to support more granular authentication scenarios.
SuccessFactors can now be used as a Profile Master. Additionally, there are multiple fixes including improved incremental import support and pulling value names instead of ids for attribute values.
Admins now only receive notifications about locked-out users who are in the group, or groups that the Admin manages.
LDAP agent version 5.4.2 is now available. This version provides:
- Support for customers using Oracle Internet Directory
- Bug fixes
- Optimizations to:
- Incremental imports
- Agent installation
- Updated LDAP Agent default settings.
For agent upgrades, your current state of enablement is preserved.
For the version history, see Okta Java LDAP Agent Version History.
The System Log now tracks the following information for network zones:
- IP addresses
- IP ranges
- Blacklist status
Primary and secondary email addresses can be the same email id for a user.
Support for the Hungarian, Indonesian, Malaysian, Polish, Romanian, and Turkish languages for the email customization is now available to all customers in Beta format. For more information, see Configure the Display Language.
Okta Verify for Android 3.2.1 is now available as an APK file on the Downloads page. For more information, see Distributing Okta Android Apps in China.
- Active Directory Agent, version 3.4.9 provides the following:
- All the fixes and enhancements provided by Early Access (EA) versions from 3.4.4 to 3.4.8.
- Updating the minimum Windows Server version to 2008.
- Providing a fix for AD-mastered users that had issues signing in with passwords containing unicode characters.
- Updated AD Agent default settings. For agent upgrades, your current state of enablement is preserved.
For details see, Okta Active Directory Agent version history.
Now an error message appears if you try to verify when the Okta Verify passcode field is empty. ![]() Screenshot
Screenshot
Selecting the information icon or clicking the rule name in API Access Management polices displays the users and groups the rule applies to, as well as the scopes that are granted to those users and groups. For more information, see Create Access Policies. ![]() Screenshot.
Screenshot.
The Okta Password Sync Agent supports Transport Layer Security (TLS) v1.2.
Validation for the correct number of parameters is improved in functions in the Okta Expression Language.
DocuSign app now uses OAuth 2.0 for authentication instead of username/password authentication performed via X-DocuSign-Authentication header.
Updated translation in Push Verify Activation email templates.
Certificate issuance, enrollment, and revocation events for Okta Device Trust for Windows are now written to the System Log.
System logs now report the Subject in API Access Management and OpenID Connect access token and refresh token events in addition to clientId and orgId.
The Network tab is now the Networks tab.
Users with numerous apps can find an app more easily with the new Search bar that accepts app names and app instances. You can also complete more tasks directly on the page, such as assigning users and groups. Additionally, you can copy embedded links straight to the clipboard from specific apps—no need to hunt through the app list to capture them. This feature is now GA. This feature is available in Production for new orgs only. ![]() Screenshot
Screenshot
Group Push now supports the ability to link to existing groups in Box, G Suite, Jive and Active Directory. You can centrally manage these apps in Okta. While this option is currently only available for the listed 4 apps, Okta will periodically add this functionality to more and more provisioning-enabled apps. This feature is now GA. This feature is available in production for new orgs only. For details, see Using Group Push.
The Private App Store for Android (AfW) and iOS devices is now Generally Available. This feature allows admins to upload internally-developed native apps to Okta and distribute them to end users via Okta Mobility Management (OMM). For details, see Private App Store.
The flow of an end user's identity throughout the different stages of access is known as a user’s lifecycle. This release contains several enhancements to define the options that manage this cycle clearly.
- Simplified Import settings: Using a profile master necessitates a clear distinction between new and imported end users to prevent conflicts. Feedback from our users prompted improvements with matching rules, auto-confirmation and auto-activation settings.
- New lifecycle settings: When an end user is deactivated in a profile mastered app, admins can now set whether they are deactivated, suspended, or remain an active user in Okta.
This feature is now GA. This feature is available in production for new orgs only. For details see Profile Masters page.
This version includes internal updates and minor fixes. For agent version history, see SSO IWA Web App Version History.
You can now specify that Workday paginated reports can behave as non-paginated reports. This allows scheduled imports run faster and ensures that the report is only called for a single user during real time sync.
*Added after release.
The Microsoft Edge browser is supported by Okta with the Okta Secure Web Authentication Plug-in v5.16.0. The plugin is available on the end-user Dashboard and the Admin Downloads page. For version history, see Browser Plugin Version History.
Firefox plugin version 5.15.3 is now GA for all orgs.
This version provides support for the latest Firefox web extension framework. There is no UI impact for customers; however, they must have this version installed as of Firefox version 57 (released on November 14, 2017).
Note: When the Okta plugin version 5.15.3 is installed, Firefox version 53 or earlier does not support single sign-on to apps through Basic Authentication. If you have any questions or concerns following the upgrade, contact Okta Support. For version history, see Browser Plugin Version History.
System Log entries related to refresh tokens in API Access Management and OpenID Connect now correctly log the clientIds and the number of tokens which were revoked.
Okta Device Trust for Windows authentication events are now written to the System Log.
The Workplace by Facebook integration is enabled for Universal Directory and is enhanced by additional properties in the User Profile. See Workplace by Facebook Provisioning Guide.
We have added the ${recoveryToken} variable to the Password Reset by Admin email template. See Customizing Email Templates for more information about email templates.
The option to change a linked group in one operation is no longer available. You must first unlink the group and then recreate the link to a different group.![]() Screenshot
Screenshot
Support for the Greek language for the end user experience is now available to all customers in Beta format. You can select the default language preference for your entire org, and your end users can select a different language preference for their own experience. The end user's preference overrides the language set for the org. For more information, see Configure the Display Language.
Admins can unlink a pushed group and remove any Group Push mappings that were created by Group Push rules. For more information, see Using Group Push.
When using Group Push, you can relink to a group that you previously deleted with the leave the group in the target app option without reimporting the group from the target app.
There are additional System Log descriptions for app approval workflow events. For a list of these events, see System Log Entries.
We now allow admins to provide unique SP Entity ID and ACS URL values when configuring SAML for Atlassian Cloud (Atlassian Jira and Confluence). This is done in preparation for upcoming SAML related changes from Atlassian; for more details on the changes please refer to our Atlassian Cloud SAML Configuration Guide.
You can now configure the RADIUS application to allow end users to submit a password and a second MFA factor, such as a security token, in a single request. The password and the second MFA factor are separated by a comma. For information on setting up and using this feature, see Advanced RADIUS Settings. ![]() Screenshot
Screenshot
Several labels and messages localized in the Italian language have been improved.
Group processing errors are tracked in the System Log. If a group rule evaluation results in an exception for a user, it's tracked in the log.
The maximum configured SAML attribute value is increased to 1024 characters.
The password complexity requirements are more fully explained on the Sign In screen. ![]() Screenshot
Screenshot
Administrators can exclude first names, last names, or both as a password complexity requirement by checking options in the Password Settings section for a policy on the Authentication page. For more information, see Complexity Requirements. ![]() Screenshot
Screenshot
In order to protect the service for all customers, Okta enforces concurrent rate limits starting with this release. Concurrent limits are distinct from the org-wide, per-minute API rate limits.
For concurrent rate limits, traffic is measured in three different areas. Counts in one area aren't included in counts for the other two:
- For agent traffic, Okta measured each org's traffic and set the limit above the highest usage in the last four weeks.
- For Office 365 traffic, the limit is 75 concurrent transactions per org.
- For all other traffic including API requests, the limit is 75 concurrent transactions per org.
Okta has verified that these limits are sufficient based on current usage or grandfathered higher limits for those orgs that have historically exceeded this limit.
The first request to exceed the concurrent limit returns an HTTP 429 error, and the first error every 60 seconds is written to the log. Reporting concurrent rate limits once a minute keeps log volume manageable.
For details on the limits, see Concurrent Rate Limits. The Okta System Log includes entries for errors resulting from too many concurrent requests.
Okta enforces a maximum subdomain length of 57 characters when creating new Okta orgs.
To improve clarity, minor changes were made to the email that Okta automatically sends when end users sign into Okta from a new or unrecognized device.
Okta has made the following enhancements to the System Log:
- Authentication failures are recorded when an app requires MFA and a user doesn’t have any MFA factors set.
- When an end user tries to access an app that has not been assigned to them, the System Log now records the app name as a target.
The union of group assignments allows you to take advantage of group prioritization and the attributes they contain. For end users belonging to multiple groups, their attributes can either be combined from string array values across groups, or set to honor the highest priority group. This feature is now Generally Available (GA). For more information, see Combine Values across Groups.
OpenID Connect scopes are returned from requests to `/api/v1/authorizationServers/:authorizationServerID/scopes’. You can edit scope descriptions in the Okta user interface or via the API. For more information on scopes, see Create Scopes. For information on using the Okta API with an authorization server, see OAuth 2.0 API.
Admins can reset passwords for AD-mastered users with the same easy process already in place for Okta-mastered users. For details, see Manage self-service password reset.
The new Help Desk Administrator role is now Generally Available. This role can perform common help desk actions. This role has a reduced set of permissions and promotes good security practices by not granting unnecessary permissions to help desk personnel.
Note that you cannot assign permissions to the Help Desk administrator role selectively. Instead, it has these fixed permissions:
- Reset Password
- Reset Multifactor Authentication
- Unlock Account
- Clear User Session
For more information, see Help Desk Administrator role.
You can now configure Advanced API Access for Office 365 instances by using the Sign On tab. This feature enables more robust provisioning functionality, and in the future will support new types of chiclets and functionality for Office 365. ![]() Screenshot
Screenshot
- To allow you to scan System Log events faster, the 20-character alphanumeric ID attribute for the actor and target fields of an event is no longer displayed. You can still access ID attributes by expanding individual events.
- The checkOSXAccessEligibility event is no longer logged to the System Log.
All group rules are processed for a user, even if one or more rules fail.
Support for the Turkish language for the end user experience is now available to all customers in Beta format. You can select the default language preference for your entire org, and your end users can select a different language preference for their own experience. The end user's preference overrides the language set for the org. For more information, see Configure the Display Language.
Until now, the reset password link in the Password Reset by Admin email redirected end users to the previous version (deprecated) of the Okta Sign In page. Now the link redirects end users to the current Okta Sign In screen if the template has not been customized. If the template was customized, you must update the link URL to ${resetPasswordLink} if you want to ensure that end users are redirected to the current Sign In page.
Note: A previous version of this announcement specified an incorrect link URL. The URL shown above is correct.
The text in standard Okta email templates that specifies when links expire now displays in the language set by the end user's locale attribute. To change custom templates to match this behavior, see Functions. Also, for consistency, all standard templates use the same function for temporary links.
Okta People Picker for Sharepoint agent version 2.2 is now available. This release includes the following:
-
Fixes an issue where users were unable to create a SharePoint site after People Picker for Sharepoint version 2.0 was installed.
-
Includes a PowerShell script to create the Sharepoint trusted token issuer in the downloadable Okta People Picker for Sharepoint packages.
-
Includes updated setup instructions for the SharePoint (On-Premise) application to indicate that the PowerShell script is now available inside the downloadable Sharepoint package.
For version history, see Sharepoint People Picker Agent history.
This feature is now Generally Available. Admins now have more options for specifying the mobile client types allowed to access Microsoft Office 365 Exchange ActiveSync from native applications. ![]() Screenshot
Screenshot
For details, see Configuring Rules for Office 365 Client Access Policies.
You can disable the use of email for initiating account recovery flows. At least one group password policy is required to make this specification.
There is now a link from a User Profile page (Directory > People > <username>) that takes you directly to the System Log with a prepopulated search query for all events related to that user. ![]() Screenshot:
Screenshot:
When a user logs in from OWA or any Office 365 web app, they are redirected to Okta to login. The user does not have to type their username as it is now automatically populated with the Okta username resolved from Office 365. Note that the username is only populated after a user has successfully authenticated at least once on the device. This feature is now Generally Available.
We have improved the performance of our Okta Usage Report by removing the detailed Preview section of the UI. Simply enter your filter criteria, then click Download CSV to download your data and view the report. For details about Okta Reports, see Reports.
If you have enabled Okta Mobility Management (OMM) enrollment through Android for Work, you can now configure a passcode policy for your Android 7.0+ end users' work profiles. You can set this policy in addition to or instead of a device passcode policy. This allows you to set a more secure policy for accessing work resources than for accessing personal apps and data. For details, see Configure a work profile passcode policy.
- We've consolidated and simplified the overall look and feel of the System Log.
- System Log values are no longer truncated in the UI.
- The Event Type field is no longer displayed on the main System Log page. Event Types are now visible by expanding an event.
For more details, see System Log.![]() Screenshot
Screenshot
You can now customize the email that is sent when LDAP-mastered users attemt to reset a forgotten password and the request is denied. This customization has been available for Active Directory and Okta-mastered users. Additionally, the subject line is standardized for allowed and denied forgot password reset emails for both LDAP and Okta-mastered users. For more information, Email and SMS Options.
You can now optionally define a regular expression when adding an Okta Template Plugin app. Regular expressions improve app security by creating a whitelist that matches patterns that you define. For more information, see Configuring Okta Template App and Plugin Template App.
![]() Screenshot
Screenshot
The System Log now includes information about the duration of each Delegated Authentication (Del Auth) request to help admins identify bottlenecks in the Active Directory (AD) Del Auth pipeline. The Del Auth System Log events now include times in milliseconds for:
- delAuthTimeTotal: The total time spent for Del Auth in Okta. This time consists of the total time at the agent and the queue wait time in Okta before an agent starts processing the request. The queue wait times can be high if there are not enough agents to serve requests.
- delAuthTimeSpentAtAgent: The total time the agent spent processing the request. This includes the time spent at the Domain Controller.
- delAuthTimeSpentAtDomainController: The time spent at the Domain Controller.
For information about the System Log, see Accessing the System Log.
Note: You must be using AD agent version 3.1.0 or higher to use this feature.
You can now customize the email template for Self-Service Unlock when Account is not Locked. For more information, see Customize the text of an email template. ![]() Screenshot
Screenshot
Incremental imports improve performance by only importing users that were created, updated, or deleted since your last import.
Okta now supports incremental imports for the following application integrations:
- SuccessFactors
- ServiceNow UD
- SmartRecruiters
The option for enabling LDAP Profile mastering is now on the LDAP Settings > Import Settings page. ![]() Screenshot
Screenshot
The IWA Web agent 1.10.3 is now Generally Available. This version restores support for Windows Server 2008. Please refer to IWA Web App Version History for more details about the change and Configuring Desktop SSO documentation for a complete list of supported platforms.
Okta sign in now uses version 2.6 of the Duo SDK. For more information on Duo, see Configuring Duo Security.
The Okta RADIUS server agent version 2.7.0 is now Generally Available. This version contains better logging, improved queue management, packet duplication fixes, and many performance optimizations. Windows event logs are not created by default. This version supports the RADIUS Generic App and Amazon Workspace App. For the version history, see Okta RADIUS Server Agent Version History.
Okta has improved the messages returned with some error codes for OpenID Connect and OAuth 2.0 client apps using the [/oauth2/v1/clients](/docs/api/resources/oauth-clients.html) and [/api/v1/apps](/docs/api/resources/apps.html) endpoints.
Okta plugin version 5.14.0 for the Chrome browser includes improvements to help prevent memory leaks. For version history, see Browser Plugin Version History.
Okta provides a preconfigured Custom Authorization Server named default. This default authorization server includes a basic access policy and rule, which you can edit to control access. It allows you to specify default instead of the authorizationServerId in requests to it:
- https://{YourOktaOrg}}/api/v1/authorizationServers/default for a default Authorization Server
- https://{YourOktaOrg}}/api/v1/authorizationServers/:authorizationServerId for other Custom Authorization Servers
For more information, see API Access Management.
OpenID Connect, which uses the Okta Authorization Server, can retrieve application groups for use in tokens. Previously, application groups could only be retrieved with the Custom Authorization Server.
You can use the Okta Expression Language getFilteredGroups to retrieve application groups.
OAuth 2.0 clients now support configuration of the web application type to use a client_credential grant type. This allows you to use one client_id for an application that needs to make user-specific calls and backend calls for data. For information on grant types, see App Wizard - Procedures.
The debug section of the System Log v2 now contains a list of the names of changed properties.
SAML forceAuthN reauthentication flows always prompt for both the user name and password.
There is a new LDAP agent version 5.3.12 with updated default settings. For agent version history, see LDAP agent history.
The simplified Android for Work setup wizard that removes the dependency on G Suite accounts is now Generally Available. For more information, see Setting up Android for Work in Okta.
Beginning with Okta Mobile for Android 2.16.0, we introduced an improved Okta Mobility Management (OMM) enrollment flow that clarifies which type of data is private and which is company-accessible. This enrollment flow is now Generally Available.![]() Screenshot
Screenshot
The ability to customize expired password flows to redirect end users to a specified website instead of the default Okta expired password form is now Generally Available.
For details, see Expired Password. ![]() Screenshot
Screenshot
The ability to generate a certificate with a specified validity period (see the Apps API and IdentityProviders API ) is now Generally Available. OpenID Connect and API Access Management are built on this feature.
OpenID Connect is a simple identity layer on top of the OAuth 2.0 protocol, which allows computing clients to verify the identity of an end user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the end user in an interoperable and RESTlike manner. In technical terms, OpenID Connect specifies a RESTful HTTP API, using JSON as a data format.
OpenID Connect allows a range of clients, including Web-based, mobile, and JavaScript clients, to request and receive information about authenticated sessions and end users. The specification suite is extensible, supporting optional features such as encryption of identity data, discovery of OpenID Providers, and session management.
Okta is certified for OpenID Connect. For more information, see OpenID Connect and Okta.
To improve performance with long lists in the Zendesk SAML app, the Edit Group Assignment page now supports paging.
You can now blacklist entire zones to deny clients from these zones access to any URL for the org. This feature is Generally Available. For more information, see Network.
We have enhanced our Workday integration to support Profile Updates. For more information about Workday provisioning, see the Workday Provisioning Guide.
The maximum number of network zones is increased to 5000 legacy network zones. For more information, see Network Zones.
The agent status indicator on the Settings page for an agent now refreshes every 30 seconds instead of every 5 seconds. This applies to Active Directory and LDAP agents.
The message that displays when an end user enters an invalid password now includes password age violations.
Bug fix for agent installation failure when an Internet Explorer proxy was in use. For version history, see On Premises Provisioning Agent and SDK Version History.
We’ve enhanced our System Log to take advantage of our new Network Zones feature. Admins can now hover over an IP address that's part of an event and navigate through the series of menus to add that IP address to either the gateway or proxy list of IP addresses. ![]() Screenshot
Screenshot
Through mobile policy rules for iOS and OS X devices (Devices > Mobile Policies), you can now disable the Wipe All Device Data option located on the Device Attributes page. Devices that are already enrolled in OMM are not affected by changes to this setting. For details, see Disable Device Wipe permission. ![]() Screenshot
Screenshot
New Okta Security menus, redesigned based on your feedback, are now available in Preview. The new menu architecture provides a more intuitive configuration and management experience. For details, see The Security menu is changing.
SAML support for Amazon Web Services (AWS) with multiple accounts allows you to set up a single chiclet to access multiple AWS accounts. You no longer have to set up multiple AWS chiclets in Okta for your end users. For details, see the AWS SAML Guide.
When adding a SAML app, you can configure multiple ACS URLs to support apps capable of choosing where the SAML response is sent. This feature is now Generally Available. For more information, see Using the App Integration Wizard.![]() Screenshot
Screenshot
Our Universal Directory integration with ServiceNow is now Generally Available. For details, see the ServiceNow Provisioning Guide.
You can now specify the minimum age of end-user passwords in Active Directory Group Password policies. ![]() Screenshot
Screenshot
A new Teams chiclet is available under the General tab for the Microsoft Office 365 app. To enable this chiclet, see Enable Microsoft Office Chiclets: ![]() Screenshot
Screenshot
The Application Page contains usability improvements based on customer feedback. We’ve refined our Search to use app instance names. The page default app list is now sorted by name; previously, it was sorted by app type and name. For more details about search, see The Applications Page.
- The event log for OMM commands displays user, device, and policy information related to the command.
- SysLog 1.0 and 2.0 track key rotation, key generation, and key cloning.
You can now customize the placeholder text that appears in dialog boxes when end users click account recovery links on the Sign-In page. For details, see Customize the placeholder text in account recovery dialog boxes. ![]() Screenshot
Screenshot
You can now customize the text of the help link on the Sign-In page. Clicking the link reveals account recovery options.
For details, see Customize Sign-In page headings and links. ![]() Screenshot
Screenshot
The Mobile Policies and Wifi config security options are now only available on the Devices menu, as shown below. Previously, they were also available on the Security menu. For details, see the Devices menu.
To allow Okta to grant authorization requests to apps that do not specify scopes on an authorization request, you can now configure scopes as defaults. If the client omits the scope parameter in an authorization request, Okta returns all default scopes in the Access Token that are permitted by the access policy rule. For details, see Create Scopes.
![]() Screenshot
Screenshot
The wizard for creating an OpenID Connect app has been improved and consolidatedonto a single screen. ![]() Screenshot
Screenshot
The Settings Page for AD-mastered users matches the Settings Page for Okta-mastered users to show the security question whether or not password reset or self-service unlock is available. ![]() Screenshot
Screenshot
Okta plugin version 5.12.0 is GA for the Chrome browser. This version updates how we describe the plugin in the Chrome web store, and provides several internal improvements. For version history, see Browser Plugin Version History.
Query string is now supported in the definition of an IdP Login URL:
- The IDP Login URL field in the Add/Edit Endpoint wizard.
- The IdP Single Sign-On URL for Inbound SAML. Reserved SAML parameters (SAMLRequest, RelayState, SigAlg, Signature) in the query strings are ignored.
Buttons on the People page for individuals are consolidated. If one or more actions are available, individual buttons appear. If three or more actions are available, a single button for a primary action appears adjacent to a More Actions button containing other available actions.
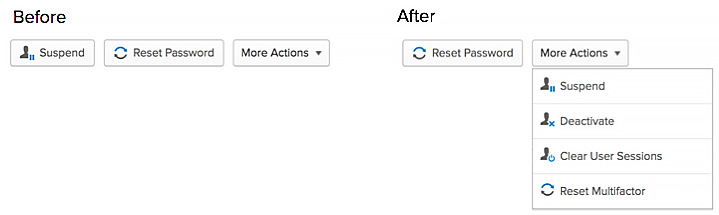
The Okta Java LDAP agent version 5.3.10 is Generally Available. This version provides various improvements to the agent log, as well as fixes to the following issues:
- Imports from LDAP failed in some orgs due to way the Okta LDAP agent handled unicode characters.
- Imports from LDAP failed in some orgs due to randomly dropped connections between the LDAP agent and Okta.
- We have finished migrating all customers to our enhanced System Log as part of our on-going GA rollout. With this release, when navigating to the System Log in your Okta Administrator Dashboard, all orgs will now see the new System Log.
- We have enhanced our System Log by logging an event (security.session.detect_client_roaming) when a session roaming event is detected.
- The Okta Expression Language function getFilteredGroups events can be tracked with the /api/v1/events call, in addition to tracking in System Log v2.
- There is additional logging for an invalid OAuth 2.0 client. If we detect five or more consecutive authentication attempts with the wrong client secret, Okta logs the events as suspicious:
- The requests may be to any OAuth 2.0 endpoint that accepts client credentials.
- The counter resets after 14 days of no invalid authentication attempts, or after a successful authentication..
- The message is Multiple requests with invalid client secret for client id.
When configuring an LDAP provisioning group, you must now enter a DN attribute in the Provisioning Destination DN field to specify the container in which new users are created in LDAP (Directory > Groups > LDAP > Manage Directories). Before this change, leaving this field unpopulated meant that Okta automatically created new users in the container specified in the User Search Base field (Directory > Directory Integrations > LDAP > Settings > LDAP Configuration). This fallback method may have produced unexpected results. For more information, see Groups.
When configuring an authorization server, you can now specify when ID token claims are included in ID tokens sent from an authorization server. For details, see Create Claims.
The Okta screens contain additional links. There is a link to the Okta Trust page from the bottom of the screen and the word Okta at the left of the menu bar is now a link to the Dashboard. Additionally, any links from an Admin banner page open in a new window by default.
 The word Okta is a link.
The word Okta is a link.
The Group Password Policy feature is now GA. For details, see Security Policies.
The Group Administrator role, previously known as the User Administrator role, is Generally Available. This role provides granular people management features and has enhanced capabilities for managing users within groups to which they are scoped. Super Admins can assign this role to isolate control over certain groups and teams within their organization. For details, see The Group Admin Role.
We are switching from the SHA-1 signature algorithm to the SHA-256 algorithm for signing assertions used to sign in to Microsoft Office apps, both for browser-based and thick client use cases.
Note: This is a phased rollout to Production that is expected to be complete by 2017.26.
Our powerful new Universal Directory (UD) integration with NetSuite is now GA. For details, see the NetSuite Provisioning Guide.
The enhanced Application Page Search is now GA. If your org has 50+ apps, you can now use a Search bar that accepts app names and instances. You can also complete more tasks directly on the page, such as assigning users and groups. Finally, you can copy embedded links straight to the clipboard from specific apps without the need to scroll through the app list to find them.
An enhanced app assignment screen is available for all preview orgs. You can toggle between people and groups on the same screen, view an error message if an assignment cannot be completed, and select Assign to people or Assign to groups from the Assign button, as shown below. For details, see Assign Applications on the Using the Applications Page.
You can unlock your user accounts in bulk in the same way that you can reset passwords and MFA in bulk. For details, see Unlock User Accounts in Bulk.
Our new provisioning integration with SmartRecruiters is now GA and supports the following features:
- Import New Users
- Push New Users
- Push Profile Updates
- Push User Deactivation
- Reactivate Users
For details, see the SmartRecruiters Provisioning Guide.
Authentication whitelisting and blacklisting based on Network zones is now Generally Available (GA). Network zones are sets of IP address ranges. You can use this feature in policies, application sign-in rules, and VPN notifications. This expands the use of Gateway IP Addresses. For more information, see Network. ![]() Screenshot
Screenshot
You can now disable the various methods your end users can use to request apps. For details, see Access Request Workflow.
![]() Screenshot
Screenshot
The following message now displays in the end users' Display Language setting if they have not specified a language preference.
We have updated the Okta Confluence Authenticator to version 2.0.5. This version adds support for custom base URLs (for example, http://confluence.onprem.com/my-confluence). For version history, see the Okta Confluence Authenticator Version History.
As both the JIRA Authenticator and the Confluence Authenticator are built on the Okta SAML Toolkit for Java, all three components are incremented to version 2.0.5 to maintain version consistency. For more details on these integrations, see Using the Confluence On Premises SAML App and Using the JIRA On-Premises SAML App. We strongly recommend that customers download and upgrade the latest SAML toolkit and the relevant Jira or Confluence authenticators. You can access all of these tools from Settings > Downloads.
Use the Okta Expression Language function getFilteredGroups to create a list of groups to which the current member belongs. With such a list you can, for example, create claims in Access Tokens and ID Tokens based on the groups. For details, see Group Functions.
The requirement that the Universal Directory locale property can only contain ISO/SCIM locale values is enforced for all new app instances. For details of this requirement, see UD Enforcement of ISO-compliant Locale Values.
You can use the login_hint property on the OAuth 2.0 API (/oauth2/:authorizationServerId/v1/authorize) to populate a username when prompting for authentication.
We have updated the following Okta authenticators:
- Okta JIRA Authenticator to version 1.0.15 for the JIRA On-Premises app version 6.x.x.
- Okta JIRA Authenticator to version 2.0.4 for the JIRA On-Premises app version 7.x.x
- Okta Confluence Authenticator to version 2.0.4 for the Confluence On-Premises SAML app
- Okta SAML Toolkit for Java to version 2.0.4
We strongly recommend that you download and upgrade to the latest SAML toolkit and the necessary Jira or Confluence authenticators. You can access all of these tools from the Okta Downloads page (Settings > Downloads). For version history, see Version History Tables.
You can now use an HTTP redirect for SAML single log-out requests.
The ServiceNow SAML application now supports Single Logout (SLO). This is an optional feature, and it is not enabled by default. To set up SLO for ServiceNow, follow the steps in the ServiceNow SAML guide.
We have updated our Jira and Confluence Cloud provisioning integrations to match with Atlassian's new identity structure using Atlassian Accounts. As part of this update, we have disabled/removed Sync Password and Update User Attributes functionality because Atlassian no longer supports them.
Atlassian is migrating all JIRA Cloud and Confluence Cloud customers by May 26th, 2017 to a new single identity called Atlassian Account. When you are ready, contact Atlassian to have your account migrated. If you do not contact Atlassian your account will be migrated automatically starting May 29th, 2017.
For details, see Migration to Atlassian Account for Jira Cloud and Confluence Cloud Customers for details.
We are migrating a significant number of our customers to our enhanced System Log as a part of our on-going GA rollout. In the next release, you may see the new System Log when navigating to Security System Log in your Okta Administrator Dashboard.
We have an enhancement for admins using .csv templates for user app assignments in lieu of provisioning. Along with importing users with Base attributes using a .csv template, you can import users with Custom attributes defined in the Profile Editor. For details on using this robust feature, see Importing People from a CSV File.
If a task is created from a group app assignment, you can change it to an individual assignment. All group assignment tasks contain an option for this permanent conversion. For details, see the Tasks Page section in The Administrator Dashboard.
The User Administrator role is now GA, including the people management features. This role has enhanced capabilities for managing groups. Super Admins can assign this role to isolate control over certain groups and teams within their organization. For details, see The User Admin Role.
To support our Concur integration, we now support TLS v1.2.
We have updated Egnyte provisioning so that once a user is provisioned into Egnyte by Okta and assigned the SSO authentication type, no further email validation is required. If you still want to receive a validation email from Egnyte for new SSO users, check the Send Egnyte Validation Email for SSO users box under the Provisioning tab.
We have added a new set of reports to our Reports page.
Auth Troubleshooting reports provide links to pre-defined queries in our System Log about the following authentication events:
- Okta Logins (Total, Failed)
- SSO Attempts
- Auths Via AD Agent (Total, Failed)
We've updated the visual progress indicators that appear in the Okta platform (spinners, progress bars).
Okta plugin version 5.11.0 is GA for Chrome, Firefox, Internet Explorer (IE), and Safari browsers. This version provides recent performance and security enhancements. For more information, see Browser Plugin Version History.
Okta is enabling two features, macOS MDM and Android for Work, for OMM customers that have not switched to our SKU packaging. For OMM customers with SKU packaging, these features are already enabled.
For more information about macOS, see OMM – MacOS Management. For details and configuration about Android for Work, see About Android for Work and Setting Up Android for Work.
The Welcome email that Okta sends to new end users is localized in the language in the users' default locale property (if specified) instead of the display language configured for your org (if different). For more information, see Configure the display language.
Admins can now examine the System Log to determine (in many cases) whether a given app login was initiated through the user's dashboard or through the browser plugin. For more information, see Reports. ![]() Screenshot
Screenshot
Group Password Policy is now Generally Available for all Preview orgs. It is still an Early Access feature for Production orgs.
Okta Admins can upload their own SAML certificates to sign the assertion for Outbound SAML apps and to sign the AuthNRequest and decrypt the assertion for Inbound SAML. For more information, see the Bring Your Own SAML App Certificate guide.
Version 1.11.0 of the Okta Sign-In Widget is available for Preview orgs. For more information, see Okta Sign-In Widget.
Okta now supports TLS v1.2 communication between Okta and the Jira-On Premises server. We recommend updating your server as soon as possible, in accordance with security best practice.
We have updated the On-Premises Provisioning (OPP) agent to version 1.01.00. This update adds an http option and makes UTF-8 encoding the default. Previously the default encoding was the one set on the OS/system on which the OPP agent was installed. After upgrading the agent, the default encoding becomes UTF-8, unless you override the default.
We have enhanced our System Log to now log the actual raw user agent string in the RawUserAgent string field.
-
We have updated the On-Premises Provisioning (OPP) agent to version 1.0.13. This allows the OPP agent to use the TLS v1.2 protocol, and deprecates TLSv1.0. We recommend updating your OPP agent as soon as possible, as TLSv1.0 is no longer considered secure.
-
Click Expand All to expand the left side event categories. This link then toggles to Collapse All.
-
More information about an event is now displayed when the category is collapsed. The following additional details are displayed (if available):
- Actor: user id
- Client: ip address
- Event: transaction id
- Target: target resource type and target resource id
 Screenshot
Screenshot
-
In addition to displaying the Outcome of an event, when the Outcome is failure, we now also display the reason why
 Screenshot
Screenshot
We have introduced a new Atlassian Cloud app integration that supports SAML for both JIRA Cloud and Confluence Cloud. In order to use SAML you will need to:
-
Switch your JIRA/Confluence Cloud tenants to Atlassian Account.
-
Switch to the Atlassian Cloud app integration in Okta.
For details, see How to Configure SAML 2.0 for Atlassian Cloud.
As part of Okta's Section 508 Compliance, links and buttons in certain areas of the Okta service are now illuminated when they're in focus. For more information about focus changes, see Testing HTML for Section 508 Compliance.
Changes to the platform for this release are published in the Platform Release Notes on http://developer.okta.com.
Our Universal Directory-enabled provisioning integrations for British Telecom (BT) Cloud Phone Production and BT Cloud Phone User Acceptance Testing (UAT) environments are now Generally Available (GA) (note that the UAT app is available in Preview orgs only). The BT Cloud Phone applications support attribute-level mastering, which allows BT Cloud Phone to act as a master for users ' direct and extension numbers while other attributes are mastered by a different source, such as Active Directory (AD). For details, see British Telecom Cloud Phone configuration guide.
Our Universal Directory-enabled provisioning integrations for RingCentral Office @ Hand for AT&T Production and RingCentral Office @ Hand for AT&T User Acceptance Testing (UAT) environments are now GA (note that the UAT app is available in Preview orgs only). The RingCentral Office @ Hand for AT&T applications support attribute-level mastering, which allows Office @ Hand for AT&T to act as a master for users ' direct and extension numbers while other attributes are mastered by a different source, such as Active Directory. For details, see RingCentral Office @ Hand for AT&T configuration guide.
When deprovisioning users, you can now do the following:
-
Remove or suspend a user in Dropbox.
-
Wipe data from users ' linked devices.
-
Transfer user files to other team member.
 Screenshot
ScreenshotFor more details, see Dropbox Business configuration guide.
Essentially, an end user can sign into SAML apps without re-entering their Okta credentials on their mobile device. This feature can be disabled if you'd rather not allow seamless SAML access to Safari. For details, see Okta Mobile SafariExtension.
We have added a new option to our current list of VPN profiles viaOMM. Admins can now provision Pulse Connect Secure as a VPN client. For details, see Configuring VPN Profiles. This feature is currently only available for iOS devices.
The cell in which your org is running now appears at the bottom of the page. A cell is an independent collection of multi-tiered, redundant hardware and software designed to effectively manage service traffic and requests for a subset of Okta tenants. Okta is comprised of multiple cells strategically deployed across several geographic regions. You may be asked to provide your cell number whenever you contact Okta Support.
As part of Okta 's 508 Compliance, input text fields are now illuminated when they 're in focus.
For more information about focus changes, see here.
This release combines features from Okta Preview Sandbox (oktapreview.com) 2017.03, 2017.04, and 2017.05.
As with Domain local and Global groups, you can now push Universal groups to Active Directory. ![]() Screenshot
Screenshot
When creating a new OpenID Connect app and configuring an Implicit grant type, you can now specify whether to include ID Tokens, Access Tokens, or both.
Per SAML standards, we now send Universal Directory (UD) array attributes in SAML 1.1 assertions as multi attribute values.
We have enhanced our System Log to now include more granular Microsoft Office 365 events.
You can configure an end-user fingerprint request that appears after the initial MFA challenge. If the user's device is lost or stolen, no one else can gain access to it. This feature is currently available only for iOS devices. For details, see Okta Verify with Touch ID.
We have improved text in the end user Welcome screen and Settings page in the Japanese language.
In addition to the index, we now support requesting the SAML ACS Endpoint by URL. For information about allowing apps to request other URLs, see Using the App Integration Wizard.
You can set an authorization server to manually rotate keys. Keys are rotated automatically by default. For more information, see API Access Management.
Important: Automatic key rotation is more secure than manual. Use manual key rotation only if you can't use automatic.
You can now search on the exact name of an authorization server or resource URI from the Authorization Servers tab (Security > API).
![]() Screenshot
Screenshot
We have enhanced the Amazon Web Services SAML SSO to allow setting of a configurable AWS ACS URL and AWS API URL. These fields are optional, and give the you added control over the app configuration. Note that if you already have an Amazon Web Services app configured, it will continue to work as-is. (This feature was hotfixed in Preview Release 2017.02).
The Okta plugin version 5.9.3 is now Generally Available (GA) for Firefox and Internet Explorer (IE) browsers. This release provides performance and security enhancements and is available to all customers via Settings > Downloads. For version history, see Browser Plugin Version History.
- The Okta IWA Web App version 1.10.1 is now GA. This release includes internal improvements as well as all the fixes and enhancements contained in EA versions 1.10.0 and 1.10.1. It is available to all customers via Settings > Downloads. For version history, see SSO IWA Web App Version History.
Unless otherwise noted, these features are available for all organizations with release 2017.02.
The Okta end user Dashboard now supports skip navigation to allow users and screen readers to bypass links at the top of the page and go directly to their desired content such as app chiclets, the Add App button, and end user Settings. For more information about skip navigation technology, see here.
- To allow more granular control of outbound provisioning to Active Directory (AD), admins can now deactivate the accounts of unassigned AD users and update user attributes in AD during app assignment and profile updates. For details, see Configuring Import and Provisioning Settings.
 Screenshot
Screenshot
-
You can permanently delete a deactivated user with the Delete button that appears in the directory screen for that user, as shown below. You cannot undo this deletion. After deletion you can reuse the user name and other identifiers; however, log entries are retained. For more information, see Deactivating and Deleting People.
2017 Application Integrations and Updates
-
Provisioning is enabled for the SightPlan Partner-Built application (OKTA-153312). For details, see the SightPlan Configuration Guide.
-
HONK Rescue (OKTA-151854)
-
Kentik (OKTA-152933)
-
OC Tanner AppreciateHub (OKTA-151853)
-
Synerion Enterprise (OKTA-152185)
-
Wombat Security Technologies (US) (OKTA-151569)
-
OverDRIVE (OKTA-151568)
-
Alerus: Account Access (OKTA-150560)
-
Amazon Vendor Central (OKTA-150503)
-
Cheetah Digital: Marketing Suite (OKTA-149943)
-
Foxit (OKTA-153102)
-
i3screen (OKTA-150608)
-
Snapseed (OKTA-153109)
-
VTS (OKTA-153111)
-
Atlassian Cloud (OKTA-151525)
-
Foxit (OKTA-152688)
-
Google Maps (OKTA-151645)
-
join.me (OKTA-152689)
-
Snapseed (OKTA-152691)
-
VTS (OKTA-152719)
-
NS1 (OKTA-150610)
-
Recurly (OKTA-151098)
-
ADP Retirement Services (Plan Sponsor/Advisor Login) (OKTA-150835)
-
Auth0 (OKTA-149833)
-
Brit Systems (OKTA-150646)
-
eZcard (OKTA-149086)
-
LastPass Affiliate (OKTA-149785)
-
Bellgram (OKTA-151286)
-
Jell (OKTA-151270)
-
Provisioning is implemented for the Verecho Partner-Built application (OKTA-150478). For details, see the Verecho Configuration Guide.
-
Code42 Provisioning, a Partner-Built integration, has updated their integration to now support Push Groups feature.
-
Provisioning is enabled for Pathgather. See the Pathgather Provisioning Guide for details.
-
Academy LMS by Praetorian Digital (OKTA-149948)
-
Jostle (OKTA-148625)
-
monday.com (OKTA-146798)
-
Sighten.io (OKTA-146496)
-
Spacebase (OKTA-149054)
-
WegoWise (OKTA-149747)
-
Ally Bank Login (OKTA-148498)
-
American Academy of Actuaries (OKTA-149200)
-
Apple Store for Business (OKTA-148098)
-
Bellgram (OKTA-149000)
-
Buddy Build (OKTA-148336)
-
CheckAlt Item Processing (OKTA-143087)
-
CN Transportation Services (OKTA-149327)
-
Conference of Consulting Actuaries (OKTA-149201)
-
CoreLogic (OKTA-149370)
-
FireEye (ETP) (OKTA-147126)
-
International SOS Assistance ()
-
Jell (OKTA-148868)
-
LexisNexis Insurance Solutions (OKTA-149001)
-
MasterCard Portfolio Viewer (OKTA-146956)
-
Microsoft Office 365 (OKTA-148998)
-
Microsoft Volume Licensing Service Center (OKTA-149245)
-
Pathgather (OKTA-150302)
-
Rollbar (OKTA-148225)
-
Society of Actuaries (OKTA-149199)
-
SunTrust SunView Treasury Manager (OKTA-148671)
-
TravelCube Pacific (OKTA-148220)
-
Virgin Pulse (OKTA-147924)
-
Airtame (OKTA-148643)
-
Confluence (Atlassian) (OKTA-149483)
-
Front (OKTA-148736)
-
Intercom (OKTA-148512)
-
International SOS Assistance (OKTA-148642)
-
JIRA Cloud (Atlassian) (OKTA-149477)
-
Marketo (OKTA-148744)
-
Nest (OKTA-149485)
-
SenderGen (OKTA-149770)
-
UberConference (OKTA-149924)
-
Workable (OKTA-149486)
-
ZScaler (OKTA-150480)
-
InVisionApp (OKTA-149768)
-
HighQ (OKTA-150276)
-
Stripe (OKTA-149772)
-
Provisioning is implemented for the Namely Partner-Built application (OKTA-147131). For details, see the Namely Configuration Guide.
-
6sense ABM and Analytics (OKTA-148708)
-
Clear Review (OKTA-147041)
-
PathSavvy (OKTA-147739)
-
Spacio (OKTA-146489)
-
WebEx (Cisco) (OKTA-148764)
-
WGM Apps (OKTA-146195)
-
EclipsePPM (OKTA-141524)
-
Abacus (OKTA-147741)
-
Aria (Customer Support Portal) (OKTA-147180)
-
AuthAnvil (OKTA-146187)
-
Deutsche Bank Autobahn (OKTA-146481)
-
Fiix (OKTA-146158)
-
Firefox (OKTA-148214)
-
Grovo (OKTA-149064)
-
ISO PAAS (OKTA-147804)
-
MultiSafepay (OKTA-146386)
-
ProofPoint Threat Insight Dashboard (OKTA-144658)
-
PWC Connect (OKTA-142763)
-
SmartBid (OKTA-145025)
-
Uber Central (OKTA-144015)
-
Zoho Books UK (OKTA-146369)
-
Abacus (OKTA-146602)
-
EverBridge (OKTA-147611)
-
Facebook (OKTA-147072)
-
Firefox (OKTA-147073)
-
Instagram (OKTA-147108)
-
LastPass (OKTA-147110)
-
MySonicWall (OKTA-147114)
-
New Relic (OKTA-149048)
-
Toggl (OKTA-147070)
-
Keepass2Android (OKTA-147109)
-
Berenberg: Equity Research Portal (OKTA-149134)
-
MiniKeePass (OKTA-147111)
-
The Pathgather app is Okta-built. The Pathgather Cloud Provisioning Connector integration is now OKTA owned and publicly available. For any existing app instances using the custom version of this integration and being migrated to this publicly available bundle, the import feature would be disabled by default. Admins will need to enable the feature on the Provisioning tab and re-save the app instance to keep using the import feature.
-
Provisioning is implemented for the LastPass Sync Partner-Built application (OKTA-147131). For details, see the LastPass Sync Configuration Guide.
-
Andromeda On-Premises (OKTA-146475)
-
Breezy HR (OKTA-146166)
-
DataScience.com Platform (OKTA-144598)
-
EmployeeChannel (OKTA-140778)
-
Retail Zipline (OKTA-145897)
-
Slemma (OKTA-146159)
-
Consumer Edge Research (OKTA-142258)
-
Evercore ISI: Equity Research (OKTA-142259)
-
Evercore ISI: Equity Research iPad (OKTA-146167)
-
Guidepoint (Client Login) (OKTA-143877)
-
LiveWell (OKTA-143858)
-
PlanGuru (OKTA-143812)
-
PostNL (OKTA-144235)
-
ProofPoint Secure Share Administration (OKTA-144523)
-
SaneBox (OKTA-145283)
-
Sentinel Security Life Admin Portal (OKTA-146067)
-
SRA (OKTA-143289)
-
Health4Me (OKTA-145156)
-
POP Tracker (OKTA-145158)
-
Termux (OKTA-143068)
-
Termux:Styling (OKTA-143067)
-
G Suite (OKTA-143066)
-
Google Quick Search (OKTA-143065)
-
DealerSocket (OKTA-145234)
-
EAT Club (OKTA-138253)
-
Engagio (OKTA-145232)
-
Frontline Vulnerability Manager (OKTA-142918)
-
Google Cloud Platform (OKTA-145110)
-
NexTravel (OKTA-142917)
-
Plex Identity Access Management (OKTA-141301)
-
ProductIP (OKTA-146194)
-
Saba (OKTA-144740)
-
SightPlan (OKTA-142620)
-
TextMagic (OKTA-143869)
-
AmericanFunds Retirement Solutions (OKTA-143495)
-
Aviva My Business (OKTA-141954)
-
Barlaycard (OKTA-141952)
-
BT Business (OKTA-141953)
-
CEB Shared Services Leadership Council (OKTA-143891)
-
CFS dataVISION (OKTA-143526)
-
Credit Suisse Plus (OKTA-141949)
-
DuPont eLearning Suite (OKTA-142178)
-
Exane BNP Paribas (OKTA-142253)
-
Google Cloud Platform (OKTA-145110)
-
Inbox by Gmail (OKTA-145603)
-
Inbox by Gmail (OKTA-145603)
-
Rhone Group (OKTA-141951)
-
Vintage King (OKTA-145160)
-
World First (OKTA-141955)
-
Cisco Spark Platform (OKTA-144000)
-
G Suite (OKTA-139982)
-
Google Cloud Platform (OKTA-145110)
-
LumApps (OKTA-143063)
-
MyCigna (OKTA-145152)
-
Autonomous (OKTA-141746)
-
Deutsche Bank: Global Markets Equities (OKTA-141743)
-
Fiix (OKTA-144609)
-
Berenberg: Corporate Portal (OKTA-141737)
-
Inbox by Gmail (OKTA-145603)
-
6sense ABM & Analytics (OKTA-143628)
-
BasicOps (OKTA-139540)
-
Branch SAML (OKTA-141410)
-
Sentry (OKTA-143868)
-
Sequr (OKTA-142392)
-
Symantec Web Security Service (OKTA-136082)
-
Udemy for Business (OKTA-143722)
-
Bernstein Research (OKTA-144390)
-
Business VAT (OKTA-141946)
-
Eden (OKTA-144050)
-
Google Docs (OKTA-142694)
-
Redburn (OKTA-141948)
-
Google Voice (OKTA-139985)
-
Bernstein Research (OKTA-141739)
-
Raymond James Equity Research (OKTA-141744)
-
SAP Cloud for Customer (OKTA-141032)
- The Okta/Slack integration now supports Schema Discovery and additional profile attribute mappings. For details, see the Slack Provisioning Guide.
- Udemy for Business (OKTA-142080)
-
Killer Tracks (OKTA-142365)
-
LeadsPedia (OKTA-142166)
-
miniOrange (OKTA-141313)
-
NFL Game Pass (OKTA-141322)
-
Star Cruise B2B (OKTA-142743)
-
Uber for Business (OKTA-141950)
-
Wolfe Research (OKTA-140617)
-
Bank of America Merrill Lynch: Mercury Login (OKTA-142038)
-
Captec: CRM (OKTA-140860)
-
J.P. Morgan Markets (OKTA-140879)
-
Morgan Stanley Matrix (OKTA-142039)
-
Morgan Stanley: Research (OKTA-140889)
-
Sentieo (OKTA-140885)
-
Société Générale: Markets (OKTA-142040)
-
Goldman Sachs 360 (OKTA-140865)
-
Jefferies: Global Equity Research (OKTA-140877)
-
RBC Insight (OKTA-141745)
-
UBS: Neo Login (OKTA-140890)
-
Atipica (OKTA-142623)
-
Coggle (OKTA-142079)
-
Expressive (OKTA-142221)
-
jTask Pulse (OKTA-141922)
-
Whistic (OKTA-128904)
-
Banc Mall (OKTA-140874)
-
CrowdStrike Support Portal (OKTA-140514)
-
Pandaw (OKTA-141916)
-
Principal Employer (OKTA-141121)
-
Shoutem (Affiliate Login) (OKTA-141851)
-
Google Authenticator (OKTA-139981)
-
Google Keep (OKTA-139983)
-
Google News & Weather (OKTA-139984)
-
Hangouts Meet (OKTA-139986)
-
HSBC Global Research (OKTA-140867)
-
Microsoft Office 365 (OKTA-138222)
-
Microsoft Teams (OKTA-138225)
-
S&P Capital IQ (OKTA-140882)
-
Google Plus (OKTA-139987)
-
Okta has implemented provisioning for the Trello Partner-Built application (OKTA-142138). For details, see the Trello Configuration Guide.
-
Coveo Cloud (OKTA-141304)
-
icare - Guidewire Policy Center (OKTA-139024)
-
MyWebTimesheets (OKTA-141411)
-
Splan Visitor (OKTA-141202)
-
UniversitySite (OKTA-141300)
-
UsefulFeedback (OKTA-134151)
-
Calendly (OKTA-140676)
-
Canaccord Genuity (OKTA-140615)
-
ClassMarker (OKTA-141175)
-
fusionZONE Automotive (OKTA-140669)
-
It Glue (OKTA-140213)
-
LoansPQ (OKTA-141025)
-
Medi-Share Provider Portal (OKTA-140351)
-
Microsoft Office 365 (OKTA-142184)
-
Office National Australia (OKTA-139526)
-
Stratocast MS Login (OKTA-140601)
-
Unbounce (OKTA-141630)
-
United Health Care (OKTA-141178)
-
Adam Phones Portal (OKTA-140839)
-
Barclays Live Client Login (OKTA-140853)
-
Citi Velocity (OKTA-140863)
-
Berenberg: Equity Research Portal (OKTA-139765)
-
CloudHealth (OKTA-141172)
-
Glint Innovation (OKTA-137507)
-
Gusto (OKTA-140767)
-
Holland and Barrett (OKTA-139764)
-
ProLease (OKTA-138755)
-
Wellworks For You (OKTA-131905)
-
HSE-Compliance (OKTA-139418)
-
AB Bernstein (OKTA-139766)
-
Abbvie (OKTA-133949)
-
AbsorbLMS (OKTA-141014)
-
ADP TotalSource (OKTA-140931)
-
Autonomous (OKTA-140614)
-
Azure Manage (OKTA-141166)
-
Azure Portal Login (OKTA-136276)
-
B. Riley Equity Research (OKTA-140607)
-
BlueMatrix (OKTA-140608)
-
Boston Private Bank: Online Banking (OKTA-138006)
-
Carerix (OKTA-140487)
-
Ceridian HR/Payroll Web (OKTA-139044)
-
Creditsafe NL (OKTA-137827)
-
Deutsche Bank: Global Markets Equities (OKTA-136778)
-
EasyKeys.com (OKTA-141168)
-
Engine Yard (OKTA-141165)
-
Financial Times (OKTA-136815)
-
Gett For Business (OKTA-136816)
-
Glint Innovation (OKTA-137507)
-
GoAnywhere Login (OKTA-136177)
-
Granite Rock Reports (OKTA-139556)
-
HFR (OKTA-140606)
-
ICICI Bank Money2India (OKTA-140806)
-
Microsoft SharePoint Online Office 365 (OKTA-140253)
-
Morning Star: Investment Research (OKTA-139767)
-
Olympex Global (OKTA-136819)
-
One Codex (OKTA-140587)
-
ONEaccess (OKTA-136813)
-
Optimal Workshop (OKTA-140491)
-
OTR Global (OKTA-140612)
-
PNC - Online Banking (OKTA-141076)
-
Pond5 (OKTA-137182)
-
RBC Insight (OKTA-140616)
-
RJ Capital Markets Equity Research (OKTA-140609)
-
Safeware (OKTA-139076)
-
UBS: Neo Login (OKTA-135350)
-
Wealthscape (OKTA-139423)
-
Ribena (OKTA-139763)
-
Receipt Bank (OKTA-138882)
-
Dropbox Business (OKTA-135103)
- My MWC Americas (OKTA-138408)
- Quip (OKTA-136945)
- LucidChart (OKTA-136946)
-
SailPoint IdentityIQ (OKTA-81678)
-
Arvest Banking (OKTA-137291)
-
BAML Works (OKTA-139658)
-
Cintellate by SAI Global (OKTA-137811)
-
ComputerShare Support Portal (OKTA-138293)
-
Creditsafe UK (OKTA-138608)
-
Macquarie (OKTA-138421)
-
Microsoft Intune Company Portal (OKTA-138764)
-
myKaarma (OKTA-139092)
-
MyKaarma (OKTA-139092)
-
NFL Game Pass (OKTA-139100)
-
Royal Mail (OKTA-136820)
-
sai.patenergy.com (OKTA-139302)
-
SeatGeek (OKTA-139120)
-
Vanguard Software (OKTA-138897)
-
Vanguard Software (OKTA-138897)
-
Visible Alpha (OKTA-136814)
-
Intune Company Portal (OKTA-138220)
-
CrossLead (OKTA-137987)
-
PageTiger (OKTA-137850)
-
PerformYard (OKTA-138423)
-
Piwik (OKTA-137352)
-
Polestar SaaS - MyPayPortal (OKTA-133390)
-
SmartRecruiters (OKTA-137424)
-
Twebcast (OKTA-133391)
-
Beonic Technologies Traffic Insight (OKTA-137971)
-
CommonwealthBank NetBank (OKTA-138420)
-
FINRA (OKTA-135356)
-
Infor EAM (OKTA-137136)
-
Saleshood (OKTA-136672)
-
SafetyStratus (OKTA-137023)
-
ThreatStream SaaS (OKTA-132850)
-
Workstars (OKTA-137849)
-
Velaro (OKTA-137485)
-
3Rivers (OKTA-136657)
-
Aviva (OKTA-136823)
-
Bank of America Merrill Lynch: Mercury Login (OKTA-136776)
-
Barclays Live Client Login (OKTA-136775)
-
Charlie HR (OKTA-136824)
-
Citizens Bank accessMONEY Manager (OKTA-136559)
-
FCA: Connect (OKTA-136767)
-
Fedex United Kingdom (OKTA-136818)
-
FINRA IARD (OKTA-136769)
-
FINRA Web CRD (OKTA-136768)
-
Mortgagebot LOS (OKTA-136686)
-
Nespresso UK (OKTA-136861)
-
Oracle WebCenter Portal (OKTA-132500)
-
RedQuarry (OKTA-136461)
-
REI: Super (OKTA-136272)
-
Sage Employee Services Portal (OKTA-137622)
-
Sainsburys Groceries (OKTA-136845)
-
UnaVista Transaction Reporting (OKTA-135357)
-
Valera Global (OKTA-136817)
-
Viking (OKTA-136821)
-
Zepbrook (OKTA-136822)
-
Kollective (OKTA-135191)
-
RedLock (OKTA-136600)
-
FCA: Gabriel (OKTA-135355)
-
Juilliard (OKTA-134620)
-
MyGeotab (OKTA-135211)
-
Ramp (OKTA-136243)
-
TestRail (OKTA-136226)
- Okta has implemented provisioning for the ThousandEyes Partner-Built application (OKTA-136978). For details, see the ThousandEyes Configuration Guide.
- VendorHawk (OKTA-135783)
-
Adam Phones Portal (OKTA-135352)
-
American Strategic Insurance - Agent Login (OKTA-135526)
-
Arizona Uniform (OKTA-136054)
-
Baker Hill Advisor (OKTA-131770)
-
Goldman Sachs 360 (OKTA-135343)
-
J.P. Morgan Markets (OKTA-135346)
-
Jefferies: Global Equity Research (OKTA-135347)
-
Morgan Stanley Matrix (OKTA-135348)
-
Piper Jaffray: Research Access (OKTA-135349)
-
Proposify (OKTA-134813)
-
Societe Generale: Markets (OKTA-135351)
-
State Street (OKTA-135354)
-
Provisioning is implemented for the TalentLMS Partner-Built application (OKTA-135457). For details, see the TalentLMS Configuration Guide.
-
We have enhanced the Roambi provisioning integration to support Roambi's European endpoint. If you are on Roambi EU, go to the Provisioning tab in Okta, and select EU from the Account Location dropdown menu.
 Screenshot
Screenshot
For details, see the Roambi Provisioning Guide.
-
The following update was deployed to Preview with 2017.28, and is now deployed to Production. The Google Apps integration includes the following improvements:
-
Reduced import time by increasing the maximum number of users returned in a page from Google from 100 to 500.
-
Reduced the time it takes to update group memberships by batching requests into a single (up to 1000 per request) request. This significantly reduces the network overhead and latency when performing a large number of updates.
-
-
Gong (OKTA-133878)
-
HappyFox Chat (OKTA-133841)
-
WebEx (Cisco) (OKTA-126745)
-
ACA Aponix Web Portal (OKTA-132502)
-
Sentieo (OKTA-113327)
-
Activist Shorts Research (OKTA-135345)
-
Alibaba Cloud (Aliyun) (OKTA-133666)
-
Attorney Information System (AIS) (OKTA-134332)
-
AutoLoop (OKTA-134497)
-
HSBC Global Research (OKTA-135344)
-
Lakeland Bank (OKTA-133317)
-
Sentieo (OKTA-135353)
-
MyGeotab (OKTA-134841)
-
Dropbox for Business (OKTA-132476)
Production release 2017.30 combined Preview releases 2017.29 and 2017.30.
- The Smartsheet integration has improved messaging.
-
Provisioning is implemented for the 15Five Partner-Built application (OKTA-134568). For details, see the 15Five Configuration Guide.
- SchoolKeep (OKTA-128903)
-
Aviso (OKTA-133528)
-
Blue Ocean Brain (OKTA-131689)
-
HelloSign (OKTA-130205)
-
KPN Zorg Messenger (OKTA-133243)
-
OneTrust (OKTA-128479)
-
Sapling (OKTA-133389)
-
UserVoice (OKTA-109584)
-
WorkRamp (OKTA-131683)
-
NS1 (OKTA-133489)
-
OneSignal (OKTA-133218)
-
TeluxHD (OKTA-132188)
-
The Courier Mail (OKTA-133043)
- FreshService (OKTA-131337)
- Intelex Mobile (OKTA-133346)
- Snapchat (OKTA-132858)
- NetDocuments (OKTA-133690)
-
Alterdesk (OKTA-131448)
-
DEEM (OKTA-104299)
-
IncentFit (OKTA-128183)
-
KPN Zorg Messenger (OKTA-130957)
-
Learndot (OKTA-105640)
-
Kamer van Koophandel (OKTA-132527)
- The CornerStone on Demand integration now supports a customizable SAML ACS URL.
- Okta now supports SHA256 Fingerprints for application Security Certificates. Users of Freshservice are advised to update their SHA1 fingerprint to SHA256.
-
DocSend (OKTA-129382)
-
Envestnet Tamarac (OKTA-129603)
-
Netskope Reverse Proxy (OKTA-121479)
-
Noggin OCA (OKTA-129599)
-
Pendo (OKTA-126426)
-
ReadMe SAML (OKTA-130202)
-
ShareVault (OKTA-129602)
-
Talla (OKTA-130777)
-
TeamsID (OKTA-127919)
-
TruSTAR (OKTA-129855)
-
Ultimate Software Perception (OKTA-130955)
-
Advent Black Diamond (OKTA-125369)
-
GoLinks (OKTA-124520)
-
Apple ID (OKTA-130193)
-
CoStar (OKTA-130094)
-
Ernst Publishing (OKTA-130675)
-
Flagstar Bank - Correspondent Purchasing System (OKTA-131690)
-
JobTeaser (OKTA-130924)
-
Oracle Fusion (OKTA-128954)
-
Spectrum Time Warner Cable (OKTA-130723)
-
The Courier Mail (OKTA-129829)
-
Replicon (OKTA-131332)
-
Diligent Boardbooks (OKTA-130402)
We have added support for EU endpoints to our NetSuite integration. You can now select EU endpoints when configuring provisioning for NetSuite.
-
Apple Search Ads (OKTA-129245)
- Contract Express (OKTA-129632)
-
TELUS Business Connect Voice Manager (OKTA-128491)
My MWC Shanghai (OKTA-128667)
-
Org2Org group membership update jobs are more resilient. Previously, jobs failed as soon as any user within the update failed; therefore, not all users were updated who could have been. Now jobs fail only when more than 90% of the user's group memberships fail to update.
The 90% threshold exists to detect and prevent situations where the Org2Org connector, or the target instance, are incorrectly configured and the job terminates early.
-
We have enhanced Smartsheet provisioning to support User Reactivation. For this enhancement to take effect, you need to re-save Provisioning settings for any existing app instances.
For details about Smartsheet provisioning, see the Smartsheet Provisioning Guide.
- Contently (OKTA-128326)
- StartMeeting (OKTA-128482)
- ValiMail (OKTA-129219)
- Google My Business (OKTA-129217)
- Nationstar (OKTA-130026)
- PennyMac (OKTA-130028)
We've enhanced error handling for Service Now Eureka app provisioning.
-
CloudAMQP (OKTA-127339)
-
Findo (OKTA-126795)
-
Gliffy (OKTA-128907)
-
ProdPad (OKTA-126422)
-
American Modern Agent Login (OKTA-128670)
We've enhanced the following integrations:
-
BambooHR: Schema Discovery now supports attributes with numerical names. Previously, we only imported attributes with alpha-character aliases, such as hireDate. Note that attributes that are members of BambooHR Tables are not supported at the moment.
-
Rally: Schema Discovery now supports all Rally user attributes available through the API, in addition to custom attributes.
UltiPro: We've improved error messaging for provisioning international employees.
We've implemented Provisioning for the following Partner-Built application:
-
Code42 (OKTA-128569). For details, see Code42's Configuration Guide.
-
Five9 Plus Adapter for Zendesk (OKTA-127619)
-
Helpjuice (OKTA-126793)
-
Infor Cloud (OKTA-93453)
-
Mode Analytics (OKTA-126792)
-
Realtime Board (OKTA-126428)
-
ScholarOne (OKTA-127984)
We have implemented the following application integrations:
- Airtable (OKTA-124530)
- Beam (OKTA-124524)
- OnDMARC (OKTA-126212)
- Tesorio (OKTA-127504)
- AvidXchange (OKTA-127776)
- Travelport ViewTrip (OKTA-126959)
- Salesforce.com (Federated ID) (OKTA-55571)
- Euromonitor Passport: We've removed Custom SSO Mode (note that SAML SSO was implemented earlier this year). For more details, see How to Configure SAML 2.0 for Euromonitor Passport.
- Egnyte: We now send the IdP Username as the Name ID value in the SAML assertion if available. If not available, we send the Username.
We have implemented the following:
SAML for the following Okta Verified applications
Benchling for Enterprise (OKTA-122008)
ClearStory Data (OKTA-125199)
cmpute.io (OKTA-120176)
Gliffy (OKTA-126552)
Klue (OKTA-124525)
LogicManager (OKTA-117451)
MuleSoft - Anypoint Platform (OKTA-108055)
Workato (OKTA-125200)
SWA for the following Okta Verified applications
Cannex Customer Portal (OKTA-126589)
Santander (OKTA-126270)
SilkRoad Learning (GreenLight) (OKTA-126207)
Sitrion (OKTA-126937)
Virtru (Google Login) (OKTA-126142)
Mobile application for use with Okta Mobility Management (OMM) ( iOS only)
ComplianceWire SWA (OKTA-126740)
We have changed the names of the following app integrations:
- SmartRecruiters is now SmartRecruiters (SWA Only)
- SmartRecruiters SAML is now SmartRecruiters (this app has provisioning and SAML functionalities)
We have implemented the following:
- StatusCast (OKTA-93551)
-
Infor EAM (OKTA-120077)
- Infor EAM (OKTA-119531)
- Outlook Web Access - 2003 (OKTA-124388)
We have implemented the following:
- Orginio (OKTA-123619)
- ParkMyCloud (OKTA-123570)
- PageUp (OKTA-66973)
- Ceridian Dayforce HCM (OKTA-122004)
- Global Relay Archive (OKTA-122777)
- My M360 by GSMA (OKTA-123799)
- GoodNotes (OKTA-122663)
-
HBS Timesuite (OKTA-123531)
- Lender Price (OKTA-123320)
- My Atlassian (OKTA-123161)
- PeopleStrategy (OKTA-123366)
-
Schwab Advisors UAT (OKTA-122167)
We have implemented the following:
-
Palo Alto Networks - CaptivePortal (OKTA-112813)
-
Palo Alto Networks - GlobalProtect (OKTA-113138)
-
SigOpt (OKTA-122575)
-
Bank Of The West - WebDirect (OKTA-120423)
-
Client Track (OKTA-122171)
-
My Cloud (OKTA-122215)
-
ONE by AOL: Video (OKTA-122583)
We've implemented the following:
-
Cylance (OKTA-118387)
-
Logit (OKTA-116516)
-
TurboRater (OKTA-121517)
-
Detectify (OKTA-122007)
-
HPE Connected MX (OKTA-117314)
-
Recognize (OKTA-116273)
-
Vena (OKTA-116275)
-
YardiOne Dashboard (OKTA-117894)
- America First Credit Union (OKTA-122681)
- MasterCard Smart Data (OKTA-122268)
- ONE by AOL: Video (OKTA-121268)
- GlobalMeet Web Audio (OKTA-118774)
- GlobalMeet Audio (OKTA-118774)
-
Sisense (OKTA-119574)
-
Akamai Enterprise Application Access (OKTA-116573)
-
Amazon Appstream (OKTA-117136)
-
Bugsnag (OKTA-120278)
-
ClearCompany (OKTA-120378)
-
Dialpad (OKTA-120168)
-
DigiCert (OKTA-121112)
-
F5 BIG IP (OKTA-111494)
-
Five9 Plus Adapter for Agent Desktop Toolkit (OKTA-120279)
-
Gatekeeper (OKTA-119753)
-
IBMid (OKTA-117726)
-
SalesLoft (OKTA-120019)
-
Shufflrr (OKTA-116274)
-
ThirdPartyTrust (OKTA-119751)
We have enhanced our Evernote integration to include support for Business Sandbox environments for SWA, SAML, and Provisioning.
We've implemented the following:
-
IBM Connections (OKTA-119786)
-
LoansPQ (OKTA-119828)
-
TrueAbility (OKTA-119073)
-
Blueboard (OKTA-117705)
-
BoardEffect (OKTA-120303)
-
Oracle Hyperion EPM Cloud Services (OKTA-116517)
-
Reflektive (OKTA-118779)
-
GreatVines Beverage Sales Execution (OKTA-119035)
-
Invision (OKTA-120152)
We've implemented the following:
-
BEAMGroups (OKTA-119020)
-
Cashet (OKTA-118123)
-
Chrome River (OKTA-119192)
-
Citrix Receiver (OKTA-116900)
-
Glip (OKTA-118950)
-
KnowBe4 (OKTA-118147)
-
LoansPQ (OKTA-116896)
-
Aurion (OKTA-109423)
-
BearTracks (OKTA-114504)
-
bob (OKTA-114648)
-
Lattice (OKTA-119365)
-
Lessonly (OKTA-114044)
-
Skyhigh Networks (OKTA-118138)
-
When I Work (OKTA-117854)
-
SoapboxHQ (OKTA-83597)
-
Basecamp (OKTA-118773)
-
Birst (OKTA-118938)
-
Glip (OKTA-119377)
-
Livestream (OKTA-118776)
-
Workfront (OKTA-119072)
-
InVisionApp (OKTA-118777)
-
CloudMine (OKTA-114839)
-
Snowflake (OKTA-114823)
-
Titanfile (OKTA-114834)
-
We have enhanced the Amazon Web Services (AWS) configuration screen to reduce sensitive information displayed.
We've implemented the following:
-
CBRE-EA (OKTA-115150)
-
A Cloud Guru (OKTA-117538)
-
Adstream (OKTA-115203)
-
Alerus Financial Retirement Account Access (OKTA-116702)
-
Atlassian Cloud (OKTA-118934)
-
BirdDogHR (OKTA-115842)
-
Cook County Illinois (OKTA-109891)
-
Ensighten (OKTA-117875)
-
J. P. Morgan Markets (OKTA-115883)
-
Merchant e-Solutions (OKTA-116199)
-
Western Union Point of Sale (OKTA-114908)
-
Bambu by Sprout Social (OKTA-116521)
-
ContractSafe (OKTA-116632)
-
Euromonitor Passport (OKTA-117579)
-
FotoWeb (OKTA-99225)
-
HireVue (OKTA-112967)
-
LiGO (OKTA-115115)
-
Merlin Guides (OKTA-115970)
-
Nmbrs (OKTA-117137)
-
Onshape (OKTA-115971)
-
Platform9 (OKTA-97788)
-
Schwab Compliance Technologies (OKTA-108582)
-
Secret Server (OKTA-115972)
-
Splunk Cloud (OKTA-114946)
-
Testable (OKTA-115562)
-
Certify (OKTA-115303)
-
Greenhouse (OKTA-115836)
-
Hightower (OKTA-87082)
-
Procore (OKTA-115699)
-
Pulse Connect Secure VPN (OKTA-115309)
-
VLC (OKTA-117613)
We've implemented the following:
-
BT Cloud Phone (OKTA-110344)
-
Fujitsu RunMyProcess (OKTA-114630)
-
myPolicies (OKTA-113177)
-
Bonusly (OKTA-114813)
-
Bullhorn (OKTA-113959)
-
Dell Boomi SAML (OKTA-114810)
-
GoodData (OKTA-114830)
-
HighQ (OKTA-114811)
-
Intuit Quickbase with SubDomain (OKTA-114812)
-
iPass (OKTA-114837)
-
Joomla (OKTA-114838)
-
Keylight Platform by LockPath (OKTA-114840)
-
SocialText (OKTA-114826)
-
SpringCM (OKTA-114829)
-
WidenCollective (OKTA-114809)
We have added the option to send email notifications upon user creation to the JIRA Cloud and JIRA on-premise app integrations. ![]() Screenshot
Screenshot
We'e implemented the following:
-
Adjust (OKTA-113618)
-
Apple MyAccess (OKTA-113555)
-
Awesome Screenshot (OKTA-113632)
-
Framer Cloud (OKTA-113964)
-
Google Partner Dash (OKTA-113487)
-
Google Tag Manager (OKTA-113211)
-
Kanbans (OKTA-69763)
-
Predictive Policing (OKTA-111943)
-
Principal Advisor (OKTA-112103)
-
WestNet Learning (OKTA-114255)
-
Duo Network Gateway (OKTA-111954)
-
Honest Buildings (OKTA-112673)
-
Keeper Password Manager and Digital Vault (OKTA-112806)
-
LiveRamp Connect (OKTA-113207)
-
MetricStream (OKTA-111284)
-
Qminder (OKTA-112438)
-
RFPIO (OKTA-112823)
-
Velpic (OKTA-113130)
-
Splunk Cloud (OKTA-96258)
-
Cornerstone OnDemand (OKTA-114007)
-
MyMWC - GSMA (OKTA-112838)
-
SDGs in Action (OKTA-110663)
-
SDGs in Action (OKTA-110663)
-
AbsorbLMS (OKTA-114002)
-
ACL GRC (OKTA-112483)
-
ANCILE uAlign (OKTA-112835)
-
BenefitSolver (OKTA-112466)
-
Bright Funds (OKTA-112472)
-
BSwift (OKTA-113982)
-
Changepoint (OKTA-114004)
-
Cisco Spark Platform (OKTA-113962)
-
Corcentric COR360 (OKTA-113989)
-
Corpedia (OKTA-112484)
-
CultureWizard (OKTA-112487)
-
Daptiv (OKTA-112488)
-
Eloqua (OKTA-113985)
-
Everbridge Manager (OKTA-112458)
-
GetThere (OKTA-112490)
-
IBM Global Expense Reporting Solutions (GERS) (OKTA-112459)
-
iMeetCentral (OKTA-112477)
-
Information Center (Deprecated)(OKTA-112478)
-
Introhive (OKTA-112491)
-
Intuit Quickbase without SubDomain (OKTA-112462)
-
KnowBe4 (OKTA-112463)
-
LeanKit (OKTA-114001)
-
MyComplianceOffice (OKTA-112493)
-
Novatus (OKTA-113963)
-
Qvidian (OKTA-113995)
-
SAP NetWeaver (OKTA-113987)
-
Schoolzilla (OKTA-112464)
-
Selectica (OKTA-113997)
-
TalentWise (OKTA-112460)
-
Towers Watson Case Management (OKTA-112470)
-
Whitehat Security (OKTA-113977)
-
Zoho (OKTA-112479)
-
ZoomForth (OKTA-112480)
Trello apps have been renamed to: Trello (SWA Only) and Trello (for SAML)
Fidelity & Guarantee Life (OKTA-110857)
Untangled Solutions (OKTA-110783)
- Citrix Netscaler Gateway (OKTA-111142)
Five9 Agent Desktop Plus (OKTA-111282)
GpsGate (OKTA-111458)
Wiredrive (OKTA-110761)
- Benefex RewardHub (OKTA-108578)
Caspio (OKTA-97787)
Sustainovation Hub (OKTA-110852)
WidePoint - ITMS (OKTA-102918)
2017 Bug Fixes
- OKTA-65773 – The number of users did not display correctly in the Password Reset Filter on the People page.
- OKTA-135913 – The Password Reset list only showed two users. The Admin had to select Show More to see the full list.
- OKTA-138274 – When creating or updating a group in Slack, existing members of the group in Slack are now downloaded into Okta. This fixed an issue where subsequent group membership could not be updated on the group.
- OKTA-143576 – Users were not forced to reset a temporary password after their accounts were locked and subsequently unlocked.
- OKTA-144882 – Group Push errors for the Slack app could not be fixed or deleted.
- OKTA-145449 – Org2Org now respects rate limits and automatically reschedules the provisioning job if rate limits are exceeded.
- OKTA-146217 – The VPN setup page failed to load for some customers.
- OKTA-146835 – Importing users from Active Directory failed after selecting no secondary email, if a value for secondary email was previously mastered and mapped in Active Directory.
- OKTA-147768 – The app user property Personal Meeting Room URL could not be mapped when pushing users to WebEx.
- OKTA-148505 – Password complexity rules were not fully localized.
- OKTA-148558 – The link expiration time sent in the Password Reset email varied from the time specified in the password policy.
- OKTA-149651 – Group rules did not retrieve all specified Okta-mastered groups when there were other groups with similar names.
- OKTA-149782 – Auto Launch for Bookmark apps could not be enabled.
- OKTA-150877 – Importing users from Active Directory and mapping them to existing users failed if the existing users had mappings to an app instance that was previously deleted by a group membership change.
- OKTA-151726 – Active Directory groups with an asterisk (*) in their names did not appear in the group list.
-
Creditsafe (OKTA-153212)
-
ISO PAAS (OKTA-151277)
-
JWPlayer (OKTA-152062)
-
KISS Metrics (OKTA-150894)
-
Schwab Equity Award Center (OKTA-152286)
-
IBM SmartCloud for Social Business (OKTA-152015)
-
JobScience (OKTA-149440)
- OKTA-145602 – Erasing all IP addresses in the Default IP Blacklist zone caused an error to display.
- OKTA-146677 – When performing a group push for SCIM apps, Okta overwrote the group memberships for that group.
- OKTA-147424 – While creating or updating user profiles using Profile Sync provisioning type for a Microsoft Office 365 app, the email address could be updated in Office 365; consequently, the attribute was no longer pushed during these profile updates. Additionally, the mapping in Universal Directory was removed for this attribute.
- OKTA-148212 – When provisioning to an app failed after assigning the app to a group, the app User Profile details were not displayed.
- OKTA-148275 – When using the Edge browser, the security image was not displayed during Sign On. Additionally, Multifactor Authentication on a per-app basis was not available after installing the Okta Browser Plugin for Edge.
- OKTA-148314 – The export to a CSV file from the MFA Usage report was formatted incorrectly.
- OKTA-148668 – The System Log did not track the addition of a new Administrator correctly.
- OKTA-149861 – The link to the CSV version of the Applications Access Audit report for current assignments was not functional.
- OKTA-149888 – The display name could not be updated during a profile push to the Slack app. As a result, the property was no longer pushed during profile updates but still can be pulled from Slack.
- OKTA-150748 – Multifactor Authentication for Microsoft RDP was not available under certain circumstances.
-
Absolute Console (OKTA-150815)
-
Amazon (OKTA-151850)
-
Cain Travel (OKTA-150780)
-
Cardmember Service by Elan Financial Services (OKTA-150776)
-
Corporate Perks (OKTA-150781)
-
Envoy (OKTA-150770)
-
J.Crew (OKTA-151571)
-
Kestra Financial (OKTA-150774)
-
Softchoice (OKTA-150773)
-
Ticketmaster (OKTA-150772)
-
TimeOff Manager (OKTA-150635)
-
JIRA On-Prem (OKTA-135556)
- OKTA-128322 – Attempting to sign in to the JIRA On-prem app or the Confluence On-prem app did not create a new session if the user already had a valid browser session for the app.
- OKTA-137503 – The Reset Password screen did not require that only one user category be selected.
- OKTA-140940 – Buttons on the Group Assignment screen were not aligned properly.
- OKTA-144636 – Password requirements were incorrectly evaluated on passwords longer than 72 characters.
- OKTA-146332 – Some imports failed for the NetSuite app.
- OKTA-146398 – After disabling Duo Security as a Multifactor Authentication factor, it still appeared on the multifactor page.
- OKTA-146745 – Some App users were not found in the System Log when searching for events by Display Name.
- OKTA-147353 – Some attributes imported from SuccessFactors had their values in the Okta profile set to external codes (identifiers configured in SuccessFactors).
- OKTA-147406 – Users were prompted for passwords on iOS 10.3 devices, even though Certificate Based Authentication was enabled for them on Microsoft Exchange ActiveSync.
- OKTA-147430 – After updating the application username format in the Application Integration Wizard SAML App, multiple requestable SSO URLs were deleted.
- OKTA-147965 – The System Log did not display password reset entries that were denied.
- OKTA-147997 – Adding the RememberMe cookie during login through JIRA authenticator configuration was not supported.
- OKTA-148200 – Accessing the Confluence On-prem app redirected users to sign in to Okta even when their accounts were not present in Okta.
- OKTA-148873 – Updating the Connector Configuration for On-Prem Provisioning settings for an app caused an error.
- OKTA-149267 – Users could not access the JIRA On-prem app during SP-initiated login using JIRA versions later than 3.0.3.
- OKTA-149329 – When converting individual users from individual to group assignments, admins were advised that some users who were eligible for conversion were not listed, when all eligible users were listed.
- OKTA-150318 – Okta improved the admin System Log message for Salesforce provisioning integration when any provisioning operation; for example, profile updates or push password, failed due to Salesforce API rate limit constraints.
- OKTA-150713 – Installation of the Okta Active Directory Agent on Windows 2012R2 server may fail in some situations.
-
AccessAudi (OKTA-149978)
-
FedEx US (OKTA-149239)
-
General Motors GlobalConnect (OKTA-149897)
-
Hellofax (OKTA-150611)
-
HelloSign (OKTA-149952)
-
iStock (OKTA-147972)
-
Linux Academy (OKTA-149374)
-
Microsoft Intune Company Portal (OKTA-149953)
-
NFL Game Pass (US) (OKTA-150001)
-
PayPal (OKTA-149500)
-
PlanGrid (OKTA-149956)
-
RingCentral (OKTA-149957)
-
RingCentral (UK) (OKTA-149976)
-
RingCentral SWA (OKTA-149388)
-
Segment (OKTA-149947)
-
Squarespace V6 (OKTA-149951)
-
TechSoup (OKTA-149955)
-
The Australian (OKTA-148795)
-
Twilio (OKTA-148606)
-
Upwork (OKTA-149097)
-
Webassessor (OKTA-149960)
-
WebEx (Cisco) (OKTA-141708)
- OKTA-135228 – For orgs with Push Groups enhancements enabled, Okta no longer updates the email address of a group when pushing updates to Google
- OKTA-136225 – Automatic activation of some Active Directory end users failed under certain circumstances.
- OKTA-137204 – A manual import from ServiceNow could not be completed.
- OKTA-138265 – AD-mastered users could not sign into Okta if their passwords contained unicode characters.
- OKTA-141457 – When users chose to reveal passwords, they could type characters into the password field.
- OKTA-141780 – The logo for the Generic RADIUS app could not be edited.
- OKTA-142922 – The System Log did not track successful IdP-initiated login events to Microsoft Office 365. This feature requires Okta customer support to enable it for your org.
- OKTA-143716 – The display date for notifications lists was not fully localized.
- OKTA-143904 – When using Group Push, unlinking a push group and keeping the group in target application prevented the group from being re-imported into Okta.
- OKTA-143942 – The System Log recorded client access policy denials as successful authentication events.
- OKTA-143955 – When users were deactivated, Admins were presented with a misleading message reading "Deactivation email sent to n people". The message text now correctly reads "n people deactivated".
- OKTA-144534 – The error messages on the sign page during Okta Verify MFA were not localized.
- OKTA-144750 – Some fields of failed MFA logins were not properly displayed in the Suspicious Activity Report.
- OKTA-145117 – The System Log entry corresponding to successfully importing a new member to an app group event was incomplete.
- OKTA-145625 – New customers were not able to setup Android for work with Managed Play Accounts.
- OKTA-146048 – When resetting a password, the New Password screen was not visible for some users.
- OKTA-146134 – End User App Settings on the General tab were not fully localized.
- OKTA-146457 – The Okta Privacy Policy Page did not render correctly on mobile devices.
- OKTA-146725 – The System Log entry corresponding to failed authentication to Active Directory had missing error codes
- OKTA-146744 – Time expressions were not localized in customized email templates.
- OKTA-147616 – Some Okta users were deactivated after the recent introduction of an Effective Date feature in the BambooHR app for organizations that were using the pre-start interval feature .
- OKTA-147970 – Admins could not configure mobile apps for an OAuth 2.0/OpenID Connect native client.
- OKTA-148451 – After changing a profile attribute, the profile sync from Okta to Active Directory did not start automatically.
- OKTA-148721 – When some users clicked on an expired forgot password link, Okta became unresponsive.
- OKTA-149046 – With the release of 2017.45, a handful of organizations with early access feature SAML_SUPPORT_ARRAY_ATTRIBUTES enabled may have experienced functional disruption to their AWS SSO flow. End users in impacted organizations either saw limited roles available when accessing AWS or were shown the error message: Your request included an invalid SAML response.
- OKTA-149283 – Time expressions were not localized in customized email templates.
- Authorize.Net Merchants (OKTA-148370)
- Barclaycard (OKTA-148011)
- Amazon (OKTA-149084)
- Amazon CA (OKTA-148898)
- Amazon DE (OKTA-148475)
- Amazon UK (OKTA-148897)
- Amazon Web Services (OKTA-149088)
- Booker (OKTA-146439)
- Carta (OKTA-147973)
- Citrix Receiver (OKTA-148386)
- CRG emPerform (OKTA-147542)
- EverBridge (OKTA-148344)
- FogBugz (OKTA-147545)
- Instagram (OKTA-148040)
- J.P. Morgan Markets (OKTA-148904)
- Knoll (OKTA-148051)
- LegalZoom (OKTA-147377)
- LucidChart (OKTA-147729)
- Maxwell Health (OKTA-147827)
- Microsoft Dynamics CRM Online (OKTA-149074)
- Mint Bills (OKTA-147827)
- MSDSonline (OKTA-147186)
- Ray Wenderlich (OKTA-148510)
- Subaru Partners (OKTA-148485)
- Uber (OKTA-148431)
- Vanguard (OKTA-148206)
- Virgin Pulse (OKTA-148204)
- Wescom Credit Union (OKTA-147541)
-
6sense ABM and Analytics (OKTA-148708)
-
TOPdesk 5 (OKTA-145409)
- OKTA-129750 – Adding a RADIUS app for RADIUS authentication did not enable the extra verfication end-user settings for some customers.
- OKTA-139543 – End users who were locked in Okta could connect to a VPN by providing the correct Multifactor Authentication token.
- OKTA-140434 – Provisioning errors were not tracked in the System Log for the GoToMeeting app.
- OKTA-142050 – Provisioning failure errors were not tracked in the System Log for the Salesforce app.
- OKTA-142758 – Some users could not use API token authentication with the IWA agent v1.11.0.
- OKTA-142976 – Activate User failed when called from the People page with a Pending Activation filter, if the Profile Editor used a Boolean custom attribute containing special characters.
- OKTA-144878 – The Push Verify Activation email templates were not translated consistently.
- OKTA-145578 – Admins could not edit group rules.
- OKTA-145605 – In most browsers a display issue prevented the addition of new groups to a group membership rule if there were more than 50 groups.
- OKTA-145720 – Updates to Okta user profiles failed when custom attribute values contained 4-byte UTF-8 characters.
- OKTA-145784 – In some cases, the user count displayed when converting individual users to group users was incorrect.
- OKTA-146210 – The help text for the Provisioning tab was not in the correct location.
- OKTA-146770 – Some text in Okta Verify localized for Chinese was not properly translated.
- OKTA-147366 – The link from the Admin console to the release notes failed.
- OKTA-147929H – Admins sending emails to large mail lists caused significant performance issues.
-
FedEx US (OKTA-146605)
-
Lead2Lease (OKTA-146486)
-
LeadLander (OKTA-144833)
-
Microsoft SharePoint Online Office 365 (OKTA-146946)
-
Mint (OKTA-147361)
-
Okta Community (OKTA-146382)
-
PlanGrid (OKTA-146598)
-
Proofpoint Secure Share (OKTA-145653)
-
Velaro (OKTA-132288)
-
Woopra (OKTA-146487)
-
Citrix Netscaler Gateway (OKTA-145561)
- OKTA-128067 – Okta to Microsoft Office 365 group synchronization sometimes caused Office 365 contacts to disappear from distribution groups. This correction applies to the Early Access feature to update the Member attribute in Office 365 groups when a new user is provisioned.
- OKTA-137826 – Admins could not assign an application to a user due to a mapping error when the user profile was mastered from an app with numeric attributes mapped to a fixed numeric value.
- OKTA-138151 – Group rules failed during JIT login and removed users from the group.
- OKTA-139772 – Events for the JIRA app were not tracked in the System Log.
- OKTA-140296 – Roles assigned for the Salesforce app were not saved.
- OKTA-140362 – When adding new members to an app group, the AppUser target in the System Log was not recording the DisplayName.
- OKTA-140509 – The Okta Verify activation link was not localized.
- OKTA-140900 – Email as a required factor for Multifactor Authentication did not work properly with RADIUS.
- OKTA-140980 – Some users were imported from LDAP incorrectly and became Okta-mastered because of an invalid date format.
- OKTA-141137 – Some mobile administrators could not change mobile policy rules.
- OKTA-141984 – When attempting to change an expired password, some users received an Unable to connect to the server error.
- OKTA-142114 – Custom Enterprise iOS apps could not be uploaded to hosted app store if they are not properly signed.
- OKTA-142627 – System Log events were not generated for voice call factor attempts.
- OKTA-143910 – Some security Network Zones could not be deleted.
- OKTA-144104 – Words and phrases in several screens were not localized correctly.
- OKTA-144294 – The policy screen for apps was not visible for some organizations.
- OKTA-144432/OKTA-144891 – The Sign In error message was not always localized.
- OKTA-144652 – The French translation contained double quotation marks (") instead of apostrophes (').
- OKTA-144661 – The country list used when setting up an SMS factor was not sorted.
- OKTA-145004 – The link for an email confirmation change page was not translated.
- OKTA-145630 – The enhanced profile page was not accessible to users of the Developer Paid Edition.
- OKTA-146566 – AUser not assigned to app error was returned from a GET/oauth2/v1/authorize for OAuth clients with a custom client ID.
-
Adjust (OKTA-145895)
-
AlertLogic (OKTA-145349)
-
AppRiver (OKTA-145520)
-
Code42 Single Tenant (OKTA-146498)
-
D&B Hoovers (OKTA-145596)
-
DealerTrack (OKTA-145445)
-
DriveHQ (OKTA-145588)
-
EchoSpan (OKTA-146213)
-
eWallet ADP (OKTA-144251)
-
FedEx US (OKTA-145604)
-
Gandi.net (OKTA-145396)
-
GoodHire (OKTA-145735)
-
HealthEquity (OKTA-145024)
-
iSqFt (OKTA-146076)
-
My Health Online (Sutter Health) (OKTA-146240)
-
MySonicWall (OKTA-144680)
-
NFL Game Pass (OKTA-145211)
-
Papyrs (OKTA-145431)
-
Right Networks Server (OKTA-145270)
-
Site24x7 (OKTA-143583)
-
Stamps.com (OKTA-146045)
-
Tenable Support Portal (OKTA-144822)
-
Visual Studio (OKTA-143568)
-
ZeroFox (OKTA-145166)
- OKTA-127045 – The Email Verification, Email Factor Challenge and Send Push Verify Activation Link email templates were not translated.
- OKTA-140149 – Error messages for failed Active Directory authentications weren't recorded in the System Log.
- OKTA-140515 – Okta Verify push notifications were displayed in English, regardless of the org's configured language.
- OKTA-141158 – The Privacy Policy page did not display correctly on mobile devices.
- OKTA-141770 – Adding specific applications to the list of apps managed by an App Admin failed if the app name contained the pipe character ( | ).
- OKTA-141960 – For orgs using the EA feature Graph API provisioning for Microsoft Office 365, updating O365 group membership using Group Push failed.
- OKTA-142985 – Admins were unable to reuse a group name with Group Push rules if the original group was deleted.
- OKTA-143578 – When attempting to convert users from individual to group-based assignments, an incorrect banner message displayed.
- OKTA-143855 – The Change Email Confirmation email template was not translated.
- OKTA-144432 – When resetting a password, an error message sometimes displayed in English instead of the language configured in the browser.
- OKTA-144435 – Some text on the Okta Sign In screen was not translated into Danish.
- OKTA-144437 – When using an expired reset password link or an expired unlock account link, the French error message was not consistent with the English.
- OKTA-144657 – When selecting a long security question in French, the field extended beyond the dialog box.
-
OKTA-144928H – Deleting an Admin who had previously approved self-service app requests sometimes impacted the ability of other Admins to approve future requests.
-
Beeline TMS (OKTA-144601)
-
GoToMeeting (OKTA-144380)
-
Instacart (OKTA-144442)
-
iSupport (OKTA-144603)
-
Microsoft SharePoint Online Office 365 (OKTA-144418)
-
Schwab Personal Finance (OKTA-144444)
-
Spectrum Time Warner Cable (OKTA-144602)
-
UsabilityHub (OKTA-144596)
-
Virgin Pulse (OKTA-144600)
-
FreshService (OKTA-138139)
-
Mobi Wireless Management (OKTA-142935)
- OKTA-136019 – The corresponding user not found error was missing from the WebEx app.
- OKTA-139077 – In the Okta Authentication Notification email, text under Sign-In Details appeared in English regardless of the configured language.
- OKTA-139667 – The link to reset password by email was visible even when email was disabled as a recovery factor.
- OKTA-140535 – The error message that appears when an invalid phone number is entered during SMS enrollment was not correctly translated into Finnish.
- OKTA-141876 – Deleting Okta users with Username/Login attribute values containing 99 or 100 characters failed.
- OKTA-143329 – App Administrators received a 403: Forbidden error when attempting to access the Applications page.
- OKTA-143712 – App Administrators could not accept or save new app assignments.
- OKTA-143913 – Existing App Administrators could not be removed from that role.
-
AWS Console (OKTA-143728)
-
Paylocity Web Pay (OKTA-143122)
-
LogicMonitor (OKTA-142693)
-
OKTA-136489 – The Webex Personal Room URL failed to update when the end user profile was updated. The fix adds a check-box on the Provisioning tab for the Webex (Cisco) app to enable such updates.
- OKTA-137447 – When importing end users from an Oracle OID LDAP server, only some were imported successfully.
- OKTA-138926 – The error message that displayed on the MFA verification screen displayed in end users' locale language instead of the default browser language.
- OKTA-140027H - When integrating AWS with Okta, adding a 40th Connected Account ID failed.
- OKTA-140622 – When importing or provisioning end users in Salesforce, not all profile types were available.
- OKTA-140486 – Some of the text in the Okta MFA challenge screen displayed in English instead of Italian.
-
OKTA-141462 – Signing into Okta using certificate-based primary authentication failed for some end users.
- OKTA-142196H – In orgs with the Early Access MFA feature, Android device users were not prompted for MFA after entering their PIN even though their org had an MFA policy configured to challenge end users.
- OKTA-143003H - Some users who had not yet activated their Okta account were locked in the Reset Password status.
- OKTA-143497H – Error messages on the Okta Sign In page appeared in English regardless of the configured language.
-
J.P. Morgan Markets (OKTA-142766)
-
Newport Group (OKTA-142163)
-
United Health Care (OKTA-142401)
- OKTA-133742 – An http 429 response code caused a cascading effect on end users' Home pages.
-
OKTA-134017 – Clicking Show More in the System Log was slow to yield results.
- OKTA-134515 – AD provisioning failures generated the following Dashboard Task: Automatic activation of user <user name> to app Active Directory failed: null.
- OKTA-137109 – In some cases, Okta returned response code 200 with a SAML response in the OPTIONS request, and in other cases, response code 302. Response code 200 is now returned in all cases with no SAML response to an OPTIONS request.
- OKTA-137268 – The ExactTarget app failed to create new users when provisioning was enabled.
- OKTA-138118 – The user reactivation function failed during provisioning for the UltiPro app.
- OKTA-138962 – The Okta Sign In page did not resize automatically in small browser windows.
-
OKTA-140014 – The content of the Event info column in some System Log entries displayed incorrectly.
- OKTA-140484 – Only a partial permissions list was displayed when assigning the Salesforce app to a group or user.
- OKTA-140517 – During the change password flow, the "success" message in the Change Password dialog box displayed in English regardless of the language set in users' Display Language.
- OKTA-140628 – The firstname and lastname fields displayed long values incorrectly on the Okta Home page.
- OKTA-140859 – The error message that end users receive when attempting to update their profile was not localized when the system mode was degraded.
- OKTA-141162 – During the reset password flow, the Reset Password dialog box displayed an untranslated message when users' Display Language was set to Portuguese.
- OKTA-141184 – An email was sent to end users even though email password reset was disabled in the Account Recovery settings when an admin presses return.
-
OKTA-142607H SP-initiated authentication to the Skype for Business app failed in orgs configured with the New Okta Sign In flow.
-
Amazon Web Services (OKTA-141303)
-
AWS Console (OKTA-140247)
-
Elegant Themes (OKTA-141769)
-
iConnectData (Comdata) (OKTA-140618)
-
MailRoute (OKTA-141171)
-
MB Marketing (OKTA-141170)
-
Nexus Payables (OKTA-141768)
-
Track What Matters (OKTA-141925)
-
Veeam (OKTA-141849)
-
Workable (OKTA-141476)
-
Wufoo (OKTA-141468)
-
OKTA-118881 — The setup instructions for the On Prem Sharepoint app contained an incorrect PowerShell command.
- OKTA-129237 — Deleting a user who was excluded from an MFA rule made the rule impossible to modify.
- OKTA-131859 — Custom attributes deleted from the Add Attribute page did not appear in the Refresh Attribute list in the Pick Schema Attributes window.
-
OKTA-132168/138650 — Some text in the Account Unlock Requested email appeared in English regardless of the language configured for the org.
- OKTA-133088 — The recommended sizes of customer-provided images (for example, in the Edit Logo dialog box) were incorrect and inconsistent.
- OKTA-133571 — When prompted to enroll a phone number for self-service password reset at sign in, the enrollment failed if the end user had at least one second factor already enrolled and had not been challenged recently for MFA.
-
OKTA-134963 — When using Find groups by rule to create a list of groups to push to an app (for example, Active Directory), the list included some groups that came from the same app.
-
OKTA-137429 — In reset password flows, the Send Message dialog box appeared in English regardless of the language configured for the org.
- OKTA-137750 — In the Welcome screen displayed to new end users, users' names were cut off if they contained diacritical marks (for example, umlauts and accents).
- OKTA-138809 — Error messages displayed in the Reset Password dialog box appeared in English regardless of the end user's configured Display Language.
- OKTA-139085H — When the iOS 11 native Mail app is configured to use Modern Authentication for Okta-mastered users who are assigned to an Office 365 WS-Fed app using either the Profile Sync or User Sync provisioning type, the Mail app continually prompts end users for a password. For details, see Announcements.
- OKTA-139087 — In the User Activation email, the text of the Activate Okta Account button appeared in English regardless of the language configured for the org.
- OKTA-139195 — When single quotation marks (') were used in UI labels and email templates, the single quotation mark did not appear and other unexpected text displayed.
- OKTA-139337 — Automatically pushing profile updates to Salesforce sometimes failed.
- OKTA-139584 — The SAML forceAuthN request prompt included a Remember me option. This option has been removed from this re-authentication flow.
- OKTA-139644 — When assigning Salesforce to Okta end users, profiles associated with the Customer Community Plus license did not appear in the Profiles drop-down list.
- OKTA-140918 — Some SP-initiated log-in flows to SAML apps failed due an issue decoding the SAML request.
- OKTA-141461H — Workday imports failed for users whose profile did not contain custom report data.
-
6sense ABM AND Analytics (OKTA-139419)
-
Azure Portal Login (OKTA-139980)
-
Bank of America (OKTA-139976)
-
BlueStar (OKTA-139997)
-
CallTower (OKTA-139996)
-
Cover-More Travel Insurance (OKTA-139393)
-
DNSPod (OKTA-139558)
-
ePayslips (OKTA-139534)
-
Fedex United Kingdom (OKTA-139977)
-
Filesanywhere (OKTA-140001)
-
FINRA (OKTA-139416)
-
Gliffy (OKTA-139954)
-
iOvation (OKTA-140002)
-
ISS ProxyExchange (OKTA-139632)
-
KnowledgeHound (OKTA-138418)
-
MCM (OKTA-140003)
-
Micro Focus (OKTA-139651)
-
Microsoft Office 365 (OKTA-138224)
-
MURAL (OKTA-140000)
-
MyActiveHealth (OKTA-139635)
-
Salesforce: Marketing Cloud (OKTA-139532)
-
SecureMail Cloud (OKTA-139535)
-
Site24x7 (OKTA-139575)
-
Socialite (OKTA-139592)
-
Synnex Vendor Portal (OKTA-139979)
-
Vistaprint (OKTA-140142)
-
Yield Software (OKTA-139634)
- OKTA-115069 — Salesforce import jobs were very slow and delayed dependent app activity.
-
OKTA-129315H — No factors appeared in the Reset Multifactor Authentication dialog box even though at least one factor was configured for the user.
- OKTA-133052 — Not all topic labels on the new user Security page were translated successfully.
- OKTA-134449 — Add user to group membership events in the System Log did not include Display Name or Alternate ID.
- OKTA-136849 — First names, last names, and middle names containing non-ASCII characters did not display legibly when users were provisioned to Adobe CQ.
- OKTA-137397 — system.na3.netsuite.com was not available in the Instance Type drop-down menu on the NetSuite App Settings page.
- OKTA-138392 — App sign on rules designed to allow trusted iOS mobile devices to access WS-Federation and SAML apps failed if the policy included a Deny rule with a higher priority.
- OKTA -138449 — When safe mode was employed, Duo was disabled even when it was the only MFA factor.
- OKTA-138982 — Admins were unable to download a CSR for setting up Apple Push Notifications. The error was caused by including special characters in the org name.
- OKTA-139256 — Activation emails in the Dutch language failed to display the correct username.
- OKTA-139855 / OKTA-105855 — Instructions for setting up the SharePoint On-Premises app referenced a file (CreateSPTrustedTokenIssue.ps1), but did not include the location of the file.
-
Buffer (OKTA-139413)
-
Campaign Monitor (OKTA-138879)
-
CareFirst (OKTA-138443)
-
Client Track (OKTA-138559)
-
CultureGrams (OKTA-139637)
-
Docebo (OKTA-139636)
-
EmblemHealth (OKTA-139302)
-
Ingram Micro (OKTA-139579)
-
myresourcelibrary (OKTA-138438)
-
OPP (OKTA-139633)
-
Principal Advisor (OKTA-138902)
-
Principal Financial Personal (OKTA-138904)
-
Spectrum Time Warner Cable (OKTA-139554)
-
Symantec Hosted Endpoint (OKTA-138267)
-
ShareFile (OKTA-139210)
- OKTA-114208 – login.okta.com now supports Preview and Developer orgs.
- OKTA-118583 – G Suite profile pushes were not successful for existing end users.
- OKTA-126080 – Push Groups failed when a user belonging to the group being pushed was deleted through the Dropbox app.
- OKTA-128444 – Under certain circumstances, incorrect System Log events were generated for Password reset operations.
- OKTA-129837 – Time unit text (days, years, months, etc.) in the Okta Welcome email appeared in English, rather than the end user's configured language.
- OKTA-130218 – Using the Show More option changed the view order of Group Assignments.
- OKTA-133078 – A System Log event was not generated when a user rejected an Okta Verify push notification.
- OKTA-133791 – The wrong year appeared in the footer of end user Home page if the Okta Home footer was disabled in Display Options.
- OKTA-133814 – Error messages did not display for some user lifecycle operations.
- OKTA-134396 – The UI incorrectly showed support for linking to a group in Office 365. Linking to a group is only supported for AD, Box and G Suite (see Using Group Push).
- OKTA-135164 – Read-Only Admins were unable to view the new Settings page, which is an Early Access feature under Provisioning.
- OKTA-135334 – There was a typo in the Generic RADIUS App Sign-On tab.
- OKTA-136213 – Clicking the Disconnect... link on the User Profile page did not disconnect users that were profile-mastered by Active Directory.
- OKTA-136844 – App logos could not be uploaded when creating a new SWA app through the App Integration Wizard.
- OKTA-137054 – The download link for the RSA SecurID agent in Security > Multifactor pointed to the wrong target.
- OKTA-137226 – Samanage API authentication failed when trying to authenticate through Okta.
- OKTA-137285 – Some apps could not be configured for provisioning when the Early Access Provisioning Settings page feature was enabled.
- OKTA-137337 – The Admin OAN Self Service page displayed a 500 Internal Server Error.
- OKTA-137429 – Not all fields were localized as specified following a Self Service Password Reset request.
- OKTA-137555 – The
AssertionConsumerServiceURLattribute in a SAML authentication requests matched one of the configured SSO URLs but an error was returned. - OKTA-138051 – Some fields and errors messages used in the Okta sign in flow were not properly localized.
- OKTA-138219 - Updated permissions for Group and User Admin roles.
-
Azure Manage (OKTA-137231)
-
Box (OKTA-138287)
- Shiftboard (OKTA-137224)
-
Truckstop.com (OKTA-137817)
-
Salesforce.com (OKTA-137272)
- MuleSoft - Anypoint Platform (OKTA-135779)
- OKTA-131120 – Box provisioning errors were not logged in the new System Log.
- OKTA-131895 – With the new sign-in flow enabled, Windows 10 phone users were unable to sign in to the following Microsoft Office 365 apps: Delve/Microsoft Flow/Microsoft Power BI/Outlook Groups/Skype for Business.
-
OKTA-133446 – The wrong error message was displayed when a self-service password reset operation was attempted for a user who had not setup their recovery security question.
- OKTA-133837 – The default time range in the new System Log was sometimes out of sync with the actual time zone, causing the most recent events not to be reported.
- OKTA-134317 – The German translation for Okta password requirements contained a typo.
-
OKTA-135367 – Inactive users in SmartRecruiters were imported to Okta as active users.
- OKTA-135970 — The Display Language section of the end-user Settings page was not fully localized.
-
OKTA-135970H — AD Group Push failed following group membership updates.
- OKTA-137133 – Users sometimes saw a double sign in prompt to sign in to Okta for SAML apps.
- OKTA-137280 – Configuring CORS origin in Chrome sometimes resulted in an internal server error.
-
Air France (OKTA-136448)
-
Amazon Developer (OKTA-136282)
-
Hightail (OKTA-136365)
-
Microsoft Office 365 (OKTA-136263)
-
Vungle (OKTA-136483)
- OKTA-123583 – Some error messages were incomplete if there were errors updating user profiles during import.
- OKTA-127450 – The Add policy button was not disabled for Org Admins since they cannot create authorization server policies.
- OKTA-129771 – After you configured a custom sign out page, some users were incorrectly directed to the primary sign in page during authentication.
- OKTA-131502 – Microsoft Office 365 email accounts of Samsung SAFE device users were deactivated when any EAS sign on policy settings in the app instance were changed.
- OKTA-132173H – The Starleaf and Cisco ISVs did not receive the active attribute when users were updated.
- OKTA-133546 – Some end users could not open Microsoft Office 365 online files with their desktop version of MS Office 2010.
-
OKTA-135969H – After enabling provisioning, existing group did not appear in the Microsoft Office 365 group assignment screen.
- OKTA-133671 – When viewed by Group administrators managing users in specific groups, the Add Person page incorrectly identified the Group field as optional.
- OKTA-133546 – End users could not open Microsoft Office 365 online files with their desktop version of MS Office 2010.
- OKTA-133671 – When viewed by Group administrators managing users in specific groups, the Add Person page incorrectly identified the Group field as optional.
- OKTA-134566 – Authentication failed during provisioning for the DocSend app.
-
OKTA-135230/OKTA-132277 – For some apps, some inactive users could not be deactivated.
- OKTA-135451 – Some Dutch and Swedish translations were missing for the sign-in widget.
- OKTA-136959 – Admins could not configure Android for Work.
-
AlertLogic (OKTA-136168)
-
AST Equity Plan Solutions (OKTA-136206)
-
Box (OKTA-136541)
-
Confluence (Atlassian) (OKTA-136065)
-
Microsoft Office 365 (OKTA-136263)
-
Ultimate Software (OKTA-135120)
-
Webassessor (OKTA-136220)
- OKTA-128784 – Sign-on policy outcome reason events did not have enough granularity in the outcome results.
- OKTA-130926 – Some third party notice links redirected to the wrong notice.
- OKTA-131320 – While creating customized email templates, localization was inconsistent.
- OKTA-133542 – When importing from the Smart Recruiters app into Okta, inactive users were treated as active.
- OKTA-133569 – SAML requests with redirect binding dropped the relay state.
- OKTA-133702 – Sometimes users were not re-prompted for credentials when signing in to a SAML app.
- OKTA-134184 – Administrators did not receive emails for User Lockout events.
- OKTA-134207 – Error messages that displayed during change and reset password flows did not match the language of the user interface.
- OKTA-134640 – When enrolling an iPad iOS device version 10.3.3 into OMM using the Okta Mobile Application, the Mobile Native Applications were not pushed to the device.
- OKTA-135230/OKTA-132277 – For some apps, some inactive users could not be deactivated.
-
ADP iPayStatements (OKTA-134635)
-
MIR3 inEnterprise (OKTA-133844)
-
NGS Connex (OKTA-133857)
-
Pivotal Academy (OKTA-134826)
-
Seek (AU) - Employer (OKTA-134584)
-
SyncBASE/OPTRACK (OKTA-133882)
-
The Australian (OKTA-134585)
- OKTA-126117 – Some users received incorrect lockout messages during Okta sign in.
- OKTA-128212 – The user name failed to autopopulate in the new sign-in screen when using On-prem Multifactor Authentication.
- OKTA-128721 – Custom SMS templates allowed messages longer than 160 characters.
- OKTA-129383 – Installation for the Okta On-premises Provisioning Agent failed when an Internet Explorer proxy was in use.
- OKTA-130314 – Selecting the Previous button caused an error during SAML app creation.
- OKTA-130513 – The link for the Apple MDM certificate renewal was incorrect.
- OKTA-130692 – System Log 2.0 dropdown lists did not scroll in the advanced filter dialog..
- OKTA-131282 – Okta Verify Push sometimes incorrectly returned an error.
- OKTA-131366 – Group app assignment for the Microsoft Office 365 app sometimes failed.
- OKTA-131421 – The Samanage app did not support a fully configurable ACS URL.
- OKTA-132091 – In System Log 2.0 the Show More option failed for some searches.
- OKTA-132097 – The Show Temporary Password feature did not work for some users.
- OKTA-132012H – Some users with accounts create with Just In Time (JIT) provisioning were locked in the Pending Activation state.
- OKTA-132733 – Some users could not update the technical contact for their accounts.
- OKTA-132774 – Some automatic profile push updates failed for the Jive app.
- OKTA-132779 – Forced Authentication did not work properly for some apps.
- OKTA-132846 – Multifactor authentication did not work properly for newly enrolled factors.
- OKTA-133611 – Default mapping did not map the correct fields in the ServiceNow UD app.
- OKTA-133751 – The Microsoft Office 365 instructions link did not work.
- OKTA-134149 – Scheduled updates from the ServiceNow app did not import users to Okta.
- OKTA-134407H – The Admin. Dashboard did not load menus and tasks when a banner was displayed.
-
Aviso (OKTA-133339)
-
Citibank (OKTA-133064)
- Eventbrite (OKTA-133710)
- Fastly (OKTA-133683)
-
FedEx US (OKTA-133418)
-
Flickr (OKTA-133397)
-
Huddle (OKTA-132781)
- Kammer van Koophandel (OKTA-134302)
- Symantec Email Quarantine (OKTA-133845)
-
Vitality (OKTA-133361)
-
Cornerstone OnDemand (OKTA-132824)
- OKTA-115069 — Importing users from Salesforce sometimes took an excessive amount of time.
- OKTA-123695 — /api/v1/apps/:appId/groups didn’t return groups if the specified app was inactive.
- OKTA-126820 — A 403 error occurred when clicking Temporary Password to reset a password.
- OKTA-129089 — Provisioning for the GoToMeeting app failed when attempting to authenticate API credentials.
- OKTA-130934 — Error messages that display to help enforce password policy rules displayed in English regardless of the configured language.
- OKTA-131339 — Provisioning users to the Adobe CQ SAML app sometimes failed.
- OKTA-131784 — Identity provider JIT reactivation of users sometimes failed when there were configured group assignments.
- OKTA-132207 — Sometimes the mapping between the external Microsoft user and the Okta user was inaccurate.
- OKTA-132290 — In the Convert Group Assignments UI, the number of group assignments to convert did not return to zero after clicking Convert All.
- OKTA-132516H — Okta's plugin for the Chrome browser consumed an excessive amount of memory.
- OKTA-133405H — In Identity Provider Authentication Settings, custom attributes did not appear in the Match against list.
-
Confluence (Atlassian) (OKTA-132033)
-
Humanity (OKTA-131083)
-
Mimecast Personal Portal v3 (OKTA-131191)
-
Saba (OKTA-132037)
- OKTA-117073 — Some links and buttons in Okta were not illuminated when they were in focus.
- OKTA-117081 — A 500 error occurred when attempting to access some SAML apps configured to prompt for MFA and enabled to honor Force Authentication.
- OKTA-125258 — Role options for all groups continued to appear after the AWS web app was changed to individual assignment.
- OKTA-128396 — If Voice Call was the last MFA method used, deleting the Forgot Password Voice Call phone number in end-user account settings blocked subsequent access to those settings.
- OKTA-128740 — OMM-enrolled Android users' custom email settings were lost after admins updated certain EAS settings for the Office 365 app in Okta.
-
OKTA-129248 — Importing users from SuccessFactors failed in certain circumstances.
- OKTA-129256 — Self-service password reset emails did not display in the intended language.
- OKTA-130069 — Several links and input fields on the Okta Sign In page customized to display in German continued to display in English.
- OKTA-130764 — Clients with a token_endpoint_auth_method set to client_secret_post did not have a selected radio button on the Client Credentials display.
- OKTA-131113 — The reset password link contained an error in the German translation of the Okta-generated Reset Password email.
-
OKTA-131294 — Okta reported an error when a SAML 2.0 Identity Provider (IdP) was created and some fields were omitted.
- OKTA-131504 — The order in which administrator types were listed on the Administrators page and the Add Administrator dialog box did not match.
-
OKTA-131875H — Removed a potential cross-site scripting vulnerability from setup instructions for some SAML apps.
-
10000ft (OKTA-129322)
-
Basecamp (OKTA-131080)
-
CSCglobal (OKTA-130350)
-
Egencia (OKTA-131089)
-
FlipKart (OKTA-130780)
-
Great-West Life (OKTA-131687)
-
MassMutual RetireSmart (OKTA-131686)
-
Microsoft Account (OKTA-130765)
-
MURAL (OKTA-131679)
-
ProofHQ (OKTA-131081)
-
ServiceNow - Eureka and later releases (OKTA-129647)
-
Veeam (OKTA-130821)
-
VMware Partner Central (OKTA-130208)
-
Yahoo Mail (OKTA-131688)
-
LiquidFiles (OKTA-129648)
- OKTA-117352 – When validating the names of scopes for social identity providers, Okta didn’t enforce the restrictions specified in the OAuth 2.0 spec.
- OKTA-118336 – Signing in to the Oracle Tab app for Android devices failed in orgs where the New Okta Sign-In page was enabled.
- OKTA-119679 – Importing users from Ultipro caused null or empty errors.
- OKTA-121703 – A newly created app failed to submit credentials in Firefox when using the Okta browser plugin.
- OKTA-121819 – Read-Only admins were denied display of Yubikey reports.
- OKTA-121924 — Users could not update Duo information within Okta during sign in.
- OKTA-122419 — A French Polynesian mobile number was shown as invalid during SMS Enrollment.
-
OKTA-123695 – Users could not view groups assigned to inactive applications.
- OKTA-124263 – Some user information failed to auto-populate in the Kronos app when the Okta plugin for Internet Explorer was installed.
- OKTA-125248 – Group Push enhancement allowed the renaming of Google groups if spaces were in the title—even when the renaming feature was disabled.
- OKTA-125678 – Enabling the Okta plugin made the Save As button of an internal app inoperative.
- OKTA-126768 – Customized language sign-in labels failed to display correctly for Chinese, Portuguese, and Dutch.
- OKTA-127353 – MFA for Chromebooks did not display the New Okta Sign-In page.
- OKTA-127377 – The Okta browser plugin sparked two password prompts on a single page.
- OKTA-128184 – A typo was found in the Dutch version of Okta Verify with Push.
- OKTA-128891 – A sign-in message displayed when signing out of a custom SAML app.
- OKTA-128945 – A new org could not successfully push groups to G-Suite.
The following SWA apps were not working correctly and are now fixed:
-
Cover-More Travel Insurance (AU) (OKTA-130939)
-
Mapbox (OKTA-130787)
-
Skylight (OKTA-130315)
-
Yahoo Mail (OKTA-130149)
- OKTA-116468 – The upgrade to Jira Authenticator v3.x altered the sign in flow and caused mixed results when users tried to access Jira.
- OKTA-120029 – The Confluence on-premises app redirected to the wrong authentication URL.
- OKTA-122794 – Some apps with a SAML 2.0 sign on mode and some Inbound SAML setups failed to use a SHA-256 certificate..
- OKTA-124753 – Read-Only Admins were able to upload Yubikey seed files.
- OKTA-124758 – The Fresh Service app required a SHA certificate that differed from the Okta Security Certificate Fingerprint.
- OKTA-124989 – The People page displayed an inaccurate count of users with expired passwords, and incorrectly listed some users as Active.
- OKTA-125263 – Active Directory-mastered users were unable to reset their passwords through SMS or email.
- OKTA-125882 – No confirmation button was visible when users signing in through O365 were prompted to select a security image.
- OKTA-126811 – Salesforce sandbox provisioning failed to import portal users.
- OKTA-127423 – An excessive import duration caused Workday to time out.
- OKTA-128360 – Scheduled imports for groups in O365 failed repeatedly.
-
OKTA-128814H – API validation failed when updating users of the Org2Org if the Country attribute was not set.
- OKTA-129862 – Authentication for the O365 app did not support additional WS-Fed parameters sent by the Outlook plugin.
- OKTA-129970 – Long running reports caused Workday imports to fail.
Doba (OKTA-129851)
Jitterbit (OKTA-129667)
Moqups (OKTA-130022)
VMware Horizon View VDI (OKTA-129398)
- OKTA-118336 – Signing into the Oracle Tap Android application failed on Android devices, while the New Sign-in Page was enabled.
- OKTA-122975 – After clicking some apps on the Okta dashboard in a Safari browser, the transition page that displays before the app opens did not render correctly.
- OKTA-124320 – Some users were unable to register U2F keys to use for MFA.
- OKTA-124802 – In some cases, authentication failed when configuring SpringCM provisioning.
- OKTA-125181 – The wrong error was reported and Okta became non-responsive after entering an incorrectly-formatted username in the Validate Configuration field (LDAP integration settings).
- OKTA-125362 – Trying to use the administrator option Show XML in the ServiceNow app failed in the Firefox browser with the Okta plugin enabled.
- OKTA-125431 – In some circumstances, when pushing a group from Okta to AD, only some group members were pushed successfully.
- OKTA-125850 – Users could not access some applications whose Sign On policy called for multifactor authentication.
- OKTA-126804 – System Log entries for Add user to group membership events were missing Display Name information.
- OKTA-126950 – The security question presented to end users during the Okta account recovery flow was in English when the end user Display Language was set to a non-English language.
- OKTA-126996 – SP-initiated logins to apps configured to redirect to a custom log-in page failed in orgs with the New Okta Sign In Page enabled.
- OKTA-127389 – Attempting to download the root certificate for certificate-based authentication for the Microsoft Office 365 app failed when the org name contained certain non-alphanumeric characters.
- OKTA-127651 – In some cases, saving changes to Microsoft Office 365 group app assignments caused a 500 error.
- OKTA-128182 – In orgs with multiple AD domains, user assignments could not be confirmed for imported users who were already imported from another AD domain.
-
OKTA-129014 – The dropdown that controls Authorization Server lifecycles failed to display properly if you navigated directly to a tab or refreshed a tab other than Settings.
- OKTA-129291 – The Okta EL function getFilteredGroups was not compatible with SAML attributes in the App Wizard or in AppUser profile mappings.
-
AvantLink (OKTA-128518)
-
Chase Bank - Personal (OKTA-127948)
-
Plex (OKTA-128351)
-
Redis Labs (OKTA-128346)
-
Vanguard (OKTA-128343)
-
Wells Fargo - Personal (OKTA-128350)
- OKTA-103403 – Some admins were unable to import users.
- OKTA-109790 – Following installation, the beta LDAP agent caused some previously imported users’ names to change.
- OKTA-117134 – The Okta browser plugin didn't detect the change password form of an Okta-managed app and didn't offer to save the password.
- OKTA-118715 – The Okta browser plugin displayed the Save this password in Okta banner to users who did not have a valid Okta session.
- OKTA-120788 – Some custom Schema Attributes failed to save.
- OKTA-124287 – The sign-in button for an Okta-managed app was inoperative.
- OKTA-125213 – The Okta browser plugin didn't offer to save the password of apps hosted on the local host.
- OKTA-127162 – Users received error messages when attempting to deactivate users for the ZScaler app.
- OKTA-128545 – Provisioning for the Coupa app failed for some users.
-
Cascade HR (OKTA-128216)
-
cloudHQ (OKTA-127742)
-
Microsoft SharePoint Online Office 365 (OKTA-127652)
-
The Street (OKTA-127935)
- OKTA-122440 – Users trying to change their current password received error messages when the password contained some html tag elements.
- OKTA-123785 – For some users with Network Zones enabled, the Messages description under VPN Notification failed to display correctly.
-
OKTA-125850H – A 404 error occurred when attempting to access some SAML apps configured to prompt for MFA and enabled to honor Force Authentication.
- OKTA-125885 – After selecting Show More to expand a list of over twenty groups, Admins were unable to change the group priority.
- OKTA-127051 – Searching for apps in Preview orgs sometimes resulted in slow response times.
- OKTA-127905 –Okta Mobile Connect Single Sign On was temporarily unusable due to missing text and buttons.
- Artifactory (OKTA-113892)
- Advent Black Diamond (OKTA-127375)
- Citrix Netscaler Gateway (OKTA-127025)
- In Honda (OKTA-126638)
- Mass Mutual (OKTA-127331)
- Miles & More (OKTA-125495)
- Zang OnEsna (OKTA-127201)
- Zoho Invoice (OKTA-127246)
- OKTA-112868 - Users launching the same app in multiple windows were prompted to confirm their identity to stay signed in.
- OKTA-119445 - The Profile Editor failed to load when an inactive or deleted Directory Integration was still listed under Profile Masters.
- OKTA-119458 - When registering an Android device in OMM using AFW, the Play Store for Work was not populated with apps.
- OKTA-120029 - Some users with custom URL context paths failed to authenticate.
- OKTA-120886 - When an Okta alert warned users about their expiring session, some users experienced errors in their workflow.
- OKTA-121390 - Importing active users failed in some cases.
- OKTA-121705 - Updating user profiles failed in some cases.
- OKTA-121859 - Provisioning failed when the securityQuestion and securityAnswer fields were left empty in User Profile Mappings.
- OKTA-125051 - Text in end users' Display Language setting was not localized in the configured display language.
- OKTA-125295 - Some groups failed to display users, and users could not be added nor removed.
- OKTA-126360 - The State field under GeographicalContext failed to populate in the System Log.
- OKTA-127512H - The Okta service sent admins multiple summary emails for the same import event.
-
Egnyte (OKTA-117225)
-
Panorama9 (OKTA-125364)
-
Sugar CRM (OKTA-67252)
-
Akamai EdgeControl (OKTA-126758)
-
ClearCompany (OKTA-126049)
-
CloudCheckr (OKTA-126623)
-
CT Lien Solutions (OKTA-117451)
-
Evernote Business (OKTA-125498)
-
Flickr (OKTA-126727)
-
Flurry (OKTA-126629)
-
G Suite (OKTA-125961)
-
HeyOrca (OKTA-126622)
-
PeopleStrategy (OKTA-126913)
-
ReadMe.io (OKTA-126630)
- OKTA-99850 – Updating the OpenID Connect property max_age incorrectly caused a new session to be created, which updated the createdAt timestamp.
- OKTA-122136 - Some users were unable to sign in to new apps.
- OKTA-122431 - In orgs with a Lock out policy configured, some Active Directory (AD) users could sign in to Okta when the AD agent was not functioning.
- OKTA-122637 – Pushing groups to an app failed if user profiles contained certain emoji characters.
- OKTA-122983 - Users with configured SMS authentication received an error message when entering their phone number to reset their password or unlock their account.
- OKTA-123686 – The Preview Sandbox banner appeared twice in the Welcome screen presented to new Okta users.
- OKTA-123939 – Okta Sign-In page failed for AD-mastered users who had not configured a security question and no password reset email was sent to them.
- OKTA-124354 - Duplicate users caused match conflicts during some AD imports.
- OKTA-125156 - Some admins were unable to reorder their Access Policies for Authorization Servers.
- OKTA-125167 - Some error messages were sent without text, causing an error.
- OKTA-127155H – OIDC/OAuth2 requests failed to respect default SAML IdP configuration.
-
CloudHealth (OKTA-123984)
-
OpsGenie (OKTA-120528)
-
AdMob (OKTA-125591)
-
Adobe Creative (OKTA-125497)
-
DoubleClick for Advertisers (OKTA-125592)
-
DoubleClick For Publishers (OKTA-125960)
-
Dropbox Business (OKTA-125948)
-
Firebase (OKTA-125593)
-
FullStory (OKTA-125929)
-
Gliffy (OKTA-125634)
-
Google Data Studio (OKTA-125788)
-
Google DoubleClick Ad Exchange (OKTA-125820)
-
Google Merchant Center (OKTA-125793)
-
Google Partner Dash (OKTA-125501)
-
Google Picasa (OKTA-125772)
-
Google Play (OKTA-125768)
-
Google Plus (OKTA-125854)
-
Google Search Console (OKTA-125709)
-
Google Tag Manager (OKTA-125857)
-
Google Voice (OKTA-125859)
-
Level 3 Communications (OKTA-125494)
-
Rise Vision (OKTA-125872)
-
Teamviewer (OKTA-125292)
-
Verint (OKTA-125496)
- OKTA-121113 — Automatically importing users failed in some circumstances.
- OKTA-121486 — Even after users reset their passwords, their status remained in a reset password state in Okta.
- OKTA-121892 — The ManagerUpn attribute on the AD appuser was not updated when pushed from Okta.
- OKTA-122450 — The Clear User Sessions button failed to display on the user profile for some users.
- OKTA-122684 — Some reset password links did not expire.
- OKTA-122780 — Some users received an internal error message when selecting the Box chiclet.
- OKTA-124266 — The custom expression link in the Active Directory integration screen redirected to the wrong page.
- LiquidFiles (OKTA-121955)
- Space IQ (OKTA-123613)
- BetterCloud (OKTA-125215)
- Evernote Business (OKTA-123979)
- Girard Securities (OKTA-111336)
- Hertz Gold Plus Rewards (OKTA-124848)
- Kaspersky CompanyAccount (OKTA-122566)
- Markel Insurance (OKTA-124511)
- QuickVTR (OKTA-123986)
- Sage Employee Self Service (OKTA-124880)
- WorkdayCommunity (OKTA-125175)
- OKTA-116651 — Backslash characters displayed twice for some users in attribute mappings.
- OKTA-119776 — Some admins received an error message when attempting to approve apps on their task page.
- OKTA-119792 — Some users were unable to enroll RSA devices with Okta’s New Sign-in flow.
- OKTA-122836 — A scheduled user update did not import custom attributes.
- OKTA-122855 — Some users saw task lists for unassigned apps.
- OKTA-123622 — Some Internet Explorer users could not mark account deprovisioning tasks as complete.
- OKTA-125194H — Authentication failed for locked out users in orgs with JIT and AD delegated authentication enabled.
- Clarizen (OKTA-113837)
- Absolute Data & Device Security (OKTA-123628)
- CloudCheckr (OKTA-124280)
- G Suite (OKTA-124179)
- Google Accounts Personal (OKTA-124302)
- Google AdSense (OKTA-124288)
- Google AdWords (OKTA-124298)
- Google Analytics (OKTA-124290)
- Google Apps Admin (OKTA-124429)
- Google Mail (Offline) (OKTA-124436)
- Google Play Developer Console (OKTA-123809)
- Guardian Insurance (OKTA-121265)
- Postmark (OKTA-123677)
- ProProfs (OKTA-124314)
- ReviewSnap (OKTA-124349)
- SHRM Online (OKTA-123189)
- Squarespace V6 (OKTA-123784)
- YouTube (OKTA-124138)
- OKTA-110523 — Agent embedded browsers failed to display OAuth options on Win2k16 when Internet Explorer (IE) Enhanced Security Configurations(ESC) are enabled.
- OKTA-113433 — Safari users received an incorrect error message when signing in to Okta.
- OKTA-115168 — Application Administrators were incorrectly allowed to create an OpenID Connect service client even though they weren't assigned an OpenID Connect client app.
- OKTA-117353 — Admins' Task counter displayed an inordinate number of tasks.
- OKTA-120425 — The OMM dashboard was non-responsive for some users.
- OKTA-120883 — The Dutch language did not translate properly in the Okta Widget for Chrome and Firefox browsers.
- OKTA-123576H — The Android for Work Setup button (Devices > Mobile Policies > Mobile tab) was non-responsive when the sign on method for the G Suite app was SAML 2.0.
- OKTA-123777H — The Okta Sign On form did not appear when signing in with Firefox version 45.x.x Extended Support Release.
- OKTA-123911H — Users received an incorrect error when attempting to reset their password.
-
ShowPro (OKTA-116217)
-
Aetna Health Insurance (OKTA-123000)
-
Donnelley Financial Solutions File16 (OKTA-123198)
-
Frontline Education (OKTA-123177)
-
Guardian by LawLogix (OKTA-122910)
-
Lifelock (OKTA-123197)
-
My Ceridian Solutions (OKTA-121195)
-
TravelCube Pacific (OKTA-123159)
- OKTA-96981 - Users changing their passwords did not receive the correct error message for invalid passwords.
- OKTA-109336 - Users changing their passwords did not receive the correct error message for insufficient password requirements.
- OKTA-110838 - Users changing their password multiple times a day or reusing old passwords did not receive the correct error message.
- OKTA-115189 - Sign-in flow failed for some users.
- OKTA-116029 - Admins were unable to sync Active Directory groups that contained users moved between an Organizational Unit (OU) that was synced to Okta and an OU that was not.
- OKTA-119626 - Modifying the tenantName attribute of existing user profiles caused an API validation failure.
- OKTA-120005 - Admins were unable to customize an email template for users with forgotten passwords.
- OKTA-120329 - Admins were unable to deactivate and reassign Yubikeys from deleted users.
- OKTA-120410 - Admins were unable to move users from a group with roles assigned to one without.
- OKTA-121122 - Running multiple tasks for some users caused Invalid Credentials.
- OKTA-121794/OKTA-123378H - Provisioning failed for Coupa OAN app.
- ADP Workforce Now (Admin) (OKTA-119713)
- Ceridian Online Customer Support (OKTA-121196)
- G Suite (OKTA-122199)
- Impraise (OKTA-122557)
- NCM Axcessa (OKTA-122565)
- ONE by AOL Mobile (OKTA-121276)
- Sophos Partner Portal (OKTA-118766)
- Ticketmaster (OKTA-122560)
- US Messenger (OKTA-122562)
- OKTA-122442H – AD LDAP Group and User filters did not work as expected because uppercase characters in Boolean variables were changed to lowercase after settings were saved.
- OKTA-88095 – Trusted proxies from network zones were not used in the Network Zones feature.
- OKTA-100438 – Users were unable to switch to other factors after selecting SMS authorization.
- OKTA-108988 – Some users assigned the G Suite application were unable to update their Google Group memberships.
- OKTA-110028 – Okta's SCIM client did not handle the response correctly when the 204 status code was returned by the server.
- OKTA-111809 – Excessive emails about certificate expiration were sent to users.
- OKTA-112868 – Some users received login error messages.
- OKTA-113809 – All password requirements were displayed when a user forgot their password instead of the password requirements selected by admins.
- OKTA-114022 – Sign out failed in the app MFA screen.
- OKTA-114853 – In some cases the SP-side API token for provisioning could not be refreshed.
- OKTA-115166 – Some app admins were unable to modify the applications permitted in their Profile Editor.
- OKTA-115179 – App admins without permission to import new users saw the option to import CSVs.
- OKTA-117461 – Admins were unable to properly modify application labels.
- OKTA-117697 – Deleting a user from a group exceptions rule caused the rule to fail.
- OKTA-118911 – Some locked out users displayed as Active on the admin dashboard.
- OKTA-118912 – Some admins received error messages when deactivating accounts.
- OKTA-118927 – Admins were unable to edit their users' mobile number in their user's Settings Page.
- OKTA-119364 – Some admins received an error when creating a new user.
- OKTA-119654 – Users received an incorrect error when attempting to reset their password.
- OKTA-120008 – Push groups by rule failed when groups had the same name, but different descriptions.
- OKTA-120678 – Identity provider signature certificates failed to display.
- OKTA-120830 – New end users whose secondEmail attribute was AD-mastered and was set to Read Only in the Profile Editor could not complete the Okta welcome flow.
- OKTA-121432 – Filtering by Event Type in the System Log failed for some users.
- OKTA-121854 – Some users were unable to enable SSL pinning on the RADIUS agent.
- OKTA-121690 – Updating a user's mobile number in the user profile did not update the number in the user's Settings Page and deleted the previously-configured number.
- JAMF Software Server (JSS) (OKTA-120322)
-
AirWatch Portal (OKTA-120568)
-
Akamai EdgeControl (OKTA-120409)
-
ASAE (OKTA-120595)
-
BT Cloud Phone (OKTA-120571)
-
CBRE (Employee Login - The Navigator) (OKTA-121509)
-
Cisco AMP for Endpoints (OKTA-120968)
-
Credible Behavioral Health (OKTA-120697)
-
CUNA Mutual (OKTA-120733)
-
Datahug (OKTA-121489)
-
G5 Action Analytics (OKTA-121506)
-
GTA Travel (OKTA-120792)
-
IBM Workspace (OKTA-121501)
-
Informatica Award Program (OKTA-120596)
-
Liveramp (OKTA-121512)
-
Maxemail (OKTA-120809)
-
MySonicWall (OKTA-120291)
-
National Life Group (OKTA-120567)
-
NGS Connex (OKTA-120591)
-
Roadmunk (OKTA-121504)
-
SAP Support Portal (OKTA-120909)
-
ShareThis (OKTA-121513)
-
TimeLog (OKTA-120590)
-
Twitter (OKTA-121124)
-
United Concordia (OKTA-120594)
-
XSplit (OKTA-121497)
- OKTA-79821 - The Save Password button failed to save the password for some users.
- OKTA-86540 - IP Zones were listed by ID instead of by name or order last added.
- OKTA-111018 - Users with the Okta New Sign-In Page enabled received a 400 Bad Request when attempting to sign into Veeva Vault app.
- OKTA-111656 - The Okta plugin failed to sign in some users.
- OKTA-112935 - When some admins attempted to create an AD-mastered user, an Okta-mastered user was sometimes created instead.
- OKTA-113253 - When admins used a Reset Password template, their end users were redirected to a 403 error page.
- OKTA-114197 - After deleting a user with an enrolled device, the Device Overview page failed to load.
- OKTA-114853 - Some users' refresh token failed to refresh.
- OKTA-115282 - Setting up the Security Key (U2F) key factor from the user account page resulted in an error message.
- OKTA-117968 - Some users received an error when importing users from their Okta Production org.]
Note: OKTA-113496H – If you experienced a timeout error while attempting to create a large number of user accounts via the API, contact Okta Support for a possible remedy.
-
CrazyEgg (OKTA-119975)
-
Egnyte (OKTA-120373)
-
ESPN (OKTA-120482)
-
Google AdSense (OKTA-120154)
-
MetLife MyBenefits (OKTA-120301)
-
Microsoft OneDrive (OKTA-120264)
-
SyncBASE (OKTA-120149)
-
Union Bank (OKTA-119767)
-
Verizon Wireless Business (OKTA-120221)
-
Saba (OKTA-112840)
-
Bill.com (OKTA-119939)
- OKTA-115172 - Read-only admins and mobile admins were able to delete users from a Profile Master.
- OKTA-114321 - Use of the Amazon Assistant plugin triggered rate limit errors for some Internet Explorer users.
- OKTA-118120 - Customers experienced a 500 error when attempting to Retry on the Task page.
- OKTA-105635 - Provisioning failed for GoToMeeting new users.
- OKTA-115172H - Read-only and Mobile admins had greater access rights for Profile Master actions than permitted by their defined roles.
- OKTA-117336 - When Okta deprovisioned a user in Rally, the user's role reverted to the original value pushed from Okta in spite of adequate mappings.
- OKTA-118733H - The label on a button located in the Okta footer was difficult to read because the font was too dark.
- OKTA-120086H - Out-of-network Windows users attempting to access Okta managed apps configured to deny such access were redirected to a Windows third-party enrollment page instead of the standard Access Denied page, as expected.
-
ADP Workforce Now (Admin) (OKTA-104388)
-
ADP Workforce Now (Employee) (OKTA-104388)
-
Awin (OKTA-118368)
-
CallRail (OKTA-119212)
-
Creately (OKTA-119223)
-
Edward Don and Company (OKTA-119203)
-
Flurry (OKTA-119224)
-
Real Capital Analytics (OKTA-119391)
-
Travitor (OKTA-116914)
-
Zkipster (OKTA-118207)
-
Attendease (OKTA-117520)
-
Rally Software (OKTA-117336)
-
Workfront (OKTA-110025)
- OKTA-107707 - AD-mastered users received an incorrect description of the password complexity requirement when changing or resetting passwords if the Group Password Policy feature was not enabled.
- OKTA-112348 - Concur users could not update employee IDs because of a change in the Concur API.
- OKTA-113061 - ADP users received an error after disabling a group in their Active Directory.
- OKTA-114022 - The Sign Out button located on the App MFA screen failed to sign out users.
- OKTA-114203 - Deleted and deactivated App Wizard or org-created applications were still assignable to admins.
- OKTA-115824 - The generated list of Zscaler IP Addresses was stale.
- OKTA-117237 - Some users could not sign into Skype for Business when the Office 365 sign-on policy denies ActiveSync traffic.
- OKTA-117305 - A link emailed to some AD-mastered users to unlock their accounts resulted in a 403 error.
- OKTA-118196 - Enabling or disabling Exchange ActiveSync settings for Office O365 failed for some orgs.
- OKTA-118544 - Removed Mobile Admin rights were incorrectly restored to some users.
- OKTA-118733H - The label on a button located in the Okta footer was difficult to read because the font was too dark.
-
AdvancedMD (OKTA-117176)
-
Amazon Associates CA Affiliate (OKTA-117060)
-
Amazon CA (OKTA-116925)
-
Amazon Web Services (OKTA-115117)
-
Amplitude (OKTA-117441)
-
AP Stylebook (OKTA-117712)
-
Atlas Solutions (OKTA-117476)
-
AvayaLive (OKTA-115557)
-
Bing Ads (OKTA-116205)
-
BioCentury (OKTA-117566)
-
Codeship (OKTA-117369)
-
Confluence (Atlassian) (OKTA-116216)
-
D2L (OKTA-117567)
-
Dash (OKTA-116424)
-
Dataloader.io (OKTA-115819)
-
DealerSocket AAX (OKTA-117127)
-
Dell EMC (OKTA-117569)
-
Docker Hub (OKTA-115331)
-
Essendex (OKTA-114906)
-
Exclusive Resorts (OKTA-117126)
-
Geckoboard (OKTA-116259)
-
Give Something Back (OKTA-117129)
-
Hellofax (OKTA-118422)
-
HelloSign (OKTA-115502)
-
Inspired eLearning (OKTA-116992)
-
JoyentCloud (OKTA-117565)
-
Kaiser (OKTA-116425)
-
Kampyle (OKTA-116427)
-
LawRoom (OKTA-117420)
-
Lifesize Cloud (OKTA-115541)
-
MarkMonitor (OKTA-117125)
-
MathWorks (OKTA-115559)
-
MetLife MyBenefits (OKTA-116356)
-
Nature.com (OKTA-116426)
-
OpenVPN Connect (OKTA-117714)
-
Operative.One (OKTA-117179)
-
Oracle Human Capital Management (OKTA-117130)
-
Oracle Partner Store (OKTA-117713)
-
Oracle Support (OKTA-116428)
-
Rackspace Cloud Control Panel (OKTA-117443)
-
RackSpace Webmail (OKTA-116598)
-
RingCentral (OKTA-115817)
-
RingCentral (UK) (OKTA-117124)
-
RingCentral SWA (OKTA-115555)
-
SendGrid (OKTA-116385)
-
Skype (OKTA-115290)
-
Smartsheet (OKTA-116462)
-
SnapAV (OKTA-117128)
-
SpyFu (OKTA-117143)
-
Team Gantt (OKTA-117007)
-
Tech Data (OKTA-115664)
-
Teladoc (OKTA-117572)
-
Twilio (OKTA-117571)
-
Uline (OKTA-118130)
-
ZocDoc (OKTA-116699)
- OKTA-115175 - Read-only admins and Mobile admins had access to an invalid navigation link.
- OKTA-117259 - When users requested access for a bookmark app they received a 500 internal server error message.
- OKTA-115205 - Some Microsoft Office 365 WS-FED events were incorrectly logged as policy errors.
- OKTA-116869 - RightNow CX provisioning failed with an HTTP transport error.
- OKTA-114241 - Assigning users to an app sometimes failed when the locale attribute contained an underscore.
- OKTA-116873 - Users were not properly imported into the Kickboard app from a CSV file.
- OKTA-97702 - Some News UK users received Google license errors.
- OKTA-115419 - Provisioning users to the Verecho app failed.
- OKTA-116655 - All groups were not visible when adding or editing groups.
- OKTA-118765H - After deleting a user, some successfully imported users did not appear on the Import tab, or appeared as imported with conflicts.
-
PhotoBucket (OKTA-117940)
-
Soundcloud (OKTA-117941)
-
Pilgrim SmartSolve (OKTA-113317)
- OKTA-26128 - The maximum length of a string in a password policy could not be validated under certain circumstances.
- OKTA-90569 - Permission errors were thrown when attempting to send messages to end users.
- OKTA-93556 - An error message was not received after entering a blank email when unlocking a user account.
- OKTA-93953 - The password field accepted only two digits instead of three when configuring password attempts.
- OKTA-107621 - The System Log incorrectly showed a Zone as OFF_NETWORK, even though it was correctly processed as ON_NETWORK.
- OKTA-108000 - In the SAML Settings section of the App Integration Wizard, the Custom Field Mappings Expressions dialog box rendered incorrectly.
- OKTA-108219 - The Okta browser plugin 's auto-login feature failed for a custom SWA app in certain circumstances.
- OKTA-110347 - The legacy EventType was missing from the downloadable System Log report.
- OKTA-110623 - Custom attributes with Read-Write user permission added to the Okta user profile did not appear in end user Personal Information settings unless the admin added an attribute value.
- OKTA-111332 - Deactivated users were not returned in user searches.
- OKTA-111339 - Users from Salesforce who have a custom profile in the EA Salesforce Community and Portal feature could not be imported.
- OKTA-111394 - When the group password policy or password policy Softlock features were enabled, users could not unlock AD accounts with self-service unlock.
- OKTA-111945 - Mobile phone information was not written to the correct location in the Facebook@Work app.
- OKTA-112045 - Reset MFA was unavailable on the Admin Dashboard when Prompt for Factor was not selected in the security policy.
- OKTA-113380 - All users were deprovisioned from the SuccessFactors app (EA) during scheduled imports in certain circumstances.
- OKTA-113485 - Some Group Push rules could not be deleted.
- OKTA-113524 - The Pending Task Notification banner displayed for some apps when there were no pending tasks.
- OKTA-113961 - Users marked as billing and technical contacts could not be deleted.
- OKTA-114101 - When trying to reset a password using SMS, sending the code failed on the first attempt.
- OKTA-114165 - Transaction event lag was not displayed in the System Log 2.0.
- OKTA-114592 - Timezone and Locale user attributes were not saved correctly in the Salesforce app.
- OKTA-114983 - Deleting API tokens failed when the admin who created the token was deleted.
- OKTA-115769 - No error message displayed when admins with insufficient permissions tried to assign users to a group.
- OKTA-117646H – In the Active Directory Import tab, a message in the Import Results screen reported that some number of imported users needed review but no user records were listed in the main table.
- OKTA-117757H – A language other than the configured language was displayed after signing in to Okta from a new device or from a browser not previously used to sign in to Okta.
- OKTA-118132H – The Okta service was temporarily unavailable for HTTP requests with invalid region values.
The following SWA apps were not working correctly and are now fixed:
-
Audible (OKTA-114601)
-
GEHA (OKTA-114569)
-
Google Merchant Center (OKTA-114806)
-
KnowledgeTree (OKTA-114606)
-
Limeade (OKTA-114803)
-
Mango Languages (OKTA-114618)
-
MINDBODY (OKTA-114620)
-
Newport Group (OKTA-114608)
-
Nextiva NextOS 3.0 (OKTA-113038)
-
SAP NetWeaver Application Server (OKTA-114801)
-
Skillshare (OKTA-114622)
-
UsabilityHub (OKTA-114160)
- OKTA-59054 - A non-operational button to globally expire passwords was displayed in error.
- OKTA-84474 - For end users required to provide MFA, the IWA background image failed to appear during sign on.
- OKTA-89842 - Users were shown a menu option for which they did not have permissions and received an error page.
- OKTA-89870 - The Assign Apps option was incorrectly available for the User Admin.
- OKTA-89874 - Users profile pages did not display assigned applications.
- OKTA-93556 - An empty email field failed to display the appropriate error message.
- OKTA-96219 - Users created in downstream applications sometimes had the wrong group level attribute.
- OKTA-98392 - Mobile setup for Duo MFA failed to scale for mobile devices.
- OKTA-104954 - Null values for SCIM app custom attributes were not pushed to third-party apps.
- OKTA-105809 - A 400 Bad Request error was caused when more than thirty users signed in using a single browser.
- OKTA-105873 - Importing users via a CSV file failed for some types of apps.
- OKTA-106534 - Box settings changes were saved even after the service account validation failed.
- OKTA-106579 - Users weren't deactivated in Okta when the option Immediate Termination Reason for a Contingent Worker was set in Workday.
- OKTA-106902 - Following an AD Import, the Employment Status and Job Information fields were not mapped in BambooHR.
- OKTA-107388 - In app attribute settings, the Group Priority option Combine values across groups reverted to Use Group Priority after provisioning settings were changed.
- OKTA-107998 - API-activated users were successfully created and assigned to a group, even when they did not meet the group's password requirements, but failed at activation.
- OKTA-108093 - Microsoft Office 365 failed to push null values for the Description in a Distribution List or Security Group.
- OKTA-108477 - Signing in to ClearCompany from the Okta dashboard failed.
- OKTA-109159 - Manipulating HTML script tags for use in the Okta MFA security question was prevented, while saving unsafe database additions was allowed.
- OKTA-110000 - When group memberships in Org2Org were updated, members were removed, then re-added. In some cases this caused unwanted deprovisioning.
- OKTA-110090 - Workday-mastered, imported end-users were intermittently arrested in an activating status.
- OKTA-111110 - An empty Reports section on the Admin Dashboard was displayed inadvertently.
- OKTA-111322 - Group Pushes to Slack failed.
- OKTA-111339 - Salesforce Community provisioning failed for custom Community user profiles.
- OKTA-111391 - End-users were prompted for MFA more often than the specified, app-specific sign on policy rule.
- OKTA-111609 - The new System Log did not log User attempted unauthorized access to app events.
- OKTA-111614 - System Log queries containing the { character failed.
- OKTA-111662 - Users imported from the RightNow CX app did not have an External ID attribute.
- OKTA-111832 - Authenticating users failed for apps that use wrappers.
- OKTA-112707 - The Show More button did not display when filtering the list of OAN applications by Supports Provisioning.
- OKTA-112713 - Users were prompted twice for credentials: once to access OKTA, and again to access a SAML app.
- OKTA-113380H - All users were deprovisioned from the EA Success Factors app during scheduled imports.
- OKTA-113406 - Passcode rules were sent to iOS and Mac OSX devices even though a Simple Passcode policy had not been configured.
- OKTA-113873 - Okta SMS failed to re-send an authentication code during MFA enrollment.
- OKTA-114245 - Requesting the SAML ACS endpoint by URL failed for some existing apps.
- OKTA-114296H - Users of Firefox browser version 51.0 and later were prompted to install the Okta browser plugin even though it was already installed and functional.
- OKTA-114334H - In our support for multiple ACS URLs, SAML responses contained incorrect recipient and destination URLs.
- OKTA-114885H - Attempting to clear a group provisioning error by changing a user's samAccountName via the Task page failed.
- OKTA-116085H - Updating app profiles for a large number of assignments failed in some circumstances.
- OKTA-116211H - Group rules were not processed in some circumstances.
The following SWA apps were not working correctly and are now fixed:
-
Account Research Manager (OKTA-112001)
-
Becker CPA Exam Review (OKTA-113793)
-
Club OS (OKTA-113777)
-
DataSafe (OKTA-113471)
-
Dell Member Purchase Program (MPP) (OKTA-112809)
-
Engage (OKTA-113764)
-
Engrade (OKTA-112825)
-
FidelityPSW (OKTA-111625)
-
FlightStats (OKTA-113795)
-
Glassdoor (OKTA-112826)
-
IFTTT (OKTA-113794)
-
IMDB Pro (OKTA-113491)
-
J.P. Morgan ACCESS (OKTA-112816)
-
MassMutual RetireSmart (OKTA-112822)
-
Mastermind (OKTA-112358)
-
Netatmo Channel (OKTA-113603)
-
PaperHost (OKTA-113602)
-
Practising Law Institute (OKTA-112812)
-
Redis Labs (OKTA-113422)
-
ROI Solutions (OKTA-113762)
-
ShipStation (OKTA-112293)
-
Site5 (OKTA-113790)
-
Stack Overflow Careers (OKTA-114146)
-
StatusCake (OKTA-114162)
-
The Hartford EBC (OKTA-113160)
-
The Institutes (OKTA-112814)
-
Ticketmaster ONE (OKTA-112819)
-
TriCare (OKTA-113402)
-
VerizonWireless (OKTA-112811)
-
ZipRecruiter (OKTA-112810)
-
Microsoft Hotmail (OKTA-113181)
- OKTA-105737 – Some diacritical marks were missing in the Czech language version of end user settings and security questions.
- OKTA-107252 – Some end-users received an error when submitting their cell number for SMS-based, self-service password reset.
- OKTA-108889 – Overly restrictive requirements prevented private apps from uploading to the Private App Store.
- OKTA-109731 – After assigning an app to a group and changing one user to individual assignment, unassigning the group failed.
- OKTA-111070 – Connecting to the Asana SCIM server failed for TLS1.2.
- OKTA-111174 – The Okta Sign In page did not resize automatically on some iPhone versions.
- OKTA-111344 – The Importing users from CSV message did not clear even though the import completed successfully.
- OKTA-111577 – SSO to the Quantas app failed for Internet Explorer.
- OKTA-111707 – After enabling the New Okta Sign-In Experience for some orgs, the sign-in fields weren't visible.
- OKTA-112193H – In certain circumstances, schema discovery failed after enabling provisioning settings of the Org2Org app.
- OKTA-112886H – In orgs with mobile policies created before introduction of the passcode option Allow simple value, iOS and OSX device users were prompted to change their passcode if any platform rules were changed.
The following SWA apps were not working correctly and are now fixed:
- Adobe Connect (OKTA-110809)
- Launch Bit (OKTA-110759)
- Majestic SEO (OKTA-111933)
- Microsoft Volume Licensing (OKTA-112002)
- Mozilla ADD-ONS (OKTA-103316)
- Schwab StockPlanManager
- (OKTA-111237)
- Tech Data (OKTA-111088)
- US Bank Pivot (OKTA-111088)
- Zoho Docs (OKTA-111582)